What is WMI?
Windows Management Instrumentation (WMI) is the infrastructure for management data and operations on Windows-based operating systems.
- WMI, the Windows Management Instrumentation gives us lots of functionality.
- Very powerful management and information-sharing infrastructure for the Windows operating system.
- It can be directly accessed using PowerShell, VBScript, programming languages like C++ and Visual Basic.
- It sets the rules for accessing data from non-uniform technologies through a standardized architecture.
- WMI is Microsoft’s implementation of this standard, and it’s actually an architecture that lets you access data and information regardless of the device that’s running it. To put it another way, this infrastructure is device-independent.
WMIC (WMI Command) extends WMI so we can access all that stuff through the command-line interface, and of course, that makes it possible for us to use that in our batch scripts. This has been available since Windows 2000 and modern Windows as well.
Role of WMI:
- Server’s primary responsibility is to listen for client requests and react appropriately. A client sends a request over the network when it requires data or functionality from a server.
- The server, by turn, receives the request, processes it, and, depending on the nature of the request, sends back the appropriate information or an error.
- The server can also do a lot of different tasks, such as validating the requester’s authentication, ensuring that the client has the proper permissions, and ensuring that the request is in the correct format, among other things.
- This feature may be built into the operating system or provided by a third-party program. Both of these sources can be combined in some instances.
WMI Feature Set:
- WMI scripts or apps can be used to automate administrative activities on remote machines.
- Provides management data to other operating system and product components.
- It has the ability to start, stop and look at processes. This is also capable of being done on remote machines.
- With WMI Computers can be rebooted remotely.
- We can query the Users & User Groups on the machine, either locally or remotely.
- We can also fetch details of Hard drives/file systems – OS settings – Services – Shares – Registry settings – Event logs.
- The registry settings are extremely significant and incredibly powerful. The WMI console can also be used to retrieve event logs, such as security event logs.
MI vs WMI:
When it comes to Management Infrastructure or Windows Management Instrumentation, we will be a little confused about what will give better operation. Obviously, WMI is most preferable because,
- It has tight alignment with standards.
- Has new native-code provider APIs.
- This API support for rich PowerShell semantics.
- It has new approach to creating PowerShell cmdlets from MI providers using XML.
- It also has backward combability with older WMI implementation.
- And MI is a downloadable update to Windows 7, Windows Server 2008 R2, and Windows Server Standard.
WMI in MITRE ATT&CK:
WMI will come under Execution Tactics where the adversary will try to run malicious code.
- Tactic ID: TA0002
- Technique ID: T1047
- Sub-techniques: No sub-techniques
- Tactic: Execution
- Platforms: Windows
- Permissions Required: Administrator, User
- Supports Remote: Yes
Attackers use WMI to execute malicious commands and payloads. WMI can be used by an adversary to connect with local and remote systems and to carry out various activities, such as gathering information for Discovery and executing files remotely as part of Lateral Movement. Some famous attacks where WMI was used by the adversaries:
- Cobalt Strike adversary simulation software designed to execute targeted attacks and emulate the post-exploitation actions of advanced threat actors. It uses WMI to deliver a payload to a remote host. [S0154]
- Ursnif (also known as Gozi, IFSB or Dreambot) is high-risk banking trojan designed to record various sensitive information. This virus typically infiltrates systems without permission, since developers proliferate it using spam email campaigns. Ursnif droppers have used WMI classes to execute PowerShell commands. [S0386]
- WannaCry is a ransomware worm that spread rapidly through across a number of computer networks in May of 2017. WannaCry utilizes wmic to delete shadow copies.[S0366]
- Deep Panda is a cyber espionage group from China with suspected links to the Chinese government. The group is highly sophisticated and diligent at covering its tracks—hence there is no clear evidence of who these individuals are or their affiliations. The Deep Panda group is known to utilize WMI for lateral movement. [G0009]
- APT29 is threat group that has been attributed to Russia’s Foreign Intelligence Service (SVR). It used WMI to steal credentials and execute backdoors at a future time. They have also used WMI for the remote execution of files for lateral movement.
Kindly refer to the Mitre Tactic T1047 for how WMI was used in various attacks by adversaries.
Why do attackers use WMI for Lateral Movement?
- As it is a built-in Windows application, it can be used a lot.
- Since its scriptable using PowerShell and Sysmon, it’s a wonderful tool for persistence.
- To use this approach, we don’t require any files.
- We can utilize via remote with the help of winrm and wmic.
- System information can be obtained and used in internal recon via WMI queries.
- The majority of the organization has little knowledge of how to monitor WMI events, and if it is done, it will create a lot of noise. As a consequence, it’s quite simple for attackers to exploit it.
Also Read: Threat Hunting Using Windows Security Log
A basic principle of detecting WMI-based attacks:
In windows we can implement rules with the below event IDs to detect WMI attacks:
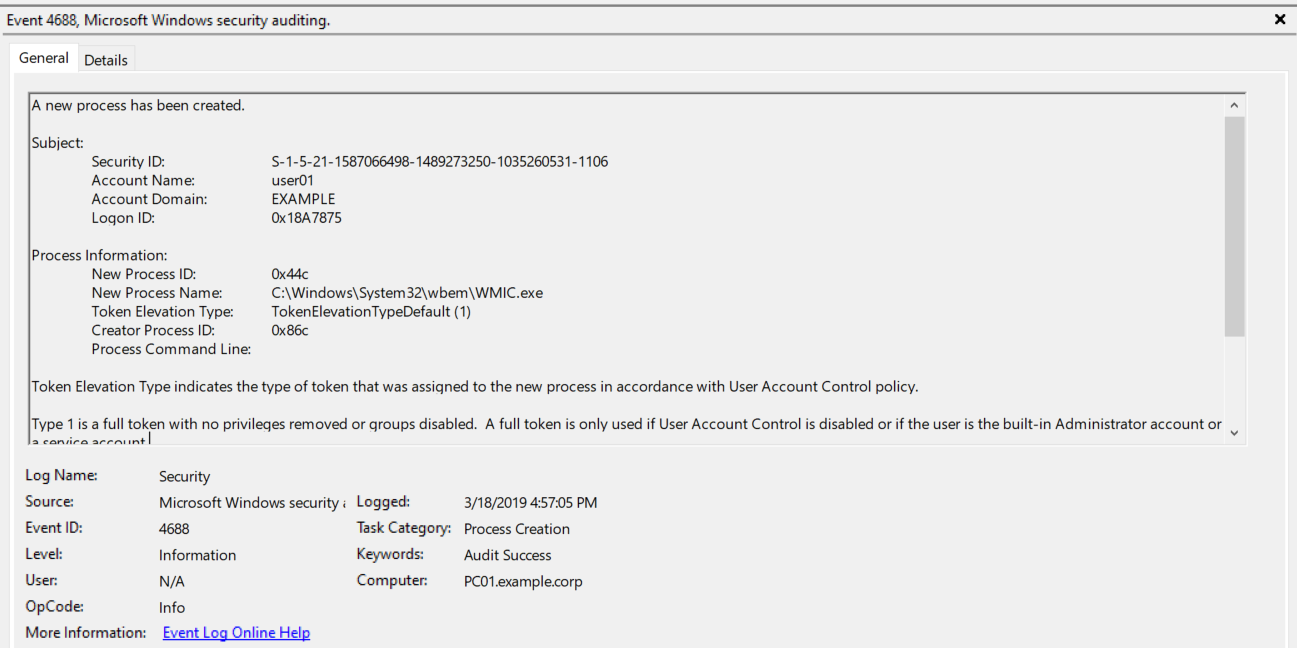
- Keep an eye on Event ID 4688 with the process name WMIC.EXE , these notifies if a new WMI process starts ( C:\Windows\System32\wbem\WMIC.exe). We’re likely to encounter more false positives; therefore we’ll need to filter out known processes.
- In the Microsoft-Windows-WMI-Activity/Operational Log, there is already a default “WMI-Event Detector,” which is Event ID 5860. We can monitor this event ID to log WMI events.
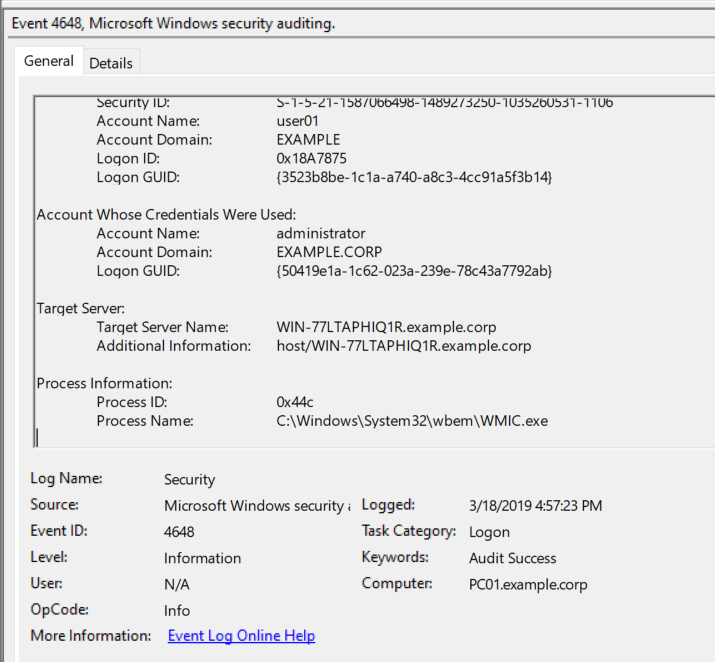
- Monitor Event ID 4648 along with the process name : C:\Windows\System32\wbem\WMIC.exe to identify A logon was attempted using explicit credentials.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
- Usually PowerShell Script Block Auditing will be enabled by default in most organizations. So keep an eye on the Event ID 4104 (Source: Microsoft-Windows-PowerShell) along with the keyword “WMI” to log it if any WMI malicious script is executed via powershell.
Also Read: Threat Hunting Using Powershell and Fileless Malware Attacks
- Furthermore, it appears that Sysmon’s additional infrastructure to monitor WMI Events is nothing more than a few WMI service requests that are then sent back to their own log space (Sysmon/Operational).
- Sysmon can be configured to monitor WMIEventFilter activity (event 19), WMIEventConsumer activity (event 20), and WMIEventConsumerToFilter activity (event 21). In addition to Sysmon logs, the %SystemRoot%\System32\winevt\Logs\Microsoft-Windows-WMI-Activity%4Operational log also records information about use of WMI.
- The only issue we found was that sysmon didn’t generate any logs for Timer-based WMI Events. If you want to catch those, keep an eye on Windows Event Id 5859/5861.
- Keep an eye on Event ID 5858 which will log for WMI-Activity.
Conclusion:
WMI is used on a daily basis by sysadmins across large domains due to its flexibility and scalability. Easy to deploy, scripts that leverage WMI can be seen everywhere. As it is a built-in application, attackers can easily use WMI and stay on the host for long periods of time. Monitoring WMI and related event IDs will improve the detection of additional attacks.