Microsoft taking steps to block Excel 4.0 (XLM or XL4) and Visual Basic for Applications (VBA) macros by default across Office apps, malicious actors are responding by refining their tactics, techniques, and procedures (TTPs).
“The use of VBA and XL4 Macros decreased approximately 66% from October 2021 through June 2022,” Proofpoint said in a report shared with The Hacker News, calling it “one of the largest email threat landscape shifts in recent history.”
In its place, adversaries are increasingly pivoting away from macro-enabled documents to other alternatives, including container files such as ISO and RAR as well as Windows Shortcut (LNK) files in campaigns to distribute malware.
“Threat actors pivoting away from directly distributing macro-based attachments in email represents a significant shift in the threat landscape,” Sherrod DeGrippo, vice president of threat research and detection at Proofpoint, said in a statement.
“Threat actors are now adopting new tactics to deliver malware, and the increased use of files such as ISO, LNK, and RAR is expected to continue.”
VBA macros embedded in Office documents sent via phishing emails have proven to be an effective technique in that it allows threat actors to automatically run malicious content after tricking a recipient into enabling macros via social engineering tactics.
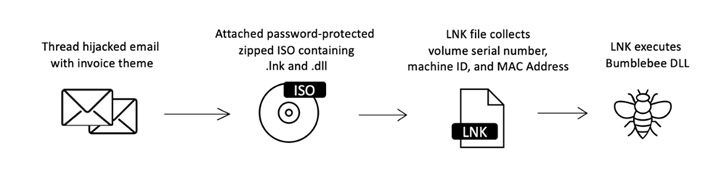
However, Microsoft’s plans to block macros in files downloaded from the internet have led to email-based malware campaigns experimenting with other ways to bypass Mark of the Web (MOTW) protections and infect victims.
This involves the use of ISO, RAR and LNK file attachments, which have surged nearly 175% during the same period. At least 10 threat actors are said to have begun using LNK files since February 2022.
“The number of campaigns containing LNK files increased 1,675% since October 2021,” the enterprise security company noted, adding the number of attacks using HTML attachments more than doubled from October 2021 to June 2022.
Some of the notable malware families distributed through these new methods consist of Emotet, IcedID, Qakbot, and Bumblebee.
“There are also cases where the attack chains are more convoluted, for example, with some recent Qbot campaigns where a .ZIP containing an ISO is embedded within an HTML file directly attached to a message.”
As for getting intended victims to open and click, the methods are the same: a wide array of social engineering tactics to get people to open and click.
Detection & Response:
Qradar:
SELECT UTF8(payload), "Image", "Computer Name", "Filename" from events where LOGSOURCETYPENAME(devicetype)='Microsoft Windows Security Event Log' and (CATEGORYNAME(category) ILIKE 'File Created' or CATEGORYNAME(category) ILIKE 'Successful File Modification') and "Filename" ilike '%.iso' and (("Filename" ilike '%\AppData\Local\Temp\%' and "Filename" ilike '%.zip\%') or "Filename" ilike '%\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\%')Splunk:
source="WinEventLog:*" AND (TargetFilename="*.iso" AND ((TargetFilename="*\\AppData\\Local\\Temp\\*" AND TargetFilename="*.zip\\*") OR TargetFilename="*\\AppData\\Local\\Microsoft\\Windows\\INetCache\\Content.Outlook\\*")) | table Image,ComputerName,TargetFileNameElastic Query:
(file.path.text:*.iso AND ((file.path.text:*\\AppData\\Local\\Temp\\* AND file.path.text:*.zip\\*) OR file.path.text:*\\AppData\\Local\\Microsoft\\Windows\\INetCache\\Content.Outlook\\*))Arcsight:
(filePath ENDSWITH ".iso" AND (((filePath CONTAINS "\AppData\Local\Temp\\" AND filePath CONTAINS ".zip\\") OR filePath CONTAINS "\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\\"))) AND type != 2 | rex field = flexString1 mode=sed "s//Sigma: ISO File Created Within Temp Folders/g"CarbonBlack:
(filemod_name:*.iso AND ((filemod_name:*\\AppData\\Local\\Temp\\* AND filemod_name:*.zip\\*) OR filemod_name:*\\AppData\\Local\\Microsoft\\Windows\\INetCache\\Content.Outlook\\*))FireEye:
(metaclass:`windows` filepath:`*.iso` ((filepath:`\AppData\Local\Temp\\` filepath:`.zip\\`) OR filepath:`\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\\`))GrayLog:
(TargetFilename.keyword:*.iso AND ((TargetFilename.keyword:*\\AppData\\Local\\Temp\\* AND TargetFilename.keyword:*.zip\\*) OR TargetFilename.keyword:*\\AppData\\Local\\Microsoft\\Windows\\INetCache\\Content.Outlook\\*))Logpoint:
(TargetFilename="*.iso" ((TargetFilename="*\\AppData\\Local\\Temp\\*" TargetFilename="*.zip\\*") OR TargetFilename="*\\AppData\\Local\\Microsoft\\Windows\\INetCache\\Content.Outlook\\*"))Microsoft Defender:
DeviceFileEvents | where (FolderPath endswith ".iso" and ((FolderPath contains @"\AppData\Local\Temp\" and FolderPath contains @".zip\") or FolderPath contains @"\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\"))Microsoft Sentinel:
SysmonEvent | where EventID == 11 | where (TargetFilename endswith '.iso' and ((TargetFilename contains @'\AppData\Local\Temp\' and TargetFilename contains @'.zip\') or TargetFilename contains @'\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\'))RSA Netwitness:
((TargetFilename contains '.iso') && (((TargetFilename contains 'AppData\Local\Temp\\') && (TargetFilename contains '.zip\\')) || (TargetFilename contains 'AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\\')))SumoLogic:
(_sourceCategory=*windows* AND ".iso" AND ((("\AppData\Local\Temp\\" AND ".zip\\") OR "\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\\")))


































