
Today, more businesses rely on technological advancements to provide mission-critical functions. However, this has also exposed them to ever-growing cyber threats. Attackers are looking for any weakness to infiltrate their systems, including applications and hardware.
Over the years, there have been many ways to manage and limit IT breaches. However, one of the most important is the ability to identify and swiftly respond to cyberattacks in real time. It minimizes the impact, saving your IT systems. Enter security information and event management (SIEM).
This article outlines what you need to know about SIEM. You’ll learn SIEM, how to build a successful system, and more.
What Is SIEM?
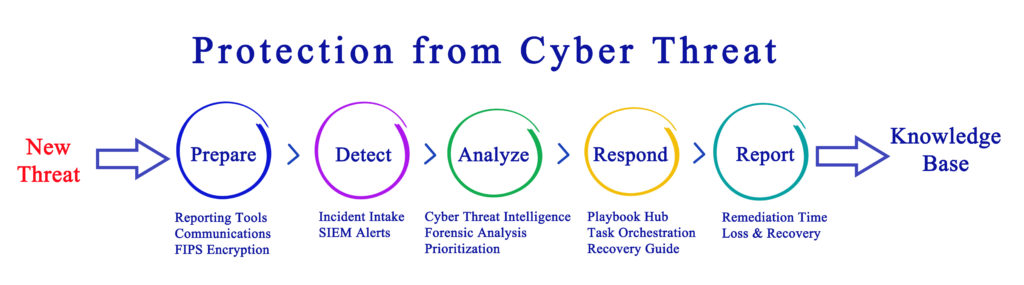
It’s a software solution that collects and analyzes activity from many resources across your network system. It also aggregates security data from servers, domain controllers, and network devices. Then it analyzes, normalizes, and stores that data in a centralized repository. Hence, it’ll be easier for the team to discover trends, detect threats, and respond accordingly.
The system helps businesses identify potential threats before disrupting the production line. It will ensure you maintain your brand image, boosting cash flow. Also, it has replaced manual processes, which could increase the chances of making an error.
The popularity of SIEM has increased exponentially over the years. Thus, there are many vendors you can choose from, which can be challenging if you’re unskilled. However, you can utilize consulting services from Netgain In Cincinnati or any credible local vendor. They’ll help you choose the right SIEM solution for your business.
How To Successfully Deploy SIEM
Building an effective SIEM strategy is daunting, especially if you’re a newbie, and you may end up implementing a futile system. However, here are the practices you might employ to guarantee you have a successful SIEM approach, giving you value for your hard-earned money:
1. Confirm Your Needs
It’s the first step in building a SIEM strategy. Please take your time to understand your current standing and what you want to achieve with SIEM. Start by identifying a list of goals and objectives. Then rank them based on their priority tag. Also, understand which tasks and processes are critical to supporting the SIEM deployment and prioritize them accordingly.
Review your security policies and identify which ones need to be emphasized. It includes existing controls in place to meet the compliance requirements.
Identifying your specific needs allows you to plan adequately. It guarantees that you don’t just implement a generic strategy. Instead, you’ll build a SIEM approach that meets the exact needs and objectives of the business.
2. Begin With A Pilot Run
Most businesses may integrate a SIEM tool into their entire IT architecture. In the event of any mishap, it’ll affect the whole production line, leading to downtime. Hence, it’s crucial to begin with a pilot run. It’ll allow you to test the advancements on a smaller subset of your network system.
The pilot run will allow you to test the feasibility of the SIEM approach. Hence, it’ll be easier to gauge how it might improve your security architecture. Also, it’ll demonstrate the return on investment (ROI).
The subset you use should represent the whole system accurately. It makes it easier to identify weaknesses in security policies and related issues. Thus, it’s imperative to research extensively to ensure you choose the ideal subsets of devices and policies to run the SIEM tool initially.
3. Understand The Pricing Model
The price of SIEM varies depending on the vendor, quality, and your specific needs. There are several pricing models for SIEM systems. For instance, some vendors charge per user while others charge per event. Business leaders must understand how these models work and how each may impact their business processes.
Understanding the pricing models allows you to formulate the proper budget. It ensures you have enough money to fund the SIEM deployment, including cloud integration, increasing its success rate.
4. Have An Effective Incident Response Plan
As mentioned above, the SIEM tool provides real-time monitoring and threat detection. However, the responsibility of accurately responding to threats falls entirely on your business. Thus, it’s crucial to implement a comprehensive incident response plan.
The plan will delegate the responsibility to the right team, reducing the cybersecurity risk. It’ll also describe which documents should be prioritized during an IT breach and protect their integrity.
In Summary
As mentioned above, businesses rely on advancement to provide quality services. However, this has exposed your IT systems to cyber threats. The attackers can use your network devices to infiltrate your system. But a SIEM tool may hugely safeguard them from ever-changing attacks. However, researching is crucial to guarantee you build a successful SIEM approach for your business.


































