Defending against malware is a real challenge for the computer security industry. Security analysts should detect the malware or threat before entering into the analysis. Only depending on automatic analysis tools for detection won’t help out more.
Sandboxes are one approach to get around the challenge. Sandboxes allow analysts to launch malware in a virtual environment and watch the execution process. This allows us to view exactly what the suspicious file does on an infected PC and collect the information that we need to further on it.
The issue is that many current virus families employ a different evasion method. They are aware that they are running on a virtual machine and behave differently than they would in a real one, allowing them to avoid detection. Now it’s time for ANY.RUN.
Malware Evasion Techniques:
Malware evasion techniques are thrown off by ANY.RUN’s interactivity. Since the service is interactive, malware can be tricked into operating as if it were running on a real machine. We can influence the simulation and interact with the virtual environment at any time as a user: drag a mouse, tap keys, and so on. We may also set up a virtual OS version and control a long list of simulation parameters.
Also Read: Malware Hiding Techniques in Windows Operating System
ANY.RUN: A Roadmap to Effective Malware Analysis:
ANY.RUN is an excellent malware detection online web service console. Let’s have a look at how it can be used to detect malware.
First Use case:
- Assume we’re looking at a suspicious file in ANY.RUN. Every piece of malware is unique and generates distinct signatures. Analyze the file interactively so that we will get more details regarding the file.
- Execute all the exe files and allow all the connections while interacting with the malware file.
- Sample File Details:
- File name: 02600004
- SHA256: CC185105946C202D9FD0EF18423B078CD8E064B1E2A87E93ED1B3D4F2CBDB65D
- Examining the network connections is an excellent place to start.
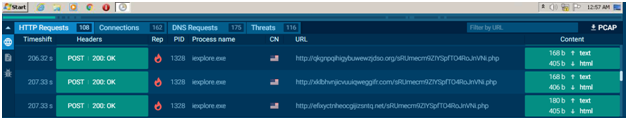
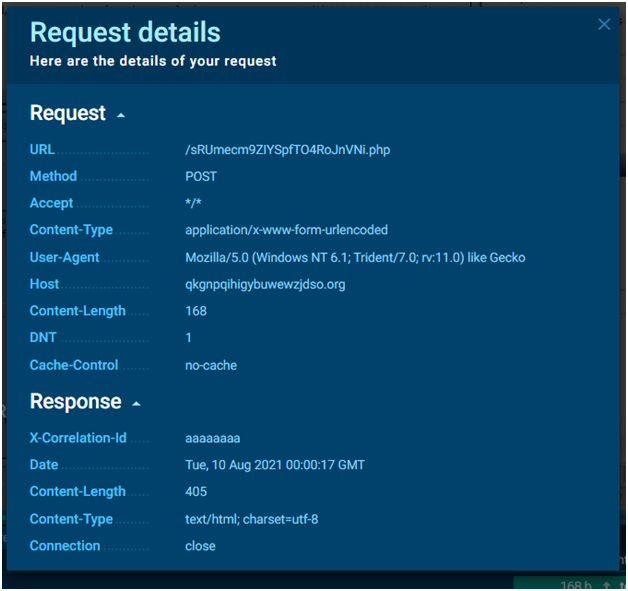
- The POST technique is used by some malware strains to communicate with the C&C. The malware strain name is rarely displayed in the user agent of the POST method. Simply click POST/GET to bring up a pop-up box with further information about the request.
- There is more POST request in the Network tab. While randomly checking 4 to 5 requests, found all the domains to be DGA domain. It’s sure enough to confirm that it is a DGA attack. Sometimes the “Useragent” will say more about the malware family/can provide keyword of the threat.
Also Read: NetworkMiner Tool – Dynamic Malware Analysis with Minimum Dwell Time
Second Use case:
However, network requests will not always succeed. Let’s take a look at another scenario.
Sample File Details:
Filename: JVC_41642.vbs
Full analysis: https://app.any.run/tasks/32dc2282-863a-4174-bb0b-8ec0c34213bf
SHA256: 95C6C6152C3E08B3D342B896C6CD5A9385E721C9C31B19C6FDBA56F7DCBE5BAC
- In the above sample file, there is no network request to identify the malware. No need to worry about it. They is always a way to find it.
- We can go with “Files tab” to check the location and the files created/associated in the local folder with the malicious behavior.
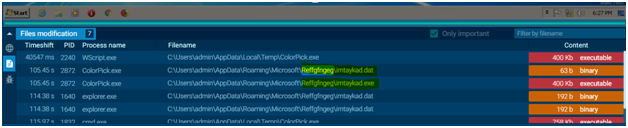
- Here we can see one DAT file and an executable is stored in the local AppData folder. While checking the keyword “imtaykad” in open source, found that it is related to Qbot files which is created in local folder while it got executed.
Third Use case:
Occasionally, we will receive a Verdict of Malicious/Suspicious Activity, but the system will not provide any tags to indicate which malware families they belong to. You’ll need to use reverse engineering to figure this out. However, it takes a long time and requires a lot of resources. ANY.RUN features a nice filter option that speeds up and simplifies this operation. Here we can go with another example:
Sample File Details:
Filename: bmd7i29.JS
Full analysis: https://app.any.run/tasks/ba44468c-a9ba-4a59-8305-1ef465c945b9
SHA256: 2C7FA3A8BCC108185DA9F9CB9C4218578FA30CF03CA9A8FEA3379CB89374FB77
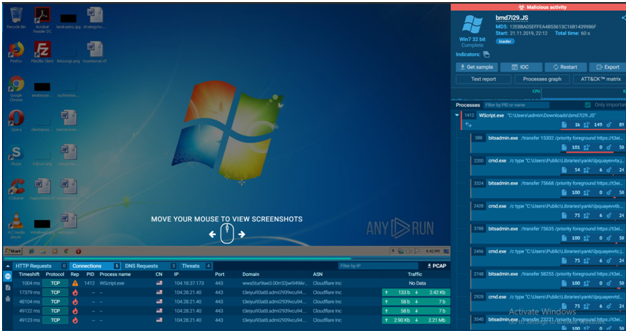
- In the above example, we don’t have HTTP requests and very less DNS and IP connections. And in “Files Tab” also there is no significant folder/file name. Although suspicious behavior has been noticed, the malware family has yet to be identified because the payload has yet to be downloaded. One of the possible causes is that the Command & Control server is now unavailable.
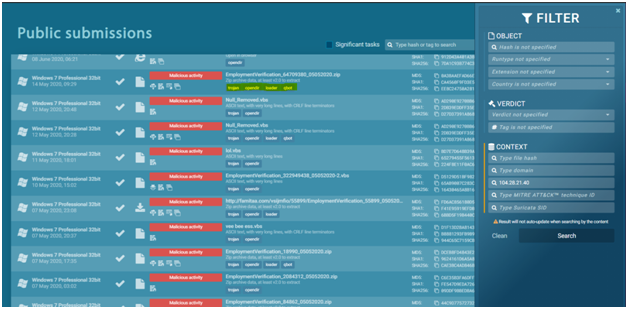
- We no longer need to manually analyse all of the IPs, domains, files, and processes in open search in this circumstance. Simply copy and paste the IP/domain into the Public Submissions tab’s search filter. The tasks associated with the IP address are now visible. Qbot malware is a malware that performs a similar operation. This feature will save you time and money, as well as the resources of the malware analyst.
Conclusion:
ANY.RUN can assist researchers in swiftly obtaining results when evaluating suspicious files, and it will function when completely automatic sandboxes fail. Malware analysts must be familiar with a variety of programming languages, as well as the internal workings of Windows, and what qualifies a user as a power user is knowledge of a variety of online malware analysis tools that can be used to study malicious code in malware.



































