Vidar is a type of malware that belongs to the category of information stealers. It is designed to infect Windows-based systems and is known for its ability to steal sensitive information such as passwords, credit card numbers, and other personal data. Vidar malware can also capture screenshots, record keystrokes, and log browser activity, among other things.
One of the ways that Vidar malware is distributed is through spam emails or malicious websites. Once a user clicks on a link or downloads a file from one of these sources, the malware will install itself on the system and start collecting data. Vidar malware can also be bundled with other software or installed through fake updates or software patches.
Vidar malware is a serious threat to user privacy and security, and it is important to take steps to protect yourself against it. This includes using anti-virus and anti-malware software, keeping your system and software up to date with the latest security patches, and avoiding suspicious links or downloads from untrusted sources.
If your computer is infected with Vidar malware, it is important to take action as soon as possible to prevent further damage and to remove the malware. Here are some steps you can take:
- Disconnect from the internet: Disconnect your computer from the internet to prevent the malware from communicating with its command and control servers.
- Run a full system scan: Use an updated anti-virus or anti-malware program to perform a full system scan and detect and remove the malware. Make sure the software is up to date with the latest virus definitions and patches.
- Change your passwords: Change your passwords for all your online accounts, including email, banking, and social media accounts. This is because Vidar malware is designed to steal passwords and other sensitive information.
- Monitor your financial accounts: Keep a close eye on your financial accounts and credit reports to detect any suspicious activity or unauthorized transactions.
- Backup important data: Make a backup of all important data and files in case they get corrupted or deleted by the malware.
- Update your system: Make sure your operating system and software are updated with the latest security patches to prevent future infections.
- Seek professional help: If you are not comfortable with removing the malware yourself, seek help from a professional IT or security expert. They can assist you in removing the malware and securing your computer.
Windows Processes Leveraged By Vidar
Vidar malware can leverage various Windows processes to carry out its malicious activities. Some of the processes that Vidar malware has been known to abuse are:
- explorer.exe: Vidar can inject code into the explorer.exe process, which is responsible for managing the Windows desktop and file manager. This allows the malware to capture screenshots and monitor user activity.
- svchost.exe: Vidar can use svchost.exe, which is a generic process that hosts multiple Windows services, to hide its presence and evade detection by security software.
- wininet.exe: Vidar can abuse the wininet.exe process, which provides network connectivity for Windows applications, to exfiltrate stolen data to its command and control servers.
- taskhost.exe: Vidar can hijack the taskhost.exe process, which manages background tasks in Windows, to perform its malicious activities without being detected.
- dllhost.exe: Vidar can use the dllhost.exe process, which is responsible for executing COM objects in Windows, to execute its own code and evade detection.
It’s worth noting that Vidar malware can also use other processes to carry out its malicious activities, and its behavior may vary depending on the specific variant of the malware.
Malware Spread:
- Initial malware infections will start with phishing email or drive-by downloads. Users who are trying to download free software for windows PC are mostly infected with Vidar Infosec stealer.
- Infected machines will start to communicate with Youtube.com and sites.google.com with site redirection.
"C:\Program Files\Internet Explorer\iexplore.exe" "https://www.youtube[.]com/redirect?event=comments&redir_token=QUFFLUhqbnFTbWRVekt6d0tpMUJmQlpQd19FT1JiZUdid3xBQ3Jtc0tsbnNzM3RwRTBxZXZ5cGJWY3RuaE9ZRVQ4ZnpIVHpYd1dpeUlmZTd6NW8zeFJZM2o4VlBZZ2lkUXpjZ2dudjY1NFRkY1FTV2FIZmc5N1JlZkU1ZldEVG5HVU01enYtLVdGLVdOczBmNlNRRGV6d3U5TQ&q=https%3A%2F%2Fsites.google[.]com%2Fview%2Ffreesoftwaresite%2F&stzid=Ugzz0NfHDi-ZHQJw_ch4AaABAg"
- Now lots of people have started to use sites.google.com to host their website and In this case attackers are hosting their webpage with software page links and show the passwords to users.
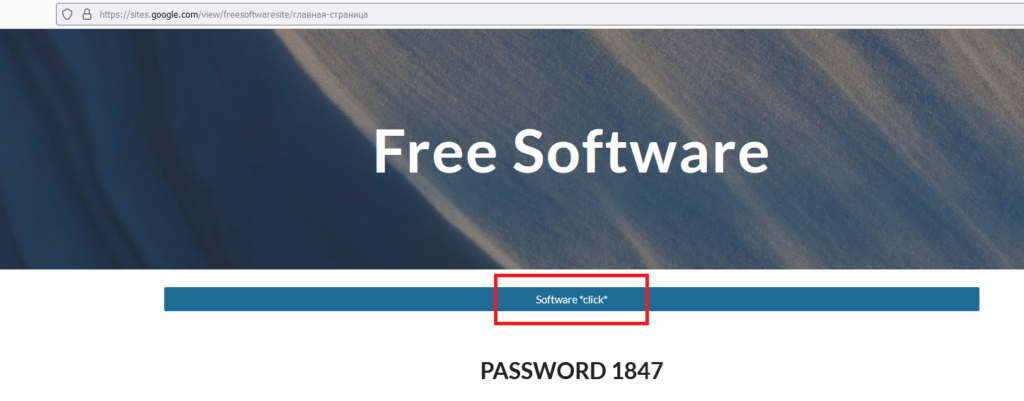
- When user clicks the above highlighted text it will take to mediafire.com were attackers uploaded the compressed a rar file.
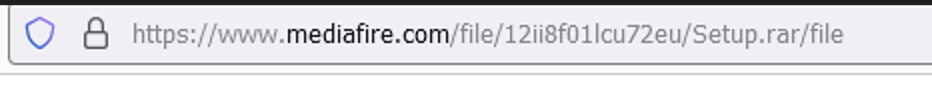
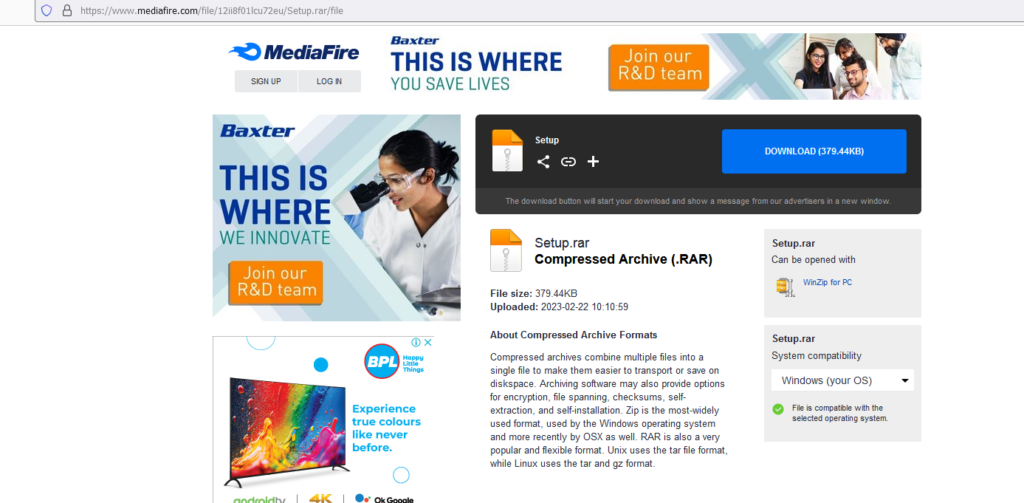
- Affected victim would download the above “setup.rar” and uses the password “1847” to extract the contents of the file.
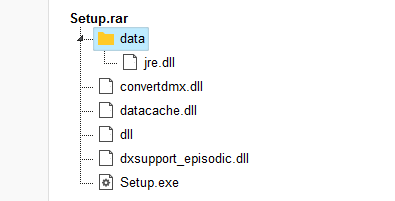
- Downloaded file is under temp folder
""C:\Users\admin\AppData\Local\Temp\Rar$EXb3412.40571\Setup.exe""and Now “setup.exe” is going to be one of the parent process in infected machine. It spawns a"applaunch.exe"( .NET ClickOnce Launch Utility ) which is a legitimate process file to compile thesetup.execodes and do the next actions. - Reads Internet Settings in registry –
HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WPAD\52-54-00-36-3E-FF and HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\INTERNET EXPLORER\SECURITY - Previously launched process “applaunch.exe” Communicates back telegram C2 IP
149.154[.]167.99and does Suspicious DLL Calls –C:\ProgramData\softokn3.dll - Malware Read browser Cookies and steals the credentials –
C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite , C:\Users\admin\AppData\Roaming\Moonchild Productions\Pale Moon\profiles.ini , C:\ProgramData\46982094595765713485915659 and commmuincated back to IP 78[.]46[.]254.12
Malware Leveraging CCleaner
- Malware has already stolen the credentials and still it searches credentials in other cache softwares “CCleaner”
- CCleaner is launched with UAC
"C:\Program Files\CCleaner\CCleaner.exe" /uacand look for personal data to steal under the pathC:\Users\admin\AppData\Local\Microsoft\Edge\User Data\ , C:\Users\admin\AppData\Roaming\Mozilla\Firefox\profiles.ini - Later it launches
"taskhost.exe"( DLL-based services run ) process and reads the file and steals itC:\Users\admin\AppData\Local\Microsoft\Windows\WebCache\WebCacheV01.dat\
Indicators of Compromise
IPs & Domains:
https://sites.google[.]com/view/freesoftwaresite/&stzid=Ugzz0NfHDi-ZHQJw_ch4AaABAg
78[.]46[.]254.12
176[.]113.115.17
149.154[.]167.99
File hashes:
a311b8137f8f47beb0c1cd3a79b97015b7d6a96074c165699ef1e2207d074556
Detection & Response
Splunk:
source=”WinEventLog:*” AND ((Image=”*iexplore.exe”) AND (CommandLine=”*https://www.youtube.com/redirect?event=comments&redir_token=*” OR CommandLine=”*sites.google.com*” OR CommandLine=”*https://sites.google.com/view/freesoftwaresite*”) AND (ParentImage=”*.EXE”) AND (CommandLine=”*\\Users\\admin\\AppData\\Local\\Temp\\Rar*\*.exe*”) AND (Image=”AppLaunch.exe”) AND (CommandLine=”*C:\\Windows\\Microsoft.NET\\Framework\\v4.0.30319\\AppLaunch.exe*”) AND (Image=”CCleaner.exe”) AND (CommandLine=”*uac*” OR CommandLine=”*C:\\Users\\admin\\AppData\\Local\\Microsoft\\Edge\\User Data\\*” OR CommandLine=”*C:\\Users\\admin\\AppData\\Roaming\\Mozilla\\Firefox\\profiles.ini*”) AND (FileName=”*\\Users\*\\AppData\\Local\\Microsoft\\Windows\\Temporary Internet Files\*\*\\*”) AND (FileName=”**.rar”) AND (FileName=”*\\Users\*\\AppData\\Local\\Microsoft\\Windows\\WebCache*”) AND (FileName=”*\\WebCacheV01.dat\\”))
Qradar:
SELECT UTF8(payload) FROM events WHERE LOGSOURCETYPENAME(devicetype)=’Microsoft Windows Security Event Log’ AND “Image” ILIKE ‘%iexplore.exe’ AND (“Process CommandLine” ILIKE ‘%https://www.youtube.com/redirect?event=comments&redir_token=%’ OR “Process CommandLine” ILIKE ‘%sites.google.com%’ OR “Process CommandLine” ILIKE ‘%https://sites.google.com/view/freesoftwaresite%’) AND (“ParentImage” ILIKE ‘%.EXE’) AND “Process CommandLine” ILIKE ‘%\Users\admin\AppData\Local\Temp\Rar*\*.exe%’ AND (“Image” = ‘AppLaunch.exe’) AND “Process CommandLine” ILIKE ‘%C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe%’ AND (“Image” = ‘CCleaner.exe’) AND (“Process CommandLine” ILIKE ‘%uac%’ OR “Process CommandLine” ILIKE ‘%C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\%’ OR “Process CommandLine” ILIKE ‘%C:\Users\admin\AppData\Roaming\Mozilla\Firefox\profiles.ini%’) AND “Filename” ILIKE ‘%\Users\*\AppData\Local\Microsoft\Windows\Temporary Internet Files\*\*\%’ AND “Filename” ILIKE ‘%*.rar’ AND “Filename” ILIKE ‘%\Users\*\AppData\Local\Microsoft\Windows\WebCache%’ AND “Filename” ILIKE ‘%\WebCacheV01.dat\’
Elastic Query:
(process.executable.text:*iexplore.exe AND process.command_line.text:(*https\:\/\/www.youtube.com\/redirect?event\=comments&redir_token\=* OR *sites.google.com* OR *https\:\/\/sites.google.com\/view\/freesoftwaresite*) AND process.parent.executable.text:*.EXE AND process.command_line.text:*\\Users\\admin\\AppData\\Local\\Temp\\Rar\*\\*.exe* AND process.executable.text:”AppLaunch.exe” AND process.command_line.text:*C\:\\Windows\\Microsoft.NET\\Framework\\v4.0.30319\\AppLaunch.exe* AND process.executable.text:”CCleaner.exe” AND process.command_line.text:(*uac* OR *C\:\\Users\\admin\\AppData\\Local\\Microsoft\\Edge\\User\ Data\\* OR *C\:\\Users\\admin\\AppData\\Roaming\\Mozilla\\Firefox\\profiles.ini*) AND file.path.text:*\\Users\\*\\AppData\\Local\\Microsoft\\Windows\\Temporary\ Internet\ Files\\*\\*\\* AND file.path.text:*\*.rar AND file.path.text:*\\Users\\*\\AppData\\Local\\Microsoft\\Windows\\WebCache* AND file.path.text:*\\WebCacheV01.dat\\)
FirEye:
(metaclass:`windows` process:[‘*iexplore.exe’] args:[‘*https://www.youtube.com/redirect?event=comments&redir_token=*’, ‘*sites.google.com*’, ‘*https://sites.google.com/view/freesoftwaresite*’] pprocess:`*.EXE` args:[‘*\\Users\\admin\\AppData\\Local\\Temp\\Rar*\\*.exe*’] process:`AppLaunch.exe` args:[‘*C:\\Windows\\Microsoft.NET\\Framework\\v4.0.30319\\AppLaunch.exe*’] process:`CCleaner.exe` args:[‘*uac*’, ‘*C:\\Users\\admin\\AppData\\Local\\Microsoft\\Edge\\User Data\\*’, ‘*C:\\Users\\admin\\AppData\\Roaming\\Mozilla\\Firefox\\profiles.ini*’] filename:[‘*\\Users\\*\\AppData\\Local\\Microsoft\\Windows\\Temporary Internet Files\\*\\*\\*’] filename:[‘**.rar’] filename:[‘*\\Users\\*\\AppData\\Local\\Microsoft\\Windows\\WebCache*’] filename:[‘*\\WebCacheV01.dat\\’])
Carbon Black:
((process_name:*iexplore.exe AND process_cmdline:(*https\:\/\/www.youtube.com\/redirect?event\=comments&redir_token\=* OR *sites.google.com* OR *https\:\/\/sites.google.com\/view\/freesoftwaresite*) AND parent_name:*.EXE AND process_cmdline:*\\Users\\admin\\AppData\\Local\\Temp\\Rar\*\\*.exe* AND process_name:”AppLaunch.exe” AND process_cmdline:*C\:\\Windows\\Microsoft.NET\\Framework\\v4.0.30319\\AppLaunch.exe* AND process_name:”CCleaner.exe” AND process_cmdline:(*uac* OR *C\:\\Users\\admin\\AppData\\Local\\Microsoft\\Edge\\User\ Data\\* OR *C\:\\Users\\admin\\AppData\\Roaming\\Mozilla\\Firefox\\profiles.ini*)) AND (((process_original_filename:*\\Users\\*\\AppData\\Local\\Microsoft\\Windows\\Temporary\ Internet\ Files\\*\\*\\*) OR (process_name:*\\Users\\*\\AppData\\Local\\Microsoft\\Windows\\Temporary\ Internet\ Files\\*\\*\\*)) AND ((process_original_filename:*\*.rar) OR (process_name:*\*.rar))) AND ((process_original_filename:*\\Users\\*\\AppData\\Local\\Microsoft\\Windows\\WebCache*) OR (process_name:*\\Users\\*\\AppData\\Local\\Microsoft\\Windows\\WebCache*)) AND ((process_original_filename:*\\WebCacheV01.dat\\) OR (process_name:*\\WebCacheV01.dat\\)))
RSA Netwitness:
((Image contains ‘iexplore.exe’) && (CommandLine contains ‘https://www.youtube.com/redirect?event=comments&redir_token=’, ‘sites.google.com’, ‘https://sites.google.com/view/freesoftwaresite’) && (ParentImage contains ‘.EXE’) && (CommandLine contains ‘\Users\admin\AppData\Local\Temp\Rar*\*.exe’) && (Image = ‘AppLaunch.exe’) && (CommandLine contains ‘C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe’) && (Image = ‘CCleaner.exe’) && (CommandLine contains ‘uac’, ‘C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\’, ‘C:\Users\admin\AppData\Roaming\Mozilla\Firefox\profiles.ini’) && (FileName contains ‘\Users\*\AppData\Local\Microsoft\Windows\Temporary Internet Files\*\*\’) && (FileName contains ‘*.rar’) && (FileName contains ‘\Users\*\AppData\Local\Microsoft\Windows\WebCache’) && (FileName contains ‘\WebCacheV01.dat\’))
Microsoft Defender:
DeviceProcessEvents | where (FolderPath endswith @’iexplore.exe’ and (ProcessCommandLine contains @’https://www.youtube.com/redirect?event=comments&redir_token=’ or ProcessCommandLine contains @’sites.google.com’ or ProcessCommandLine contains @’https://sites.google.com/view/freesoftwaresite’) and InitiatingProcessFolderPath =~ @’*.EXE’ and ProcessCommandLine contains @’\Users\admin\AppData\Local\Temp\Rar*\*.exe’ and FolderPath =~ @’AppLaunch.exe’ and ProcessCommandLine contains @’C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe’ and FolderPath =~ @’CCleaner.exe’ and (ProcessCommandLine contains @’uac’ or ProcessCommandLine contains @’C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\’ or ProcessCommandLine contains @’C:\Users\admin\AppData\Roaming\Mozilla\Firefox\profiles.ini’) and FolderPath contains @’\Users\*\AppData\Local\Microsoft\Windows\Temporary Internet Files\*\*\’ and FolderPath endswith @’*.rar’ and FolderPath contains @’\Users\*\AppData\Local\Microsoft\Windows\WebCache’ and FolderPath endswith @’\WebCacheV01.dat\’)
SumoLogic:
((_sourceCategory=*windows* AND (Image=*iexplore.exe) AND (CommandLine=*https://www.youtube.com/redirect?event=comments&redir_token=* OR CommandLine=*sites.google.com* OR CommandLine=*https://sites.google.com/view/freesoftwaresite*) AND (ParentImage = *.EXE) AND (CommandLine=*\Users\admin\AppData\Local\Temp\Rar*\*.exe*) AND (Image = AppLaunch.exe) AND (CommandLine=*C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe*) AND (Image = CCleaner.exe) AND (CommandLine=*uac* OR CommandLine=*C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\* OR CommandLine=*C:\Users\admin\AppData\Roaming\Mozilla\Firefox\profiles.ini*) AND (((\Users\ AND \AppData\Local\Microsoft\Windows\Temporary Internet Files\ AND \ AND \))) AND (.rar) AND (((\Users\ AND \AppData\Local\Microsoft\Windows\WebCache))) AND (\WebCacheV01.dat\)))
GrayLog:
(Image:*iexplore.exe AND CommandLine:(*https\:\/\/www.youtube.com\/redirect?event=comments&redir_token=* *sites.google.com* *https\:\/\/sites.google.com\/view\/freesoftwaresite*) AND ParentImage.keyword:*.EXE AND CommandLine:*\\Users\\admin\\AppData\\Local\\Temp\\Rar*\*.exe* AND Image:”AppLaunch.exe” AND CommandLine:*C\:\\Windows\\Microsoft.NET\\Framework\\v4.0.30319\\AppLaunch.exe* AND Image:”CCleaner.exe” AND CommandLine:(*uac* *C\:\\Users\\admin\\AppData\\Local\\Microsoft\\Edge\\User\ Data\\* *C\:\\Users\\admin\\AppData\\Roaming\\Mozilla\\Firefox\\profiles.ini*) AND FileName:*\\Users\*\\AppData\\Local\\Microsoft\\Windows\\Temporary\ Internet\ Files\*\*\\* AND FileName:**.rar AND FileName:*\\Users\*\\AppData\\Local\\Microsoft\\Windows\\WebCache* AND FileName:*\\WebCacheV01.dat\\)
Securonix:
index = archive AND (rg_functionality = “Microsoft Windows” AND (((@destinationprocessname ENDS WITH “iexplore.exe”) OR (@customstring54 ENDS WITH “iexplore.exe”)) AND (@resourcecustomfield3 CONTAINS “https://www.youtube.com/redirect?event=comments&redir_token=” OR @resourcecustomfield3 CONTAINS “sites.google.com” OR @resourcecustomfield3 CONTAINS “https://sites.google.com/view/freesoftwaresite”) AND (@sourceprocessname ENDS WITH “.EXE”) AND (@resourcecustomfield3 = “*\Users\admin\AppData\Local\Temp\Rar**.exe*”)) AND (((@destinationprocessname = “AppLaunch.exe”) OR (@customstring54 = “AppLaunch.exe”)) AND (@resourcecustomfield3 CONTAINS “C:\Windows\Microsoft.NET\Framework\v4.0.30319\AppLaunch.exe”)) AND ((@destinationprocessname = “CCleaner.exe”) OR (@customstring54 = “CCleaner.exe”)) AND (@resourcecustomfield3 CONTAINS “uac” OR @resourcecustomfield3 CONTAINS “C:\Users\admin\AppData\Local\Microsoft\Edge\User Data” OR @resourcecustomfield3 CONTAINS “C:\Users\admin\AppData\Roaming\Mozilla\Firefox\profiles.ini”) AND (rawevent = “*\Users*\AppData\Local\Microsoft\Windows\Temporary Internet Files***”) AND (rawevent = “**.rar*”) AND (rawevent = “*\Users*\AppData\Local\Microsoft\Windows\WebCache*”) AND (rawevent CONTAINS “\WebCacheV01.dat”))
Google Chronicle:
(target.process.file.full_path = /.*iexplore\.exe$/) and (target.process.command_line = /.*https:\/\/www\.youtube\.com\/redirect\?event=comments&redir_token=.*/ or target.process.command_line = /.*sites\.google\.com.*/ or target.process.command_line = /.*https:\/\/sites\.google\.com\/view\/freesoftwaresite.*/) and principal.process.file.full_path = /.*.*\.EXE$/ and (target.process.command_line = /.*\\Users\\admin\\AppData\\Local\\Temp\\Rar*\\*\.exe.*/) and target.process.file.full_path = “AppLaunch.exe” and (target.process.command_line = /.*C:\\Windows\\Microsoft\.NET\\Framework\\v4\.0\.30319\\AppLaunch\.exe.*/) and target.process.file.full_path = “CCleaner.exe” and (target.process.command_line = /.*uac.*/ or target.process.command_line = /.*C:\\Users\\admin\\AppData\\Local\\Microsoft\\Edge\\User Data\\.*/ or target.process.command_line = /.*C:\\Users\\admin\\AppData\\Roaming\\Mozilla\\Firefox\\profiles\.ini.*/) and (target.file.full_path = /.*\\Users\\*\\AppData\\Local\\Microsoft\\Windows\\Temporary Internet Files\\*\\*\\.*/) and (target.file.full_path = /.**\.rar$/) and (target.file.full_path = /.*\\Users\\*\\AppData\\Local\\Microsoft\\Windows\\WebCache.*/) and (target.file.full_path = /.*\\WebCacheV01\.dat\\$/)
Conclusion
Vidar is known for its ability to evade detection by many anti-virus programs, making it a particularly dangerous threat. To protect against Vidar and other malware threats, it is important to keep your computer’s software up to date, use a reputable anti-virus program, and exercise caution when opening email attachments or downloading software from the internet.



































