Introduction to Suspicious Windows Service Creation
Windows services created/modified to execute malicious payloads in your system? Don’t you know how the adversaries entered into the organization? Haven’t any idea from where the detection occurs? No worries! This article will let you know about the most important technique’s WINDOWS SERVICE CREATION(T1543.003) actual behavior, the way of adversaries take over the system, and after the attack is simulated, where do we go and check for detection. By knowing these three we can hunt pro-actively.
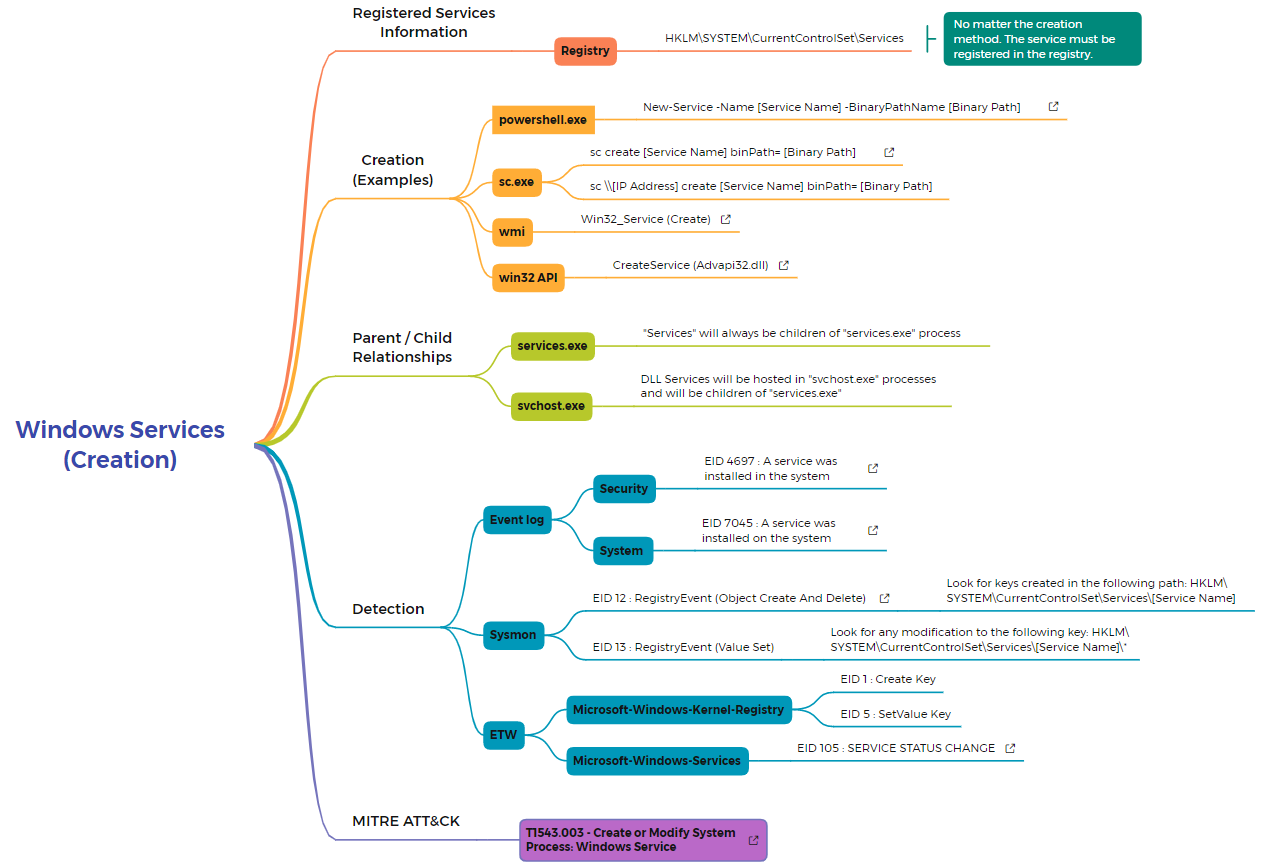
Windows service creation is the technique of creating or modifying the windows services to continuously execute malicious payload to the system. This technique occurs as a part of persistence. Every time when windows boots up it starts services that run background system function and this information is stored in the registry including the file path.
An adversary may attempt to manipulate features of creating services to make them appear legitimate and to make the detection analysis more challenging.
Also Read: Malware Analysis Use Cases with ANY.RUN Sandbox
How are Adversaries Creating Services?
Creating/Modifying services are not the big deal for attackers. The most commonly used three ways are explained below with the respective commands.
1.Powershell:
Adversaries can use PowerShell as a tool to perform a number of actions including the discovery of information and execution of code. PowerShell may also be used to download and run executables from the Internet, which can be executed from disk or in memory without touching disk.
Cmd for creating services:
New-service-New[service Name] –BinaryPathName [Binary Path]
2.WMI(Windows management instrumentation)
An adversary can use WMI to interact with local and remote systems and use it as a means to perform many tactic functions, such as gathering information for Discovery and remote Execution of files as part of Lateral Movement.
Win32_service(create)
3.SC.exe(Service control)
In Generic,sc.exe is responsible for managing windows services. Here, an adversary can use this sc.exe as a tool to create or modify the windows services to execute malware. It allows administrative users to establish a program as a Windows service in the Service Control Manager (SCM) database and the Registry, either locally or remotely.
SC create [service name]binPath=[Binary path]
SC \\ [IP Address] create [service Name]binpath=[Binary path]
If the Task Manager shows “sc.exe” running continuously, it may be malware.
4.Win32Api
The Win32 API is the native platform for Windows apps. This API is best for desktop apps that require direct access to system features and hardware. Same as others, it is also used to create the process by the adversary.
Win32_service(Advapi32.dll)
Where the Detection Occurs?
Services are created by the attacker to execute malicious code. How we will come to know? Here is the answer! By checking event logs and Look for changes in the registry.
Also Read: Latest Cyber Security News – Hacker News !
1.Event log:
If the new service is created in the system, Event id 4697 and/or 7045 will be generated. So by looking at these events IDs, we came to know that something cause suspicious in the services.
Event ID:4697(System log)- This event generates when a new service was installed in the system. We recommend monitoring for this event, especially on high-value assets or computers, because a new service installation should be planned and expected. Unexpected service installation should trigger an alert.
Event id:7045- A new service was installed by the user indicated in the subject. The subject often identifies the local system (SYSTEM) for services installed as part of native Windows components and therefore you can’t determine who actually initiated the installation.
2.Sysmon:
In Symon, Look for changes to service Registry entries (Event id 12 and 13)that do not correlate with known software, patch cycles, etc. Service information is stored in the Registry at HKLM\SYSTEM\CurrentControlSet\Services. Changes to the binary path and the service startup type changed from manual or disabled to automatic, if it does not typically do so, maybe suspicious.
Sysmon Event id:12- Registry key and value create and delete operations map to this event type, which can be useful for monitoring for changes to Registry autostart locations or specific malware registry modifications.
Looking for keys created in the following path:
HKLM\SYSTEM\CurrentControlSet\Services\Service name
Sysmon Event id:13- This Registry event type identifies Registry value modifications.
Looking for any modification to the following key:
HKLM\SYSTEM\CurrentControlSet\Services\Service name\*
3.ETW(Event Tracing for Windows):
Event Tracing for Windows (ETW) is the mechanism Windows uses to trace and log system events. It looks something like Symon and other similar security monitoring-oriented tools. It is an efficient kernel-level tracing facility that lets you log kernel or application-defined events to a log file.
Here, Look into Mirosoft-windows-Kernel-Registry and Microsoft-windows-services.
In Mirosoft-windows-Kernel-Registry, Event id 1 and 5 will be generated if anyone creates or set the value to the key in the registry.
In Microsoft-windows service, Event id 105, will be generated if the status of the service changed.
Also Read : Latest Ransomware CVEs – Vulnerabilities Abused by Ransomware Actors
Conclusion:
The defenders are being able to detect /stop every attack before / when it happens and to know exactly. No matter the techniques or tools. We have come a long way in being able to detect and understand some attacks.
Happy Hunting!



































