FATT is a protocol fingerprinting tool for extracting network metadata and fingerprints for SSL/TLS, SSH, RDP, HTTP, gQUIC. It can be used as a live network sniffer mode to monitor to profile the list of protocols and anomaly detection. Captured PCAP files can also be imported to populate the fingerprints of the protocols. fatt works on Linux, macOS, and Windows.
It can be used for network forensics and malware analysis You can use other network analysis tools such as Bro/Zeek for more excellent use cases.
Getting Started
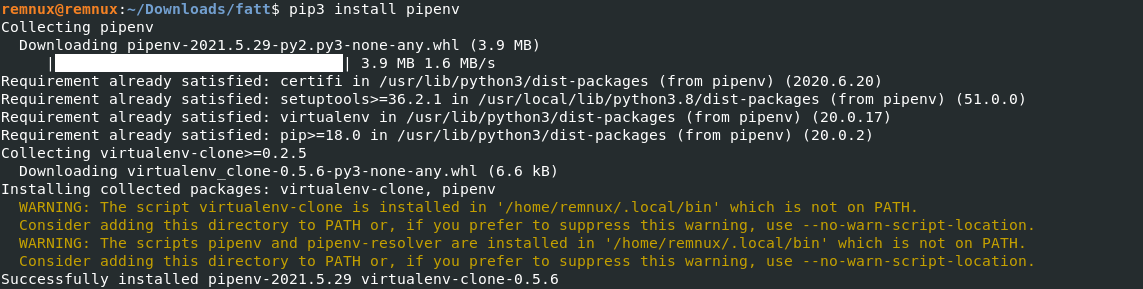
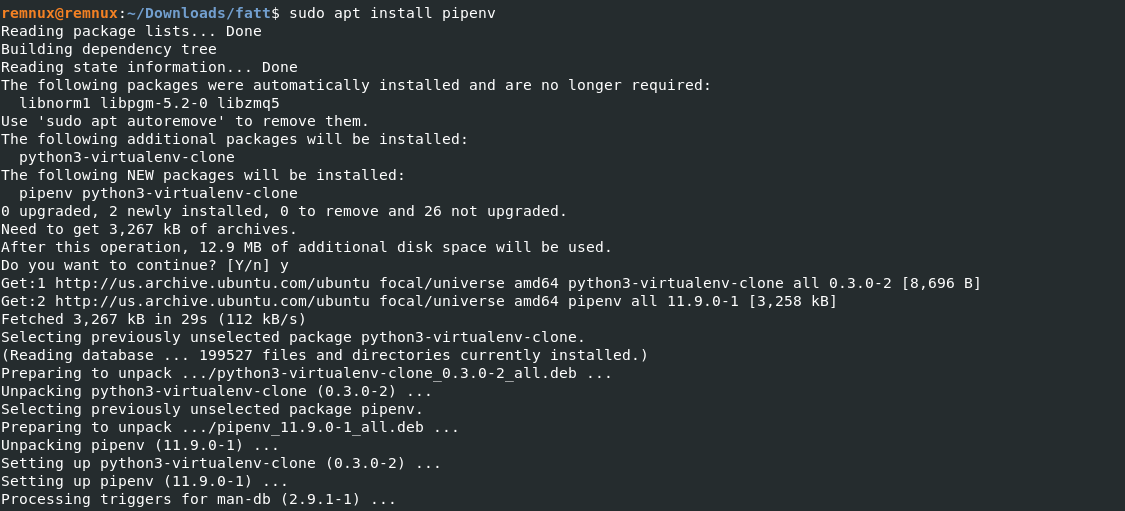
- Download the tool here & Install the dependencies
Network Monitor Mode & Hash Generation
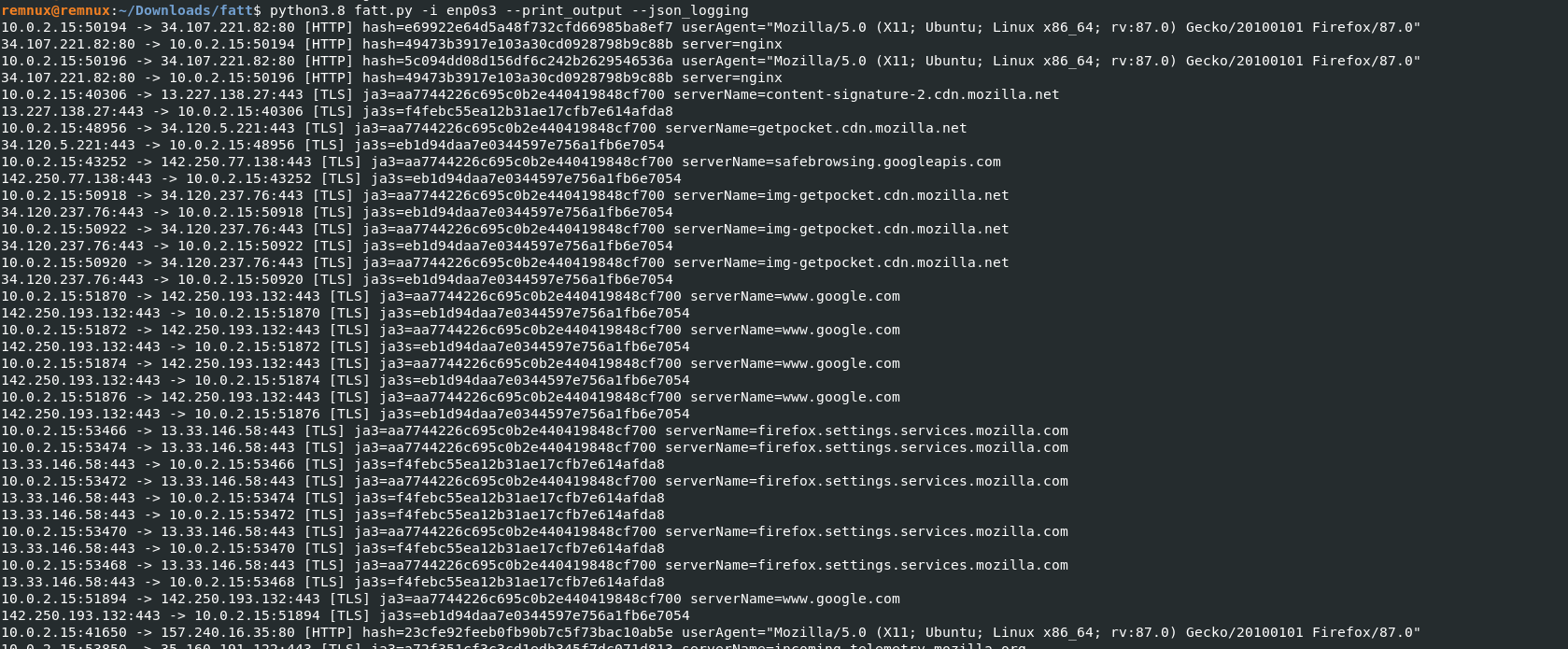
- Starting the monitor mode , python3.8 fatt.py -i enp0s3 --print_output --json_logging
- -i = Network interface –print_output = output file –json_logging = Logging method
- Above figure shows , Fatt started capturing the the supported protocol with the unique fingerprints.
Also Read: FireEye’s Open-Source Tool – CAPA to Identify Malware Capabilities
Hunting on HTTP Protocol
- Hunting for specfic hash on the logs , cat fatt.log | grep 5c094xxxxxxxxxxxx536a
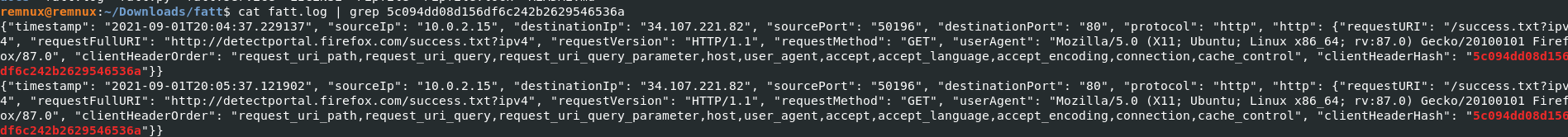
- Client machines connctions to the specfic url and IP address which has a unique HTTP hash. Multiple clients connects to the any domain or Ip address with specific HTTP hash on network, which be a good indicator of malware.
- Fingerprints methods are purley based on indicator of attack.
Example: Attackers have registered a new domain and this domain is not blacklisted by third-party intel feeds, Profiling method definitely helps analysts to find the anomaly based on the HTTP signatures/fingerprints.
Also Read : Soc Interview Questions and Answers – CYBER SECURITY ANALYST
- Similar hashes will be genrated for SSH & other supported protocols.
Analysing PCAP Files with FATT
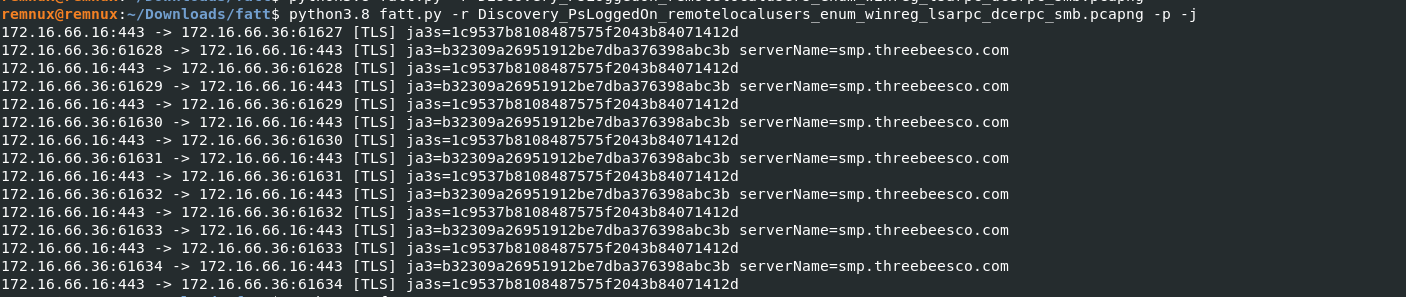
- FATT also supports importing existing PCAP files to fingerprint.
- Import your PCAP under fatt folder and start it, python3.8 fatt.py -r PCAPFILE -p -j
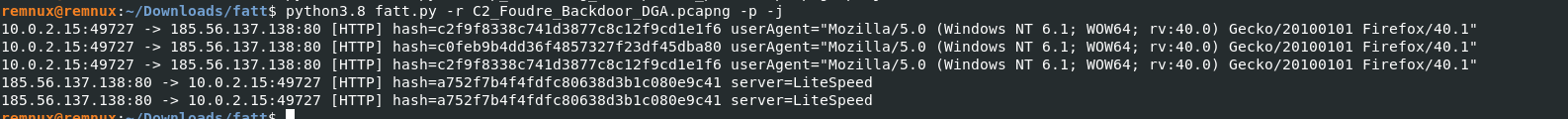
- The generated fingerprints are useful for grouping requests, or discovering unknown malicious requests omitted by other security systems but which share fingerprint. Implemeting tools like this or similar will enable faster incident reponse.
- Machine learning usecases can be developed for this hash fields to determine the likelihood of threat.
Also, Find Latest Cyber Security News – Hacker News!