HTML smuggling has been used in targeted, spear-phishing email campaigns that deliver banking Trojans (such as Mekotio), remote access Trojans (RATs) like AsyncRAT/NJRAT, and Trickbot. These are malware that aid threat actors in gaining control of affected devices and delivering ransomware or other payloads.
MSTIC said the technique was used in a spear-phishing attack by the notorious NOBELIUM, the threat actor behind the noteworthy, nation-state cyberattack on SolarWinds.
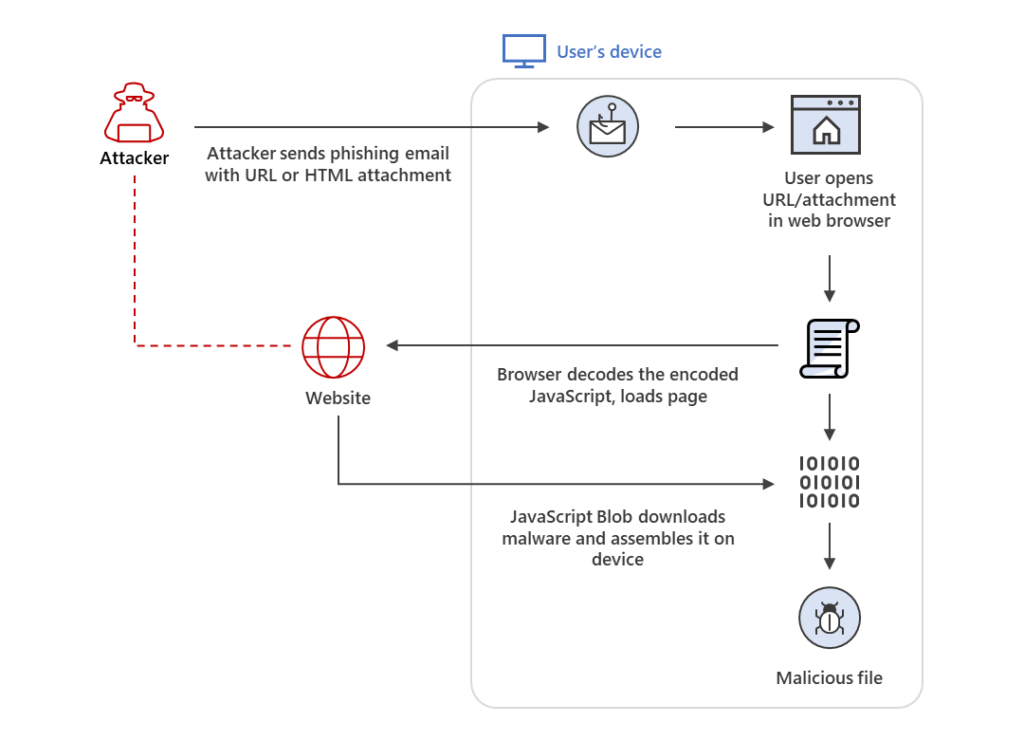
How HTML smuggling works
What is HTML smuggling?
HTML smuggling got its name from the way attackers smuggle in or hide an encoded malicious JavaScript blob within an HTML email attachment. Once a user receives the email and opens this attachment, their browser decodes the malformed script, which then assembles the malware payload onto the affected computer or host device.
Usually, malware payloads go through the network when someone opens a malicious attachment or clicks a malicious link. In this case, the malware payload is created within the host. This means that it bypasses email filters, which usually look for malicious attachments.
HTML smuggling is a particular threat to an organization’s network because it bypasses customary security mitigation settings aimed at filtering content. Even if, for example, an organization has disabled the automatic execution of JavaScript within its environment—this could stop the JavaScript blob from running—it can still be affected by HTML smuggling as there are multiple ways to implement it. According to MSTIC, obfuscation and the many ways JavaScript can be coded could evade conventional JavaScript filters.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
HTML smuggling isn’t new, but MSTIC notes that many cybercriminals are embracing its use in their own attack campaigns. “Such adoption shows how tactics, techniques, and procedures (TTPs) trickle down from cybercrime gangs to malicious threat actors and vice versa … It also reinforces the current state of the underground economy, where such TTPs get commoditized when deemed effective.”
Some ransomware gangs have already started using this new delivery mechanism, and this could be early signs of a fledgling trend. Even organizations confident with their perimeter security are called to double back and take mitigation steps to detect and block phishing attempts that could involve HTML smuggling. As we can see, disabling JavaScript is no longer enough.
Staying secure against HTML smuggling attacks
A layered approach to security is needed to successfully defend against HTML smuggling. Microsoft suggests killing the attack chain before it even begins. Start off by checking for common characteristics of HTML smuggling campaigns by applying behavior rules that look for:
- an HTML file containing the suspicious script
- an HTML file that obfuscates a JS
- an HTML file that decodes a Base64 JS script
- a ZIP file email attachment containing JS
- a password-protected attachment
Organizations should also configure their endpoint security products to block:
- JavaScript or VBScript from automatically running a downloaded executable file
- Running potentially obfuscated scripts
- Executable files from running “unless they meet a prevalence, age, or trusted list criterion”
Finally, organizations must educate their employees about HTML smuggling and train them on how to respond to it properly when encountered.
Detection & Response:
Qradar:
SELECT UTF8(payload) from events where (LOGSOURCETYPENAME(devicetype)='Microsoft Windows Security Event Log' and (CATEGORYNAME(category) ILIKE 'File Created' or CATEGORYNAME(category) ILIKE 'Successful File Modification')) and ((("TargetFilename" ilike '%.htm' or "TargetFilename" ilike '%.html') and ("TargetFilename" ilike '%\Users\%\Downloads\%' or "TargetFilename" ilike '%\Users\%\Content.Outlook\%' or "TargetFilename" ilike '%\Users\%\AppData\Local\Temp\%' or "TargetFilename" ilike '%\Users\%\AppData\Local\Temp\7z%' or "TargetFilename" ilike '%\Users\%\AppData\Local\Temp\Rar%')) or (("Image" ilike '%\chrome.exe' or "Image" ilike '%\msedge.exe' or "Image" ilike '%\firefox.exe' or "Image" ilike '%\iexplore.exe') and ("Process CommandLine" ilike '%\Users\%\Downloads\%.htm%' or "Process CommandLine" ilike '%\Users\%\Content.Outlook\%.htm%' or "Process CommandLine" ilike '%\Users\%\AppData\Local\Temp\%.htm%' or "Process CommandLine" ilike '%\Users\%\AppData\Local\Temp\7z%.htm%' or "Process CommandLine" ilike '%\Users\%\AppData\Local\Temp\Rar%.htm%')))Splunk:
source="WinEventLog:*" AND (((TargetFilename="*.htm" OR TargetFilename="*.html") AND (TargetFilename="*\\Users\*\\Downloads\*" OR TargetFilename="*\\Users\*\\Content.Outlook\*" OR TargetFilename="*\\Users\*\\AppData\\Local\\Temp\*" OR TargetFilename="*\\Users\*\\AppData\\Local\\Temp\\7z*" OR TargetFilename="*\\Users\*\\AppData\\Local\\Temp\\Rar*")) OR ((Image="*\\chrome.exe" OR Image="*\\msedge.exe" OR Image="*\\firefox.exe" OR Image="*\\iexplore.exe") AND (CommandLine="*\\Users\*\\Downloads\*.htm*" OR CommandLine="*\\Users\*\\Content.Outlook\*.htm*" OR CommandLine="*\\Users\*\\AppData\\Local\\Temp\*.htm*" OR CommandLine="*\\Users\*\\AppData\\Local\\Temp\\7z*.htm*" OR CommandLine="*\\Users\*\\AppData\\Local\\Temp\\Rar*.htm*")))Elastic Query:
((file.path:(*.htm OR *.html) AND file.path:(*\\Users\*\\Downloads\* OR *\\Users\*\\Content.Outlook\* OR *\\Users\*\\AppData\\Local\\Temp\* OR *\\Users\*\\AppData\\Local\\Temp\\7z* OR *\\Users\*\\AppData\\Local\\Temp\\Rar*)) OR (process.executable:(*\\chrome.exe OR *\\msedge.exe OR *\\firefox.exe OR *\\iexplore.exe) AND process.command_line:(*\\Users\*\\Downloads\*.htm* OR *\\Users\*\\Content.Outlook\*.htm* OR *\\Users\*\\AppData\\Local\\Temp\*.htm* OR *\\Users\*\\AppData\\Local\\Temp\\7z*.htm* OR *\\Users\*\\AppData\\Local\\Temp\\Rar*.htm*)))Arcsight:
(((filePath CONTAINS "*.htm" OR filePath CONTAINS "*.html" AND filePath CONTAINS "*\\Users\\*\\Downloads\\*" OR filePath CONTAINS "*\\Users\\*\\Content.Outlook\\*" OR filePath CONTAINS "*\\Users\\*\\AppData\\Local\\Temp\\*" OR filePath CONTAINS "*\\Users\\*\\AppData\\Local\\Temp\\7z*" OR filePath CONTAINS "*\\Users\\*\\AppData\\Local\\Temp\\Rar*") OR (((deviceProcessName CONTAINS "*\\chrome.exe" OR deviceProcessName CONTAINS "*\\msedge.exe" OR deviceProcessName CONTAINS "*\\firefox.exe" OR deviceProcessName CONTAINS "*\\iexplore.exe" OR sourceProcessName CONTAINS "*\\chrome.exe" OR sourceProcessName CONTAINS "*\\msedge.exe" OR sourceProcessName CONTAINS "*\\firefox.exe" OR sourceProcessName CONTAINS "*\\iexplore.exe" OR destinationProcessName CONTAINS "*\\chrome.exe" OR destinationProcessName CONTAINS "*\\msedge.exe" OR destinationProcessName CONTAINS "*\\firefox.exe" OR destinationProcessName CONTAINS "*\\iexplore.exe")) AND ((destinationServiceName CONTAINS "*\\Users\\*\\Downloads\\*.htm*" OR destinationServiceName CONTAINS "*\\Users\\*\\Content.Outlook\\*.htm*" OR destinationServiceName CONTAINS "*\\Users\\*\\AppData\\Local\\Temp\\*.htm*" OR destinationServiceName CONTAINS "*\\Users\\*\\AppData\\Local\\Temp\\7z*.htm*" OR destinationServiceName CONTAINS "*\\Users\\*\\AppData\\Local\\Temp\\Rar*.htm*" OR deviceCustomString1 CONTAINS "*\\Users\\*\\Downloads\\*.htm*" OR deviceCustomString1 CONTAINS "*\\Users\\*\\Content.Outlook\\*.htm*" OR deviceCustomString1 CONTAINS "*\\Users\\*\\AppData\\Local\\Temp\\*.htm*" OR deviceCustomString1 CONTAINS "*\\Users\\*\\AppData\\Local\\Temp\\7z*.htm*" OR deviceCustomString1 CONTAINS "*\\Users\\*\\AppData\\Local\\Temp\\Rar*.htm*")))))Carbonblack:
((filemod_name:(*.htm OR *.html) AND filemod_name:(*\\Users\*\\Downloads\* OR *\\Users\*\\Content.Outlook\* OR *\\Users\*\\AppData\\Local\\Temp\* OR *\\Users\*\\AppData\\Local\\Temp\\7z* OR *\\Users\*\\AppData\\Local\\Temp\\Rar*)) OR (process_name:(*\\chrome.exe OR *\\msedge.exe OR *\\firefox.exe OR *\\iexplore.exe) AND process_cmdline:(*\\Users\*\\Downloads\*.htm* OR *\\Users\*\\Content.Outlook\*.htm* OR *\\Users\*\\AppData\\Local\\Temp\*.htm* OR *\\Users\*\\AppData\\Local\\Temp\\7z*.htm* OR *\\Users\*\\AppData\\Local\\Temp\\Rar*.htm*)))GrayLog:
((TargetFilename.keyword:(*.htm *.html) AND TargetFilename.keyword:(*\\Users\*\\Downloads\* *\\Users\*\\Content.Outlook\* *\\Users\*\\AppData\\Local\\Temp\* *\\Users\*\\AppData\\Local\\Temp\\7z* *\\Users\*\\AppData\\Local\\Temp\\Rar*)) OR (Image.keyword:(*\\chrome.exe *\\msedge.exe *\\firefox.exe *\\iexplore.exe) AND CommandLine.keyword:(*\\Users\*\\Downloads\*.htm* *\\Users\*\\Content.Outlook\*.htm* *\\Users\*\\AppData\\Local\\Temp\*.htm* *\\Users\*\\AppData\\Local\\Temp\\7z*.htm* *\\Users\*\\AppData\\Local\\Temp\\Rar*.htm*)))Logpoint:
((TargetFilename IN ["*.htm", "*.html"] TargetFilename IN ["*\\Users\*\\Downloads\*", "*\\Users\*\\Content.Outlook\*", "*\\Users\*\\AppData\\Local\\Temp\*", "*\\Users\*\\AppData\\Local\\Temp\\7z*", "*\\Users\*\\AppData\\Local\\Temp\\Rar*"]) OR (Image IN ["*\\chrome.exe", "*\\msedge.exe", "*\\firefox.exe", "*\\iexplore.exe"] CommandLine IN ["*\\Users\*\\Downloads\*.htm*", "*\\Users\*\\Content.Outlook\*.htm*", "*\\Users\*\\AppData\\Local\\Temp\*.htm*", "*\\Users\*\\AppData\\Local\\Temp\\7z*.htm*", "*\\Users\*\\AppData\\Local\\Temp\\Rar*.htm*"]))Microsoft Defender:
DeviceFileEvents | where (((FolderPath endswith ".htm" or FolderPath endswith ".html") and (FolderPath matches regex @".*\\Users\.*\\Downloads\.*" or FolderPath matches regex @".*\\Users\.*\\Content\.Outlook\.*" or FolderPath matches regex @".*\\Users\.*\\AppData\\Local\\Temp\.*" or FolderPath matches regex @".*\\Users\.*\\AppData\\Local\\Temp\\7z.*" or FolderPath matches regex @".*\\Users\.*\\AppData\\Local\\Temp\\Rar.*")) or ((InitiatingProcessFolderPath endswith @"\chrome.exe" or InitiatingProcessFolderPath endswith @"\msedge.exe" or InitiatingProcessFolderPath endswith @"\firefox.exe" or InitiatingProcessFolderPath endswith @"\iexplore.exe") and (InitiatingProcessCommandLine matches regex @".*\\Users\.*\\Downloads\.*\.htm.*" or InitiatingProcessCommandLine matches regex @".*\\Users\.*\\Content\.Outlook\.*\.htm.*" or InitiatingProcessCommandLine matches regex @".*\\Users\.*\\AppData\\Local\\Temp\.*\.htm.*" or InitiatingProcessCommandLine matches regex @".*\\Users\.*\\AppData\\Local\\Temp\\7z.*\.htm.*" or InitiatingProcessCommandLine matches regex @".*\\Users\.*\\AppData\\Local\\Temp\\Rar.*\.htm.*")))Microsoft Sentinel:
SecurityEvent | where EventID == 11 | where (((TargetFilename endswith '.htm' or TargetFilename endswith '.html') and (TargetFilename matches regex '(?i).*\Users\.*\Downloads\.*' or TargetFilename matches regex '(?i).*\Users\.*\Content.Outlook\.*' or TargetFilename matches regex '(?i).*\Users\.*\AppData\Local\Temp\.*' or TargetFilename matches regex '(?i).*\Users\.*\AppData\Local\Temp\7z.*' or TargetFilename matches regex '(?i).*\Users\.*\AppData\Local\Temp\Rar.*')) or ((NewProcessName endswith @'\chrome.exe' or NewProcessName endswith @'\msedge.exe' or NewProcessName endswith @'\firefox.exe' or NewProcessName endswith @'\iexplore.exe') and (CommandLine matches regex '(?i).*\Users\.*\Downloads\.*.htm.*' or CommandLine matches regex '(?i).*\Users\.*\Content.Outlook\.*.htm.*' or CommandLine matches regex '(?i).*\Users\.*\AppData\Local\Temp\.*.htm.*' or CommandLine matches regex '(?i).*\Users\.*\AppData\Local\Temp\7z.*.htm.*' or CommandLine matches regex '(?i).*\Users\.*\AppData\Local\Temp\Rar.*.htm.*')))RSA Netwitness:
(((TargetFilename contains '.htm', '.html') && (TargetFilename regex '.*\\Users\.*\\Downloads\.*', '.*\\Users\.*\\Content\.Outlook\.*', '.*\\Users\.*\\AppData\\Local\\Temp\.*', '.*\\Users\.*\\AppData\\Local\\Temp\\7z.*', '.*\\Users\.*\\AppData\\Local\\Temp\\Rar.*')) || ((Image contains '\chrome\.exe', '\msedge\.exe', '\firefox\.exe', '\iexplore\.exe') && (CommandLine regex '.*\\Users\.*\\Downloads\.*\.htm.*', '.*\\Users\.*\\Content\.Outlook\.*\.htm.*', '.*\\Users\.*\\AppData\\Local\\Temp\.*\.htm.*', '.*\\Users\.*\\AppData\\Local\\Temp\\7z.*\.htm.*', '.*\\Users\.*\\AppData\\Local\\Temp\\Rar.*\.htm.*')))Sumologic:
(_sourceCategory=*windows* AND ((((".htm" OR ".html") AND (("\Users\" AND "\Downloads\") OR ("\Users\" AND "\Content.Outlook\") OR ("\Users\" AND "\AppData\Local\Temp\") OR ("\Users\" AND "\AppData\Local\Temp\7z") OR ("\Users\" AND "\AppData\Local\Temp\Rar"))) OR ((Image = "*\chrome.exe" OR Image = "*\msedge.exe" OR Image = "*\firefox.exe" OR Image = "*\iexplore.exe") AND (CommandLine = "*\Users\*\Downloads\*.htm*" OR CommandLine = "*\Users\*\Content.Outlook\*.htm*" OR CommandLine = "*\Users\*\AppData\Local\Temp\*.htm*" OR CommandLine = "*\Users\*\AppData\Local\Temp\7z*.htm*" OR CommandLine = "*\Users\*\AppData\Local\Temp\Rar*.htm*")))))Google Chronicle:
(((target.file.full_path = /.*\.htm$/ or target.file.full_path = /.*\.html$/) and (target.file.full_path = /.*\\Users\\.*\\Downloads\\.*/ or target.file.full_path = /.*\\Users\\.*\\Content\.Outlook\\.*/ or target.file.full_path = /.*\\Users\\.*\\AppData\\Local\\Temp\\.*/ or target.file.full_path = /.*\\Users\\.*\\AppData\\Local\\Temp\\7z.*/ or target.file.full_path = /.*\\Users\\.*\\AppData\\Local\\Temp\\Rar.*/)) or ((target.process.file.full_path = /.*\\chrome\.exe$/ or target.process.file.full_path = /.*\\msedge\.exe$/ or target.process.file.full_path = /.*\\firefox\.exe$/ or target.process.file.full_path = /.*\\iexplore\.exe$/) and (target.process.command_line = /.*\\Users\\.*\\Downloads\\.*\.htm.*/ or target.process.command_line = /.*\\Users\\.*\\Content\.Outlook\\.*\.htm.*/ or target.process.command_line = /.*\\Users\\.*\\AppData\\Local\\Temp\\.*\.htm.*/ or target.process.command_line = /.*\\Users\\.*\\AppData\\Local\\Temp\\7z.*\.htm.*/ or target.process.command_line = /.*\\Users\\.*\\AppData\\Local\\Temp\\Rar.*\.htm.*/)))Aws OpenSearch:
((file.path:(*.htm OR *.html) AND file.path:(*\\Users\*\\Downloads\* OR *\\Users\*\\Content.Outlook\* OR *\\Users\*\\AppData\\Local\\Temp\* OR *\\Users\*\\AppData\\Local\\Temp\\7z* OR *\\Users\*\\AppData\\Local\\Temp\\Rar*)) OR (process.executable:(*\\chrome.exe OR *\\msedge.exe OR *\\firefox.exe OR *\\iexplore.exe) AND process.command_line:(*\\Users\*\\Downloads\*.htm* OR *\\Users\*\\Content.Outlook\*.htm* OR *\\Users\*\\AppData\\Local\\Temp\*.htm* OR *\\Users\*\\AppData\\Local\\Temp\\7z*.htm* OR *\\Users\*\\AppData\\Local\\Temp\\Rar*.htm*)))Source/Credits: https://blog.malwarebytes.com/explained/2021/11/evasive-maneuvers-html-smuggling-explained/
http:twitter.com/SBousseaden



































