JARM is the tool developed by the Salesforce team. This tool can be proactively used for threat hunting and incident response. It identifies the malware c2 connections within an intranet or outside the internet. Threat hunters can use this tool to generate a list of TLS hashes for connections established from clients to external servers and fingerprint each of those TLS connections to detect malware.
JARM fingerprints Generation & Uses:
- JARM has 10 TLS Client Hello packets in JARM which have been specially crafted to pull out unique responses in TLS servers.
- Responses are collected for the TLS version, cipher suites, extensions, and more into the TLS protocol layer.
- Collected parameters are used to generate the fuzzy hash which is called JARM Fingerprints, Example: google.com, JARM Fingerprint –
(27d40d40d29d40d1dc42d43d00041d4689ee210389f4f6b4b5b1b93f92252d )
Recommended Read to understand SSL/TLS attacks :TLS handshake & attacks - Most of the malware C2 domains are using the signed SSL certificates with their domains and show them as they are legit and spread infection and exfiltrate data.
- JARM will profile the malware domain’s TLS version, cipher suites, extensions, and more other parameters and it will generate the unique JARM fingerprint.
- Profiling of TLS traffic can be used to identify the malware C2 domains which is trying to mimic legitimate domains. Legitimate domains will always have a unique SSL certification with expiry dates, cipher suites, and more.
- Generates fingerprints can be used to identify malware domains versus legitimate domains.
- Threat hunters can use this technique to generate the list of JARM fingerprints and have a proactive blocklist of IPs and domains list.
- JARM support has been or is being added to SecurityTrails, Shodan, BinaryEdge, RiskIQ, Palo Alto Networks, Censys, 360.
Deployment into Detection and Response
- Download and install the JARM from github repository download here.
remnux@remnux:~/home$ git clone https://github.com/salesforce/jarm
- JARM tool itself will have a ready list for Top 500 alexa ranking websites , were SSL/TLS hashes can be generated . But for this demo we can manually create a list of domains to be monitored and generate the fuzzy hash.
- Above is my list of some social media websites, Since my organization’s employees keep visiting social media and other stuff, So I can be the next target to threats that can use legitimate domains that can be tampered with and spread c2 domains to infect networks. For example, Cobalt strike is the tool for red teamers and adversary simulation. Cobalt strick uses fake TLS certificates with the name of legitimate domains to infect machines and exfiltrate data. Profile list found here.
- Therefore JARM TLS profiling can be used to detect specfic machines that sends a signal to c2 domains.

- Start jarm.sh with the added domains in the list and save the output in any name.txt, Here it is fuzzyhash.txt.
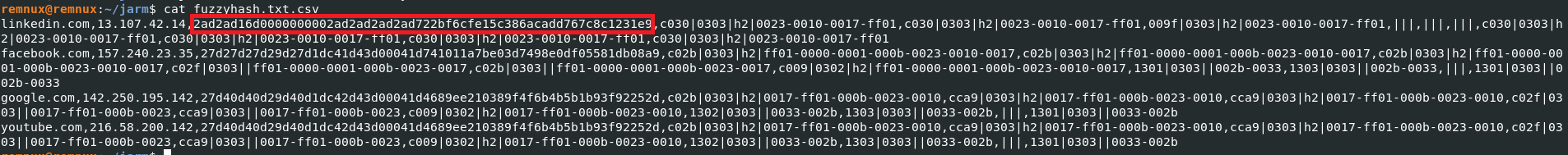
- Now we known the unique value for all legitimate domains , If any attacker is trying to mimic the legitimate domains that JARM hash will different and which shows as malicious activity.
| TLS Profile | Function | JARM HASH |
| linkedin[.]com | legitimate Domain and clean | 2ad2ad16d0000000002ad2ad2ad2ad722bf6cfe15c386acadd767c8c1231e9 |
| łinkedin[.]com | Malware | 3a7ankXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXaa8a8 |
Use cases :
- Lots of people will communicate to legitimate domains like youtube, google, etc, But as an incident responder whether all clients establish TLS connections with legitimate domains or malicious domains TLS connections.
- Prepare a proactive list of malware C2 servers and block them before they reach you.
- Comparing your JARM fingerprints with SSL abuse labs



































