While most cyberattacks are sent off through email, attackers are continuously searching for better approaches to connect with victims. Recently, the threat intelligence team at Abnormal Security noticed a few assaults focusing on their clients that began through an online contact form. BazarLoader is generally firmly connected with the cybercrime bunch known as Wizard Spider, credited with fostering the Trickbot banking trojan and Conti ransomware.
In these new missions, the actors picked a much lower-sway topic, professing to be an expected client in the customary course of business.
Online Contact Form to Initiate Communication
Between December 2021 and January 2022, Abnormal security recognized a progression of phishing efforts focusing on a few of its clients. From the beginning, the general volume of messages appeared to be low; nonetheless, as they maintained investigating these assaults, obviously the volume was misleadingly collapsed in light of the fact that email was not the underlying specialized technique utilized.
Rather than straightforwardly sending a phishing email, the attacker in these cases started a discussion through an association’s site contact form.
When the contact form has been put together by the attacker, they essentially delay until somebody at the objective organization connects with them to follow up.
After Successful Contact, Attackers Send a Malicious File
After completely laying out their cover personality through email, the threat actors proceeded with project dealings with an end goal to persuade their casualty to download a malicious document. Regularly this elaborates with social engineering.
BazarLoader Malware Analysis
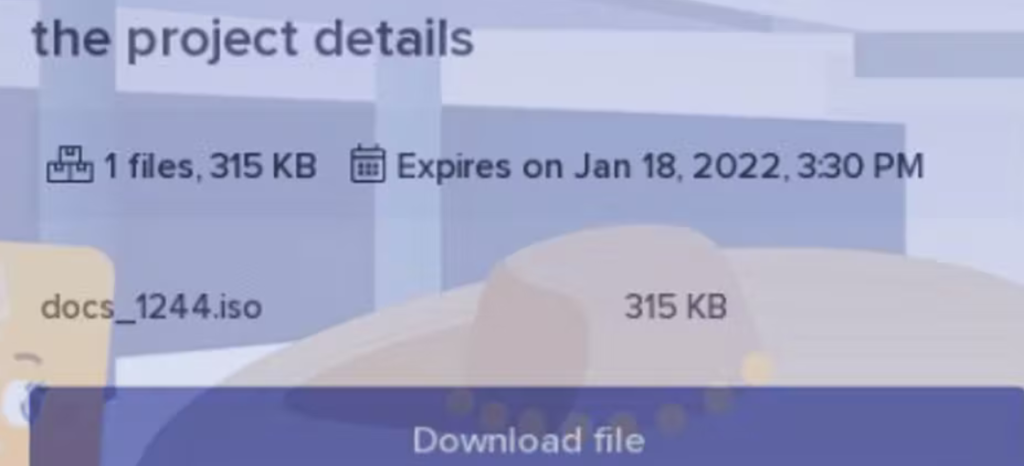
The file shared by the threat actor is a .iso file with two components, both masquerading as a different file type. At first glance, the .iso file appears to contain a shortcut to the folder with the project and a .log file bearing the name of a legitimate Windows file as an anti-detection technique. In actuality, the two are a windows .lnk file and a .log file that is not DumpStack.log.
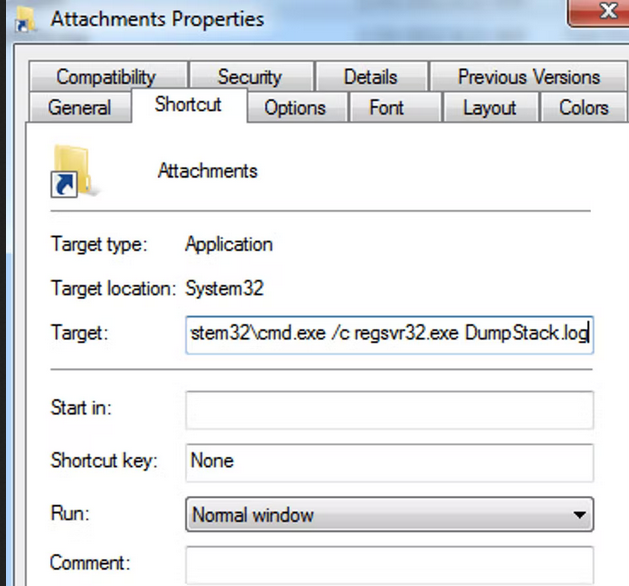
Because shortcut .lnk files allow their creator to specify command-line arguments to perform an action on the victim’s device, cybercriminals can use them for nefarious means.
In this case, the .lnk file properties contain a command instruction to open a terminal window using regsvr32.exe to run the so-named file DumStack.log. In reality, it’s a BazarLoader Dynamic-link library (DLL) file.
With a process injection technique, the DLL uses svchost.exe service to evade detection and establish a connection with their command and control (C2) server at the IP address 13.107.21[.]200 using port 443.
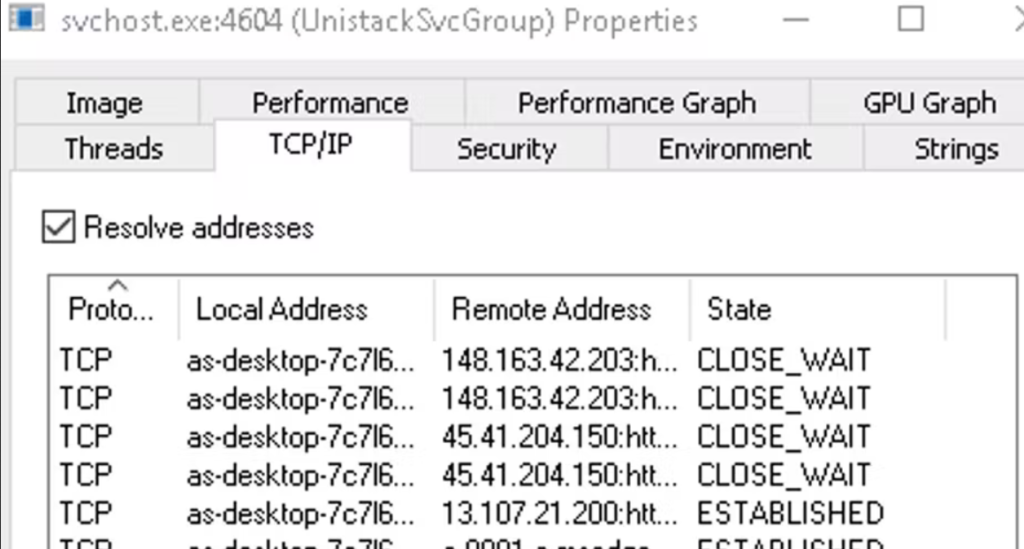
Connection established with C2.

At the time of this investigation, some of the C2 IP addresses were down, and the others were not able to download the second stage of the attack. This leaves some level of uncertainty as to the intended second-stage malware payload. However, past relationships between the IP address 13[.]107[.]21[.]200 illustrated in red in the graph below reveal previous links to malware.
Malware previously related to the IP address 13[.]107[.]21[.]200 has included the following:
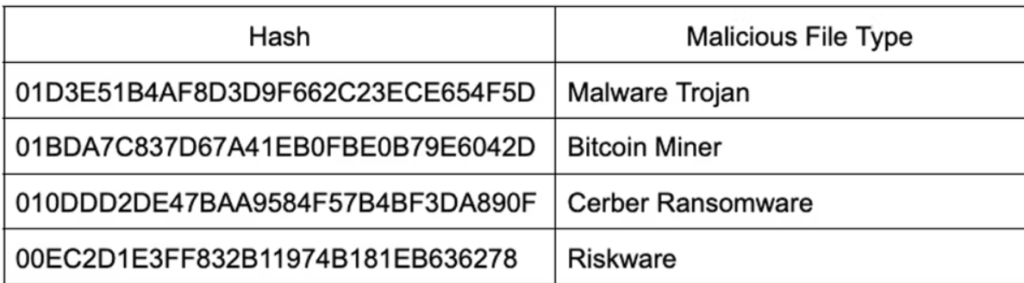
Based on this, it’s clear that the threat actors were attempting to execute a multi-stage attack with BazarLoader as a first step.
The actors in this campaign attempted to improve their credibility by using customer contact forms to establish their identity as trusted senders. Then, they sent emails from spoofed domains to impersonate a known business. These spoofed domains were difficult to detect given that they are identical to the legitimate website other than the top-level domain, which was changed from .com to .us to trick users.
Indicators of Compromise (IOCs)
104[.]215[.]148[.]63
45[.]15[.]131[.]126
148[.]163[.]42[.]203
45[.]41[.]204[.]150
193[.]169[.]86[.]84
76[.]6[.]231[.]20
131[.]253[.]33[.]200
72[.]21[.]91[.]29
docs_1244.iso
97806F6DA402F135FA0556ADF5809D6D3BC629E967A0771B9FEB5BA55267D560
DumpStack.log
8395B26BE4A7D57F9B60839257C3E7B9E6756DBBEB818DE6575987D6E041C8FD
Attachments.lnk
CE6E63191588E449DE4AB45FF4D32E1BBD1C67681C74C32DE3A4DB63331278CC
( Source: abnormalsecurity )



































