Helminfosec explained the Weird Trick that blocks Password-Protected files in the Microsoft 365 and Exchange products. Threat actors deploying ransomware typically gain access to victims’ networks through either phishing emails that get them access to a victim’s computer or by exploiting external access like a vulnerable server or network device.
Figuring out ways to stop the tactics, techniques, and procedures (TTPs) used by the threat actors can help your organization be more prepared and resilient to ransomware and other attacks.
One common threat actor tactic is to send emails to victims with a password-protected file containing a payload. The email may also contain a password for the victim to use to open the password-protected file, or they may send it separately.
Another common ransomware access tool is IcedID, which until recently was often emailing encrypted zip files to deliver a Microsoft Word document containing a malicious macro.
During regular business, many users are not going to be sending or receiving password-protected emails. Many organizations now have file-sharing capabilities through services like Microsoft 365, Citrix ShareFile, Egnyte Platform, and Google Drive that allow users to share files securely without having to separately encrypt them. So blocking (or at the very least quarantining) these emails with password-protected attachments can have a positive impact on your organization’s cyber security posture with limited impact on the business.
If an organization is using Microsoft 365 or Exchange for its email platform, the Microsoft Exchange Admin Center can be used to block these password-protected documents easily. Google Workspace Gmail also provides an easy rule creation workflow to quarantine these messages.
Also Read: Windows Event ID 5379 to Detect Malicious Password-Protected File unlock
Microsoft 365 and Exchange
Within the Exchange Admin Center, go to the Mail Flow > Rules screen. Once there, you’ll be able to create a new rule:
Once you get to the Create New Rule screen (opens in a new pop-up window), open More Options to select the conditions to block.
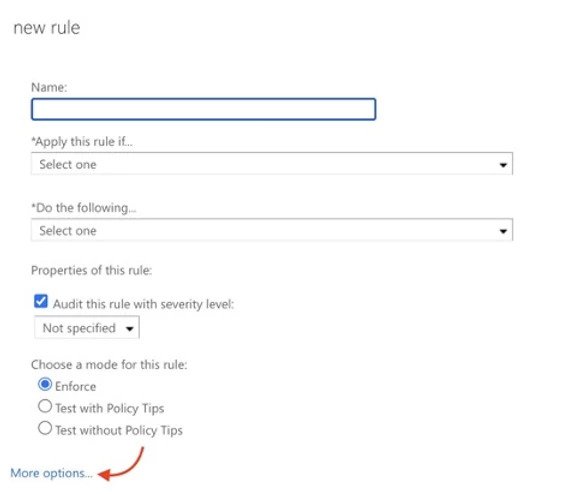
Depending on your organization’s processes, you may want to create separate rules for each of the content types being blocked. From the list of potential rules for attachments, there are four conditions to block based on the TTPs in this post:
- Content can’t be inspected
- Didn’t complete the scanning
- Has executable content
- Is password protected
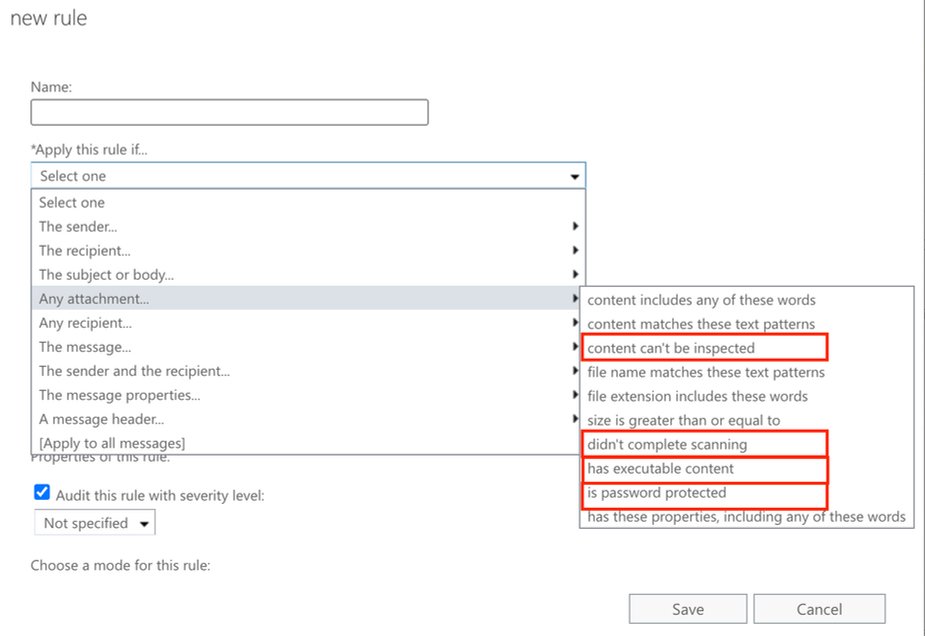
Once you select the condition, then select the action “deliver to hosted quarantine” and “stop processing more rules.”
After creating the rules, your Exchange Mail Flow rules should show the four rules.
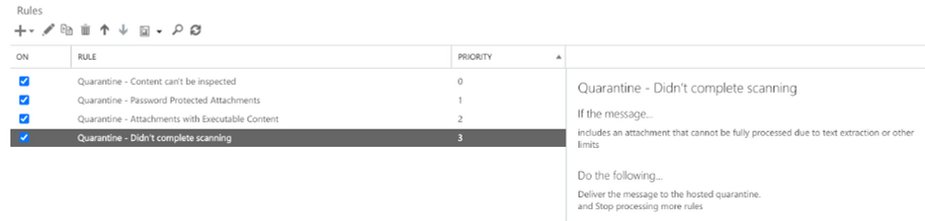
Also Read: Latest Cyber Security News – Hacker News !
Google Workspace Gmail
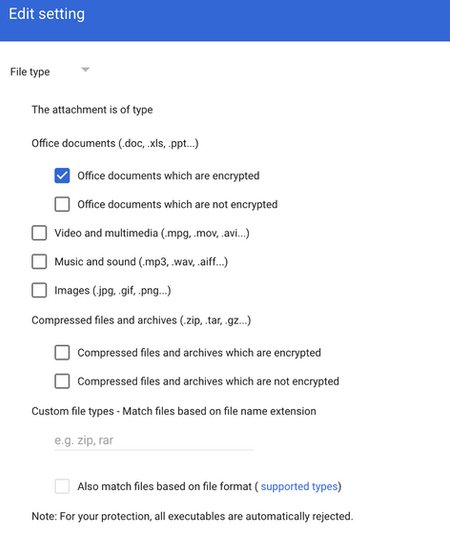
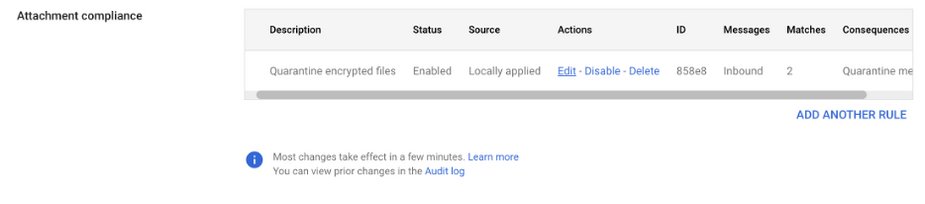
Within Gmail, administrators can block password-protected documents and compressed files. Once logged into the Google Workspace Admin Console, navigate to Apps > Google Workspace > Gmail > Compliance, then scroll down to Attachment compliance. Next, add a rule for inbound email messages. Create two expressions for conditions. The first condition would be Office documents which are encrypted, and the second condition is compressed files which are encrypted.
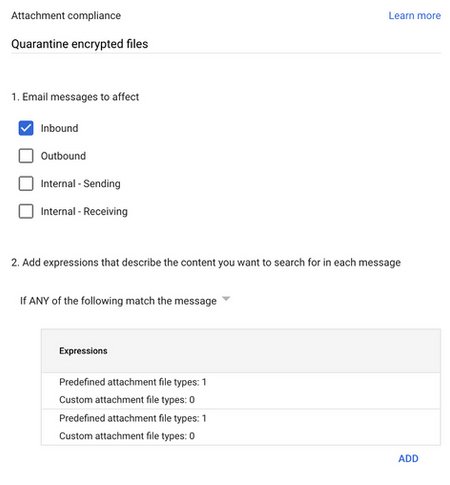
After configuring expressions, the rule should look like this:
After configuring the expressions, set the action in Step 3 to “Quarantine message” and scroll down to save.
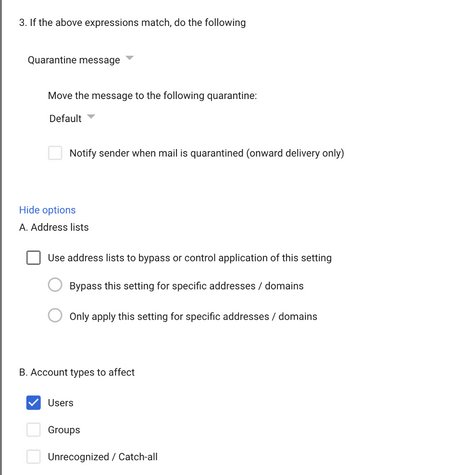
The attachment compliance rule will now look like this:
Also Read: Malspam with new Matanbuchus Loader – Detection & Response
Another compliance expression that can be added would be any compressed file (even if not encrypted). Email filtering “trick” can help your organization make itself more resilient to future phishing emails containing malware.
Source/Credits: https://www.helminfosec.com/post/one-weird-trick-blocking-password-protected-files-to-combat-ransomware



































