Unseen tactics, techniques, and procedures (TTP) are deployed by the member of the Cuba ransomware operation. Including a novel RAT (remote access trojan) and a new local privilege escalation tool.
The threat actor was named ‘Tropical Scorpius’ by researchers at Palo Alto Networks Unit 42 and is likely an affiliate of the Cuba ransomware operation. While it is clear the Tropical Scorpius threat actors are constantly developing and updating their toolkit, the core Cuba Ransomware payload has remained roughly the same since its discovery in 2019.
Cuba Ransomware payload used to encrypt the files on a compromised system, appending the .cuba extension to the files – but then observed that the exfiltrated data was posted for sale on the Industrial Spy marketplace.

As discussed by Trend Micro, the developers of Cuba Ransomware have built onto the list of targeted processes and services that will be terminated on runtime, as well as increasing the number of directories and extensions to avoid encrypting.
Targeted processes and services:
MySQL
MySQL82SQLSERVERAGENT
MSSQLSERVER
SQLWriter
SQLTELEMETRY
MSDTC
SQLBrowser
sqlagent.exe
sqlservr.exe
sqlwriter.exe
sqlceip.exe
msdtc.exe
sqlbrowser.exe
vmcompute
vmms
vmwp.exe
vmsp.exe
outlook.exe
MSExchangeUMCR
MSExchangeUM
MSExchangeTransportLogSearch
MSExchangeTransport
MSExchangeThrottling
MSExchangeSubmission
MSExchangeServiceHost
MSExchangeRPC
MSExchangeRepl
MSExchangePOP3BE
MSExchangePop3
MSExchangeNotificationsBroker
MSExchangeMailboxReplication
MSExchangeMailboxAssistants
MSExchangeIS
MSExchangeIMAP4BE
MSExchangeImap4
MSExchangeHMRecovery
MSExchangeHM
MSExchangeFrontEndTransport
MSExchangeFastSearch
MSExchangeEdgeSync
MSExchangeDiagnostics
MSExchangeDelivery
MSExchangeDagMgmt
MSExchangeCompliance
MSExchangeAntispamUpdate
Microsoft.Exchange.Store.Worker.exe
Avoided directories:
\windows\
\program files\microsoft office\
\program files (x86)\microsoft office\
\program files\avs\
\program files (x86)\avs\
\$recycle.bin\
\boot\
\recovery\
\system volume information\
\msocache\
\users\all users\
\users\default user\
\users\default\
\temp\
\inetcache\
\google\
Avoided extensions:
.exe
.dll
.sys
.ini
.lnk
.vbm
.cuba
Tropical Scorpius Defense Evasion
The New technique is legitimate but an invalidated NVIDIA certificate was stolen and leaked by LAPSUS to sign a kernel driver dropped at the initial stages of an infection.
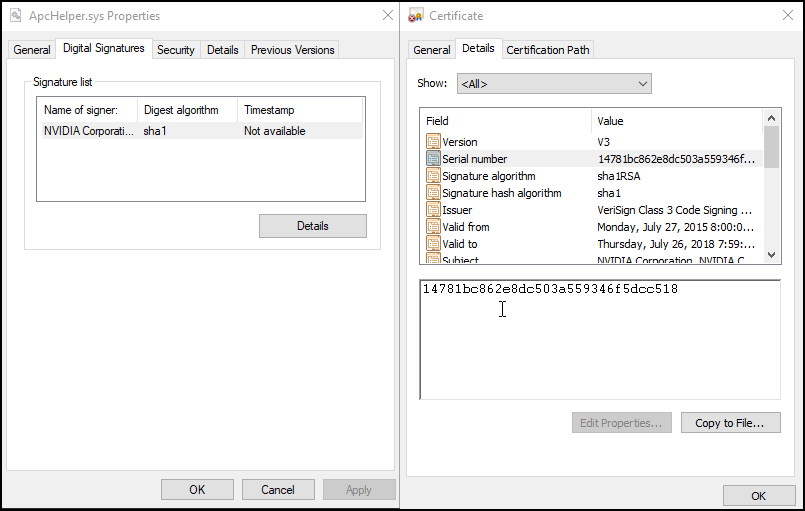
The malicious dropper file names sophos_jareld.exe , 07905de4b4be02665e280a56678c7de67652aee318487a44055700396d37ecd0 and ApcHelper.sys was not signed, however, the kernel driver was signed using the certificate found in the LAPSUS NVIDIA leak.
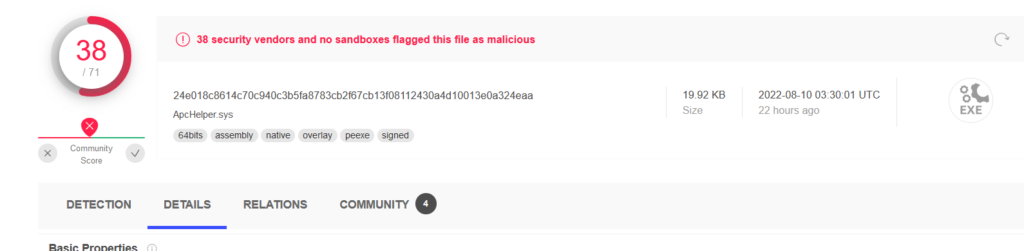
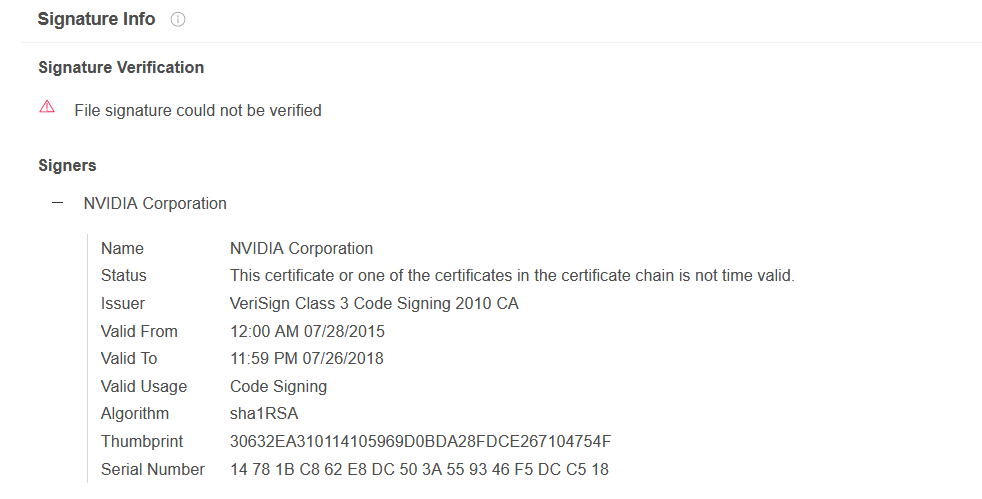
After the kernel driver drops onto the file system, the loader will first run a deletion command argument via cmd.exe for the file path.

After this, it will create a new service using cmd.exe and run the argument below to set up a service for the kernel driver.

Then the loader copies the kernel driver responsible for terminating security products onto the file system.
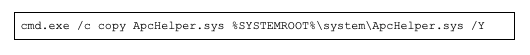
The core functionality of the kernel driver dropped and loaded is to resolve additional kernel APIs for performing functionality and targeting a list of security products for termination. Threat actors evade detection in the compromised environment.

Local Privilege Escalation
The local privilege escalation tool leveraged by Tropical Scorpius was initially downloaded from the web hosting platform tmpfiles[.]org by using PowerShell’s Invoke-WebRequest.
Threat actors leverage a binary that abused CVE-2022-24521, a vulnerability in the Common Log File System (CLFS).
Ticket to Lateral Movement
The Tropical Scorpius threat actor leveraged various tools for the initial system reconnaissance. ADFind and Net Scan were downloaded from the web hosting platform tmpfiles[.]org by using PowerShell’s Invoke-WebRequest.
Credential preparation and collection on lower-privilege systems was performed using a PowerShell-based script, GetUserSPNs.ps1.
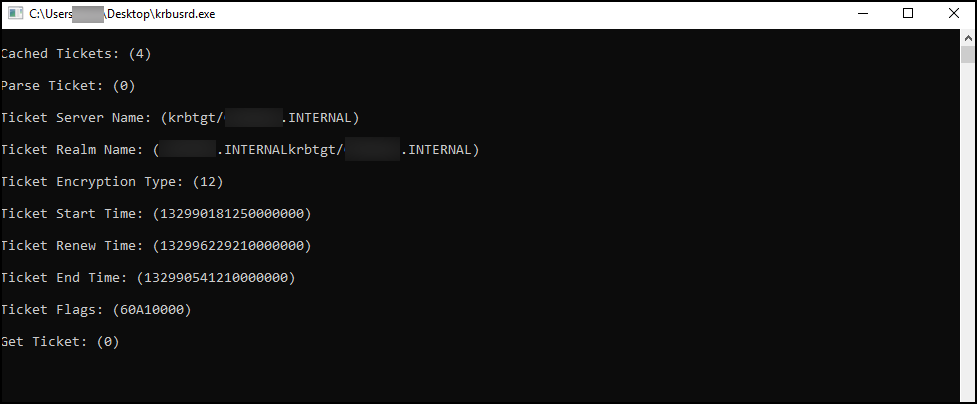
The threat actor used this process to pinpoint accounts worth targeting for their associated Active Directory Kerberos ticket, in order to collect and crack the Kerberos ticket offline via the technique called Kerberoasting.
To Domain Admin
The Domain Admin tool leveraged by Tropical Scorpius was initially downloaded from the web hosting platform tmpfiles[.]org by using PowerShell’s Invoke-WebRequest.
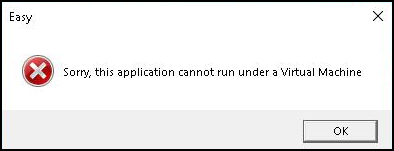
The sample was packed using the Anti-VM features of Themida, a well-known commercial packing tool. It was also masquerading as the filename Filezilla.
Upon execution, if running in a virtualized environment, the packer will display the following message:
The unique commands associated with the hacktool provide high confidence Zero.exe is a ZeroLogon hack tool. The ZeroLogon hacktool is used to abuse CVE-2020-1472 to gain Domain Administrator (DA) privileges by requesting an NTLM hash from the domain controller.
ROMCOM RAT
Custom remote access Trojan/backdoor containing a unique command and control (C2) protocol. Based on the strings within the binary as well as the functionality.
ROMCOM RAT can be executed through the use of one of its two exports:
ServiceMain
startWorker
Upon execution of the ServiceMain export, ROMCOM will execute the following command line:
C:\\Windows\\System32\\rundll32.exe
C:\\Windows\\System32\\comDll.dll,startWorker
Finally, Tropical Scorpius deploys “ROMCOM RAT,” a previously unseen malware that handles C2 communications via ICMP requests performed through Windows API functions.
ROMCOM RAT supports ten commands as listed below:
- Return connected drive information
- Return file listings for a specified directory
- Start up a reverse shell under the name svchelper.exe within the %ProgramData% folder
- Upload data to C2 as ZIP file, using IShellDispatch to copy files
- Download data and write to worker.txt in the %ProgramData% folder
- Delete a specified file
- Delete a specified directory
- Spawn a process with PID Spoofing
- Only handled by ServiceMain, received from C2 server and instructs the process to sleep for 120,000 ms
- Iterate through running processes and gather process IDs
Tropical Scorpius remains an active threat. The group’s activity makes it clear that an approach to tradecraft using a hybrid of more nuanced tools focusing on low-level Windows internals for defense evasion and local privilege escalation can be highly effective during an intrusion.
Indicators of Compromise
Driver Dropper:
07905de4b4be02665e280a56678c7de67652aee318487a44055700396d37ecd0
af6561ad848aa1ba53c62a323de230b18cfd30d8795d4af36bf1ce6c28e3fd4e
24e018c8614c70c940c3b5fa8783cb2f67cb13f08112430a4d10013e0a324eaa
ZeroLogon Hacktool:
ab5a3bbad1c4298bc287d0ac8c27790d68608393822da2365556ba99d52c5dfb
6866e82d0f6f6d8cf5a43d02ad523f377bb0b374d644d2f536ec7ec18fdaf576
3febf726ffb4f4a4186571d05359d2851e52d5612c5818b2b167160d367f722c
3a8b7c1fe9bd9451c0a51e4122605efc98e7e4e13ed117139a13e4749e211ed0
36bc32becf287402bf0e9c918de22d886a74c501a33aa08dcb9be2f222fa6e24
1450f7c85bfec4f5ba97bcec4249ae234158a0bf9a63310e3801a00d30d9abcc
Cuba Ransomware:
0a3517d8d382a0a45334009f71e48114d395a22483b01f171f2c3d4a9cfdbfbf
0eff3e8fd31f553c45ab82cc5d88d0105626d0597afa5897e78ee5a7e34f71b3
Privilege Escalation Tool:
a4665231bad14a2ac9f2e20a6385e1477c299d97768048cb3e9df6b45ae54eb8
KerberCache Hacktool:
cfe7b462a8224b2fbf2b246f05973662bdabc2c4e8f4728c9a1b977fac010c15
ROMCOM RAT:
B5978cf7d0c275d09bedf09f07667e139ad7fed8f9e47742e08c914c5cf44a53
324ccd4bf70a66cc14b1c3746162b908a688b2b124ad9db029e5bd42197cfe99
3496e4861db584cc3239777e137f4022408fb6a7c63152c57e019cf610c8276e
Infrastructure:
CombinedResidency[.]org
optasko[.]com
Detection & Response
Qradar:
SELECT UTF8(payload) from events where LOGSOURCETYPENAME(devicetype)='Microsoft Windows Security Event Log' and (((("ParentImage" ilike '%\cmd.exe') and ("Process CommandLine" ilike '%ApcHelper.sys%' or "Process CommandLine" ilike '%/c%' or "Process CommandLine" ilike '%del%' or "Process CommandLine" ilike '%system%' or "Process CommandLine" ilike '%sc%' or "Process CommandLine" ilike '%create%' or "Process CommandLine" ilike '%ApcHelper%' or "Process CommandLine" ilike '%kernal%')) or ("Image" ilike '%\powershell.exe' and ("Process CommandLine" ilike '%Invoke-WebRequest%'))) or ("Image" ilike '%\cmd.exe' and "Process CommandLine" ilike '%rundll32.exe%' and "Process CommandLine" ilike '%startWorker%' and "Process CommandLine" ilike '%comDll.dll%' and "Process CommandLine" ilike '%system32%'))Elastic Query:
(((process.parent.executable.text:*\\cmd.exe AND process.command_line.text:(*ApcHelper.sys* OR *\/c* OR *del* OR *system* OR *sc* OR *create* OR *ApcHelper* OR *kernal*)) OR (process.executable.text:*\\powershell.exe AND process.command_line.text:*Invoke\-WebRequest*)) OR (process.executable.text:*\\cmd.exe AND process.command_line.text:*rundll32.exe* AND process.command_line.text:*startWorker* AND process.command_line.text:*comDll.dll* AND process.command_line.text:*system32*))Splunk:
source="WinEventLog:*" AND ((((ParentImage="*\\cmd.exe") AND (CommandLine="*ApcHelper.sys*" OR CommandLine="*/c*" OR CommandLine="*del*" OR CommandLine="*system*" OR CommandLine="*sc*" OR CommandLine="*create*" OR CommandLine="*ApcHelper*" OR CommandLine="*kernal*")) OR (Image="*\\powershell.exe" AND (CommandLine="*Invoke-WebRequest*"))) OR (Image="*\\cmd.exe" AND CommandLine="*rundll32.exe*" AND CommandLine="*startWorker*" AND CommandLine="*comDll.dll*" AND CommandLine="*system32*"))CarbonBlack:
(((parent_name:*\\cmd.exe AND process_cmdline:(*ApcHelper.sys* OR *\/c* OR *del* OR *system* OR *sc* OR *create* OR *ApcHelper* OR *kernal*)) OR (process_name:*\\powershell.exe AND process_cmdline:*Invoke\-WebRequest*)) OR (process_name:*\\cmd.exe AND process_cmdline:*rundll32.exe* AND process_cmdline:*startWorker* AND process_cmdline:*comDll.dll* AND process_cmdline:*system32*))Crowdstike:
((((ParentBaseFileName="*\\cmd.exe") AND ((CommandLine="*ApcHelper.sys*" OR CommandLine="*/c*" OR CommandLine="*del*" OR CommandLine="*system*" OR CommandLine="*sc*" OR CommandLine="*create*" OR CommandLine="*ApcHelper*" OR CommandLine="*kernal*") OR (CommandHistory="*ApcHelper.sys*" OR CommandHistory="*/c*" OR CommandHistory="*del*" OR CommandHistory="*system*" OR CommandHistory="*sc*" OR CommandHistory="*create*" OR CommandHistory="*ApcHelper*" OR CommandHistory="*kernal*"))) OR (ImageFileName="*\\powershell.exe" AND ((CommandLine="*Invoke-WebRequest*") OR (CommandHistory="*Invoke-WebRequest*")))) OR (ImageFileName="*\\cmd.exe" AND (CommandLine="*rundll32.exe*" OR CommandHistory="*rundll32.exe*") AND (CommandLine="*startWorker*" OR CommandHistory="*startWorker*") AND (CommandLine="*comDll.dll*" OR CommandHistory="*comDll.dll*") AND (CommandLine="*system32*" OR CommandHistory="*system32*")))Fireeye:
(metaclass:`windows` (((pprocess:`*\cmd.exe` args:[`ApcHelper.sys`,`/c`,`del`,`system`,`sc`,`create`,`ApcHelper`,`kernal`]) OR (process:`*\powershell.exe` args:`Invoke-WebRequest`)) OR (process:`*\cmd.exe` args:`rundll32.exe` args:`startWorker` args:`comDll.dll` args:`system32`)))Microsoft Defender:
DeviceProcessEvents | where ((((InitiatingProcessFolderPath endswith @"\cmd.exe") and (ProcessCommandLine contains "ApcHelper.sys" or ProcessCommandLine contains "/c" or ProcessCommandLine contains "del" or ProcessCommandLine contains "system" or ProcessCommandLine contains "sc" or ProcessCommandLine contains "create" or ProcessCommandLine contains "ApcHelper" or ProcessCommandLine contains "kernal")) or (FolderPath endswith @"\powershell.exe" and (ProcessCommandLine contains "Invoke-WebRequest"))) or (FolderPath endswith @"\cmd.exe" and ProcessCommandLine contains "rundll32.exe" and ProcessCommandLine contains "startWorker" and ProcessCommandLine contains "comDll.dll" and ProcessCommandLine contains "system32"))Microsoft Sentinel:
SecurityEvent | where EventID == 4688 | where ((((ParentProcessName endswith @'\cmd.exe') and (CommandLine contains 'ApcHelper.sys' or CommandLine contains '/c' or CommandLine contains 'del' or CommandLine contains 'system' or CommandLine contains 'sc' or CommandLine contains 'create' or CommandLine contains 'ApcHelper' or CommandLine contains 'kernal')) or (NewProcessName endswith @'\powershell.exe' and (CommandLine contains 'Invoke-WebRequest'))) or (NewProcessName endswith @'\cmd.exe' and CommandLine contains 'rundll32.exe' and CommandLine contains 'startWorker' and CommandLine contains 'comDll.dll' and CommandLine contains 'system32'))RSA Netwitness:
((((ParentImage contains '\cmd\.exe') && (CommandLine contains 'ApcHelper\.sys', '/c', 'del', 'system', 'sc', 'create', 'ApcHelper', 'kernal')) || ((Image contains 'powershell.exe') && (CommandLine contains 'Invoke-WebRequest'))) || ((Image contains 'cmd.exe') && (CommandLine contains 'rundll32.exe') && (CommandLine contains 'startWorker') && (CommandLine contains 'comDll.dll') && (CommandLine contains 'system32')))GrayLog:
(((ParentImage.keyword:*\\cmd.exe AND CommandLine.keyword:(*ApcHelper.sys* *\/c* *del* *system* *sc* *create* *ApcHelper* *kernal*)) OR (Image.keyword:*\\powershell.exe AND CommandLine.keyword:*Invoke\-WebRequest*)) OR (Image.keyword:*\\cmd.exe AND CommandLine.keyword:*rundll32.exe* AND CommandLine.keyword:*startWorker* AND CommandLine.keyword:*comDll.dll* AND CommandLine.keyword:*system32*))SumoLogic:
(_sourceCategory=*windows* AND ((((((ParentImage = "*\cmd.exe") AND (CommandLine = "*ApcHelper.sys*" OR CommandLine = "*/c*" OR CommandLine = "*del*" OR CommandLine = "*system*" OR CommandLine = "*sc*" OR CommandLine = "*create*" OR CommandLine = "*ApcHelper*" OR CommandLine = "*kernal*")) OR (Image="*\powershell.exe" AND (CommandLine = "*Invoke-WebRequest*")))) OR (Image="*\cmd.exe" AND CommandLine="*rundll32.exe*" AND CommandLine="*startWorker*" AND CommandLine="*comDll.dll*" AND CommandLine="*system32*"))))Logpoint:
(((ParentImage IN "*\\cmd.exe" CommandLine IN ["*ApcHelper.sys*", "*/c*", "*del*", "*system*", "*sc*", "*create*", "*ApcHelper*", "*kernal*"]) OR (Image="*\\powershell.exe" CommandLine IN "*Invoke-WebRequest*")) OR (Image="*\\cmd.exe" CommandLine="*rundll32.exe*" CommandLine="*startWorker*" CommandLine="*comDll.dll*" CommandLine="*system32*"))Arcsight Rule:
(((((sourceProcessName ENDSWITH "\cmd.exe" AND ((destinationServiceName CONTAINS "ApcHelper.sys" OR destinationServiceName CONTAINS "/c" OR destinationServiceName CONTAINS "del" OR destinationServiceName CONTAINS "system" OR destinationServiceName CONTAINS "sc" OR destinationServiceName CONTAINS "create" OR destinationServiceName CONTAINS "ApcHelper" OR destinationServiceName CONTAINS "kernal" OR deviceCustomString4 CONTAINS "ApcHelper.sys" OR deviceCustomString4 CONTAINS "/c" OR deviceCustomString4 CONTAINS "del" OR deviceCustomString4 CONTAINS "system" OR deviceCustomString4 CONTAINS "sc" OR deviceCustomString4 CONTAINS "create" OR deviceCustomString4 CONTAINS "ApcHelper" OR deviceCustomString4 CONTAINS "kernal"))) OR (((sourceProcessName ENDSWITH "\powershell.exe" OR destinationProcessName ENDSWITH "\powershell.exe" OR deviceProcessName ENDSWITH "\powershell.exe")) AND ((destinationServiceName CONTAINS "Invoke-WebRequest" OR deviceCustomString4 CONTAINS "Invoke-WebRequest"))))) OR (((sourceProcessName ENDSWITH "\cmd.exe" OR destinationProcessName ENDSWITH "\cmd.exe" OR deviceProcessName ENDSWITH "\cmd.exe")) AND (((destinationServiceName CONTAINS "rundll32.exe" OR deviceCustomString4 CONTAINS "rundll32.exe")) AND ((destinationServiceName CONTAINS "startWorker" OR deviceCustomString4 CONTAINS "startWorker")) AND ((destinationServiceName CONTAINS "comDll.dll" OR deviceCustomString4 CONTAINS "comDll.dll")) AND ((destinationServiceName CONTAINS "system32" OR deviceCustomString4 CONTAINS "system32")))))) AND type != 2 | rex field = flexString1 mode=sed "s//Sigma: aagh/g"Source/Reference: https://unit42.paloaltonetworks.com/cuba-ransomware-tropical-scorpius/



































