PE Tree Tool is a new open-source tool developed by the BlackBerry Research and Intelligence team for viewing Portable Executable (PE) files in a tree-view using PEfile and PyQt5. Basically it’s aimed at the reverse engineering community, PE Tree also integrates with HexRays’ IDA Pro decompiler to allow for easy navigation of PE structures, as well as dumping in-memory PE files and performing import reconstruction. PE Tree is developed in Python and supports the Windows, Linux and Mac operating systems. It can be installed and run as either a standalone applications.
Features:
• Standalone application, IDAPython plugin and Rekall plugin.
• Supports Windows/Linux/Mac.
• Rainbow PE ratio map:
◘ High-level overview of PE structures, size and file location.
◘ Allows for fast visual comparison of PE sample.
• Displays the following PE headers in a tree view:
◘ MZ header
◘ DOS stub
◘ Rich headers
◘ NT/File/Optional headers
◘ Data directories
◘ Sections
◘ Imports
◘ Exports
◘ Debug information
◘ Load config
◘ TLS
◘ Resources
◘ Version information
◘ Certificates
◘ Overlay
• Extract and save data from:
◘ DOS stub
◘ Sections
◘ Resources
◘ Certificates
◘ Overlay
• Send data to CyberChef
• VirusTotal search of:
◘ File hashes
◘ PDB path
◘ Timestamps
◘ Section hash/name
◘ Import hash/name
◘ Export name
◘ Resource hash
◘ Certificate serial
• Standalone applications:
◘ Double-click VA/RVA to disassemble with capstone
◘ Hex-dump data
• IDAPython plugin:
◘ Easy navigation of PE file structures
◘ Double-click VA/RVA to view in IDA-view/hex-view
◘ Search IDB for in-memory PE files;
◘ Reconstruct imports (IAT + IDT)
◘ Dump reconstructed PE files
◘ Automatically comment PE file structures in IDB
◘ Automatically label IAT offsets in IDB
• Rekall plugin:
◘ Operates against memory dump or live system
◘ View, dump and rebuild PE files from;
◘ Active processes and modules
◘ Loaded kernel-mode drivers
1. Standalone Application:
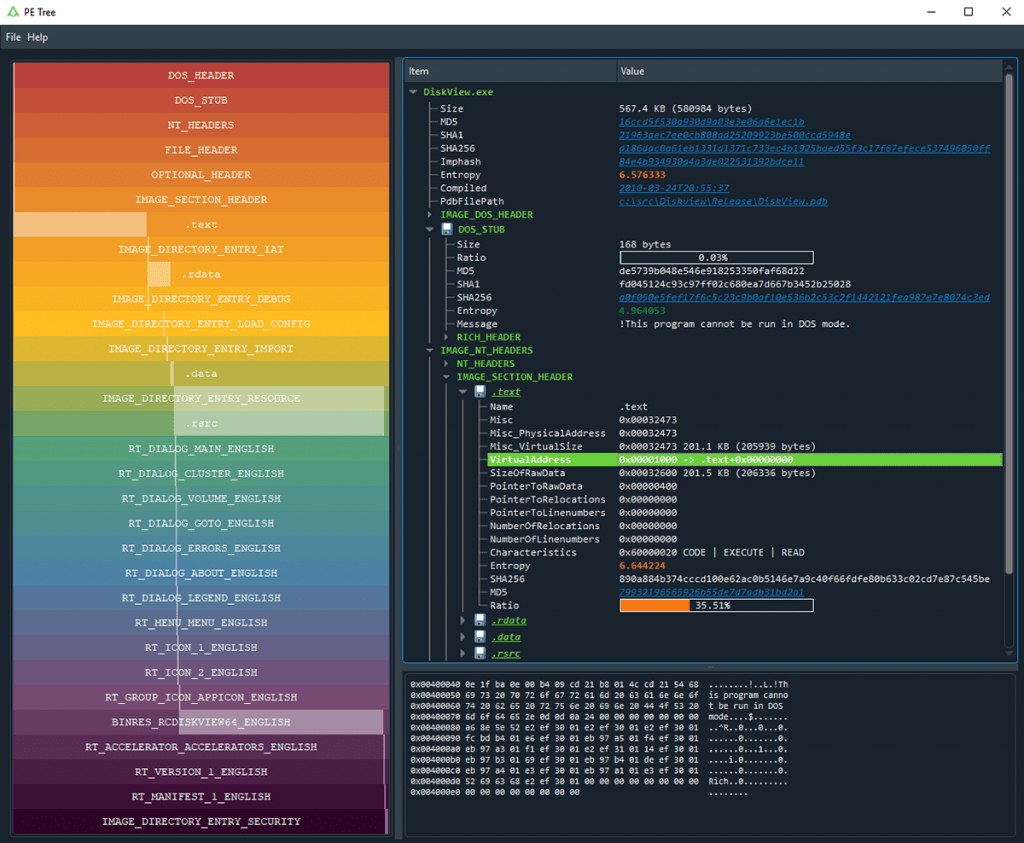
Requirements:
Installation:
Install directly from GitHub using a fresh virtual environment and pip:
For Windows:
| virtualenv env env\Scripts\activate pip install –upgrade pip pip install git+https://github.com/blackberry/pe_tree.git |
For Mac/Linux:
| $ python3 -m venv env $ source ./env/bin/activate $ pip install –upgrade pip $ pip install git+https://github.com/blackberry/pe_tree.git |
For developers: Git clone the repository and setup for development.
For Windows:
| git clone https://github.com/blackberry/pe_tree.git cd pe_tree virtualenv env env\Scripts\activate pip install -e . |
For Mac/Linux:
| $ git clone https://github.com/blackberry/pe_tree.git $ cd pe_tree $ python3 -m venv env $ source ./env/bin/activate $ pip install -e . |
Usage:
| Run PE Tree and use the GUI to select a file to view: $ pe-tree Run PE Tree and view the specified file/folder: $ pe-tree <path> Dark-mode can be enabled by installing QDarkStyle: $ pip install qdarkstyle |
2. IDAPython Plugin:
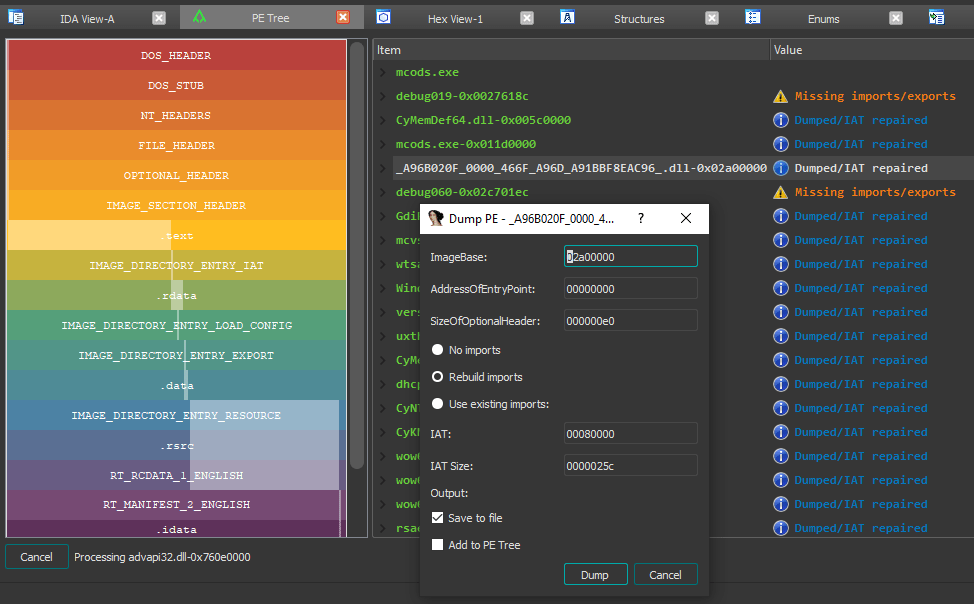
Requirements:
- • IDA Pro 7.0+ with Python 2.7
- • IDA Pro 7.4+ with Python 2.7 or 3.x
Installation:
To install and run as an IDAPython plugin you can either use setup-tools or install manually. Download pe_tree and install requirements for the global Python interpreter used by IDA: Here I had installed manually.
$ git clone https://github.com/blackberry/pe_tree.git $ cd pe_tree $ pip install -r requirements.txt |
Copy pe_tree_ida.py and the contents of ./pe_tree/ to your IDA plugins folder.
IDA plugins folders:
| OS | Plugins folder |
| Windows | %ProgramFiles%\IDA Pro 7.X\plugins |
| Linux | /opt/ida-7.X/plugins |
| Mac | ~/.idapro/plugins |
Usage:
• Run IDA and disassemble a PE file (select Manual Load and Load Resources for best results!).
• Click Edit -> Plugins -> PE Tree.
3. Rekall:
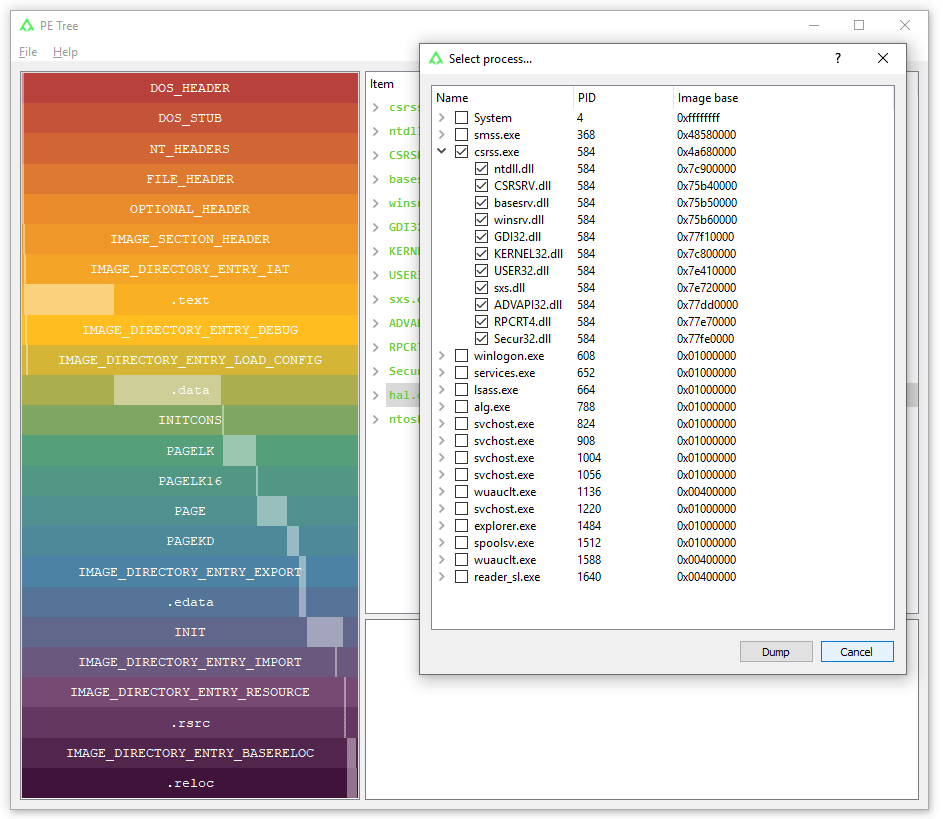
Requirements:
Installation:
• Install Rekall from GitHub.
• Install PE Tree standalone application (see Installation) under the same virtual environment.
Usage:
Run Rekall and dump active processes, DLLs and drivers on a live system:
| $ rekall –live Memory [1] Live (Memory) 00:00:00> run -i pe_tree_rekall.py |
Alternatively, run Rekall/PE Tree against an existing memory dump:
| $rekall -f memory.vmem [1] memory.vmem 00:00:00> run -i pe_tree_rekall.py |
Credits: Tom Bonner



































