A new zero-day Windows Search vulnerability can be used to automatically open a search window for remotely hosted malware executables simply by opening a Word document. Hackers can take advantage of this security issue because Windows supports a URI controller called search ms, which allows HTML programs and links to perform custom searches on devices.
Pass Your Next IT Certification Exam Fast with ExamSnap Website
While most Windows search queries look at local device code, remote hosts can query file sections and use a special search window title to force a Windows search.
Also Read: Latest Cyber Security News – Hacker News !
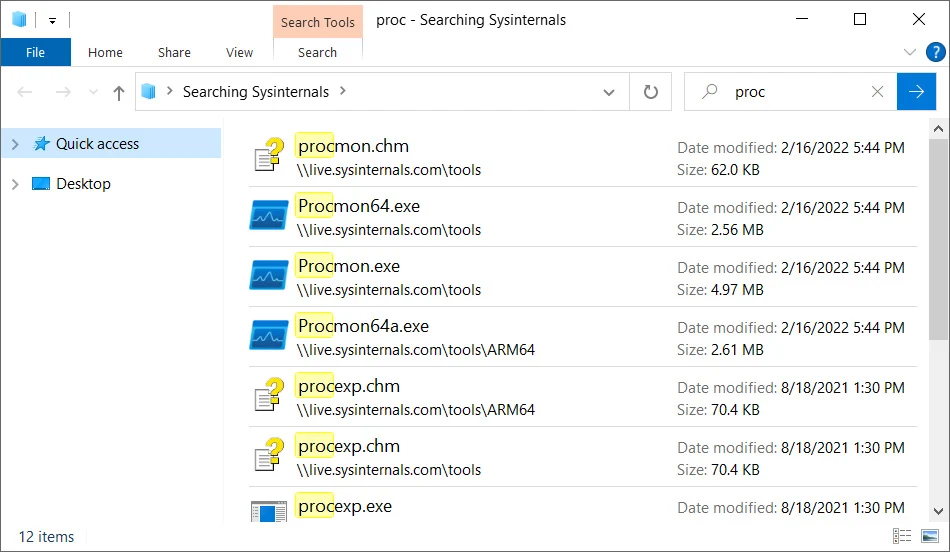
For example, the popular Sysinternals toolkit allows you to remotely mount live.sysinternals.com as a network share to run utilities. To search only in the list of files that match this remote share and the given name, you can use the following “search-ms” URI.
search-ms:query=proc&crumb=location:%5C%5Clive.sysinternals.com&displayname=Searching%20SysinternalsAs you can see from the command above, the ‘search-ms-variable’ crumb ‘specifies the search location, and the’ display name ‘variable specifies the search name.
Also Read: CVE-2022-30190 Detection Extended For Directory Traversal
A customized search window will appear when this command is executed from a Run dialog or web browser address bar on Windows 7, Windows 10, and Windows 11, as shown below.
Attackers can take a similar approach to malicious attacks when phishing emails are sent in such a way that they pretend they need security updates or installations. They can then set up a remote Windows section that can be used to host hidden malware such as security updates, and then add the ms-search URI to their links or phishing emails.
This was seen yesterday when Hickey converted existing Microsoft Word MSDT exploits to use the search-ms protocol handler we described earlier.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
By using this type of malicious Word document, threat actors can create elaborate phishing campaigns that automatically launch Windows Search windows on recipients’ devices to trick them into launching malware.
To mitigate this vulnerability, Hickey says you can use the same mitigation for ms-msdt exploits – delete the search-ms protocol handler from the Windows Registry.
- Run Command Prompt as Administrator.
- To back up the registry key, execute the command “reg export HKEY_CLASSES_ROOT\search-ms search-ms.reg“
- Execute the command “reg delete HKEY_CLASSES_ROOT\search-ms /f“
Detection Rules:
MDE:
DeviceProcessEvents | where ((InitiatingProcessFolderPath contains "WINWORD.EXE" or InitiatingProcessFolderPath contains "OUTLOOK.EXE") and (ProcessCommandLine contains "firefox.exe" or ProcessCommandLine contains "msedge.exe" or ProcessCommandLine contains "chrome.exe" or ProcessCommandLine contains "opera.exe") and (ProcessCommandLine contains "explorer.exe" or ProcessCommandLine contains "search-ms:query") and (FolderPath endswith ".html"))Qradar:SELECT UTF8(payload) from events where LOGSOURCETYPENAME(devicetype)='Microsoft Windows Security Event Log' and ("ParentImage" ilike '%WINWORD.EXE%' or "ParentImage" ilike '%OUTLOOK.EXE%') and ("Process CommandLine" ilike '%firefox.exe%' or "Process CommandLine" ilike '%msedge.exe%' or "Process CommandLine" ilike '%chrome.exe%' or "Process CommandLine" ilike '%opera.exe%') and ("Process CommandLine" ilike '%explorer.exe%' or "Process CommandLine" ilike '%search-ms:query%') and ("Filename" ilike '%.html')Elastic:(process.parent.executable:(*WINWORD.EXE* OR *OUTLOOK.EXE*) AND process.command_line:(*firefox.exe* OR *msedge.exe* OR *chrome.exe* OR *opera.exe*) AND process.command_line:(*explorer.exe* OR *search\-ms\:query*) AND file.path:*.html)Splunk:(source="WinEventLog:*" AND (ParentImage="*WINWORD.EXE*" OR ParentImage="*OUTLOOK.EXE*") AND (CommandLine="*firefox.exe*" OR CommandLine="*msedge.exe*" OR CommandLine="*chrome.exe*" OR CommandLine="*opera.exe*") AND (CommandLine="*explorer.exe*" OR CommandLine="*search-ms:query*") AND (FileName="*.html"))FireEye Helix:(metaclass:`windows` pprocess:[`WINWORD.EXE`,`OUTLOOK.EXE`] args:[`firefox.exe`,`msedge.exe`,`chrome.exe`,`opera.exe`] args:[`explorer.exe`,`search-ms:query`] filename:`*.html`)MS Sentinel:SecurityEvent | where EventID == 1 | where ((ParentProcessName contains 'WINWORD.EXE' or ParentProcessName contains 'OUTLOOK.EXE') and (CommandLine contains 'firefox.exe' or CommandLine contains 'msedge.exe' or CommandLine contains 'chrome.exe' or CommandLine contains 'opera.exe') and (CommandLine contains 'explorer.exe' or CommandLine contains 'search-ms:query') and (TargetFilename endswith '.html'))Windows Powershell:Get-WinEvent | where {(($_.message -match "ParentImage.*.*WINWORD.EXE.*" -or $_.message -match "ParentImage.*.*OUTLOOK.EXE.*") -and ($_.message -match "CommandLine.*.*firefox.exe.*" -or $_.message -match "CommandLine.*.*msedge.exe.*" -or $_.message -match "CommandLine.*.*chrome.exe.*" -or $_.message -match "CommandLine.*.*opera.exe.*") -and ($_.message -match "CommandLine.*.*explorer.exe.*" -or $_.message -match "CommandLine.*.*search-ms:query.*") -and ($_.message -match "FileName.*.*.html")) } | select TimeCreated,Id,RecordId,ProcessId,MachineName,MessageReference: https://www.bleepingcomputer.com/news/security/new-windows-search-zero-day-added-to-microsoft-protocol-nightmare/



































