A SOC analyst is a professional responsible for protecting an organization against cybersecurity threats. This includes their monitoring and analysis, attack investigation and prevention. Such an analyst also has an important role in the improvement and development of corporate security framework, educating and training employees, and ensuring compliance with the legal requirements.
To fulfill their tasks, analysts require a comprehensive set of tools and services. A core part of this inventory is monitoring and detection systems (SIEM, IDS/IPS) and analytic services (sandboxes, vulnerability scanners, threat intelligence solutions). Also, of much use are response and mitigation tools, services for teamwork, staff training and community collaboration.
Let’s see how these tools can help.
1. Threat Intelligence Lookup: Smart Threat Investigation
Threat Intelligence Lookup from ANY.RUN is a good example of a multifunctional analytic tool. It is a search engine for threat indicators and attack events with contextual data within a database of malware samples.
Search requests may include indicators of compromise, of behavior, and of attack (IOCs, IOBs, IOAs). Several dozens of search parameters are supported: they describe indicators’ features and behaviors, network connections and processes, and can be combined to architect queries for precise results. TI Lookup supports MITRE ATT&CK matrix, and YARA and Suricata rules.
TI Lookup in SOC expert’s routine
TI Lookup provides invaluable data not only for studying and understanding threats, attacks and adversaries. It helps implement a proactive approach to security by using the findings for setting up and fine-tuning security systems.
It also speeds up incident investigation and provides data for informed decision-making on all the levels of risk management. Automated updates of search results help the security team stay on top of new and emerging threats and be ready before they strike.
This example of a TI Lookup query includes the name of the recently active malware and the path to one of the malicious files used in an attack:
filePath:”dbghelp.dll” AND threatName:”lumma”
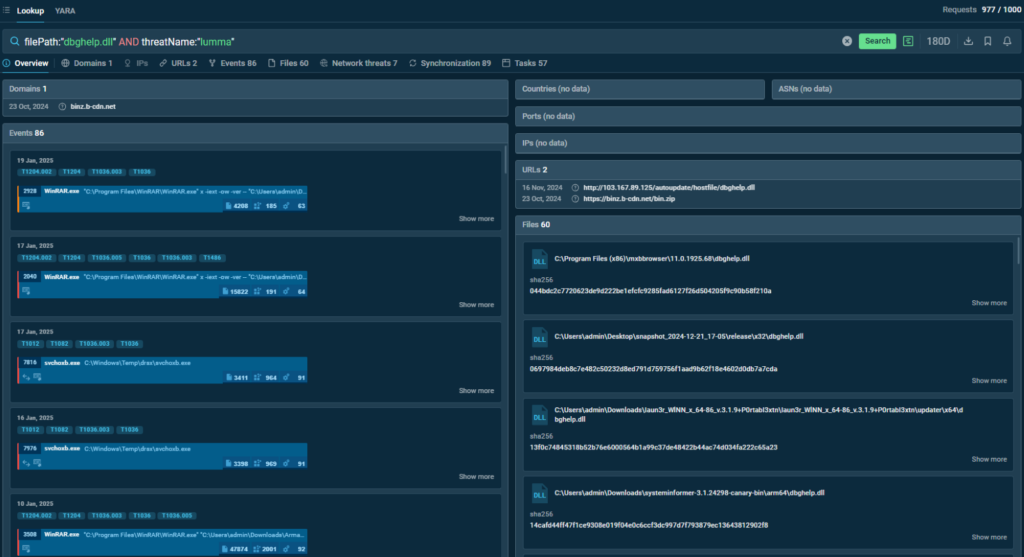
Results displayed by TI Lookup for the query
TI Lookup finds files associated with the attack and shows sandbox sessions featuring analysis of samples belonging to the same campaign.
2. Malware Sandbox: Detonate the Threat in Safe Environment
ANY.RUN’s Interactive Sandbox allows to execute potentially malicious software, open suspicious links or files in the safety of a customizable virtual machine.
Using sandbox is the easiest first step into malware analysis, even setting up the virtual machine is not mandatory. Interactive session provides fast understanding of malware behavior and mechanics.
When a security expert is ready to dive deeper, the above-mentioned TI Lookup is there for them to further study the artifacts and indicators discovered via a sandbox session. The Sandbox and Lookup actually can work as an integral research ecosystem with a user switching between them while gathering and analyzing more and more data.
For instance, the search results on AsyncRat trojan in TI Lookup feature a “Tasks” tab that lists recent sandbox sessions with this malware.
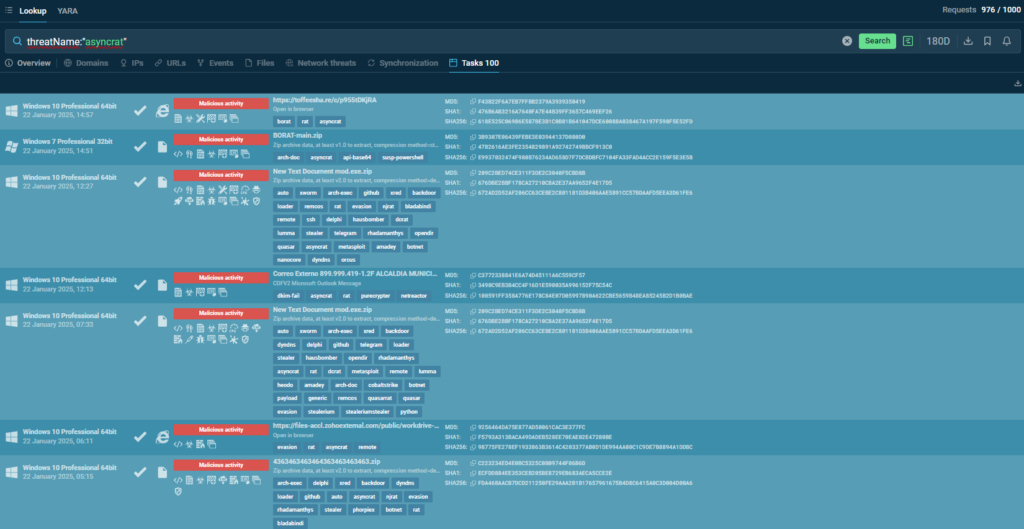
Sandbox sessions in which AsyncRat malware was spotted
Each of the found sandbox sessions can be restarted with the same or adjusted parameters of the virtual machine. All the processes, connections, requests, files, domains, and other indicators can be searched and researched via TI Lookup.
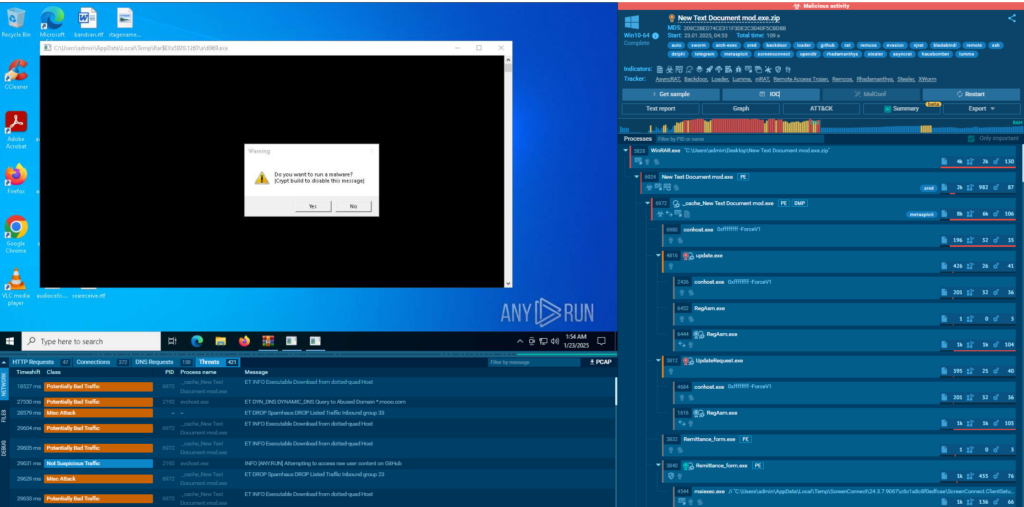
One of the sandbox sessions found via TI Lookup with AsyncRat analysis
3. SIEM: Watch Your Perimeter Closely
Security Information and Event Management (SIEM) systems concentrate on events that occur in the organization’s own network. By analyzing system logs, the SOC team identifies events that might indicate a security incident, analyzes patterns or sequences of events to understand its potential relation to a cyberattack. Various correlation rules are used to link events that do not seem suspicious in isolation but could be part of an attack when viewed together.
Real-time monitoring and alerts are set up to notify security teams of suspicious signals.
Threat intelligence services like TI Lookup provide SIEM systems with data on artifacts and indicators that could be used to uncover the malicious nature of events and detect threats before they detonate.
4. IDS/IPS: When the Worst Happens
Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) are there to react to happening or attempted attacks. An IDS monitors network traffic for signs of possible incidents, violations, or imminent threats. It looks for signatures of known threats or anomalies in network behavior.
These systems can detect attacks in real-time or near real-time. But their signature-based approach might cause them to miss zero-day exploits. Even if detection is well-tuned, false positives sometimes happen. Manual intervention is typically required to address detected threats.
An Intrusion Prevention System (IPS) not only detects but also takes immediate action to stop or prevent attacks. It reduces the need for manual intervention by automatically responding to threats but can introduce latency due to inline processing of network traffic.
Risk of false positives blocking legitimate traffic and processes is also present. The system requires careful configuration to balance security with network performance.
5. Threat Intelligence Feeds: Data Ready-To-Use
TI Feeds are data streams of indicators of compromise (like malicious domains, IP addresses, links and file hashes). They are integrated into security systems and enable SOC staff to quickly detect and respond to malicious activity, including the execution of zero-day exploits and emerging malware.
The data in the feeds is from their intelligence sources and channels, structured, de-duplicated, and formatted into a standardized layout. It may get enriched by correlating with other sources to add more context around each indicator. It’s then used to generate detection rules, signatures, watchlists, and so on.
ANY.RUN’s TI Feeds contain data from public malware and phishing samples analyzed by a community of 500,000 researchers in the interactive sandbox. Feeds contain information on malicious IP addresses, domain names, and URLs, enriched with contextual details such as related files and ports.
Conclusion
A SOC analyst nowadays has an impressive arsenal of useful tools at their disposal. In order not to get lost in this variety, start building your inventory with data providing multifunctional solutions like Treat Intelligence Lookup by ANY.RUN.
Get 50 free requests to evaluate the potential of TI Lookup.



































