What is Ngrok?
Ngrok is a program that allows you to access your private systems that are behind NAT or a firewall from the outside (internet). It’s an encrypted TCP tunnel that provides an address that anyone can access from the internet, and then connects the other end of the tunnel to local functionality.
How does Ngrok work?
You’re using ngrok on a local machine to provide a service to others across the internet. Simply run the command and specify the protocol you want to use, as well as the local port it’s listening on. Ngrok then creates a cloud address that people can access. It then connects those two things via an encrypted tunnel, so that when you go to the Internet address, you automatically land on your local service!
Ngrok uses secure tunnels to connect local servers behind NATs and firewalls to the public internet. We can connect to our laptop or server via SSH from the public internet using Ngrok.
Also Read: Web Malware Removal | How to Remove Malware From Your Website?
Use Cases
Tunneling SSH
Description:
Use Ngrok service to make local SSH connection available to internet users for successful secured connection.
Workflow:
- Enable SSH in the local machine by the command “sudo systemctl start ssh” and check its status by the command “sudo systemctl status ssh”
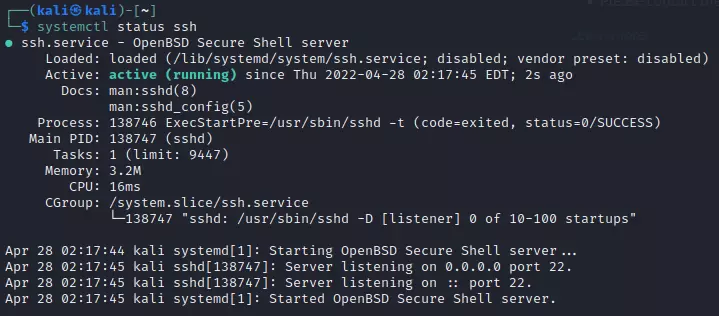
- Start Ngrok to forward SSH traffic from local machine to Ngrok service by the command “sudo ngrok tcp 22 –authtoken < YOUR_AUTH_TOKEN >”
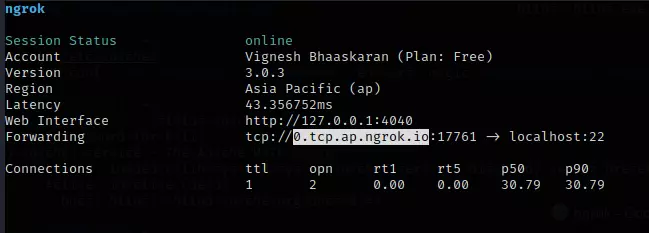
Note: Auth token can be found here https://dashboard.ngrok.com/get-started/your-authtoken
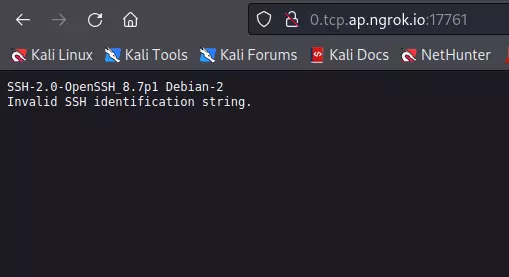
- Open the browser, paste the Ngrok link along with port number displaying on the screen starts with tcp://<Ngrok link>: port number and verify the SSH banner which is running on local machine.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
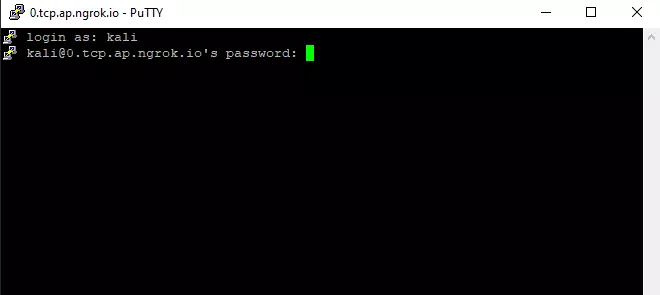
- On the other machine, using putty try to connect to Ngrok Link along with port number which as per the screen short below.
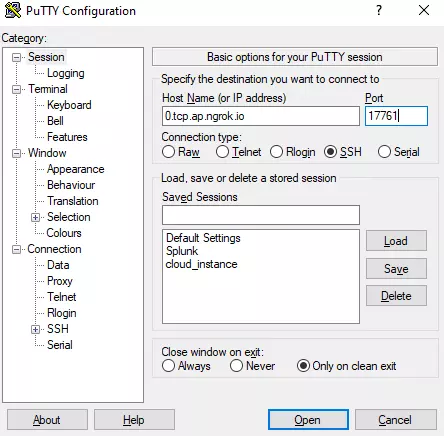
- Provide proper username and password to login successfully.
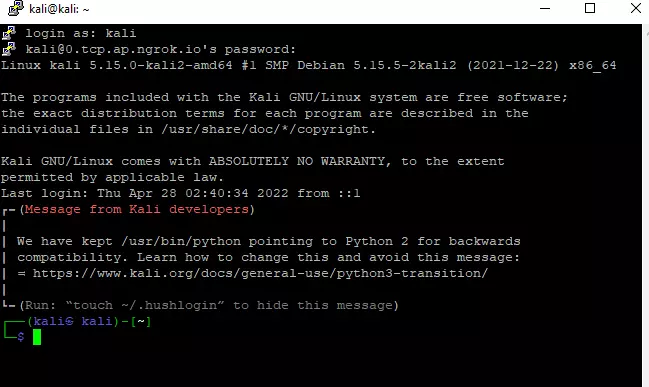
- Finally, will observe the local machine SSH service banner.
Tunneling RDP
Description:
Use Ngrok service to make local RDP connection available to Remote users bu hiding your original IP or hostname.
Workflow:
- Enable RDP connection on any windows machine by navigating to Remote Desktop Settings
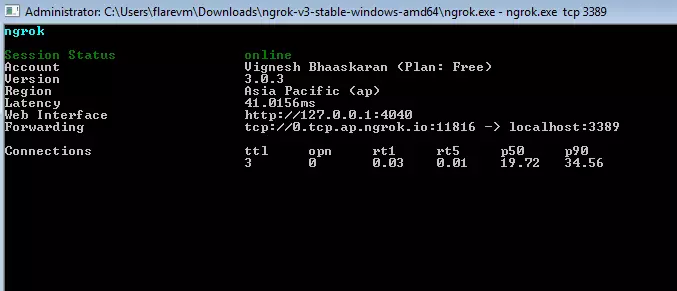
- Start Ngrok to forward RDP 3389 traffic from local machine to Ngrok service by the command “ngrok tcp 3389”.
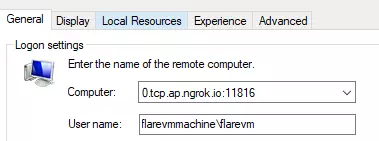
- On the other machine, using putty try to connect to Ngrok Link along with port number which as per the screen short below.
- Provide proper username and password to login successfully.
- Finally, will observe the local machine Desktop using forwarded RDP traffic by Ngrok service.
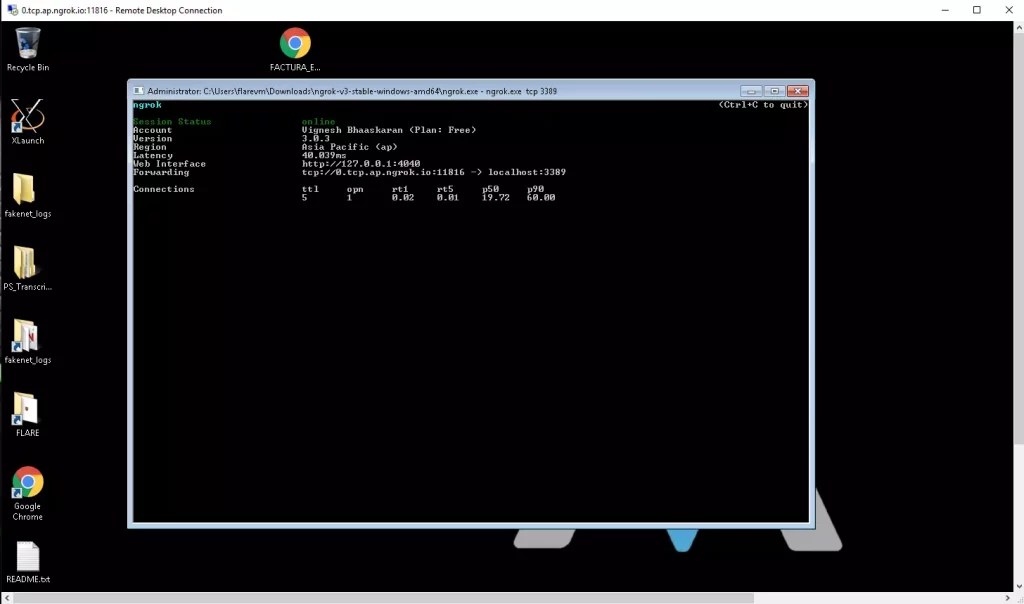
The idea behind this technique is to use a free tunneling service provided by ngrok.com to redirect all TCP packets to our local system by running a ngrok client on the local system. Because Remote Desktop uses TCP with port 3389, all TCP packets arriving at ngrok will be redirected to the TCP of the localhost. We can also connect to RDP over the internet.
Also Read: What is Port Forwarding and the Security Risks?
There are many use cases and here what we depicted are some of those. To work on different use cases please refer to Ngrok documentation.
SIEM Detection
Splunk:
For Endpoint Events
(source="<your_winevent_log_source>:*" AND ((CommandLine="* tcp 139*" OR CommandLine="* tcp 445*" OR CommandLine="* tcp 3389*" OR CommandLine="* tcp 5985*" OR CommandLine="* tcp 5986*") OR (CommandLine="* start *" AND CommandLine="*--all*" AND CommandLine="*--config*" AND CommandLine="*.yml*") OR ((Image="*ngrok.exe") AND (CommandLine="* tcp *" OR CommandLine="* http *" OR CommandLine="* authtoken *"))))For DNS Logs
index=<your_dns_index> ("tunnel.us.ngrok.com" OR "tunnel.eu.ngrok.com" OR "tunnel.ap.ngrok.com" OR "tunnel.au.ngrok.com" OR "tunnel.sa.ngrok.com" OR "tunnel.jp.ngrok.com" OR "tunnel.in.ngrok.com" OR "*.ngrok.io")For Firewall Traffic
index=<your_firewall_index> ("3.20.27.198" OR "3.16.250.205" OR "3.12.62.205" OR "3.134.73.173" OR "3.133.228.214" OR "3.136.132.147" OR "3.123.83.158" OR "3.125.234.140" OR "52.28.187.147" OR "3.122.29.226" OR "13.228.59.63" OR "18.141.102.200" OR "13.251.162.108" OR "52.220.69.60" OR "52.220.126.110" OR "54.153.228.243" OR "13.239.180.227" OR "13.54.73.251" OR "3.105.185.27" OR "3.104.168.138" OR "18.229.114.140" OR "18.229.94.125" OR "54.233.161.49" OR "18.229.186.234" OR "18.228.107.150" OR "52.196.202.158" OR "54.178.247.185" OR "18.177.129.29" OR "13.112.247.114" OR "18.177.245.43" OR "13.126.63.42" OR "13.232.212.61" OR "13.232.27.141" OR "3.6.96.240" OR "13.233.205.122")The above IPs are obtained from the source link https://s3.amazonaws.com/dns.ngrok.com/tunnel.json and the Ngrok services are hosted in Amazon as public info https://www.abuseipdb.com/whois/ngrok.com
Defender for Endpoint:
For Endpoint Process Execution
DeviceProcessEvents | where ((ProcessCommandLine contains " tcp 139" or ProcessCommandLine contains " tcp 445" or ProcessCommandLine contains " tcp 3389" or ProcessCommandLine contains " tcp 5985" or ProcessCommandLine contains " tcp 5986") or (ProcessCommandLine contains " start " and ProcessCommandLine contains "--all" and ProcessCommandLine contains "--config" and ProcessCommandLine contains ".yml") or ((FolderPath endswith "ngrok.exe") and (ProcessCommandLine contains " tcp " or ProcessCommandLine contains " http " or ProcessCommandLine contains " authtoken ")))Identifying the Number of devices that groups Process Commandline, Parent Filename, Remote IP, etc.
union DeviceEvents,DeviceProcessEvents,DeviceFileEvents,DeviceNetworkEvents
| where FileName has "ngrok" or InitiatingProcessCommandLine has "ngrok" or ProcessCommandLine has "ngrok" or InitiatingProcessParentFileName has "ngrok"
| summarize Folderpath=make_set(FolderPath), ProcessCommandLine=make_set(ProcessCommandLine), InitiatingProcessCommandLine=make_set(InitiatingProcessCommandLine), InitiatingProcessParentFileName=make_set(InitiatingProcessParentFileName), Filename=make_set(FileName), PreviousFileName=make_set(PreviousFileName), PreviousFolderPath=make_set(PreviousFolderPath), ProcessVersionInfoInternalFileName=make_set(ProcessVersionInfoInternalFileName), ProcessVersionInfoOriginalFileName=make_set(ProcessVersionInfoOriginalFileName), ActionType=make_set(ActionType), RemoteIP = make_set(RemoteIP ), RemoteUrl=make_set(RemoteUrl), FileOriginUrl=make_set(FileOriginUrl), FileOriginReferrerUrl = make_set(FileOriginReferrerUrl), FileOriginIP = make_set(FileOriginIP) by DeviceNameCrowdstrike:
For Process Execution
((CommandLine="* tcp 139*" OR CommandLine="* tcp 445*" OR CommandLine="* tcp 3389*" OR CommandLine="* tcp 5985*" OR CommandLine="* tcp 5986*") AND (CommandLine="* start *" AND CommandLine="*--all*" AND CommandLine="*--config*" AND CommandLine="*.yml*") AND ((ImageFileName="*ngrok.exe") AND (CommandLine="* tcp *" OR CommandLine="* http *" OR CommandLine="* authtoken *")))Conclusion
Hackers, as usual, take advantage of a utility’s legitimate function and repurpose it for nefarious purposes. While Ngrok has been used by undesirable actors in the past.
Any open access to any graphical-interface remote control, such as public-facing RDP, could be disastrous for a business. Hackers utilize it for persistence in this scenario, but they can also use it to continue their campaign, exfiltrate data, perhaps do more lateral movement, and more. After all, it is remote access. On the open Internet, command and control with a full desktop session is waiting for hackers anywhere in the world.
References:
- https://www.huntress.com/blog/abusing-ngrok-hackers-at-the-end-of-the-tunnel
- https://blog.cyble.com/2021/02/15/ngrok-platform-abused-by-hackers-to-deliver-a-new-wave-of-phishing-attacks/
- https://c99.sh/hunting-ngrok-activity/
- https://www.youtube.com/watch?v=pR2qNnVIuKE
- https://www.softwaretestinghelp.com/ngrok-introduction/
- https://danielmiessler.com/study/ngrok/
- https://bytexd.com/ngrok-tutorial-for-beginners/
- https://www.endtoend.ai/tutorial/ngrok-ssh-forwarding/
- http://myowntechshare.blogspot.com/2020/08/remote-desktop-over-internet-without.html



































