Hacking groups and ransomware operations are moving away from Cobalt Strike to the newer Brute Ratel post-exploitation toolkit to evade detection by EDR and antivirus solutions.
Researchers from Palo Alto Networks Unit 42 discovered that a sample uploaded to the VirusTotal database on May 19, 2022, and considered benign by almost all the antivirus, was containing a payload associated with Brute Ratel C4 (BRc4), a new red-teaming and adversarial attack simulation tool.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
Unlike Cobalt strike beacons, BRc4 payloads are less popular, but with similar capabilities. The tool was specifically designed to avoid detection by security solutions such as endpoint detection and response (EDR) and antivirus (AV). Its effectiveness at doing so can clearly be witnessed by the aforementioned lack of detection across vendors on VirusTotal.
Brute Ratel is the most advanced Red Team & Adversary Simulation Software in the current C2 Market. It can not only emulate different stages of an attacker kill-chain but also provide a systematic timeline and graph for each of the attacks executed to help the Security Operations Team validate the attacks and improve the internal defensive mechanisms.” reads the description of the tool on its website.
Brute Ratel comes prebuilt with several opsOpec features which can ease a Red Team’s task to focus more on the analytical part of an engagement instead of focusing or depending on Open source tools for post-exploitation. Brute Ratel is a post-exploitation C2 in the end and however does not provide exploit generation features like Metasploit or vulnerability scanning features like Nessus, Acunetix, or BurpSuite.
Attack Details:
The file was uploaded to VirusTotal on May 19, 2022, from Sri Lanka, it is named Roshan_CV.iso and poses as a curriculum vitae. Upon clicking on the ISO file, users are presented with an apparent harmless Word document, but after launching it the attack chain will start. An instance of the BRc4 is installed on the user’s machine and attempts to contact a remote server.
According to Unit42 experts, threat actors are spreading the ISO files via spear-phishing messages.
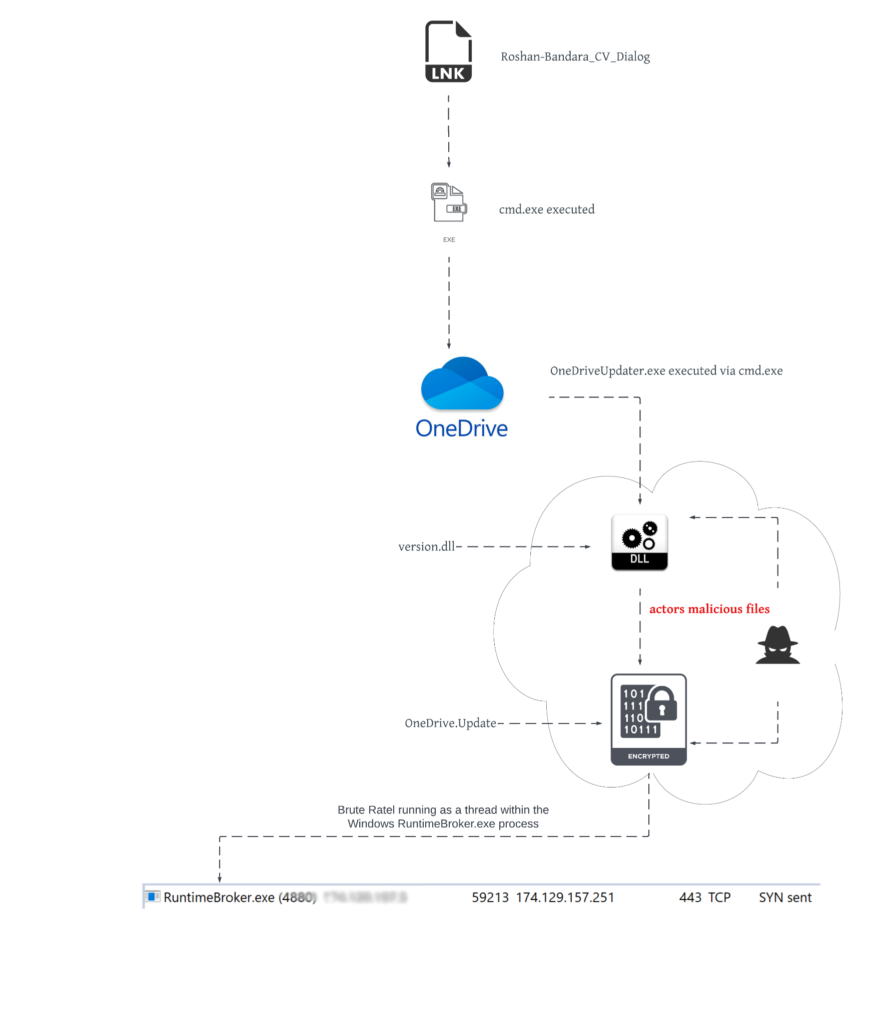
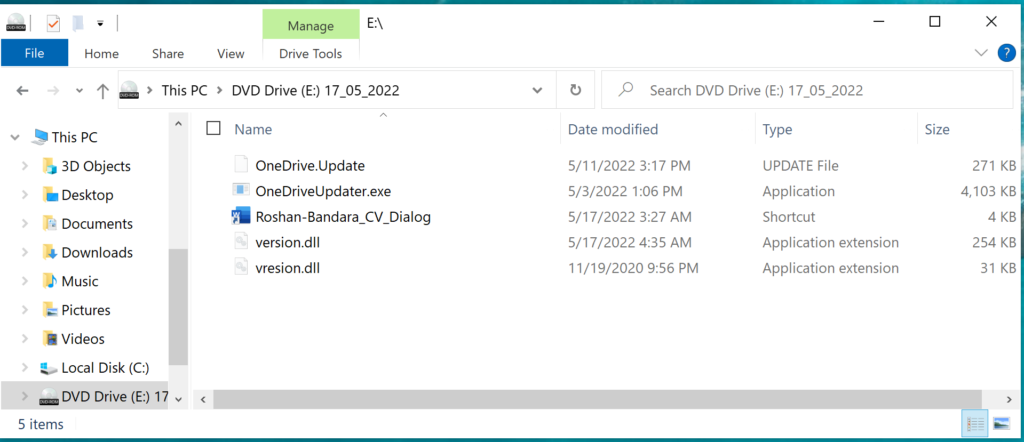
The delivery of packaged ISO files is typically sent via spear-phishing email campaigns, although it’s not clear if the same method was used to deliver the payload to the target environment.
However, the ‘Roshan-Bandara_CV_Dialog’ résumé file is actually a Windows shortcut that will launch the bundled OneDriveUpdater.exe file, as shown in the file’s properties below.
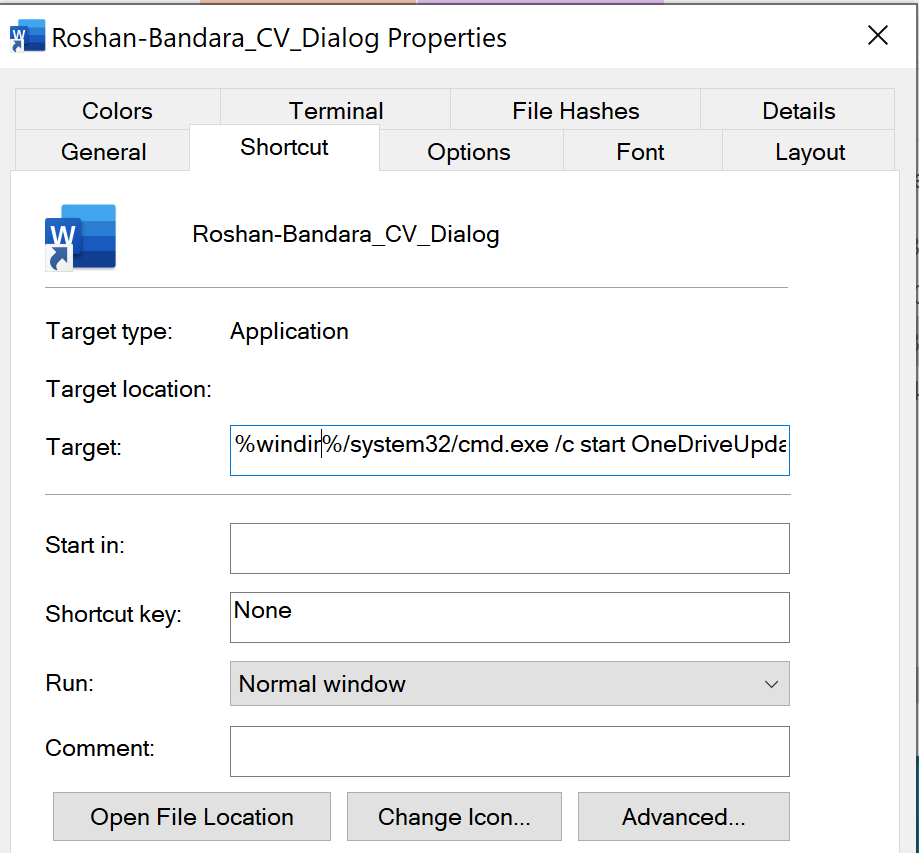
While OneDriveUpdater.exe is a legitimate Microsoft executable, the included version.dll that is loaded by the program has been modified to act as a loader for a Brute Ratel badger, which is loaded into the RuntimeBroker.exe process.
The experts noticed that the composition of the ISO file, Roshan_CV.ISO, is highly compatible with TTP associated with the Russia-linked APT29 group.
“The composition of the ISO file, Roshan_CV.ISO, closely resembles that of another nation-state APT tradecraft. The following table shows a side-by-side comparison of Roshan_CV.ISO and that of a previously identified APT29 sample (Decret.ISO).” reads the analysis published by Palo Alto Networks.
The researchers also spotted a second sample that was uploaded to VirusTotal from Ukraine a day after the Roshan_CV.ISO file was uploaded. The experts observed significant code overlaps of a module used to load BRc4 into memory. Further investigation allowed the researchers to discover seven more BRc4 samples dating back to February 2021.
The analysis of the C2 server allowed the experts to identify a number of potential victims, including an Argentinian organization, an IP television provider providing North and South American content, and a major textile manufacturer in Mexico.
“The emergence of a new penetration testing and adversary emulation capability is significant. Yet more alarming is the effectiveness of BRc4 at defeating modern defensive EDR and AV detection capabilities.
Indicator Of Compromise:
Brute Ratel C4 ISO Samples:
1FC7B0E1054D54CE8F1DE0CC95976081C7A85C7926C03172A3DDAA672690042C
X64 Brute Ratel C4 Windows Kernel Module:
31ACF37D180AB9AFBCF6A4EC5D29C3E19C947641A2D9CE3CE56D71C1F576C069
X64 Brute Ratel C4 Samples:
3ED21A4BFCF9838E06AD3058D13D5C28026C17DC996953A22A00F0609B0DF3B9
3AD53495851BAFC48CAF6D2227A434CA2E0BEF9AB3BD40ABFE4EA8F318D37BBE
973F573CAB683636D9A70B8891263F59E2F02201FFB4DD2E9D7ECBB1521DA03E
DD8652E2DCFE3F1A72631B3A9585736FBE77FFABEE4098F6B3C48E1469BF27AA
E1A9B35CF1378FDA12310F0920C5C53AD461858B3CB575697EA125DFEE829611
EF9B60AA0E4179C16A9AC441E0A21DC3A1C3DC04B100EE487EABF5C5B1F571A6
D71DC7BA8523947E08C6EEC43A726FE75AED248DFD3A7C4F6537224E9ED05F6F
5887C4646E032E015AA186C5970E8F07D3ED1DE8DBFA298BA4522C89E547419B
Malicious DLLs:
EA2876E9175410B6F6719F80EE44B9553960758C7D0F7BED73C0FE9A78D8E669
Malicious Encrypted Payloads:
B5D1D3C1AEC2F2EF06E7D0B7996BC45DF4744934BD66266A6EBB02D70E35236E
X.509 Cert SHA1s:
55684a30a47476fce5b42cbd59add4b0fbc776a3
66aab897e33b3e4d940c51eba8d07f5605d5b275
Infrastructure linked to X.509 Certs or Samples:
104.6.92[.]229
137.184.199[.]17
138.68.50[.]218
138.68.58[.]43
139.162.195[.]169
139.180.187[.]179
147.182.247[.]103
149.154.100[.]151
15.206.84[.]52
159.223.49[.]16
159.65.186[.]50
162.216.240[.]61
172.105.102[.]247
172.81.62[.]82
174.129.157[.]251
178.79.143[.]149
178.79.168[.]110
178.79.172[.]35
18.133.26[.]247
18.130.233[.]249
18.217.179[.]8
18.236.92[.]31
185.138.164[.]112
194.29.186[.]67
194.87.70[.]14
213.168.249[.]232
3.110.56[.]219
3.133.7[.]69
31.184.198[.]83
34.195.122[.]225
34.243.172[.]90
35.170.243[.]216
45.144.225[.]3
45.76.155[.]71
45.79.36[.]192
52.48.51[.]67
52.90.228[.]203
54.229.102[.]30
54.90.137[.]213
89.100.107[.]65
92.255.85[.]173
92.255.85[.]44
94.130.130[.]43
ds.windowsupdate.eu[.]org
Detection & Response:
Splunk:
(((Image="*\\cmd.exe") AND CommandLine="*C:\\Users\\*" AND CommandLine="*.lnk*" AND CommandLine="*cmd /c*" AND CommandLine="*\\Admin\\AppData\\Local\\Temp\\*" AND CommandLine="*\\AppData\\Local\\Temp\\*" AND (CommandLine="*C:\\Windows\\system32\\cmd.exe*" OR CommandLine="*/c*" OR CommandLine="*start*" OR CommandLine="*OneDriveUpdater.exe*")) OR (Image="*\\OneDriveUpdater.exe" AND (CommandLine="*C:\\Users\\Admin\\AppData\\Local\\Temp\\*" OR CommandLine="*VERSION.dll*" OR CommandLine="*vresion.DLL*" OR CommandLine="*OneDrive.Update*"))) AND source="WinEventLog:*"Qradar:
SELECT UTF8(payload) from events where LOGSOURCETYPENAME(devicetype)='Microsoft Windows Security Event Log' and ((("Image" ilike '%\cmd.exe') and "Process CommandLine" ilike '%C:\Users\%' and "Process CommandLine" ilike '%.lnk%' and "Process CommandLine" ilike '%cmd /c%' and "Process CommandLine" ilike '%\Admin\AppData\Local\Temp\%' and "Process CommandLine" ilike '%\AppData\Local\Temp\%' and ("Process CommandLine" ilike '%C:\Windows\system32\cmd.exe%' or "Process CommandLine" ilike '%/c%' or "Process CommandLine" ilike '%start%' or "Process CommandLine" ilike '%OneDriveUpdater.exe%')) or ("Image" ilike '%\OneDriveUpdater.exe' and ("Process CommandLine" ilike '%C:\Users\Admin\AppData\Local\Temp\%' or "Process CommandLine" ilike '%VERSION.dll%' or "Process CommandLine" ilike '%vresion.DLL%' or "Process CommandLine" ilike '%OneDrive.Update%')))Elastic Query:
((process.executable:*\\cmd.exe AND process.command_line:*C\:\\Users\\* AND process.command_line:*.lnk* AND process.command_line:*cmd\ \/c* AND process.command_line:*\\Admin\\AppData\\Local\\Temp\\* AND process.command_line:*\\AppData\\Local\\Temp\\* AND process.command_line:(*C\:\\Windows\\system32\\cmd.exe* OR *\/c* OR *start* OR *OneDriveUpdater.exe*)) OR (process.executable:*\\OneDriveUpdater.exe AND process.command_line:(*C\:\\Users\\Admin\\AppData\\Local\\Temp\\* OR *VERSION.dll* OR *vresion.DLL* OR *OneDrive.Update*)))Arcsight:
(((((destinationProcessName CONTAINS "*\\cmd.exe" OR sourceProcessName CONTAINS "*\\cmd.exe" OR deviceProcessName CONTAINS "*\\cmd.exe")) AND (((deviceCustomString1 CONTAINS "*C:\\Users\\\\*" OR destinationServiceName CONTAINS "*C:\\Users\\\\*")) AND ((deviceCustomString1 CONTAINS "*.lnk*" OR destinationServiceName CONTAINS "*.lnk*")) AND ((deviceCustomString1 CONTAINS "*cmd /c*" OR destinationServiceName CONTAINS "*cmd /c*")) AND ((deviceCustomString1 CONTAINS "*\\Admin\\AppData\\Local\\Temp\\\\*" OR destinationServiceName CONTAINS "*\\Admin\\AppData\\Local\\Temp\\\\*")) AND ((deviceCustomString1 CONTAINS "*\\AppData\\Local\\Temp\\\\*" OR destinationServiceName CONTAINS "*\\AppData\\Local\\Temp\\\\*"))) AND ((destinationProcessName CONTAINS "*\\cmd.exe" OR sourceProcessName CONTAINS "*\\cmd.exe" OR deviceProcessName CONTAINS "*\\cmd.exe")) AND ((deviceCustomString1 CONTAINS "*C:\\Windows\\system32\\cmd.exe*" OR deviceCustomString1 CONTAINS "*/c*" OR deviceCustomString1 CONTAINS "*start*" OR deviceCustomString1 CONTAINS "*OneDriveUpdater.exe*" OR destinationServiceName CONTAINS "*C:\\Windows\\system32\\cmd.exe*" OR destinationServiceName CONTAINS "*/c*" OR destinationServiceName CONTAINS "*start*" OR destinationServiceName CONTAINS "*OneDriveUpdater.exe*"))) OR (((destinationProcessName ENDSWITH "*\\OneDriveUpdater.exe" OR sourceProcessName ENDSWITH "*\\OneDriveUpdater.exe" OR deviceProcessName ENDSWITH "*\\OneDriveUpdater.exe")) AND ((deviceCustomString1 CONTAINS "*C:\\Users\\Admin\\AppData\\Local\\Temp\\\\*" OR deviceCustomString1 CONTAINS "*VERSION.dll*" OR deviceCustomString1 CONTAINS "*vresion.DLL*" OR deviceCustomString1 CONTAINS "*OneDrive.Update*" OR destinationServiceName CONTAINS "*C:\\Users\\Admin\\AppData\\Local\\Temp\\\\*" OR destinationServiceName CONTAINS "*VERSION.dll*" OR destinationServiceName CONTAINS "*vresion.DLL*" OR destinationServiceName CONTAINS "*OneDrive.Update*")))))CarbonBlack:
((process_name:*\\cmd.exe AND process_cmdline:*C\:\\Users\\* AND process_cmdline:*.lnk* AND process_cmdline:*cmd\ \/c* AND process_cmdline:*\\Admin\\AppData\\Local\\Temp\\* AND process_cmdline:*\\AppData\\Local\\Temp\\* AND process_cmdline:(*C\:\\Windows\\system32\\cmd.exe* OR *\/c* OR *start* OR *OneDriveUpdater.exe*)) OR (process_name:*\\OneDriveUpdater.exe AND process_cmdline:(*C\:\\Users\\Admin\\AppData\\Local\\Temp\\* OR *VERSION.dll* OR *vresion.DLL* OR *OneDrive.Update*)))Crowdstike:
(((ImageFileName="*\\cmd.exe") AND ((CommandLine="*C:\\Users\\*" OR CommandHistory="*C:\\Users\\*") AND (CommandLine="*.lnk*" OR CommandHistory="*.lnk*") AND (CommandLine="*cmd /c*" OR CommandHistory="*cmd /c*") AND (CommandLine="*\\Admin\\AppData\\Local\\Temp\\*" OR CommandHistory="*\\Admin\\AppData\\Local\\Temp\\*") AND (CommandLine="*\\AppData\\Local\\Temp\\*" OR CommandHistory="*\\AppData\\Local\\Temp\\*")) AND ((CommandLine="*C:\\Windows\\system32\\cmd.exe*" OR CommandLine="*/c*" OR CommandLine="*start*" OR CommandLine="*OneDriveUpdater.exe*") OR (CommandHistory="*C:\\Windows\\system32\\cmd.exe*" OR CommandHistory="*/c*" OR CommandHistory="*start*" OR CommandHistory="*OneDriveUpdater.exe*"))) OR (ImageFileName="*\\OneDriveUpdater.exe" AND ((CommandLine="*C:\\Users\\Admin\\AppData\\Local\\Temp\\*" OR CommandLine="*VERSION.dll*" OR CommandLine="*vresion.DLL*" OR CommandLine="*OneDrive.Update*") OR (CommandHistory="*C:\\Users\\Admin\\AppData\\Local\\Temp\\*" OR CommandHistory="*VERSION.dll*" OR CommandHistory="*vresion.DLL*" OR CommandHistory="*OneDrive.Update*"))))FireEye:
(metaclass:`windows` ((process:`*\cmd.exe` args:`C:\Users\\` args:`.lnk` args:`cmd /c` args:`\Admin\AppData\Local\Temp\\` args:`\AppData\Local\Temp\\` args:[`C:\Windows\system32\cmd.exe`,`/c`,`start`,`OneDriveUpdater.exe`]) OR (process:`*\OneDriveUpdater.exe` args:[`C:\Users\Admin\AppData\Local\Temp\\`,`VERSION.dll`,`vresion.DLL`,`OneDrive.Update`])))Google Chronicle:
((target.process.file.full_path = /.*\\cmd\.exe$/ and target.process.command_line = /.*C:\\Users.*/ and target.process.command_line = /.*\.lnk.*/ and target.process.command_line = /.*cmd \/c.*/ and target.process.command_line = /.*\\Admin\\AppData\\Local\\Temp.*/ and target.process.command_line = /.*\\AppData\\Local\\Temp.*/ and (target.process.command_line = /.*C:\\Windows\\system32\\cmd\.exe.*/ or target.process.command_line = /.*\/c.*/ or target.process.command_line = /.*start.*/ or target.process.command_line = /.*OneDriveUpdater\.exe.*/)) or (target.process.file.full_path = /.*\\OneDriveUpdater\.exe$/ and (target.process.command_line = /.*C:\\Users\\Admin\\AppData\\Local\\Temp.*/ or target.process.command_line = /.*VERSION\.dll.*/ or target.process.command_line = /.*vresion\.DLL.*/ or target.process.command_line = /.*OneDrive\.Update.*/)))GrayLog:
((Image.keyword:*\\cmd.exe AND CommandLine.keyword:*C\:\\Users\\* AND CommandLine.keyword:*.lnk* AND CommandLine.keyword:*cmd\ \/c* AND CommandLine.keyword:*\\Admin\\AppData\\Local\\Temp\\* AND CommandLine.keyword:*\\AppData\\Local\\Temp\\* AND CommandLine.keyword:(*C\:\\Windows\\system32\\cmd.exe* *\/c* *start* *OneDriveUpdater.exe*)) OR (Image.keyword:*\\OneDriveUpdater.exe AND CommandLine.keyword:(*C\:\\Users\\Admin\\AppData\\Local\\Temp\\* *VERSION.dll* *vresion.DLL* *OneDrive.Update*)))Logpoint:
((Image IN "*\\cmd.exe" CommandLine="*C:\\Users\\*" CommandLine="*.lnk*" CommandLine="*cmd /c*" CommandLine="*\\Admin\\AppData\\Local\\Temp\\*" CommandLine="*\\AppData\\Local\\Temp\\*" CommandLine IN ["*C:\\Windows\\system32\\cmd.exe*", "*/c*", "*start*", "*OneDriveUpdater.exe*"]) OR (Image="*\\OneDriveUpdater.exe" CommandLine IN ["*C:\\Users\\Admin\\AppData\\Local\\Temp\\*", "*VERSION.dll*", "*vresion.DLL*", "*OneDrive.Update*"]))Microsoft Defender:
DeviceProcessEvents | where (((FolderPath endswith @"\cmd.exe") and ProcessCommandLine contains @"C:\Users\" and ProcessCommandLine contains ".lnk" and ProcessCommandLine contains "cmd /c" and ProcessCommandLine contains @"\Admin\AppData\Local\Temp\" and ProcessCommandLine contains @"\AppData\Local\Temp\" and (ProcessCommandLine contains @"C:\Windows\system32\cmd.exe" or ProcessCommandLine contains "/c" or ProcessCommandLine contains "start" or ProcessCommandLine contains "OneDriveUpdater.exe")) or (FolderPath endswith @"\OneDriveUpdater.exe" and (ProcessCommandLine contains @"C:\Users\Admin\AppData\Local\Temp\" or ProcessCommandLine contains "VERSION.dll" or ProcessCommandLine contains "vresion.DLL" or ProcessCommandLine contains "OneDrive.Update")))Microsoft Sentinel:
SecurityEvent | where EventID == 4688 | where (((NewProcessName endswith @'\cmd.exe') and CommandLine contains @'C:\Users\' and CommandLine contains '.lnk' and CommandLine contains 'cmd /c' and CommandLine contains @'\Admin\AppData\Local\Temp\' and CommandLine contains @'\AppData\Local\Temp\' and (CommandLine contains @'C:\Windows\system32\cmd.exe' or CommandLine contains '/c' or CommandLine contains 'start' or CommandLine contains 'OneDriveUpdater.exe')) or (NewProcessName endswith @'\OneDriveUpdater.exe' and (CommandLine contains @'C:\Users\Admin\AppData\Local\Temp\' or CommandLine contains 'VERSION.dll' or CommandLine contains 'vresion.DLL' or CommandLine contains 'OneDrive.Update')))RSA Netwitness:
(((Image contains '\cmd\.exe') && (CommandLine contains 'C:\Users\\') && (CommandLine contains '.lnk') && (CommandLine contains 'cmd /c') && (CommandLine contains 'Admin\AppData\Local\Temp\\') && (CommandLine contains 'AppData\Local\Temp\\') && (CommandLine contains 'C:\\Windows\\system32\\cmd\.exe', '/c', 'start', 'OneDriveUpdater\.exe')) || ((Image contains 'OneDriveUpdater.exe') && (CommandLine contains 'C:\\Users\\Admin\\AppData\\Local\\Temp\\\', 'VERSION\.dll', 'vresion\.DLL', 'OneDrive\.Update')))Sumologic:
(_sourceCategory=*windows* AND ((((Image = "*\cmd.exe") AND CommandLine="*C:\Users\\*" AND CommandLine="*.lnk*" AND CommandLine="*cmd /c*" AND CommandLine="*\Admin\AppData\Local\Temp\\*" AND CommandLine="*\AppData\Local\Temp\\*" AND (CommandLine = "*C:\Windows\system32\cmd.exe*" OR CommandLine = "*/c*" OR CommandLine = "*start*" OR CommandLine = "*OneDriveUpdater.exe*")) OR (Image="*\OneDriveUpdater.exe" AND (CommandLine = "*C:\Users\Admin\AppData\Local\Temp\\*" OR CommandLine = "*VERSION.dll*" OR CommandLine = "*vresion.DLL*" OR CommandLine = "*OneDrive.Update*")))))Source/References: ht://securityaffairs.co/wordpress/132922/hacking/brc4-used-in-attacks.html
https://unit42.paloaltonetworks.com/brute-ratel-c4-tool/
hts://www.bleepingcomputer.com/news/security/ransomware-hacking-groups-move-from-cobalt-strike-to-brute-ratel/



































