Tor network is the least-worst option for protecting your privacy in a web browsing context, in its highest security mode.
In the olden days, spy agencies use the dark web to silently share their details. Although the dark web is known for being a hazardous site where narcotics are sold and mobsters are hired, it can also be a secure way to browse the internet if your privacy is a major issue. It’s simple to use the Tor Browser.
Even the most famous websites and web applications are hosted in via “onions” on the dark web. so that they can be accessed via the TOR browser. CIA has officially announced that the onion site is one of several ways individuals can contact them.
The Onion Router, also known as Tor, is a network that allows users to remain anonymous online and avoid being tracked. With a customized Mozilla Firefox ESR web browser, you can connect to the Tor network. Tor hides the user’s true identity, allowing them to browse the internet anonymously. It shields the user from network eavesdropping and traffic analysis.
The Invention of TOR:
- Tor employs the ‘Onion Routing’ idea, which was created in the 1990s by Paul Syverson, Michael G. Reed, and David Goldschlag at the United States Naval Research Laboratory.
- The Electronic Frontier Foundation (EFF) provided financial support for further development.
- Tor Project Inc. is a non-profit corporation that is in charge of maintaining and developing Tor. It has mostly received funding from the US government, with additional support from the Swedish government, NGOs, and individual donors.
What is TOR?
The Onion Router (TOR) is a network that routes your traffic through random nodes, encrypting it each time to make it impossible to track and it’s maintained and accessed using the Tor browser. Although this may appear to be an extreme method of surfing the web, such protections are becoming increasingly important.
Tor is probably the most popular and secure anonymous internet connectivity option. Here we’re going to discuss the Tor network, which is used to access the TOR browser.
TOR Architecture:
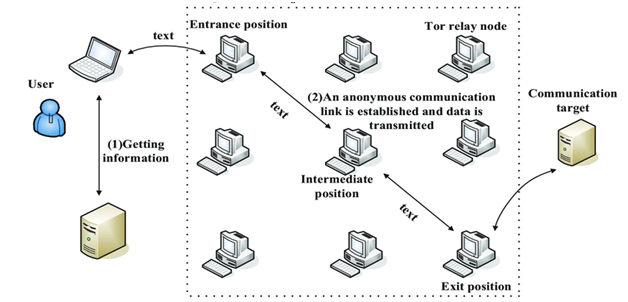
- Tor employs the ‘Onion Routing’ approach, in which user data is encrypted before being routed across the Tor network’s various relays/nodes.
- Hence, it provides multi-layered encryption (layers like an onion) and a tough path to protect the user’s identity. As a outcome, nobody can link your identity to any single point.
- One encryption layer is decrypted at each successive Tor relay, and the remaining data is forwarded to any random relay until it reaches its destination server. For the destination server, the last Tor node/exit relay appears as the origin of the data. It is thus tough to trace the identity of the user or the server by any surveillance system acting as the middleman.
- TOR hidden services will also provide anonymity to individual users, websites and servers.
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
TOR Directory nodes:
- When you want to connect with the Tor network you need to have some IP addresses from nodes that can accept your connection. This information is provided by the Tor Directory Nodes.
- The state of the Tor network is tracked and publicized by a group of 9 trusted servers, each of which is controlled by a different person or organization.
- It have 9 distinct nodes which provides stability if any one node goes down or one of them is hacked.
- If a TOR client or node needs to know the current state of the network, it asks to directory node.
- The latest network news is kept up to date by sending each directory node a notification whenever they come online or change their settings.
- When a directory node receives one of these notifications, it adjusts its personal opinion of the Tor network’s current state.
Tor circuit:
- The Tor daemon on your machine must select the three nodes it wants in its circuit, ask about their availability, and then negotiate a symmetric encryption key with each of them.
- Once your Tor browser has created a circuit, it will use it for all of your traffic for the following 10 minutes before creating a new one.
- All new TCP streams are routed through this new circuit, while existing TCP streams are routed through the old circuit.
- The Tor daemon selects the three nodes that will make up its circuit based on available nodes collected from directory nodes. So, the Tor daemon will require access to an up-to-date list of all Tor nodes and their capabilities.
Before entering into the concept of how TOR circuit formation is done, let’s explain the names of the 3 nodes.
TOR nodes:
The network becomes more secure and speedier as the number of nodes increases. When a user selects their path through the Tor network, they select a minimum of three nodes. There are three special types of Tor nodes in any connection:
- Entry nodes or guard node
- Middle node
- Exit node
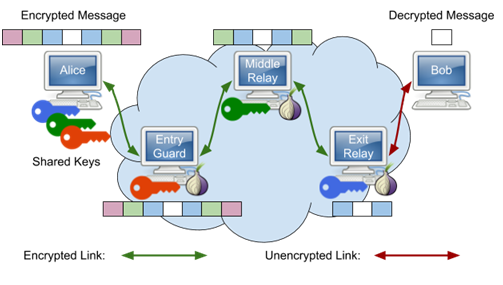
Entry nodes or guard node:
The first node is the node where their traffic enters the Tor network, and it’s known as the entry node. Any node on the Tor network can serve as the entry node. There’s really no difference between serving as the entry node or another node in the middle of the connection. There is one important difference from the client’s perspective. Because of perfect forward secrecy, the entry node knows only the identity of the user/client and the next node in the circuit. The entry node does not know the final destination of the traffic, so the only conclusion it can reach about the user is that the user is communicating with the Tor network.
Middle node:
The relay nodes’ sole purpose is to unwrap more layers of perfect forward secrecy. You’ll have one node in the middle of your Tor circuit by default, but you can increase it if you like. Just keep in mind that each node you add to your Tor circuit lengthens the time it takes for your communications to reach its destination.
Exit node:
The exit node is the node that communicates with the target system. Nodes must volunteer to serve as exit nodes, for an important reason. The target system sees the exit node as the source of the traffic headed to it. For this reason, the operators of exit nodes are frequently accused of causing whatever activity Tor users engage in using the network. This results in many inquire from law enforcement and leave exit node operators explaining how Tor works to investigators over and over again. The operators of Tor nodes perform a public service that helps keep the network running smoothly. Tor would not function without these nodes.
Also Read: Threat Hunting using Firewall Logs – Soc Incident Response Procedure
TOR circuit formation:
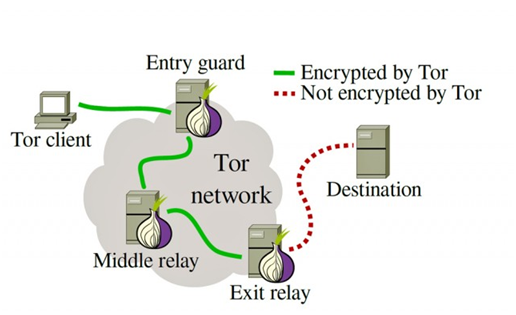
- TOR circuit is formed with above three nodes: Entry node, Middle node, and Exit node.
- The client initiates the circuit formation process by contacting the entry node it has picked. Every node will have a symmetric encryption key associated to it.
- The client and entry node establish a TLS session, and the client requests assistance from the entry node in establishing a Tor circuit.
- The information just passes to the middle node where this is the one who doesn’t know from which client the information is getting passed and the final destination.
- This implies the client can never communicate directly with the middle node, even to negotiate a TLS session, because doing so would expose the client’s IP address to the middle. Hence, the client communicates with the middle node through the entry node.
- The client and the middle node negotiate a new TLS session of their own by transmitting traffic to each other through the entry node, without ever forming a direct connection.
- The client and the middle node have agreed on a secret symmetric encryption key, and the client’s Tor circuit has been extended by one node once they’ve completed.
- The client then completes a second and final circuit extension, this time to the exit node. This process is identical to extending the circuit to the middle node, except this time the TLS session negotiation between client and exit node happens via both the guard and middle nodes.
- The client has negotiated a separate, symmetric TLS key with each node in its circuit once the circuit’s final hop has been established.
Using the triply-encrypted method described above, the circuit is ready to send and receive data.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
TOR Network applications:
Few programs use the TOR network to provide anonymous solutions. Those are mentioned below:
Tor Browser:
The Tor Browser developed by the Tor project officially is the most popular client. The application is based on Mozilla Firefox’s stable ESR version, with add-ons from NoScript and HTTPS Everywhere together with Tor-specific control and installation components. For Windows, macOS, Linux, and Android, this client is available.
Tails:
The live operating system Tails, designed for IT security, data protection, and anonymity, conducts all Internet traffic through the Tor network by default. In addition, the Tor Browser is a standard package pre-installed in Tails.
OnionShare:
OnionShare is a service enabling anonymous and safe data exchange using the Tor network. This software can be used in the operating systems: Windows, macOS, and Linux.
Onion Browser:
Onion Browser is a mobile browser for Apple iOS and is also designed as open source. In contrast to the Tor Browser, this software uses WebKit rather than Mozilla’s Gecko engine due to the platform.
Disadvantages of TOR Network:
- The Tor network is a powerful tool for masking internet activity. However, Tor is not free of vulnerabilities and errors. There is always a risk that attackers will control and monitor a variety of nodes. If a route’s entry point and exit node are under the control of a single player, it is possible to determine the user’s identity.
- There can never be completely eradicated vulnerabilities in the Tor Browser itself as well as in the executed NoScript and HTTPS Everywhere plugins. Security researchers have successfully smuggled malicious malware through flaws in extensions into the Tor Browser in the past.
- In addition, anonymity may be guaranteed in the Tor network only if you do not leave traces of your identity in the form of the cookies, additional add-ons or the usage of the BitTorrent service.
Advantages of TOR Network:
- Protection against anti-spies: Tor prevents others from tracking the websites you visit.
- Identity anonymous: Tor tries to make all users look-alike to stop anyone identifying you from the characteristics of your browser or devices.
- Encryption with multiple layers: Your traffic in the Tor network is redirected and encrypted multiple times to keep you anonymous.
- Free access: The Tor browser allows you access to websites blocked by your network.
- Hides your online activity. Your browsing history and cookies are automatically reset when you stop using it.
Is the TOR network is really secured?
Tor is often used by individuals who are aware of privacy and who want to avoid surveillance, but it is not perfect. Simple errors can render hours of cautious privacy protection unnecessary, so it’s worth taking special precautions when browsing with Tor. Here are a few things that you really should look for:
Tor has vulnerabilities that can be exploited:
As with regular web browsing, a security bug can always compromise your web browser. Although contemporary browsers, such as the Tor Browser based in Firefox, offer excellent exploit protection, the kinds of adversaries that aim for Tor users will also exploit browser stockpiles that browser providers do not know fully about (“zero-day” bugs).
The timing-based statistical techniques may de-anonymize your traffic:
Another concern for security is when the entry and exit relays both exist on the same autonomous Internet system as if both IP addresses are owned by the same network operator. If so, this network operator is able to use timing statistical techniques to determine the origin of a specific network request from a specific computer. This technique is hard to implement, so only governments can usually pull it down. It can also be expensive, so usually it is not an issue, apart from high-value targets.
Tor will not protect you from sophisticated methods of fingerprinting:
Fingerprint users can also use other signals. If you’re browsing an endangered website with JavaScript-enabled Tor (or the website you’re browsing uses endangered third-party JavaScript), you can find who your mouse moves are based. Most people are moving their mouse distinctly so that a Tor browsing session can be correlated with a regular non-Tor browsing session.
Unencrypted is the final part of the communication:
Although Tor encrypts data in the Tor network and within the Tor network between the user’s computer and the server, it does not encrypt the final connection part between the exit node and the server. In consequence, traffic between the exit node and destination servers can be eavesdropped on by any government or internet provider. Because the complete list of Tor exit nodes is available to the public, unencrypted traffic from the exit nodes can be monitored closely.
Also Read: Latest Cyber Security News – Hacker News !
How to effectively use TOR:
- Just use extension HTTPS Everywhere. This ensures that only HTTPS websites are browsed and that your personal information is protected between the exit node and the target server.
- Flip the security level of the Tor Browser to maximum. This disables Javascript on every website, deactivates many types of fonts and images and clicks on media like video and audio. This level of security decreases significantly how much browser code you execute when you view a web page to protect you against various bugs and fingerprinting methods.
- Never use BitTorrent over Tor as a general rule. Although people who pirating illegal copyrighted content may want their actual identity to be obscured, BitTorrent is extremely difficult to use in such a way that your real IP address is not disclosed. Tor is rather slow, so it’s hard to use BitTorrent.
- Keep Tor Browser ( and any extensions) always updated to reduce the surface of your attack.
- Really do not connect to your usual accounts – Facebook and Google in particular.
- Try to just not follow single browsing patterns that can identify you personally.
Conclusion:
Tor is frequently promoted as a way to surf the internet anonymously. Tor is a popular means to achieve substantially more anonymity than you would typically have online, from human rights activists evading oppressive governments to drug dealers selling through online markets. Tor, on the other hand, isn’t perfect, and if used wrongly, it might give the impression of security.
Stay tuned for the article to identify TOR activities & default rules..



































