Researchers at Asec Lab have observed the new indicators of Magniber. Since February 2022, Magniber has been using a Windows installer package file (.msi) instead of IE browser vulnerability for its distribution. The ransomware includes a valid certificate and was distributed in DLL form inside the MSI file. However, starting from July 20th (Wednesday), it is now being distributed as a CPL file extension instead of MSI.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
As the cases of using an MSI file for distribution are decreasing, the attacker of Magniber likely has changed the method of distribution.
(July 19th, 2022) MS.Upgrade.Database.Cloud.msi
(July 20th, 2022) MS.Upgrade.Database.Cloud.cpl (Chrome)
(July 20th, 2022) MS.Upgrade.Database.Cloud.zip (Edge)
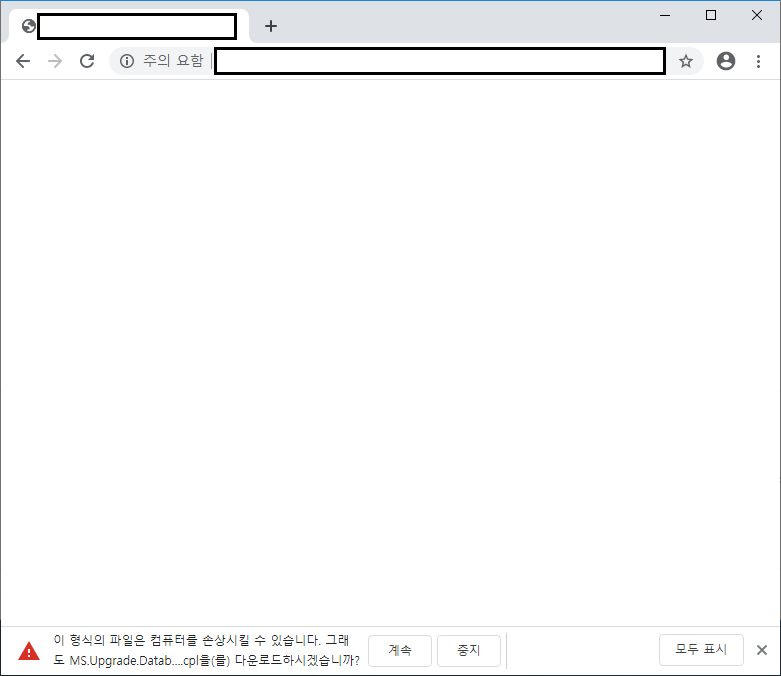
The CPL file is directly downloaded in Chrome. For Edge, it is distributed as a compressed zip file since downloading CPL files are blocked in the browser.
Also Read: Anatomy Of The Ransomware Cybercrime Economy
Windows Control Panel file (.cpl) downloaded from a webpage that distributes Magniber
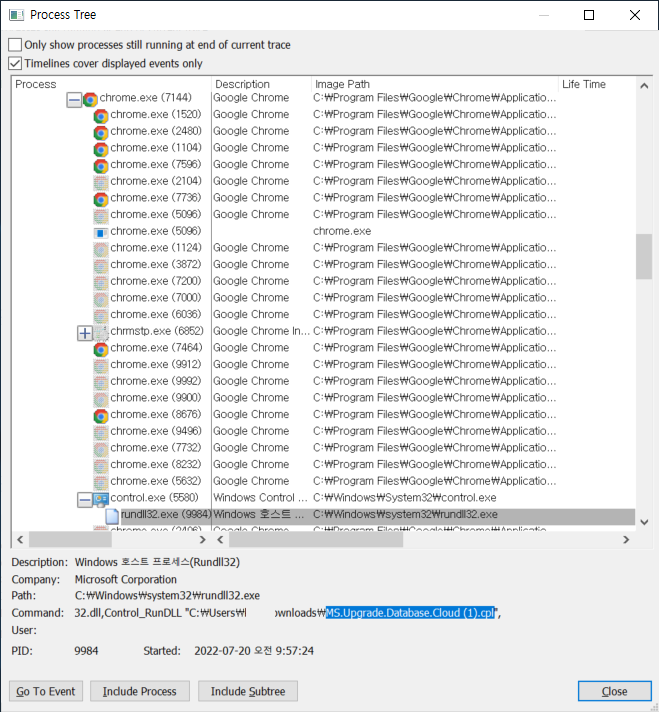
When users open the downloaded [Magniber].cpl file, a Windows normal process named control.exe runs the cpl file using rundll32.exe.
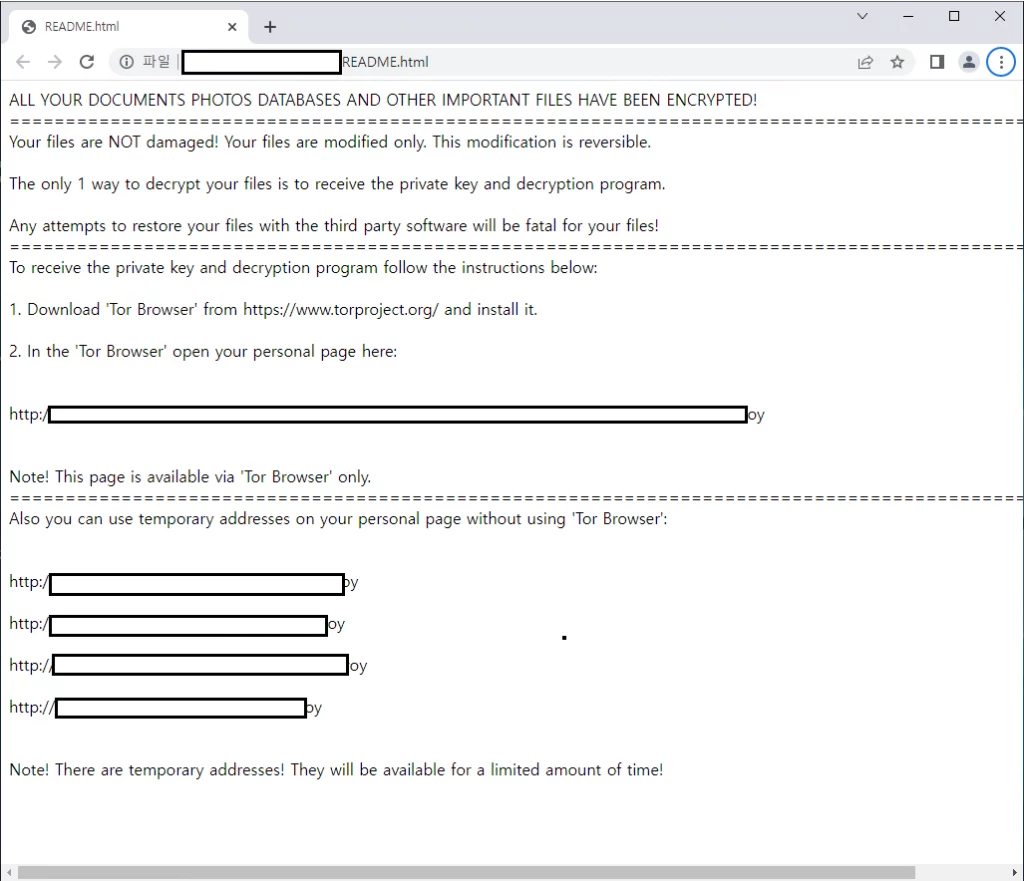
Magniber is currently being distributed in a typosquatting method that exploits typos made when entering domains, targeting Chrome and Edge users with the latest Windows version. As users may download ransomware by entering incorrect domains, extra caution is required.
AhnLab is currently responding to Magniber as shown in the following:
[IOC]
[File Detection]
Ransomware/Win.Magniber.C5211694 (2022.07.20.02)
[.cpl MD5]
C49DD67AFB59A85FBCBC77C412338255
Detection & Response:
Splunk:
source="WinEventLog:*" AND ((((TargetFilename="*.cpl" OR TargetFilename="*.zip") AND (TargetFilename="*\\Users\*\\Downloads\*")) OR (Image="*\\control.exe" AND (CommandLine="*.cpl*"))) OR (Image="*\\rundll32.exe" AND (CommandLine="*.cpl*")))Qradar:
SELECT UTF8(payload) from events where (LOGSOURCETYPENAME(devicetype)='Microsoft Windows Security Event Log' and (CATEGORYNAME(category) ILIKE 'File Created' or CATEGORYNAME(category) ILIKE 'Successful File Modification')) and (((("TargetFilename" ilike '%.cpl' or "TargetFilename" ilike '%.zip') and ("TargetFilename" ilike '%\Users\%\Downloads\%')) or ("Image" ilike '%\control.exe' and ("Process CommandLine" ilike '%.cpl%'))) or ("Image" ilike '%\rundll32.exe' and ("Process CommandLine" ilike '%.cpl%')))Elastic Query:
(((file.path.text:(*.cpl OR *.zip) AND file.path.text:*\\Users\*\\Downloads\*) OR (process.executable.text:*\\control.exe AND process.command_line.text:*.cpl*)) OR (process.executable.text:*\\rundll32.exe AND process.command_line.text:*.cpl*))CarbonBlack:
(((filemod_name:(*.cpl OR *.zip) AND filemod_name:*\\Users\*\\Downloads\*) OR (process_name:*\\control.exe AND process_cmdline:*.cpl*)) OR (process_name:*\\rundll32.exe AND process_cmdline:*.cpl*))Google Chronicle:
(((((target.file.full_path = /.*\.cpl$/ or target.file.full_path = /.*\.zip$/) and target.file.full_path = /.*\\Users\\.*\\Downloads\\.*/) or (target.process.file.full_path = /.*\\control\.exe$/ and target.process.command_line = /.*\.cpl.*/))) or (target.process.file.full_path = /.*\\rundll32\.exe$/ and target.process.command_line = /.*\.cpl.*/))GrayLog:
(((TargetFilename.keyword:(*.cpl *.zip) AND TargetFilename.keyword:*\\Users\*\\Downloads\*) OR (Image.keyword:*\\control.exe AND CommandLine.keyword:*.cpl*)) OR (Image.keyword:*\\rundll32.exe AND CommandLine.keyword:*.cpl*))Logpoint:
(((TargetFilename IN ["*.cpl", "*.zip"] TargetFilename IN "*\\Users\*\\Downloads\*") OR (Image="*\\control.exe" CommandLine IN "*.cpl*")) OR (Image="*\\rundll32.exe" CommandLine IN "*.cpl*"))Microsoft Defender:
DeviceFileEvents | where ((((FolderPath endswith ".cpl" or FolderPath endswith ".zip") and (FolderPath matches regex @".*\\Users\.*\\Downloads\.*")) or (InitiatingProcessFolderPath endswith @"\control.exe" and (InitiatingProcessCommandLine contains ".cpl"))) or (InitiatingProcessFolderPath endswith @"\rundll32.exe" and (InitiatingProcessCommandLine contains ".cpl")))Microsoft Sentinel:
SecurityEvent | where EventID == 11 | where ((((TargetFilename endswith '.cpl' or TargetFilename endswith '.zip') and (TargetFilename matches regex '(?i).*\Users\.*\Downloads\.*')) or (Image endswith @'\control.exe' and (CommandLine contains '.cpl'))) or (Image endswith @'\rundll32.exe' and (CommandLine contains '.cpl')))RSA Netwitness:
((((TargetFilename contains '.cpl', '.zip') && (TargetFilename regex '.*\\Users\.*\\Downloads\.*')) || ((Image contains 'control.exe') && (CommandLine contains '.cpl'))) || ((Image contains 'rundll32.exe') && (CommandLine contains '.cpl')))SumoLogic:
(_sourceCategory=*windows* AND ((((((".cpl" OR ".zip") AND (("\Users\" AND "\Downloads\"))) OR (Image="*\control.exe" AND (CommandLine = "*.cpl*")))) OR (Image="*\rundll32.exe" AND (CommandLine = "*.cpl*")))))Source/Credits: asec.ahnlab.com/en/37012/



































