In the last article, we have discussed a few Splunk commands which we used in daily searches to produce advanced results. Today we are going to see the “BIN” command which is effectively used while fine-tuning.
Also Read: Splunk Commands – Append , Chart and Dedup
BIN Command:
Description:
The bin command puts continuous numerical values into discrete sets i.e grouping the events by adjusting the value of <field> so that all the items in a particular set have the same value.
Syntax:
bin
[<bin-options>…]
<field> [AS <newfield>]
Example Query:
The below query detects an executable in the Windows folder accessing github.com. bin command to group all the users and process for 60 seconds interval. Consider the following timestamps.
(index=”sysmon”) EventCode=”3″ Image=”C:\\Windows\\*” (DestinationHostname=”*.github.com” OR DestinationHostname=”*.githubusercontent.com”)
| bin span=60s _time
| stats values(process_name) as process_name values(user) as user by _time
Results:
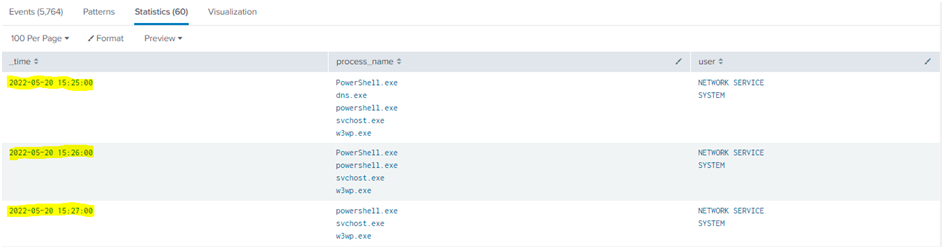
Explanation for bin query:
| bin span=60s _time
| stats values(process_name) as process_name values(user) as user by _time
The bin command will group all the data for 60 seconds with the selected fields ( Process_name and User ) in the Splunk query. The grouped data will aggregate with mentioned values over time.
For example, if we need to exclude GitHub connection initiating from a genuine process and the parent process is not in the alerting event. So, we can group all the events for a certain time like 1 min or 5 min as needed and after that, we can exclude them. JOIN and BIN commands will work in different scenarios. JOIN command can be used where we need to include different SourceType or Index logs to perform finetuning. But BIN can be only used within the same SourceType or Index.
Also Read: Splunk Commands – Field-value pair matching , Boolean and comparison , Operator and Wildcards
We have covered bin command and scenario to make our searches and finetuning effective. Let’s see the different commands in the next blog. Happy Hunting!!!!



































