Privilege escalation involves gaining illicit access to elevated rights for a user or application. Adversaries use to gain higher-level permissions on a system or network in order to install and execute the malware on the target machine. The most common approaches are to take advantage of system weaknesses, misconfigurations, and vulnerabilities.
What is Windows UAC ?
User Account Control is a mandatory access control enforcement feature introduced with Microsoft’s Windows Vista and Windows Server 2008 operating systems, with a more relaxed version also present in Windows 7, Windows Server 2008 R2, Windows 8, Windows Server 2012, Windows 8.1, Windows Server 2012 R2, and Windows 10.
To understand how this attack works , Let us do a quick demo on it.
Privilege Escalation and UAC Bypass
There are plenty of system utilities in windows that can be used to bypass security controls and make sure to apply possible folder access policies and implement controls for a standard user who cannot access the system utilities to stop privilege escalation.
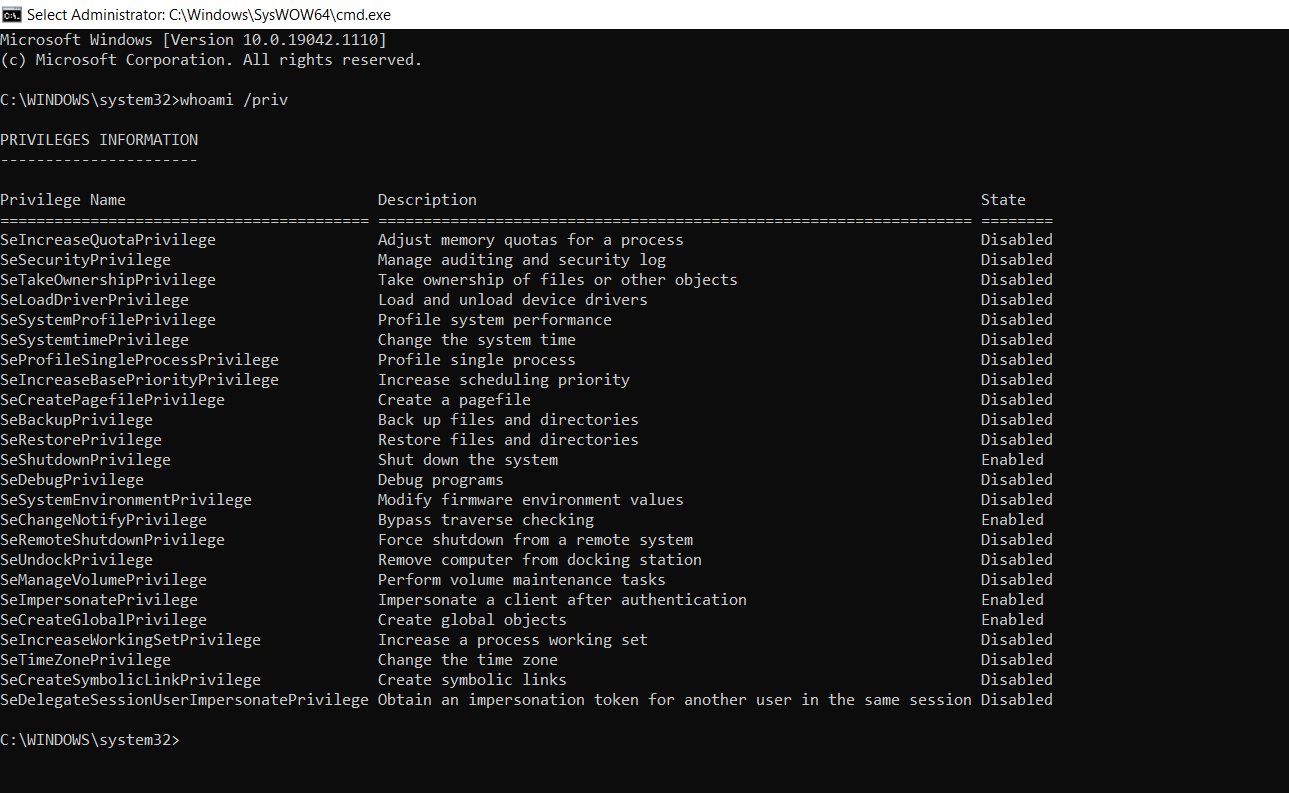
- Opening the cmd.exe and checking my current Privilege with whoami /priv. It will list down the privilege names and the state.
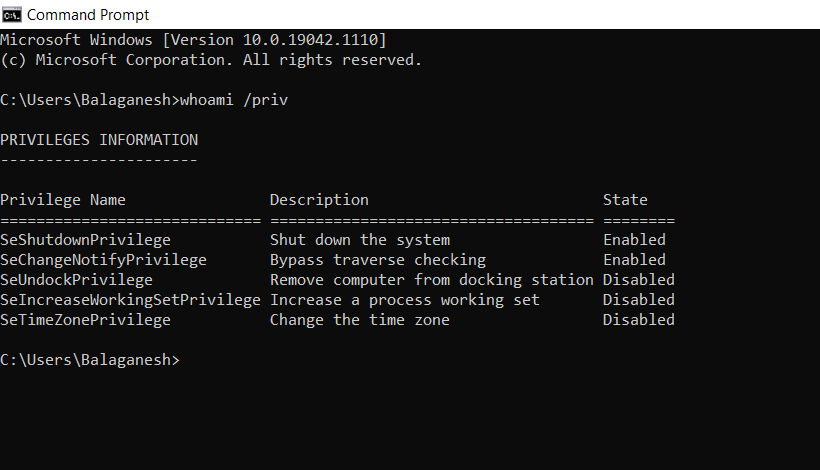
- Some of the privileges are by default enabled or disabled for the normal user in this machine.
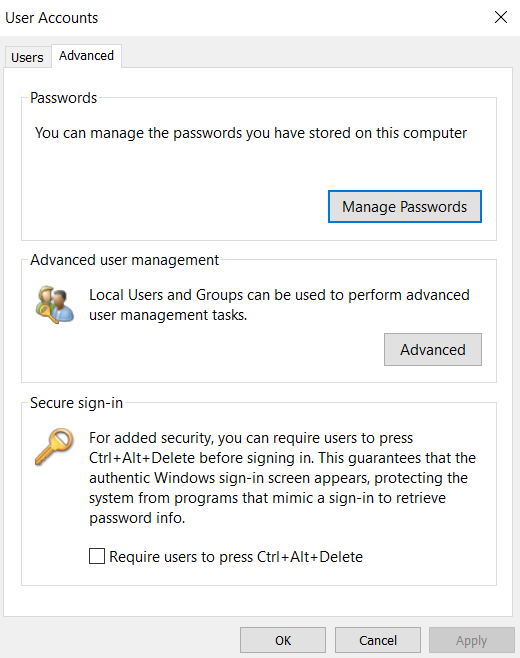
- Netplwiz.exe is a tool used to manage user accounts in most of the Windows operating systems such as Windows 10, 7, 8, 8.1, some other versions. It is located in C:\Windows\System32
- Let us try to use Netplwiz.exe to do privilege escalation, Netplwiz is a windows system utility that manages the user account.
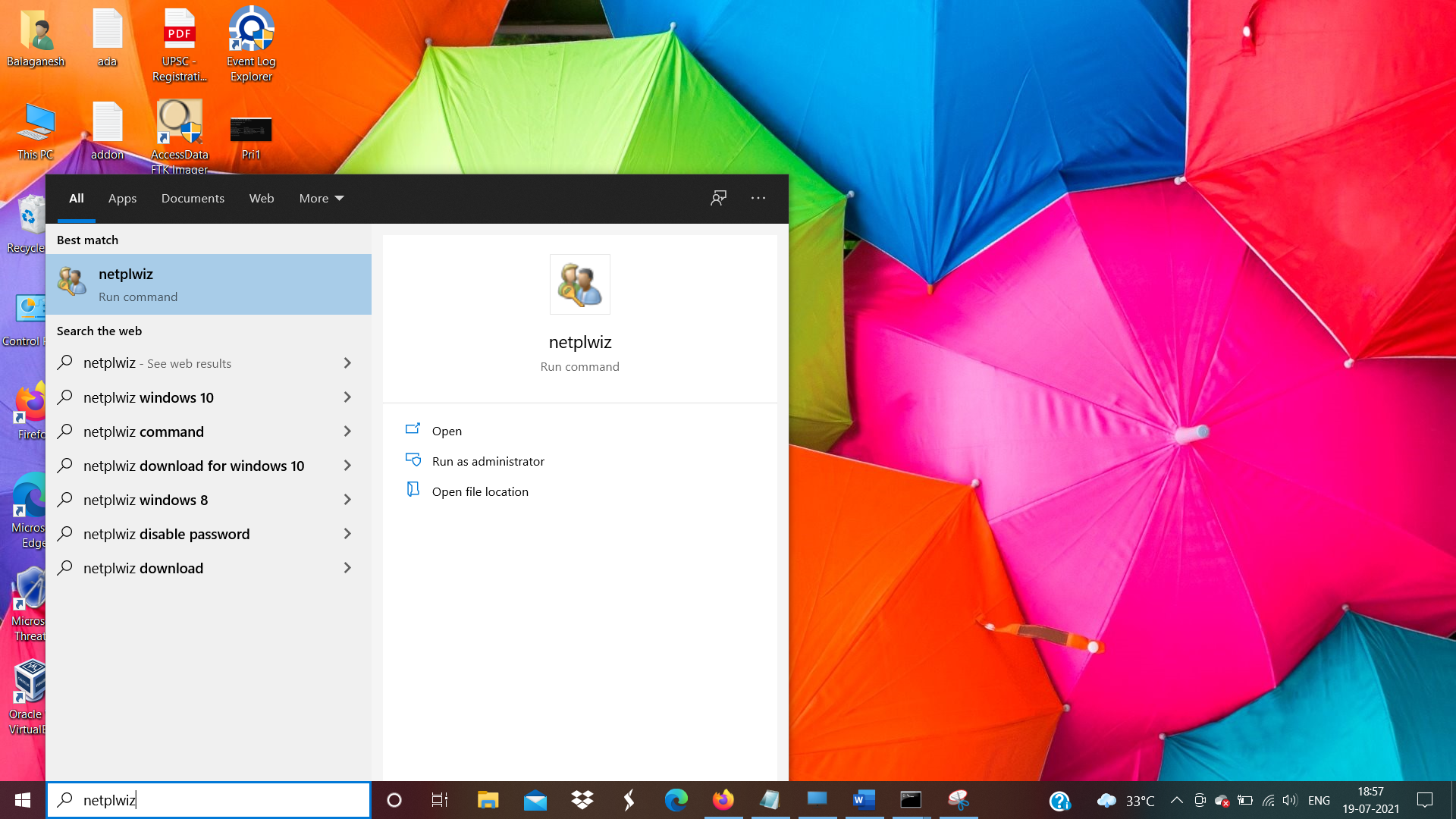
Note: Open netplwiz without admin privilege.
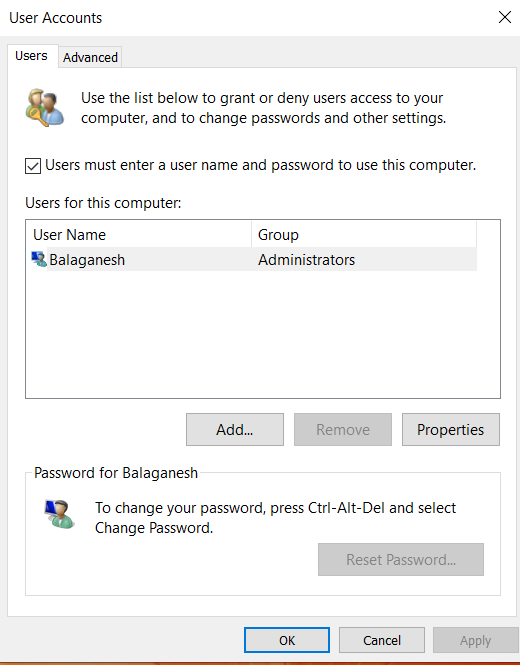
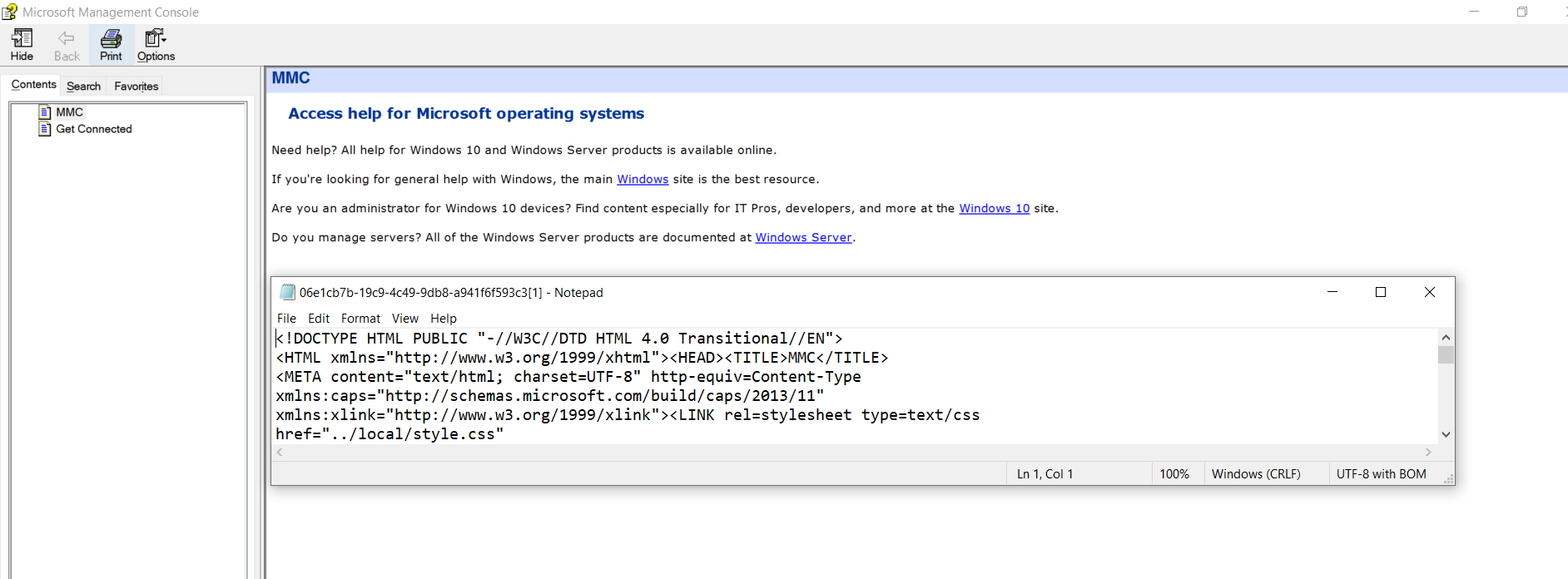
- Source codes opens up an original source code for help menu in notepad editor.
- Open the notepad option , File > Open
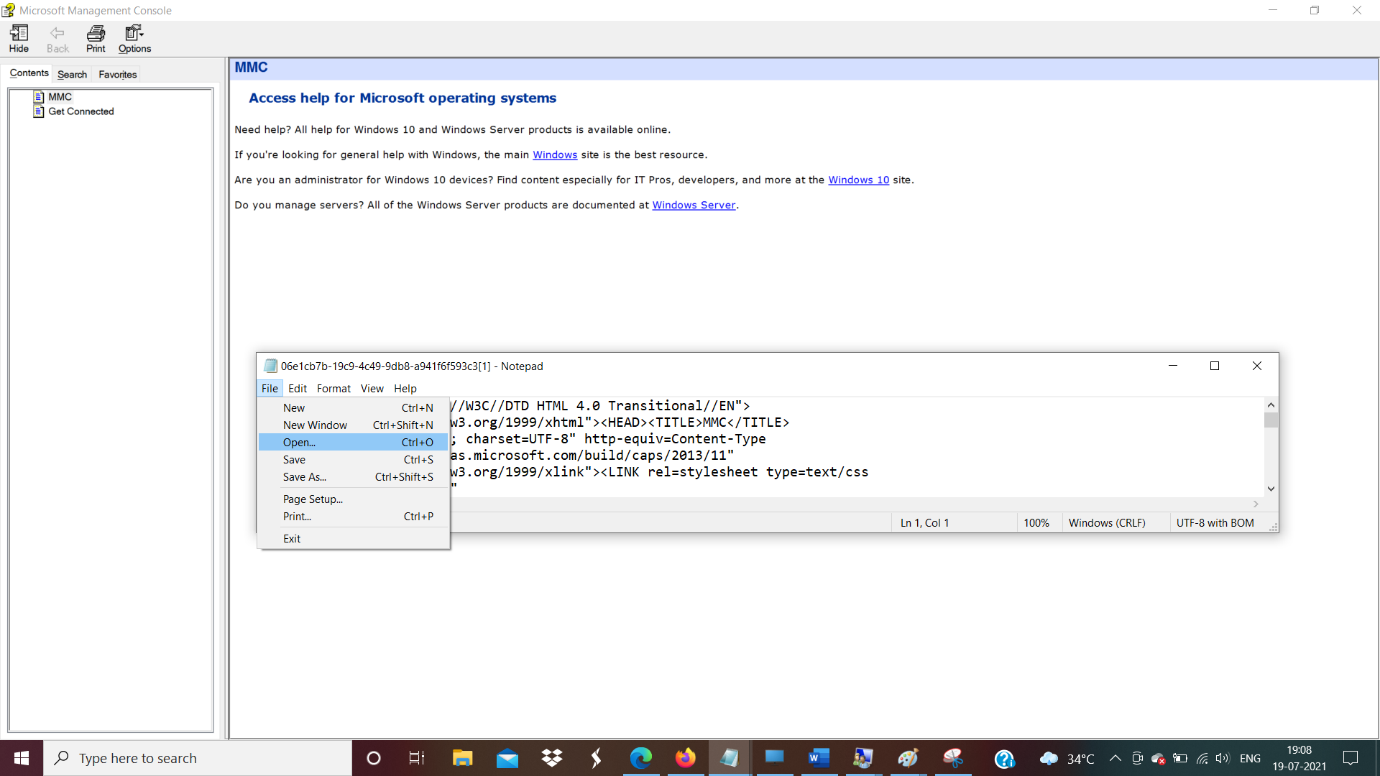
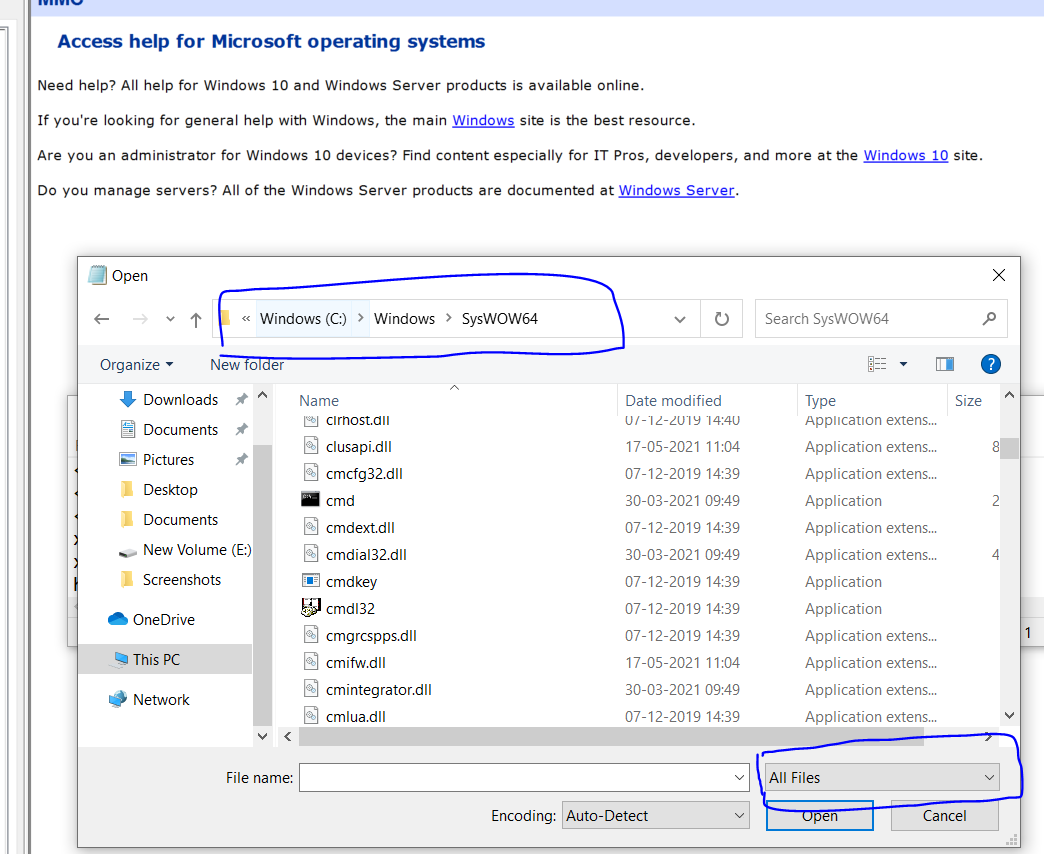
- Click the open and windows pops up , Select the file format as All files.
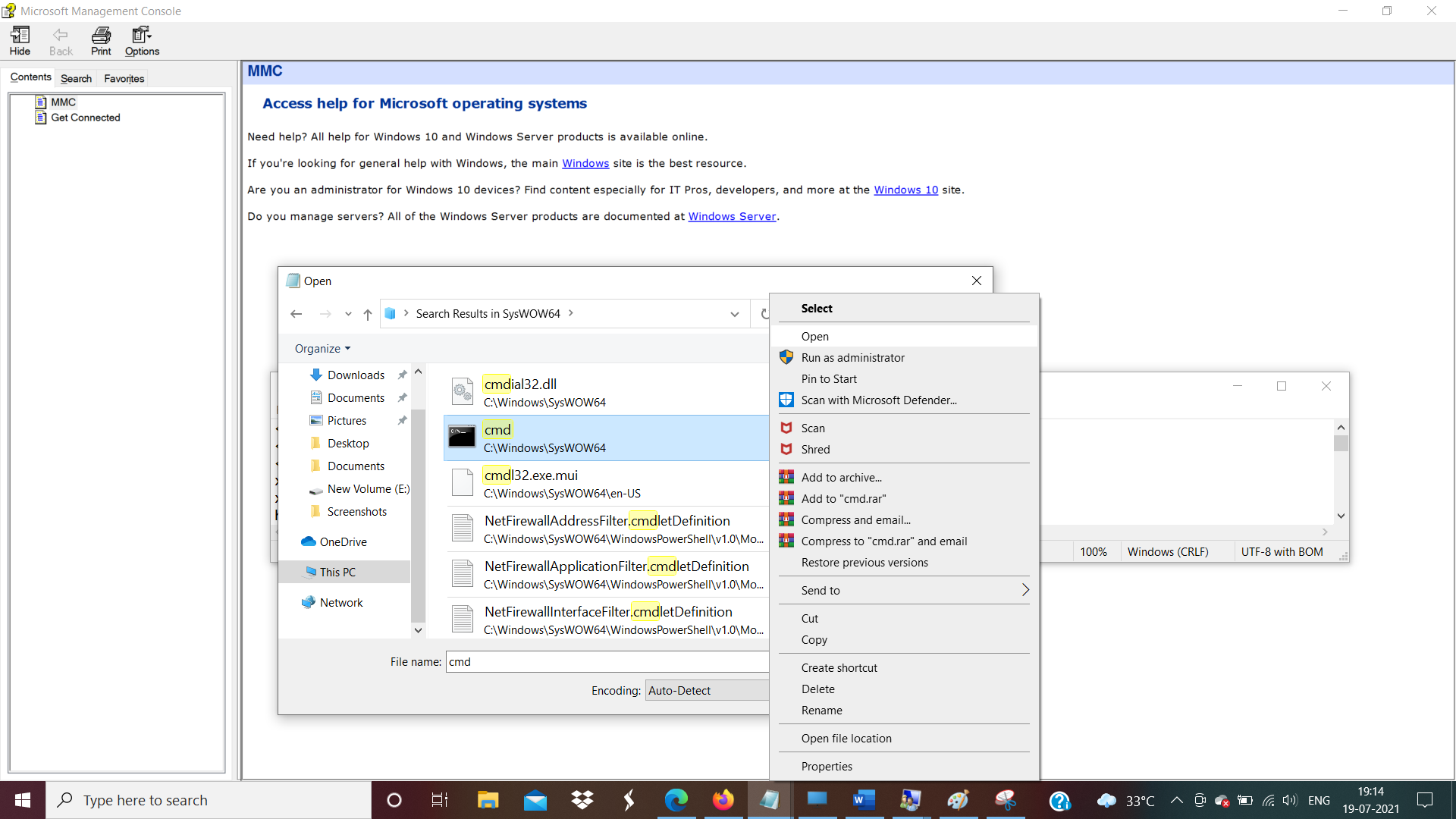
- Now we could see the cmd turns as administrator which shows we have a higher privilege.
- The above figure shows Normal user has gained higher-level permissions on a system to perform actions like installing malware and more.
- Most of the privileged state is disabled, this can be turned on as we have the privilege now.
- There are lots of similar system utilities which can be used by attackers to level up the privileges.
- Limit access to standard user for the system utilites which is not in use. Ensure windows hardening best practices in place.
Also Read: Threat Hunting using Sysmon – Advanced Log Analysis for Windows
Detection in Logs
- Hunt for event ID 4672: Special privileges assigned to new logon.
- Event ID Event ID 4624, Successful logon followed by Event ID 4672 special logon.
- Explore more uncommon processes and add it to your rule engine .file_path=\Windows\System32\sethc.exe OR Filesystem.file_path=\Windows\System32\utilman.exe OR Filesystem.file_path=\Windows\System32\osk.exe OR Filesystem.file_path=\Windows\System32\Magnify.exe OR Filesystem.file_path=\Windows\System32\Narrator.exe OR Filesystem.file_path=\Windows\System32\DisplaySwitch.exe OR Filesystem.file_path=*\Windows\System32\AtBroker.exe
- Hunt for timeline investigation where Event ID 4657 Windows registry changes with Events IDs 4624 & 4672.



































