Weeks ago, the hacker group known as LAPSUS$ broke into NVIDIA’s servers and grabbed almost 1TB of delicate information. The gathering then, at that point, continued to hold said information emancipate, requesting that the GPU brand pay them so as not to deliver data relating to its chipset records, illustrations, and silicon utilized. As of late, apparently, the gathering is currently involving its not well-gotten gains for something different: marking malware off with terminated NVIDIA authentications.
Security experts have discovered that the signing certificate that was also included in this first batch of files is now used by malware. What is important to note here is that both leaked signing certificates are expired, however, Windows operating system still allows the drivers signed with those certificates to be loaded with the system which poses a great security risk.
Security researchers Kevin Beaumont and Will Dormann shared that the stolen certificates utilize the following serial numbers:
43BB437D609866286DD839E1D00309F5
14781bc862e8dc503a559346f5dcc518Some of the files were likely uploaded to VirusTotal by security researchers but others appear to be used by threat actors for malware campaigns.
Security researcher Florian Roth (@cyb3rops) shared the statement on Twitter as Now we see many malware samples signed with the leaked NVIDIA certs on @virustotal – Florian Roth
VirusTotal Queries:
VT Dorks to Find Samples Signed with Leaked NVIDIA Certificates.
Samples (Munin output), hashes, and Infos:
Click Google Docs for sample hash lookups.
YARA Signature:
Github Link
import “pe”
rule SUSP_NVIDIA_LAPSUS_Leak_Compromised_Cert_Mar22_1 {
meta:
description = “Detects a binary signed with the leaked NVIDIA certifcate and compiled after March 1st 2022”
author = “Florian Roth”
date = “2022-03-03”
modified = “2022-03-04”
score = 70
reference = “https://twitter.com/cyb3rops/status/1499514240008437762”
condition:
uint16(0) == 0x5a4d and filesize < 100MB and pe.timestamp > 1646092800 and // comment out to find all files signed with that certificate
for any i in (0 .. pe.number_of_signatures) : (
pe.signatures[i].issuer contains “VeriSign Class 3 Code Signing 2010 CA” and (
pe.signatures[i].serial == “43:bb:43:7d:60:98:66:28:6d:d8:39:e1:d0:03:09:f5” or
pe.signatures[i].serial == “14:78:1b:c8:62:e8:dc:50:3a:55:93:46:f5:dc:c5:18”
)
)
}
Hunting for NVIDIA Certificates:
(Source: crowdstrike )
Find NVIDIA Signed Software
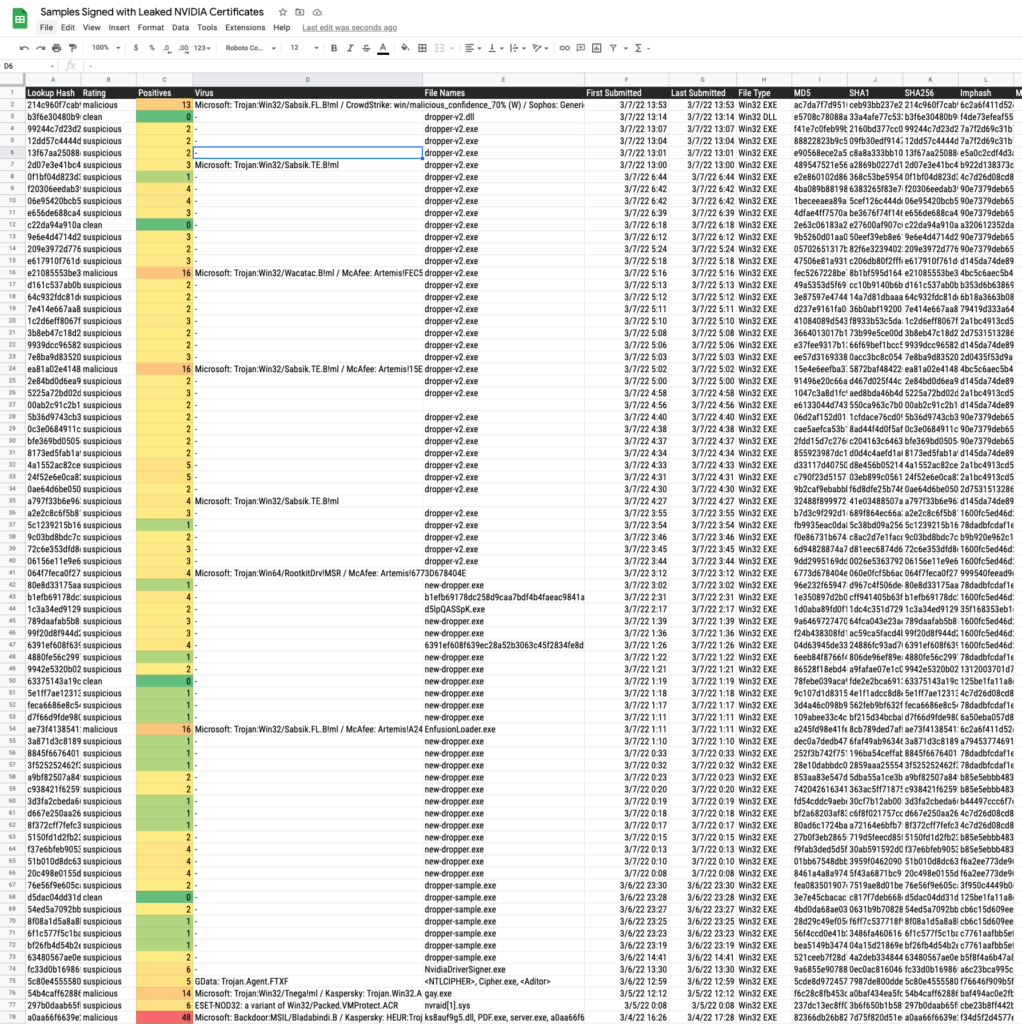
First, we want to see how much stuff we’re dealing with. To do this, we’ll look for binaries signed with NVIDIA’s code signing certificate. If we want to cast the widest possible net, we can look for all NVIDIA signed binaries like so:
index=json ExternalApiType=Event_ModuleSummaryInfoEvent
| search SubjectCN IN ("NVIDIA Corporation")
| lookup local=true appinfo.csv SHA256HashData OUTPUT FileName, ProductName, ProductVersion , FileDescription , FileVersion , CompanyName
| fillnull value="Unknown" FileName, ProductName, ProductVersion , FileDescription , FileVersion , CompanyName
| stats values(SubjectDN) as SubjectDN, values(SHA256HashData) as sha256 by IssuerCN, FileName, ProductName, ProductVersion , FileDescription , FileVersion , CompanyName
| sort + FileName
This list will (likely) be very, very large.
If we want to be more restrictive, we can key-in on specific certificate serial numbers — below are the two serial numbers that we’ve observed being used in open source malware repositories (1) (2). If, after this post is published, you wish to add additional serial numbers to the scope of the search, just append them to the list in the second line. That query will look like this:
index=json ExternalApiType=Event_ModuleSummaryInfoEvent
| search SubjectSerialNumber IN (43bb437d609866286dd839e1d00309f5, 14781bc862e8dc503a559346f5dcc518)
| lookup local=true appinfo.csv SHA256HashData OUTPUT FileName, ProductName, ProductVersion , FileDescription , FileVersion , CompanyName
| fillnull value="Unknown" FileName, ProductName, ProductVersion , FileDescription , FileVersion , CompanyName
| stats values(SHA256HashData) as sha256 by IssuerCN, SubjectCN, SubjectDN, FileName, ProductName, ProductVersion , FileDescription , FileVersion , CompanyName
- Line one grabs all the
Event_ModuleSummaryInfoEventdata from the selected search window. This event will show PE Authenticode and Certificate data. - Line two narrows our scope to the two certificate serial numbers we have in scope at the moment.
- Line three uses a lookup table to see if the ThreatGraph knows what the name of this file is.
- Line four sets the value of columns to “Unknown” if a value can’t be found.
- Line five organizes our output to make it a little easier to read.
The output should look like this:
Right at the top of both queries, you will see there is a list of “Unknown” SHA256 values. To be clear, this DOES NOT mean these are bad, rogue, etc. This is the collection of SHA256 values that we’re going to further research.
Know the Unknowns
To get a handle on the unknowns, we’re going to create another search. In my list above (in the second query), the following hashes don’t have data associated with them:
17d22cf02b4121efd4526f30b16371a084f5f41b8746f9359bad4c29d7deb715
31f87d4188f210be2df99b0a88fb437628a9864a3bffea4c5238cbc7dcb14df8
31fef1519f5dd7b74d21a19b453ace2c677922b8060fea11d6f53bf8f73bd99c
4d4e71840e5802b9ab790bae15bcadb0a31b3285009189be50573e313db07fe2
6b02469349125bf474ae29303d81e84ad2f073ee6b6c619015bf7b9fea371ce6
6bf1d0b94f4097f65fd611ea570b10aff7c5141d76736b0cb001a5de60fb778b
9fac39999d2d87e0b60eedb4126fa5a25d142c52d5e5ddcd8bdb6bf2a836abb9
a86a788e4823caa25f6eb3f6c5d7e59de225f121af6ed24077e118ba324e4e19
b4226ed448e07357f216c193ca8f4ec74268e41fa369196b6de54cf058f622d1
b4bd732e766e7de094378d2dec07264e16eb6b75e9c3fa35c2219dfe3726cc27
b7c21ee31c8dea07cc5ccc9736e4aac31428f073ae14ad430dc8bdf999ab0813
cbf74c0c0f5f05a501c53ab8f96c716522096cf60f545ecadd3100b578b62900
d4210f400bcf3bc2553fc7c62493e96554c1b3b82d346db8adc84c75cea124d6
db22f4465ed5bb82e8b9322291cafc554ded1dc8ecd7d7f2b1b14784617a0f5a
ed5728d26a7856886faec9e3340ce7dbafbf8daa4c36aad79a8e7106b998d76a
f39ce105207842154e69cedd3e332b2bfefad82cdd40832245cc991dad5b8f7c
fce84e34a971e1bf8420639689c8ecc6170357354deb775c02f6d70a28723680
Ff3935ba15be2d74a810b695bdc6529103ddd81df302425db2f2cafcbaf10040
If you’re using the first query, your list of hashes will be MUCH longer. That’s fine, just place the giant list into the same section outlined below.
Note: in our first query where we found these hashes, we use the event Event_ModuleSummaryInfoEvent. This data persists in Falcon for one year; regardless of the retention package you purchased. The query we’re about to run uses events that are linked to your specific retention period. For this reason, when we run this next query I’m not expecting to see all the SHA256 values present. They could be, but they also might not be.
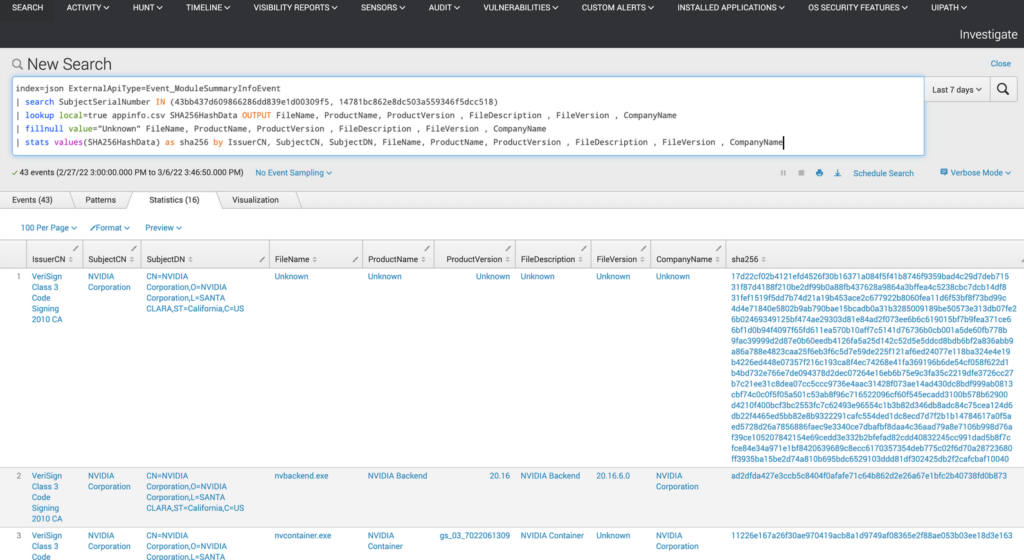
Here is the query:
index=main sourcetype IN (ProcessRollup*, ImageHash*, PeFileWritten*, DriverLoad*) event_platform=win event_simpleName IN (ProcessRollup2, ImageHash, PeFileWritten, DriverLoad)
| search SHA256HashData IN (
17d22cf02b4121efd4526f30b16371a084f5f41b8746f9359bad4c29d7deb715
31f87d4188f210be2df99b0a88fb437628a9864a3bffea4c5238cbc7dcb14df8
31fef1519f5dd7b74d21a19b453ace2c677922b8060fea11d6f53bf8f73bd99c
4d4e71840e5802b9ab790bae15bcadb0a31b3285009189be50573e313db07fe2
6b02469349125bf474ae29303d81e84ad2f073ee6b6c619015bf7b9fea371ce6
6bf1d0b94f4097f65fd611ea570b10aff7c5141d76736b0cb001a5de60fb778b
9fac39999d2d87e0b60eedb4126fa5a25d142c52d5e5ddcd8bdb6bf2a836abb9
a86a788e4823caa25f6eb3f6c5d7e59de225f121af6ed24077e118ba324e4e19
b4226ed448e07357f216c193ca8f4ec74268e41fa369196b6de54cf058f622d1
b4bd732e766e7de094378d2dec07264e16eb6b75e9c3fa35c2219dfe3726cc27
b7c21ee31c8dea07cc5ccc9736e4aac31428f073ae14ad430dc8bdf999ab0813
cbf74c0c0f5f05a501c53ab8f96c716522096cf60f545ecadd3100b578b62900
d4210f400bcf3bc2553fc7c62493e96554c1b3b82d346db8adc84c75cea124d6
db22f4465ed5bb82e8b9322291cafc554ded1dc8ecd7d7f2b1b14784617a0f5a
ed5728d26a7856886faec9e3340ce7dbafbf8daa4c36aad79a8e7106b998d76a
f39ce105207842154e69cedd3e332b2bfefad82cdd40832245cc991dad5b8f7c
fce84e34a971e1bf8420639689c8ecc6170357354deb775c02f6d70a28723680
ff3935ba15be2d74a810b695bdc6529103ddd81df302425db2f2cafcbaf10040
)
| eval falconPID=coalesce(ContextProcessId_decimal, TargetProcessId_decimal)
| eval ProcExplorer=case(falconPID!="","https://falcon.crowdstrike.com/investigate/process-explorer/" .aid. "/" . falconPID)
| stats values(FileName) as fileName, dc(aid) as endpointCount, count(aid) as runCount, values(FilePath) as filePaths, values(event_simpleName) as eventType by SHA256HashData, ProcExplorer
Again, what you need to do to customize this query is to remove the block of my SHA256 values and replace them with your “Unknown” list.
The query is looking for file write, file execute, DLL load, and driver load events that belong to one of these SHA256 values we’ve specified. The output will look similar to this:
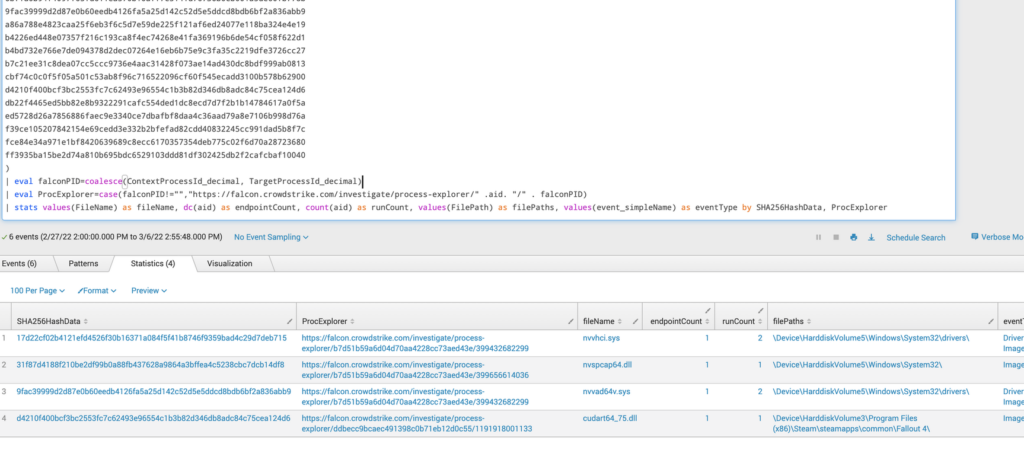
All of this activity appears normal to me — with the exception of the last line as it appears I have a co-worker running Fallout 4 on a system with Falcon installed on it (sigh).
If you want to drill-in on any of these results, you can click the “ProcExplorer” link to be taken to the Process Explorer view.
Frequency Analysis
The most effective way to deal with a dataset this large and an event this common is likely to perform frequency analysis. The following can help with that:
index=main sourcetype IN (ProcessRollup*, ImageHash*, PeFileWritten*, DriverLoad*) event_platform=win event_simpleName IN (ProcessRollup2, ImageHash, PeFileWritten, DriverLoad)
| search SHA256HashData IN (
INSERT SHA256 LIST HERE
)
| eval falconPID=coalesce(ContextProcessId_decimal, TargetProcessId_decimal)
| eval ProcExplorer=case(falconPID!="","https://falcon.crowdstrike.com/investigate/process-explorer/" .aid. "/" . falconPID)
| rex field=FilePath ".*\\HarddiskVolume\d+(?<trimmedPath>.*)"
| stats values(FileName) as fileName, dc(aid) as endpointCount, count(aid) as runCount, values(trimmedPath) as filePaths, values(event_simpleName) as eventType by SHA256HashData
The output will look similar to this:
From here, I might look for things in AppData/Temp, a users Download folder, or similar — as those are not places I expect NVIDIA binaries to be. I also might initially target exe files as NVIDIA driver files are typically in the sys or dll format.
The queries can be further customized to suit your specific hunting needs, but this is meant to get those creative juices flowing.
(Source: crowdstrike )



































