Source/Credits/Written By: Jamie St. Patrick
Crimson RAT is a Remote Access Trojan – a malware that hides behind a legitimate file and infects computers when downloaded and installed. The moment it is installed, it pretty much operates like any other malware and causes havoc. This particular malware has been seen targeting diplomatics and research facilities using misinformation about the pandemic as a scare tactic in its spear-phishing campaign.
General Description
When Crimson RAT is downloaded and installed, it can perform several malicious functions. The RAT can perform audio surveillance using the victim’s microphone, take screenshots and capture webcam video and steal credentials from web-browsers. Moreover, it has the capability to download files from a command and control (C2) server to exfiltrate data and emails from outlook.
Also Read: Anatomy of the Infamous EMPIRE Powershell Framework
Execution Process
The execution process is pretty straightforward. The malware executable file is located directly inside a malicious document and once the user opens it, the file drops the trojan. In other instances, a malicious document can contain a macro that leverages Powershell to download and start a Crimson executable file. When the trojan starts, it will try to establish a connection with a C2 server and transmit information about the victim’s system and the list of running processes on that system.
Technical Details
Note: The malware was run on a Windows 7 Professional SP1 (32 bit) environment.
When the excel executable file is dropped, two directories named “Edlacar” and “Uahaiws” are created. In order to load the payload, the malware dropper checks whether the target is running on a 32-bit or 64-bit operation system so it can execute the correct payload. It then drops the payload into the Uahaiws directory and unzips its content in the Edlacar directory. In the end, it executes the PowerShell script to load the dhrwarsav.exe.
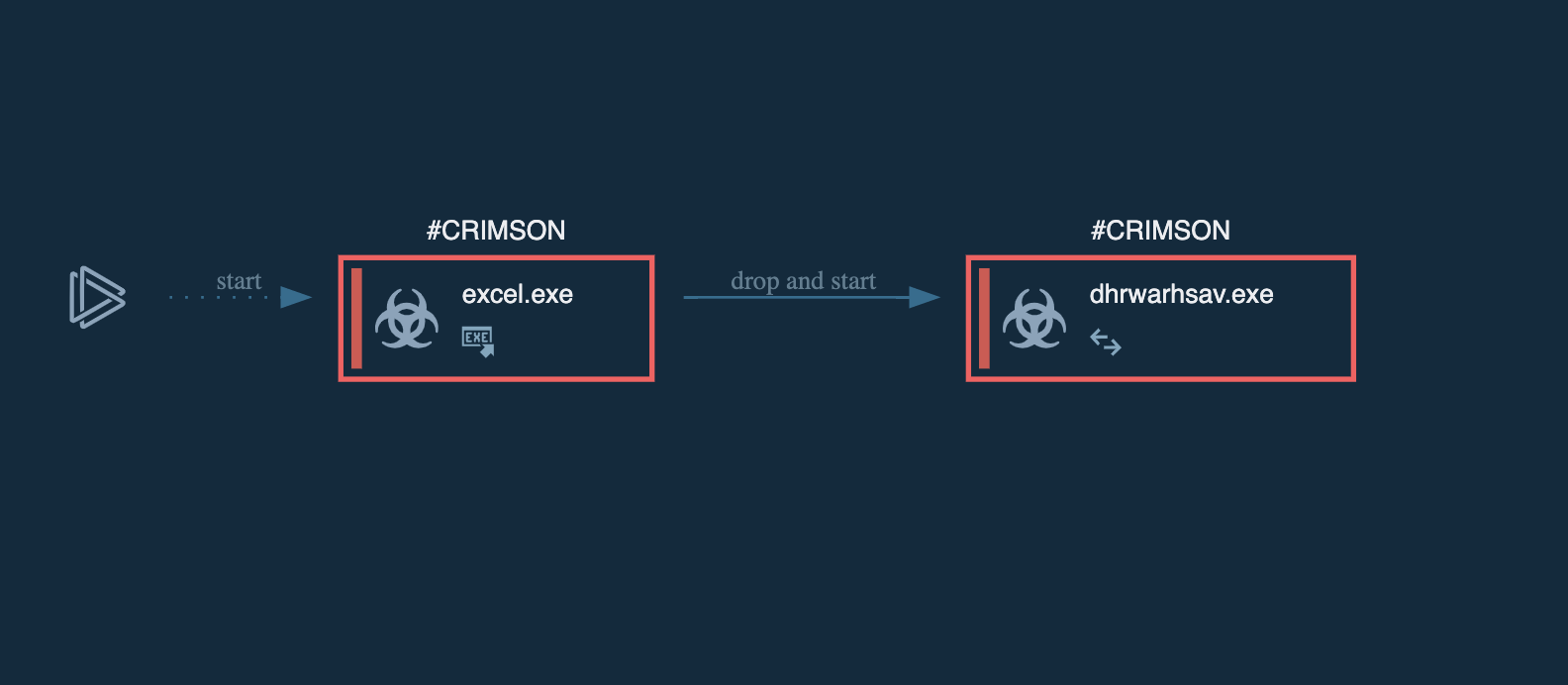
excel.exe
The executable interacts with the Windows registry to gather information about the system, configuration and installed software. The registry contains a significant amount of information about the operating system, configuration, software, and security.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
dhrwarhsav.exe
The executable runs a command and control (C2) over a protocol and port pair that is typically not associated to bypass proxies and firewalls that have been improperly configured. In this instance, the C2 was over HTTPS over 6728 as suppose to 443.
Detection
Digital Forensic Analyst can detect the Crimson RAT based on its file operations. From the windows event logs under application or Powershell, do a filter search for “Edlacar” or “Uahaiws”. If such names are found, contain its content and run it through a sandbox environment. That may be the Crimson RAT.
Also Read: Topmost Signs of Compromise Detected with Windows operating System
Conclusion
So far, this malware has mostly been used exclusively in military espionage, but it may very well become more widespread in the future.
Source
This article wouldn’t be possible without the work of others. Here are the sources I’ve used during my investigation:
- Dedola, G. (2020, August 20). Transparent Tribe: Evolution analysis, part 1. Retrieved September 2, 2021.
- https://attack.mitre.org/software/S0115/ Last accessed: Wed 16 Feb, 2022



































