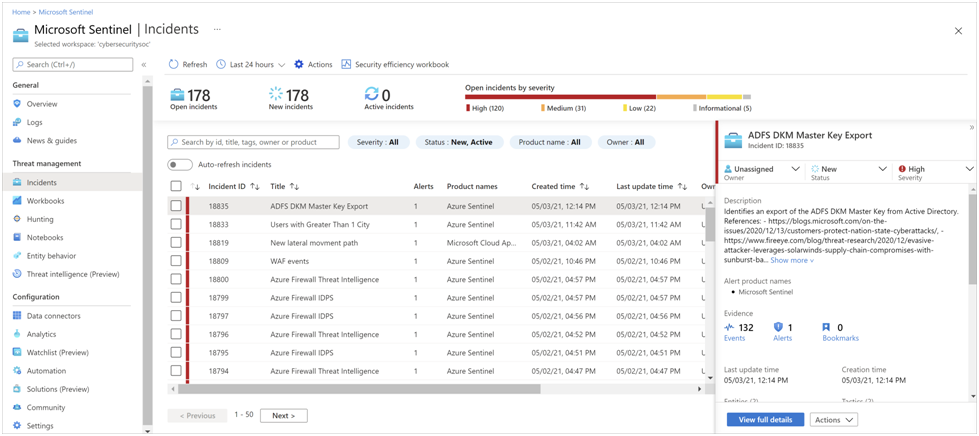
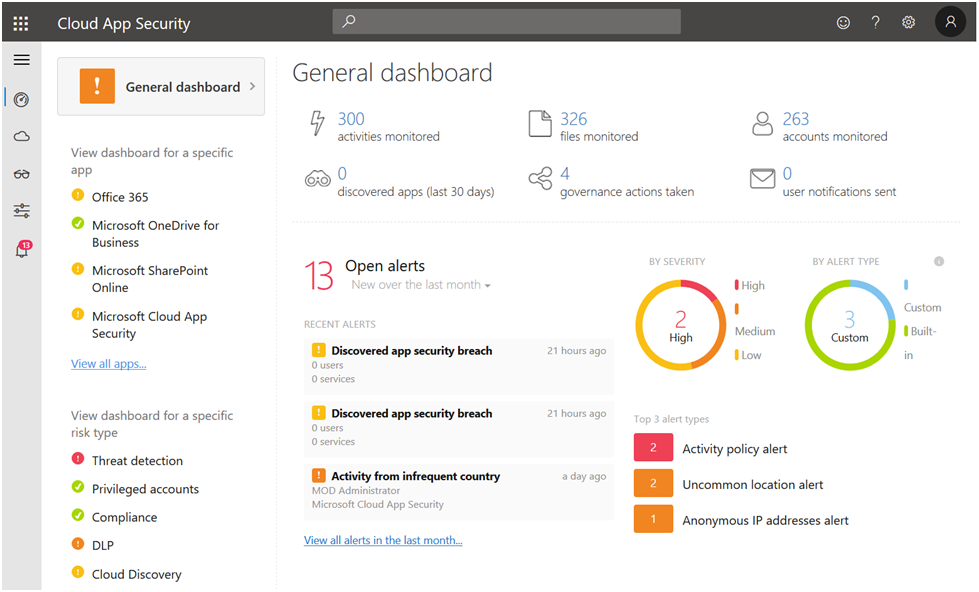
The majority of organizations are focusing on improving log analysis and developing a SIEM capability for cloud-based workloads. The traditional SIEM is perfect for on-premises, but enterprises that are becoming digital are quickly adopting public cloud technologies. Azure sentinel is one of the Microsoft products which acts as SIEM. Microsoft provides a fantastic set of cloud security solutions for use; here are a few examples:
- Azure Security Center
- Microsoft 365 Security Center
- Azure AD Identity Protection
- Microsoft Defender ATP
- Azure ATP & O365 ATP
- Cloud App Security
- Azure Sentinel
Speed Up Software Innovation Without Sacrificing Security Oxeye
Also Read: Azure Sentinel and its Components
Today we will be covering how to integrate Microsoft cloud architecture and the sample architecture with cloud security solutions.
Hybrid Enterprise Cybersecurity Reference Architecture:
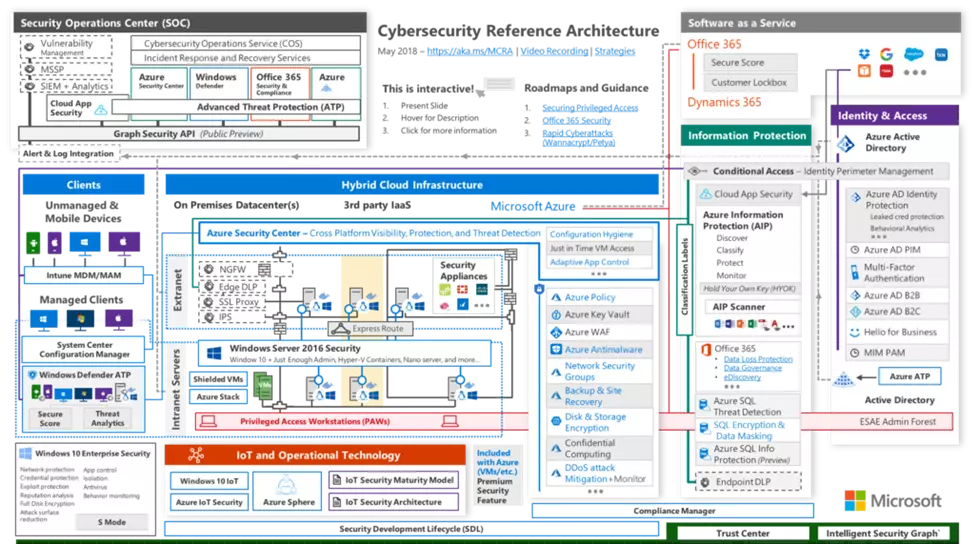
When it comes to security monitoring in the Microsoft cloud, integrations and licenses play a key role in gaining the most out of the security solutions. Some of the integrations are pre-installed, but the majority of them must be enabled by an administrator.
Also Read: Process Injection Techniques used by Malware – Detection & Analysis
Sample Integration Architecture with cloud security solutions:
Here I have not covered all possible security solutions and integration scenarios; rather, provided an overview of which solutions can be used to investigate alerts and suspicious activity in the cloud or in on-premises. In most cases, we must integrate with the investigation solution. The alert is triggered by Sentinel, and the investigation begins from there. It may also be replaced by a third-party SIEM (Splunk, QRadar, etc). Both Sentinel and Cloud App Security have a strong set of investigation capabilities and store a lot of data from the user identity, device identity, and network traffic. The fact that the investigation does not begin with Azure Security Center or M365 Security Center implies that alerts from these solutions can be found and sent to SIEM – Sentinel.
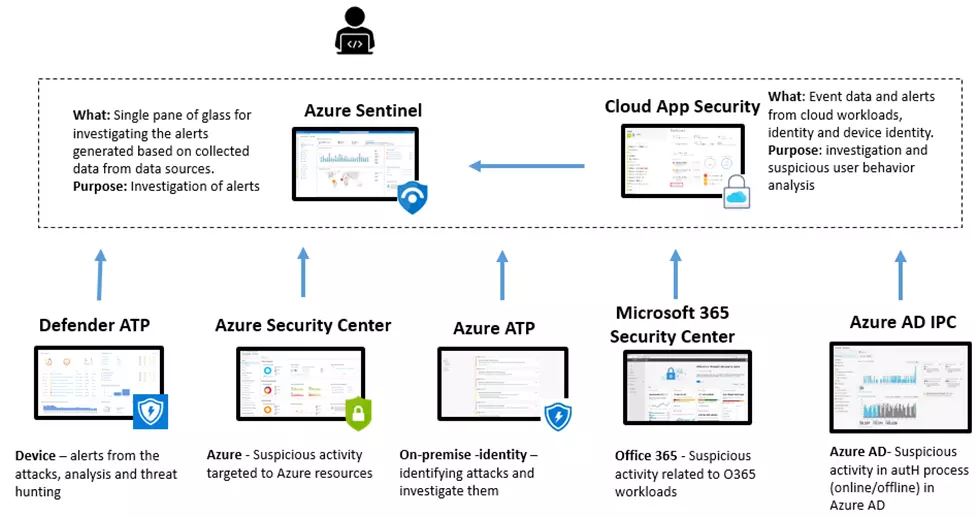
Also Read: Security Researchers Revealed the Infrastructure of Karakurt Linked to Conti Hacking Group
Top Category: Investigating the Alerts:
As previously stated, we recommend beginning the investigation with SIEM (Sentinel) or MCAS. Deep dive analysis can be performed within the alert source itself, such as MDATP if the initial alert was generated there.
Azure Sentinel:
Sentinel is a fully cloud-based SIEM solution that also supports SOAR. Sentinel offers a single pane of glass solution for alert detection, threat visibility, proactive hunting, and threat response, as well as Azure Workbooks and Jupyter Notebooks for advanced threat hunting and investigation scenarios.
Also Read: Latest Cyber Security News – Hacker News !
Microsoft Cloud App Security (MCAS):
Microsoft Cloud App Security (MCAS) is a Cloud Access Security Broker that offers a variety of deployment options such as log collection, API connectors, and reverse proxy. MCAS supports UEBA, and it is best for investigating internal user suspicious and potentially malicious activity.
In the following blogs, we will go over cloud solutions in full depth.