Last article we can see the Windows Event ID 5379 to Detect Malicious Password-Protected File unlock which is the windows native compression to detect use cases like malware files are compressed with passwords that are used in a phishing campaign. In this article, we will cover a similar case with the WinRAR utility and its Sysmon Event ID for registry changes that are generated each time when a user opens the file with a valid password.
Also Read: Threat Hunting using Sysmon – Advanced Log Analysis for Windows
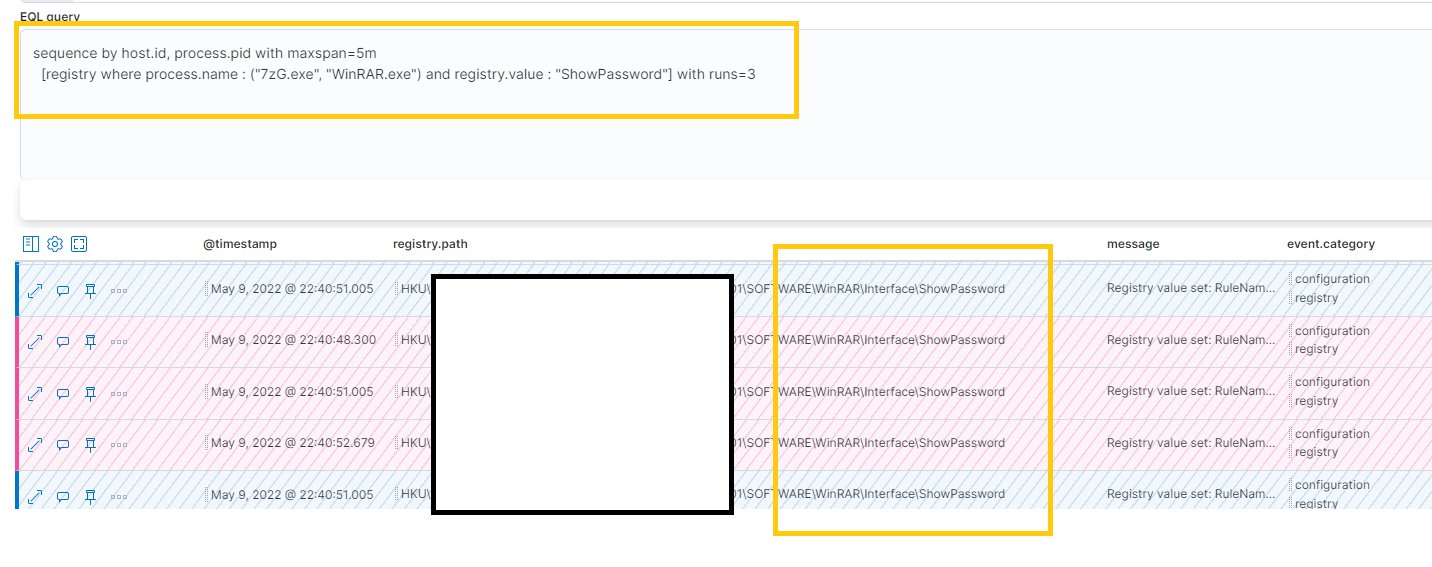
Attack Detection with Registry Changes
Example 1: Attack Detection Case
Security Researcher Samir says opening a password-protected archive WinRAR (GUI) will generate a registry modification event. In the registry navigate to the hive Computer\HKEY_CURRENT_USER\SOFTWARE\WinRAR where you will see the list of sub-keys. Check for interface with ShowPassword.
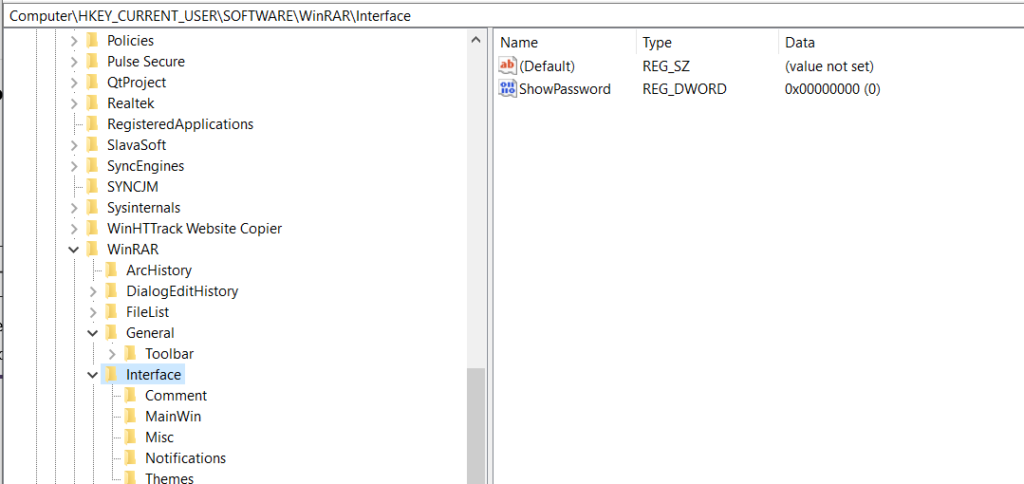
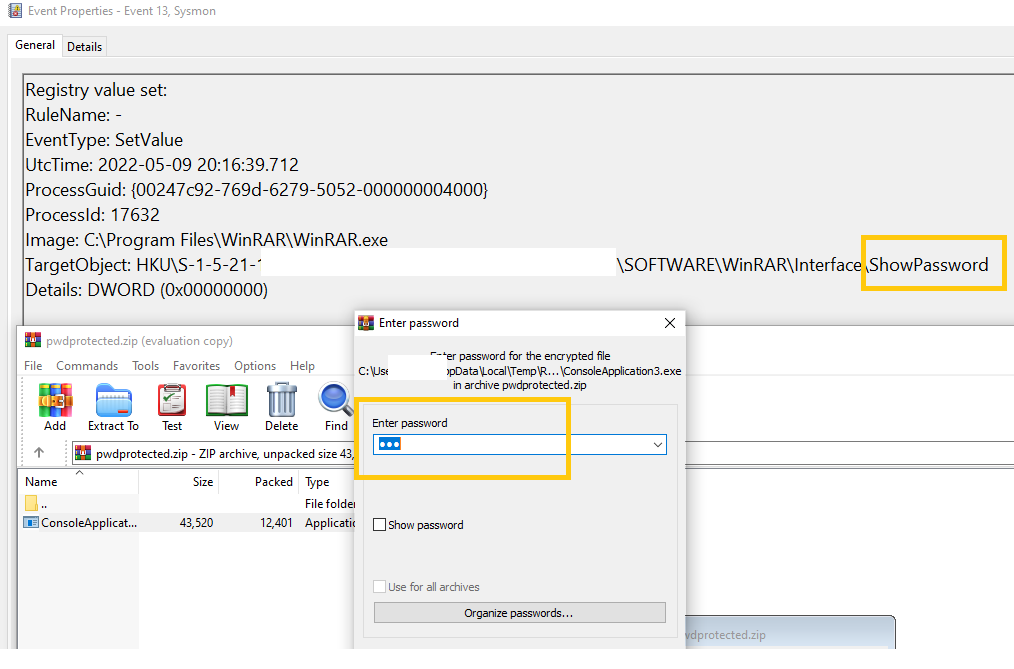
The above figures illustrate, that the WinRAR interface show password with REG_DWORD 0 means the user has entered the password, and the files are viewed. At this point, malware would have started the malicious actions on the machine.
Also Read: Logon Tracer – Investigate & Visualize Malicious Windows Logon
Example 2: Attack Detection Case
In your investigation, if you detect REG_DWORD 1 which is the indicator of the user is enabling the show password dialogue box in WinRAR to view the password in cleartext.
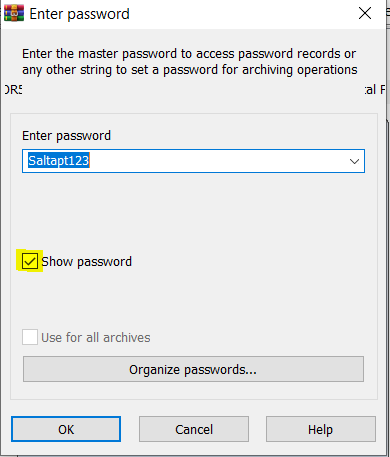
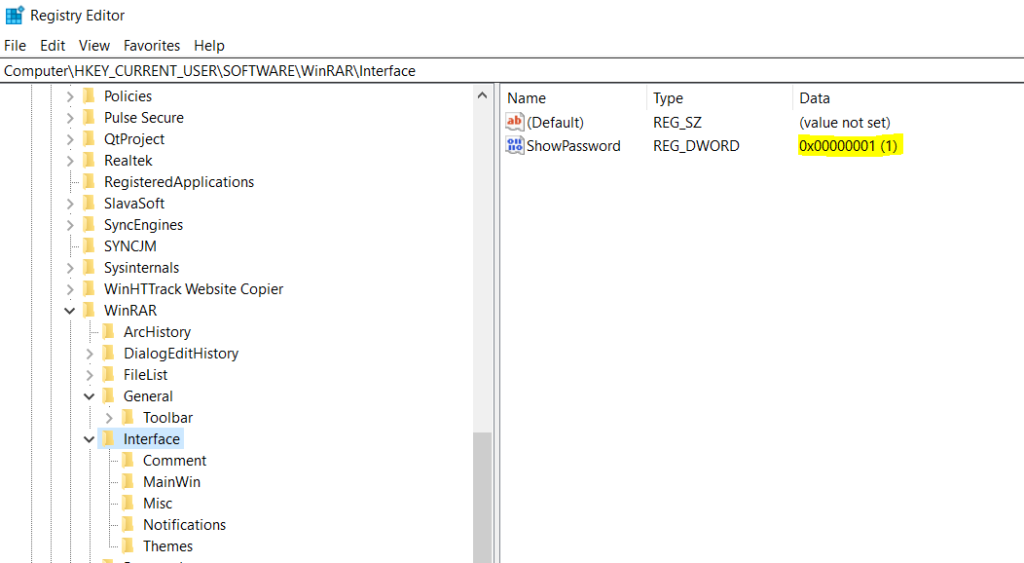
The above figures illustrate that REG_DWORD 1 is set in the registry when the user enables the show password. This is also a clear indicator of successful file access. If the user has closed the password prompt or opened an unprotected archive no event is generated.
A lot of those events from the same user could be suspicious like someone trying to open unauthorized password-protected archives.
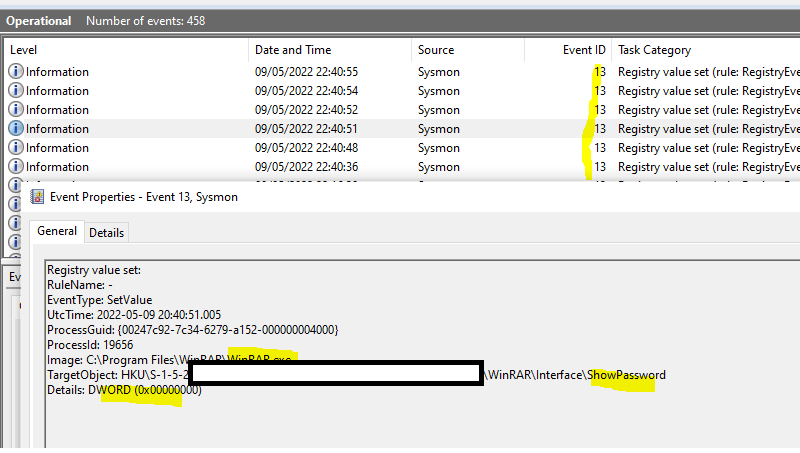
Sysmon Event ID to Monitor
Monitoring the Sysmon Event ID 13 identifies Registry value modifications. The event records the value written for Registry values of type DWORD and QWORD. Drilldown and check for the Image name and processID to conclude the user action.
Also Read: Densityscout – Entropy Analyzer for Threat Hunting and Incident Response
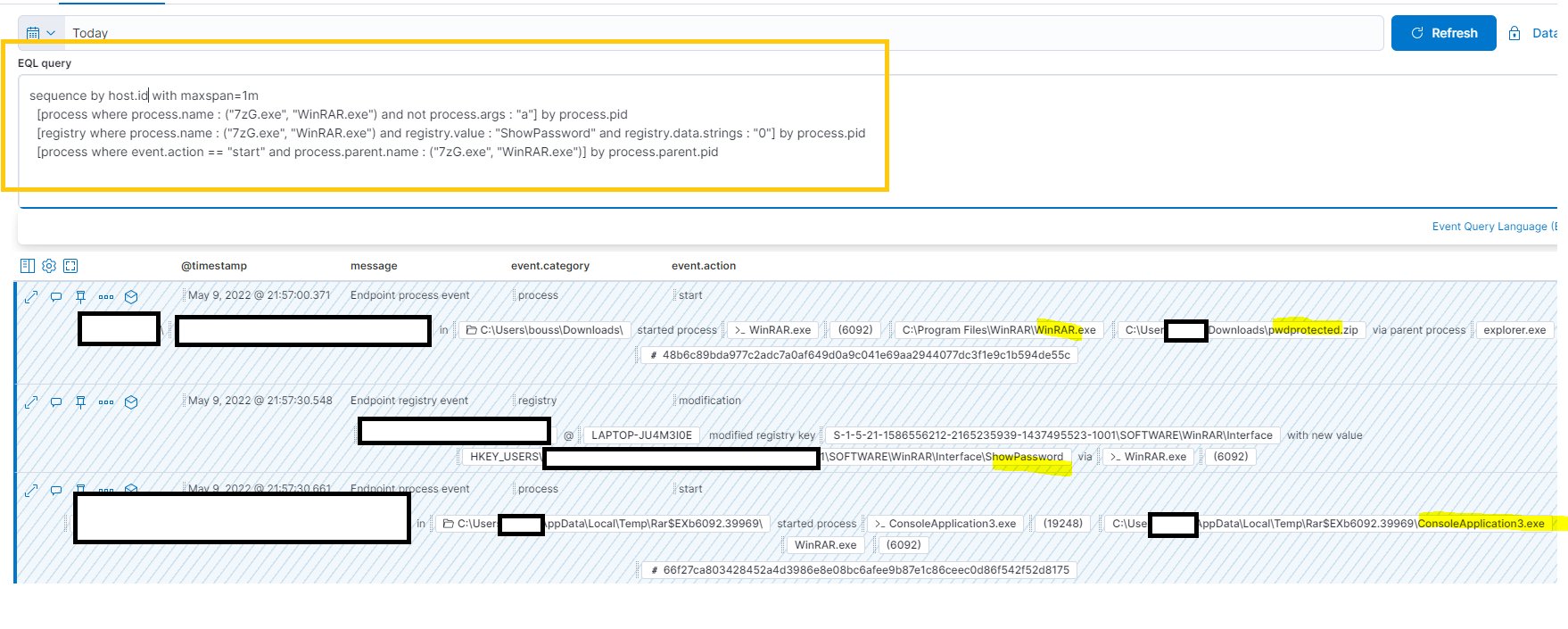
EQL Detection Query:
sequence by host.id with maxspan=1m
[process where process.name : ("7zG.exe", "WinRAR.exe") and not process.args : "a"] by process.pid
[registry where process.name : ("7zG.exe", "WinRAR.exe") and registry.value : "ShowPassword" and registry.data.strings : "0"] by process.pid
[process where event.action == "start" and process.parent.name : ("7zG.exe", "WinRAR.exe")] by process.parent.pid
Happy Hunting!
References/Source:
https://www.ultimatewindowssecurity.com/securitylog/encyclopedia/event.aspx?eventid=90013
https://gist.github.com/Samirbous/7124ced9828cf38645b793c4a747c5a3



































