Hunting threats with EventID is rather frequent these days. However, the event ids with which we create rules are quite crucial. Some Event IDs are quite crucial because when an attacker hooks the machine, changes are almost always made. Unique event ids can be used to track all changes. Now we’ll look at how the defense team uses the Event ID 5145 to keep their organization safe.
Event ID 5145:
“5145: A network share object was checked to see whether the client can be granted desired access”
Event Description:
This event generates every time the network share object (file or folder) was accessed. Failure events are generated only when access is denied at the file share level. No events are generated if access was denied on the file system (NTFS) level.
File access codes:
| Access | Hex Value, Schema Value | Description |
|---|---|---|
| ReadData (or ListDirectory) | 0x1, %%4416 | ReadData – For a file object, the right to read the corresponding file data. For a directory object, the right to read the corresponding directory data. ListDirectory – For a directory, the right to list the contents of the directory. |
| WriteData (or AddFile) | 0x2, %%4417 | WriteData – For a file object, the right to write data to the file. For a directory object, the right to create a file in the directory (FILE_ADD_FILE). AddFile – For a directory, the right to create a file in the directory. |
| AppendData (or AddSubdirectory or CreatePipeInstance) | 0x4, %%4418 | AppendData – For a file object, the right to append data to the file. (For local files, write operations will not overwrite existing data if this flag is specified without FILE_WRITE_DATA.) For a directory object, the right to create a subdirectory (FILE_ADD_SUBDIRECTORY). AddSubdirectory – For a directory, the right to create a subdirectory. CreatePipeInstance – For a named pipe, the right to create a pipe. |
| ReadEA | 0x8, %%4419 | The right to read extended file attributes. |
| WriteEA | 0x10, %%4420 | The right to write extended file attributes. |
| Execute/Traverse | 0x20, %%4421 | Execute – For a native code file, the right to execute the file. This access right given to scripts may cause the script to be executable, depending on the script interpreter. Traverse – For a directory, the right to traverse the directory. By default, users are assigned the BYPASS_TRAVERSE_CHECKING privilege, which ignores the FILE_TRAVERSE access right. See the remarks in File Security and Access Rights for more information. |
| DeleteChild | 0x40, %%4422 | For a directory, the right to delete a directory and all the files it contains, including read-only files. |
| ReadAttributes | 0x80, %%4423 | The right to read file attributes. |
| WriteAttributes | 0x100, %%4424 | The right to write file attributes. |
| DELETE | 0x10000, %%1537 | The right to delete the object. |
| READ_CONTROL | 0x20000, %%1538 | The right to read the information in the object’s security descriptor, not including the information in the system access control list (SACL). |
| WRITE_DAC | 0x40000, %%1539 | The right to modify the discretionary access control list (DACL) in the object’s security descriptor. |
| WRITE_OWNER | 0x80000, %%1540 | The right to change the owner in the object’s security descriptor |
| SYNCHRONIZE | 0x100000, %%1541 | The right to use the object for synchronization. This enables a thread to wait until the object is in the signaled state. Some object types do not support this access right. |
| ACCESS_SYS_SEC | 0x1000000, %%1542 | The ACCESS_SYS_SEC access right controls the ability to get or set the SACL in an object’s security descriptor. |
Mitre techniques and hunting tips:
1-Lateral Movement – T1021, T1053-Remote AT Task:
Technique T1021: Remote Services
Valid Accounts can be used by attackers to log into a service that accepts remote connections, such as telnet, SSH, or VNC. After that, the adversary can act as the logged-on user. Servers and workstations in an enterprise environment can be organized into domains. Domains allow users to log in with a single set of credentials throughout the whole network, providing centralized identity management i.e nowadays we using SSO for all applications. If an adversary has a set of valid domain credentials, they can use remote access protocols like secure shell (SSH) or remote desktop protocol (RDP) to log into a variety of devices.
Technique T1053: Scheduled Task/Job
Attackers may abuse task scheduling functionality to facilitate the initial or recurring execution of malicious code and to execute programs at system startup or on a scheduled basis for persistence. These mechanisms can also be abused to run a process under the context of a specified account (such as one with elevated permissions/privileges).
Hunting Tips:
- Hunt for Share Name: \\*\IPC$ & Relative Target Name: atsvc
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
2-Lateral Movement – T1021, T1053-GPO Scheduled Task:
Technique T1021 & T1053 has been explained in the previous paragraph.
Hunting Tips:
- Hunt for Share Name: “*\\SYSVOL & “Relative Target Name:” end with “*\Scheduled Tasks.xml” and “Access:” contains “WriteData”.
3-Discovery – T1087 Account Discovery:
Technique T1087: Account Discovery
Attackers may try to obtain a list of accounts on a system or in a given environment. This information can assist opponents in determining which accounts exist in order to aid in subsequent actions.
Hunting Tips:
- At least need to hunt 3 of EventID 5145 of different Relative TargetName from same DC.
- Share Name: \\*\IPC$ & Relative TargetName is in (srvsvc, Isarpc, samr, winreg) & Same source IP:port & SourceUserName not eq to “*DC*$” (DC machine accountname)
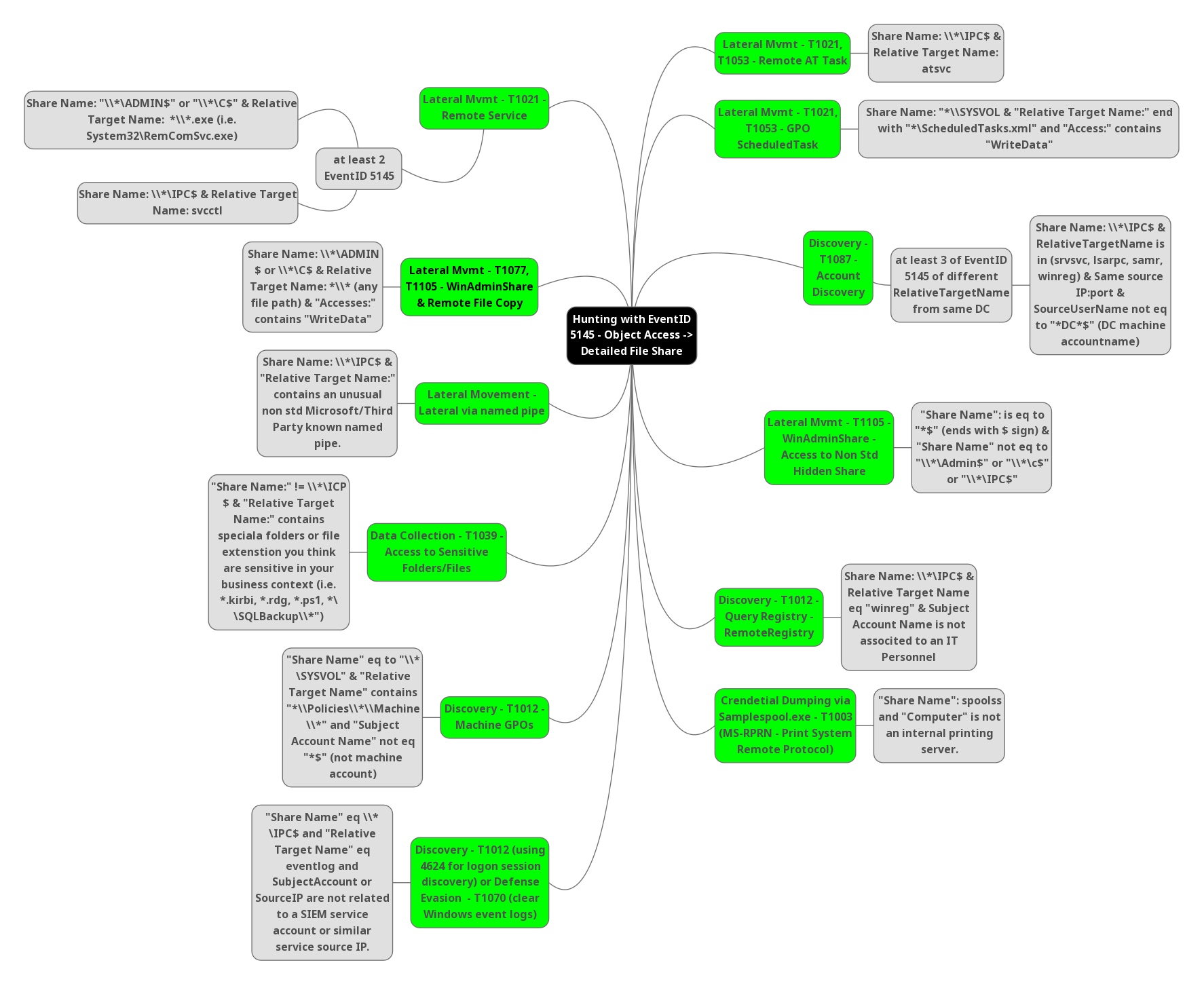
4-Lateral Movement – T1105 WinAdminShare – Access to Non Std Hidden Share:
Technique T1105: Ingress Tool Transfer
Adversaries may transfer tools or other files into a compromised environment from an external system. To bring tools into the target network, files can be copied from an external adversary-controlled machine over the command and control channel or via other protocols using another tool such as FTP. On Mac and Linux, native technologies such as scp, rsync, and sftp can be used to copy files.
Hunting Tips:
- Hunt for “Share Name”: is eq to “*$” (ends with $ sign) & “Share Name” not eq to “\\*\Admin$” or “\\*\C$” or “\\*\IPC$”
Also Read: FireEye’s Open-Source Tool – CAPA to Identify Malware Capabilities
5-Discovery- T1012 Query Registry – RemoteRegistry:
Technique T1012:
Attackers may use the Windows Registry to collect data about the system, configuration, and installed software. The Registry stores a great deal of data on the operating system, settings, software, and security. The Reg utility makes it simple to query the Registry, while there are other ways to do so. Some of the data could help attackers in advancing their operations within a network. During automated discovery, adversaries may use information from the Query Registry to affect subsequent activities, such as whether or not the adversary fully infects the target and/or attempts certain actions.
Hunting Tips:
- Hunt for Share Name: \\*\IPCS & Relative Target Name eq “winreg” & Subject Account Name is not associated to IT Personnel.
6-Crendetial Dumping via Samplespool.exe – T1003 (MS-RPRN – Print System Remote Protocol):
Technique T1003: OS Credential Dumping:
Adversaries may try to dump credentials from the operating system and applications to get account login and credential material, usually in the form of a hash or a clear-text password. After then, credentials can be used to perform Lateral Movement and gain access to restricted data.
Both attackers and professional security testers can employ several of the technologies outlined in related sub-techniques. Additional custom tools are almost certainly available.
Hunting Tips:
- Hunt for “Share Name”: spoolss and “Computer” is not an internal printing server.
7-Lateral Movement – T1021 Remote Service:
Technique T1021 has been explained previously.
Hunting Tips:
- Hunt for Share Name: “\\*\ADMIN$” or “\\*\C$” & Relative Target Name: *\\*.exe (i.e. System32\RemComSvc.exe)
- Hunt for Share Name: \\*\IPC$ & Relative Target Name: svcctl
8-Lateral Movement – T1077, T1105 – WinAdminShare & Remote File Copy:
Technique T1105 has been explained previously.
Technique T1077: Remote Services: SMB/Windows Admin Shares:
- SMB is a file, printer, and serial port sharing protocol for Windows machines on the same network or domain. Adversaries may use SMB to interact with file shares, allowing them to move laterally throughout a network. Linux and macOS implementations of SMB typically use Samba.
- Windows systems have hidden network shares that are accessible only to administrators and provide the ability for remote file copy and other administrative functions.
- Attackers may use this technique in conjunction with administrator-level Valid Accounts to remotely access a networked system over SMB, to interact with systems using remote procedure calls (RPCs),[2] transfer files, and run transferred binaries through remote Execution.
- Attackers can also use NTLM hashes to access administrator shares on systems with Pass the Hash and certain configuration and patch levels.
Hunting Tips:
- Hunt for Share Name: \\*\ADMIN $ or \\*\C$ & Relative Target Name: *\\* (any file path) & “Accesses:” contains “WriteData”
9-Lateral Movement – Lateral via named pipe:
Hunting Tips:
- Hunt for Share Name: \\*\IPC$ & “Relative Target Name:” contains an unusual non std Microsoft/Third Party known named pipe.
10-Data Collection – T1039 Access to Sensitive Folders/Files:
Technique T1039 : Data from Network Shared Drive:
In order to find files of interest, attackers may explore network shares on devices they have hacked. Prior to Exfiltration, sensitive data from faraway systems can be acquired via shared network drives (host shared directory, network file server, etc.) that are accessible from the current system. It’s possible that interactive command shells are being used, and that ordinary cmd functionality is being leveraged to gather data.
Hunting Tips:
- Hunt for “Share Name:” != \\*\ICP $ & “Relative Target Name:” contains speciala folders or file extenstion you think are sensitive in your business context (i.e. *kirbi, *.rdg. *.ps1, *\ \SQLBackup\\*”)
11-Discovery – T1012 Machine GPOS:
Technique T1012 has been explained previously.
Hunting Tips:
- Hunt for “Share Name” eq to “\\* \SYSVOL” & “Relative Target Name” contains “*\\Policies\\*\\Machine\\*” and “Subject Account Name” not eq “*$” (not machine account)
Also Read: Latest Cyber Security News – Hacker News !
12-Discovery- T1012 (using 4624 for logon session discovery) or Defense Evasion T1070 (clear Windows event logs):
Technique T1012 has been explained previously.
Technique T1070 : Indicator Removal on Host:
Attackers may delete or alter generated artifacts on a host system, including logs or captured files such as quarantined malware. Locations and format of logs are platform or product-specific, however, standard operating system logs are captured as Windows events or Linux/macOS files such as Bash History and /var/log/*.
These actions may cause issues with event collecting, reporting, or other intrusion detection notifications. This could compromise the integrity of security solutions by causing significant events to go unnoticed. Due to a lack of data to determine what happened, this action may also obstruct forensic analysis and incident response.
Hunting Tips:
- Hunt for “Share Name” eq \\* \IPC$ and “Relative Target Name” eq eventlog and SubjectAccount or Source IP are not related to a SIEM service account or similar service source IP.
Conclusion:
Even with just one EventID, the blue team may defend against attackers in a variety of ways. It’s not just a basic notion; even a minor opening in the wall can entice attackers to stay inside.



































