What is the Malware Information Sharing Platform (MISP)?
MISP (formerly known as Malware Information Sharing Platform) is an open-source software medium for collecting, storing, distributing, and sharing cybersecurity indicators, incidents analysis, and malware analysis. Also, it helps incident analysts, security and ICT professionals, or malware reverse engineers to support their day-to-day operations to share structured information efficiently.
MISP plays a major role in security researching for analyzing threat data on detected malware attacks, automatically creating connections among malware and their characteristics, and storing data in a structured format. In addition, MISP also helps to make the rules for network intrusion detection systems (NIDS) and enables the sharing of malware information with third parties, which aims to create a platform of trust by locally storing threat information and enhancing malware detection to encourage information exchange among organizations.
Flow Diagram of MISP:
How does MISP work?
The MISP structure consists of events, feeds, communities, and subscribers. Normally an event is a threat entry containing information related to the threat and the associated IOCs. Once an event has been created, a user assigns it to a specific feed that acts as a centralized list of events belonging to a specific organization and containing certain events or grouping specifications.
MISP is utilized by numerous independent organizations in different industries, each with public-, proprietary-, or community-driven threat feeds. Once an instance is created, organizations can add events to their own feeds viewable by either only organization, or only community, or connected communities, or all communities.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
Accessible via a web interface or REST API, MISP consists of trusted independent users and organizational threat submissions, both ingested by the respective user base. Upon joining MISP communities, organizations can subscribe to feeds related to threats in their respective industries. After subscribing to the feeds, organizations can start ingesting API pull requests into SIEM platforms, detection rules, firewall blacklists, and so on. Moreover, organizations can contribute to the community, adding their feeds and events which can be shared among other community subscribers.
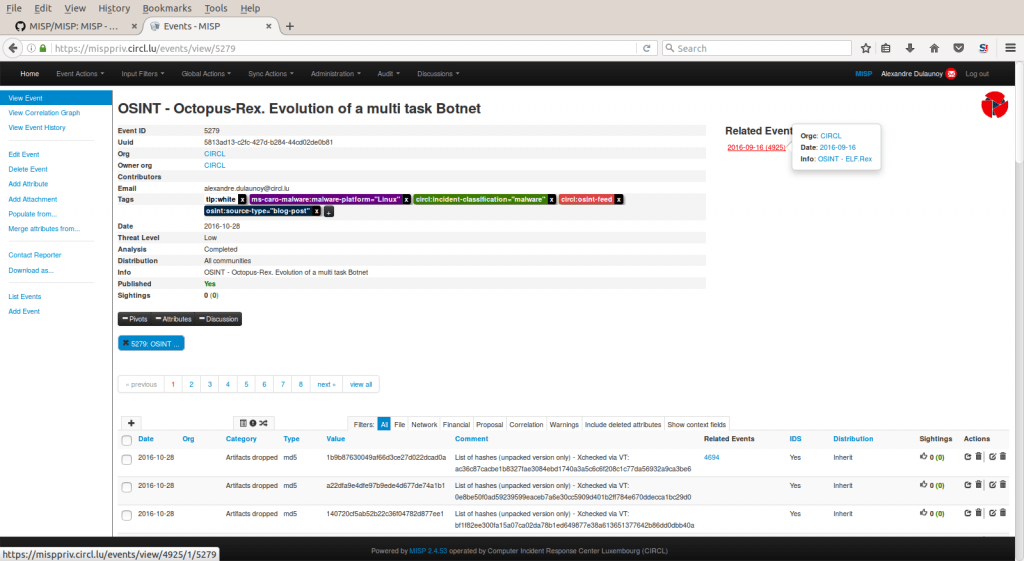
A sample event encoded in MISP:
What are the core functionalities of MISP?
| • Flexible free text import tool to ease the integration of unstructured reports into MISP. |
| • An efficient IOC and indicators database allowing to store technical and non-technical information about malware samples, incidents, attackers, and intelligence. |
| • Automatic correlation finding relationships between attributes and indicators from malware, attack campaigns, or analysis. The correlation engine includes correlation between attributes and more advanced correlations like Fuzzy hashing correlation (e.g. ssdeep) or CIDR block matching. Correlation can also be enabled or event disabled per attribute. |
| • A flexible data model where complex objects can be expressed and linked together to express threat intelligence, incidents, or connected elements. Also Read: Clickjacking Attack – How to Detect & Prevent this Attack? |
| • Built-in sharing functionality to ease data sharing using different models of distributions. MISP can automatically synchronize events and attributes among different MISP instances. Advanced filtering functionalities can be used to meet each organization’s sharing policy including a flexible sharing group capacity and attribute level distribution mechanisms. |
| • An intuitive user interface for end-users to create, update and collaborate on events and attributes/indicators. A graphical interface to navigate seamlessly between events and their correlations. An event graph functionality to create and view relationships between objects and attributes. Advanced filtering functionalities and warning lists to help the analysts to contribute events and attributes and limit the risk of false-positives. |
| • Storing data in a structured format (allowing automated use of the database for various purposes) with the extensive support of cybersecurity indicators along with fraud indicators as in the financial sector. |
| • Export: generating IDS, OpenIOC, plain text, CSV, MISP XML or JSON output to integrate with other systems (network IDS, host IDS, custom tools), Cache format (used for forensic tools), STIX (XML and JSON) 1 and 2, NIDS export (Suricata, Snort and Bro/Zeek) or RPZ zone. Many other formats can be easily added via the MISP-modules. |
| • Import: bulk-import, batch-import, import from OpenIOC, GFI sandbox, ThreatConnect CSV, MISP standard format, or STIX 1.1/2.0. Many other formats easily added via the MISP-modules. |
| • A gentle system to collaborate on events and attributes allowing MISP users to propose changes or updates to attributes/indicators. |
| • Data-sharing: automatically exchange and synchronize with other parties and trust-groups using MISP. |
| • Delegating of sharing: allows a simple pseudo-anonymous mechanism to delegate publication of events/indicators to another organization. |
| • Expansion modules in Python to expand MISP with your own services or activate already available MISP-modules. |
| • Sighting support to get observations from organizations concerning shared indicators and attributes. Sighting can be contributed via MISP user-interface, API as MISP document, or STIX sighting documents. |
| • STIX support: import and export data in the STIX version 1 and version 2 format. |
| • Real-time publish-subscribe channel within MISP to automatically get all changes (e.g. new events, indicators, sightings, or tagging) in ZMQ (e.g. MISP-dashboard) or Kafka publishing. |
| • Flexible API to integrate MISP with your own solutions. MISP is bundled with PyMISP which is a flexible Python Library to fetch, add or update events attributes, handle malware samples or search for attributes. An exhaustive restSearch API to easily search for indicators in MISP and exports those in all the format supported by MISP. |
| • Adjustable taxonomy to classify and tag events following your own classification schemes or existing classification. The taxonomy can be local to your MISP but also shareable among MISP instances. Also Read: Important Skills Required for Soc analyst from beginners to advanced level |
| • Intelligence vocabularies called MISP galaxy and bundled with existing threat actors, malware, RAT, ransomware or MITRE ATT&CK which can be easily linked with events and attributes in MISP. |
Installation:
For installation and download, Please check here.
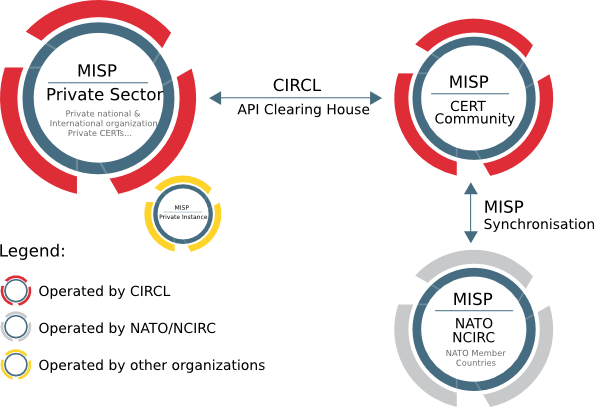
MISP organizations charts and community interactions:
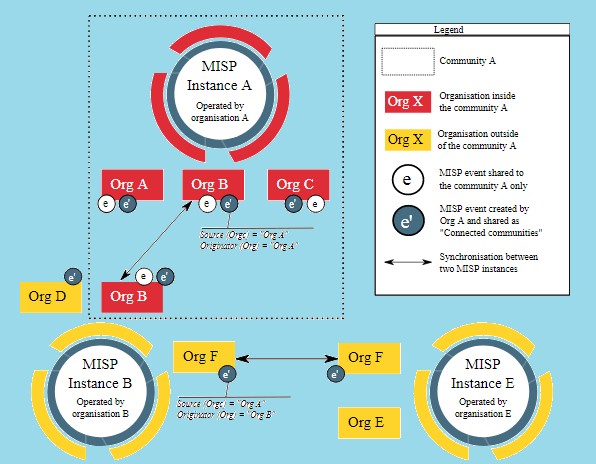
Also Read: Insecure Direct Object Reference – Prevention and Detection of IDOR
MISP is an open-source and flexible platform specifically made to be used by information-sharing communities, even when only some members of an organization are permitted to access the information shared in MISP. Also, it could help many organizations, in order to improve their cyber-defense capabilities.



































