There are lots of malware analysis tools to record malware behaviors and such tools have the capabilities of filtering out certain events and apply analysis skills to judge whether the file is malware or not. Getting out a CSV format of such events is an excellent source to track all behaviors of malware on the infected machine. Procmon is one of the best tools for windows internals analysis. Procmon can be effective regardless if you are already an expert in malware analysis or a beginner. Analyzing the exported CSV with Microsoft excel may put your analysis a little boring, So here comes an awesome tool called Timeline Explorer. Written by ericzimmerman.
Tool Features
- An activity timeline view of events.
- Full-text search of specific events such as registry keys, servers, files, file path, Operation, Event Detail, PID, etc.
- Match Criteria search with logical conditions ( AND / OR /Mixed ) to get insights.
- Filtered Events Export.
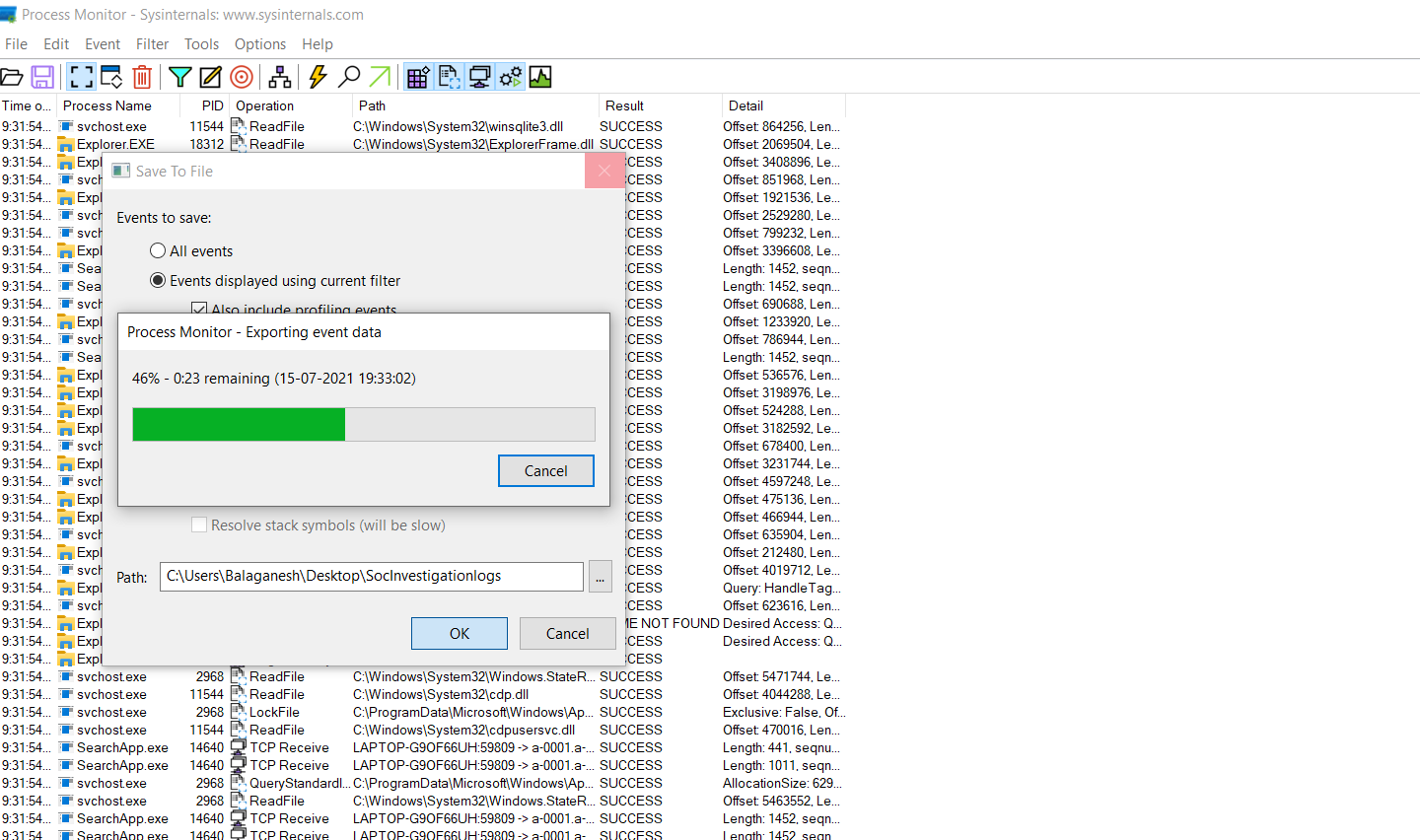
Collecting Events using Procmon
- Performing an dynamic malware analysis using promon and collecting the malware events in .csv format.
Also Read : Dynamic Malware Analysis – Procmon to Extract Indicators of Compromise
Getting Started with Timeline Explorer
- Download the file here.
- Export the zip and run the file as administrator.
- Import your CSV file in Timeline explorer.
- Imported CSV will be loaded in few seconds depends upon the file size.
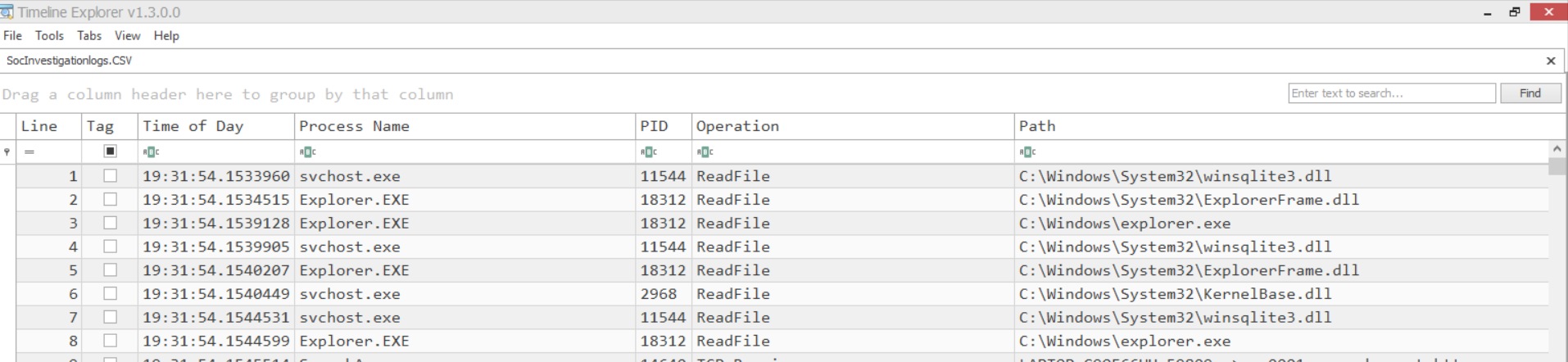
- Above Figure illustrates , Each events and its timeline was neatly shown with search bar to find the specific events.
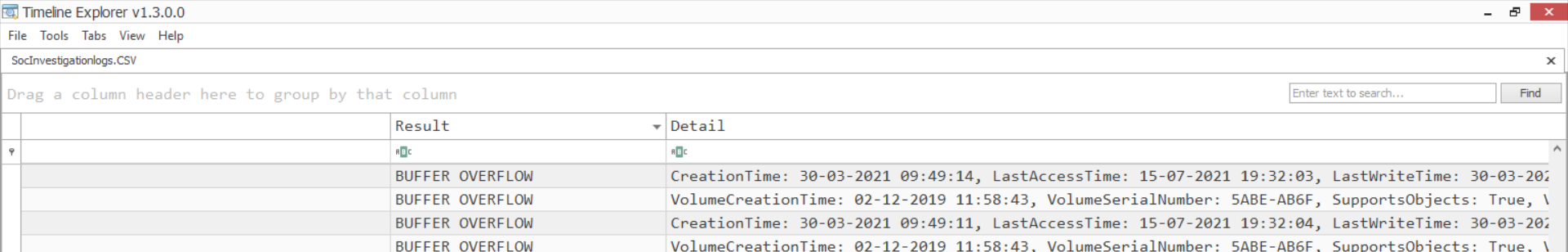
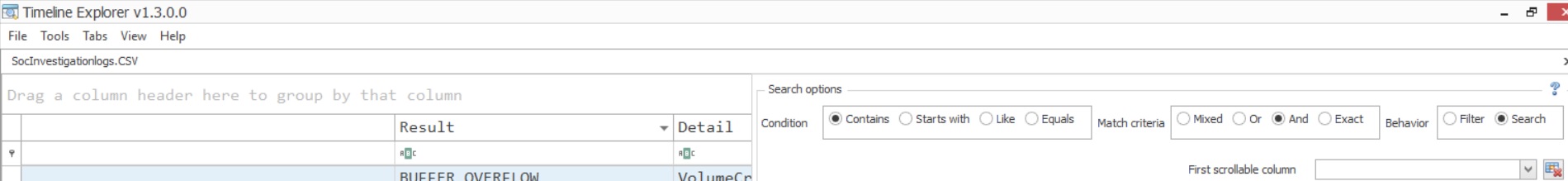
- Advanced search options filers enable analysts to quickly filter out and check infected file paths and malware persistence in the registry etc.
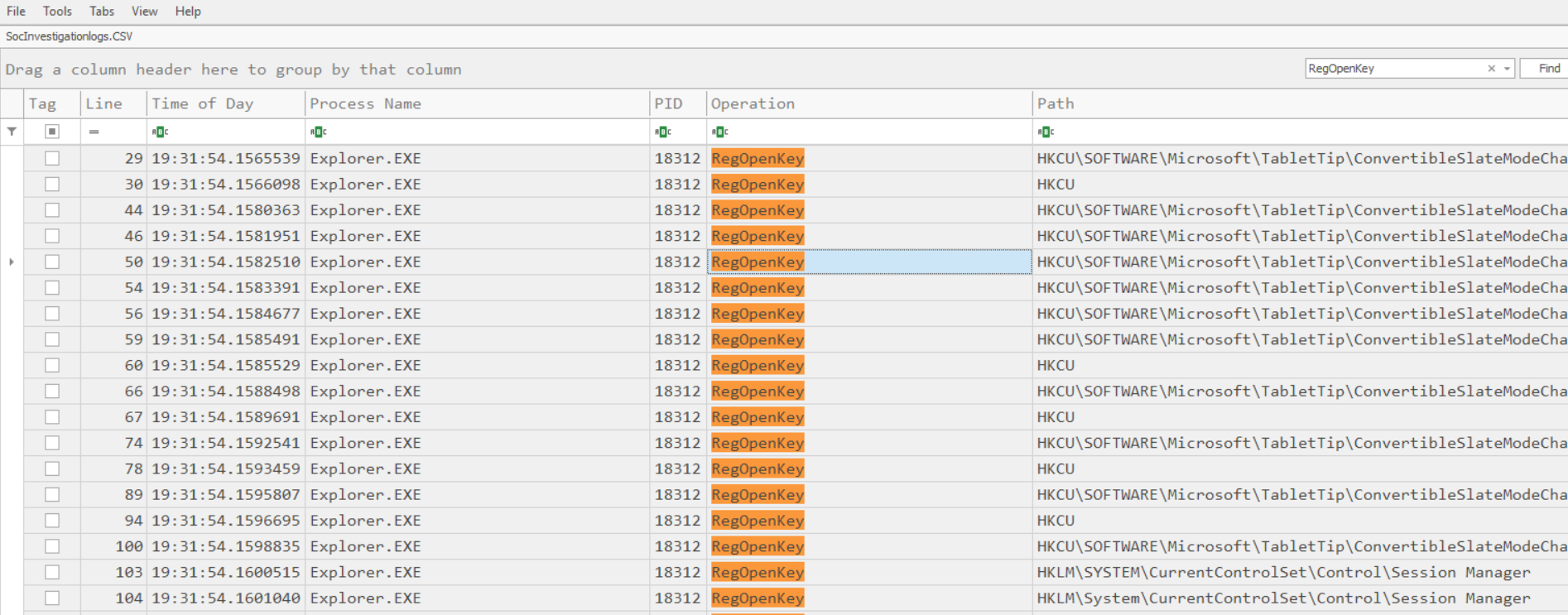
- Exporting a certain list of malware operation and on the file path.
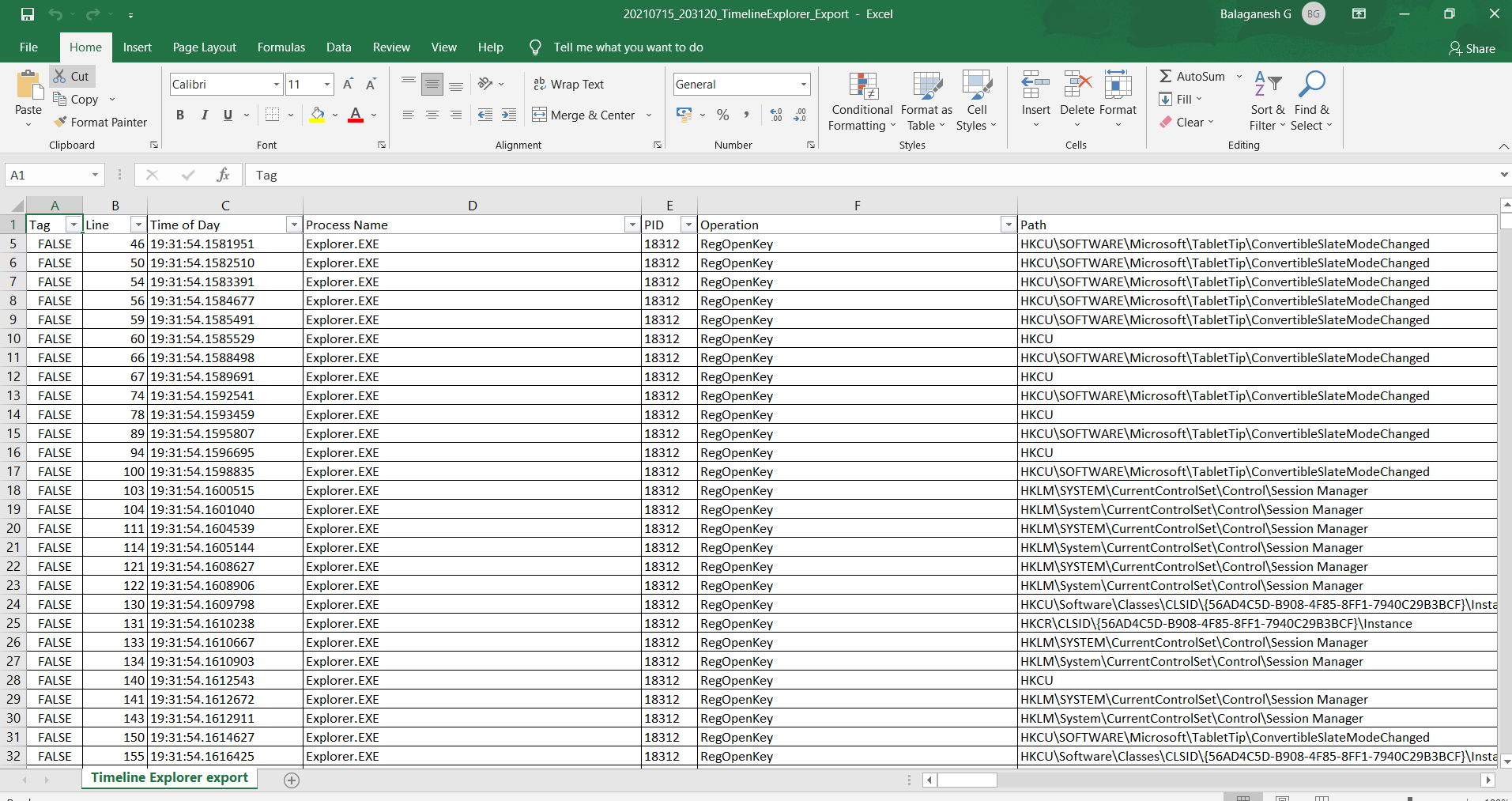
- Above Report shows the exported action of Regopenkey on registry hives.
Wrap Up
There are also lots of tools available for malware analysis and timeline views, although timeline explorer is a little tool. It does an excellent job to provide us a hassle-free view of each event on time of the day and helps incident responders and malware analyst to get a glance of the workflow of the malware and it changes on the system.



































