Ursnif is a banking Trojan and variant of the Gozi malware observed being spread through various automated exploit kits, Spear phishing Attachments, and malicious links. Ursnif is associated primarily with data theft, but variants also include components (backdoors, spyware, file injectors, etc.) capable of a wide variety of behaviors.
Scenario
- LAN segment range: 10.18.20.0/24 (10.18.20.0 through 10.18.20.255)
- Domain: icemaiden.com
- Domain controller: 10.18.20.8 – Icemaiden-DC
- LAN segment gateway: 10.18.20.1
- LAN segment broadcast address: 10.18.20.255
Icemaiden Company was recently attacked by malware attack and need to quickly the identify malware beacons on the network and isolate the infected machine from network. John is the lead incident responder for this company and his SOC team hunts as per john’s guidelines. Jennifer is the chief information security officer.
Questions to IR/SOC from CISO :
- What is the IP address, MAC address, and host name of the infected Windows host?
- What is the Windows user account name of the victim on this infected Windows host?
- What type of malware was the victim infected with?
- Based on traffic from the pcap, where did the malware likely come from?
- After the initial infection, what type of web page/website did the victim appear to visit?
- Review all logs/Packets and identify the root cause for this incident.
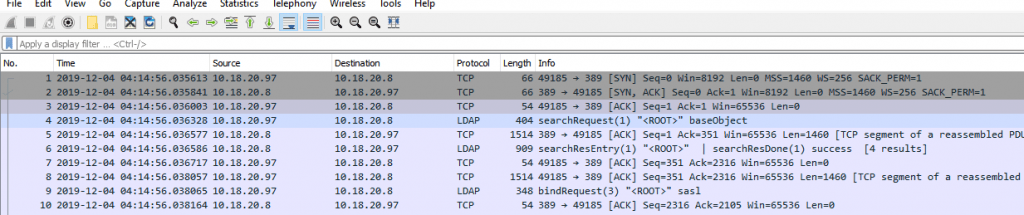
Above packets shows lots and lots of communications that happened in the network. But we want to check specific packets with quick Wireshark filters to identify the attacks much faster.
The first questions asked is to identify the IP address, MAC address, and host name which is infected in the network. Here we like to quickly go with Statistics report for the Source and the destination addresses.
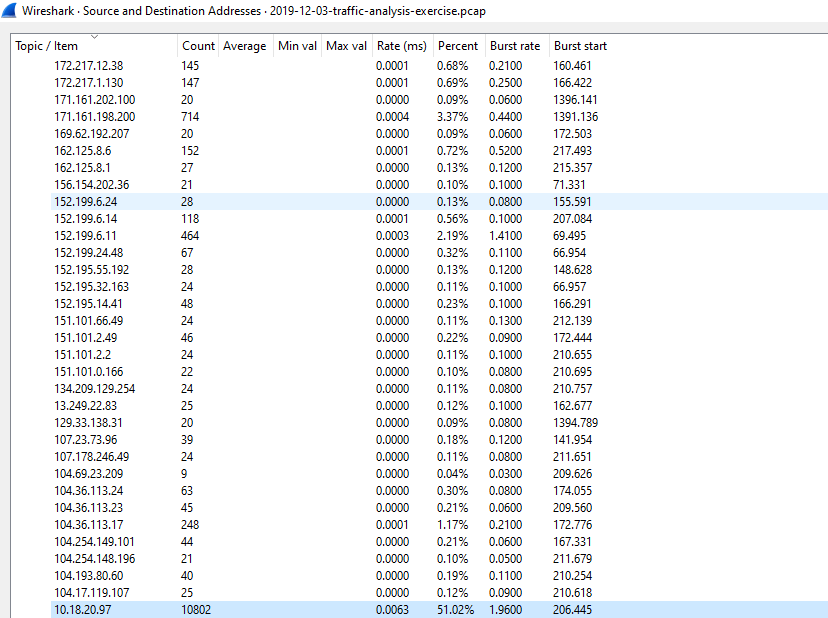
While checking it, we found large counts of connections to the IP address 10.18.20.97. There are around 10802 connections towards the IP 10.18.20.97 with 51 % of traffic is flowed towards this IP address.
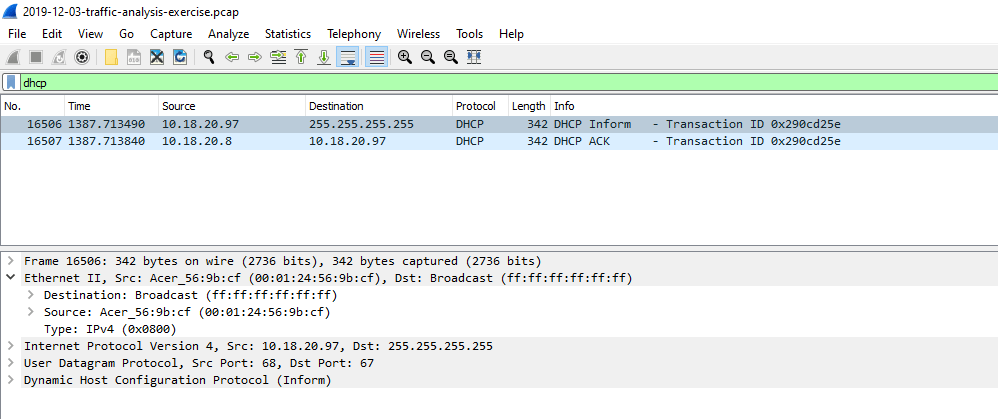
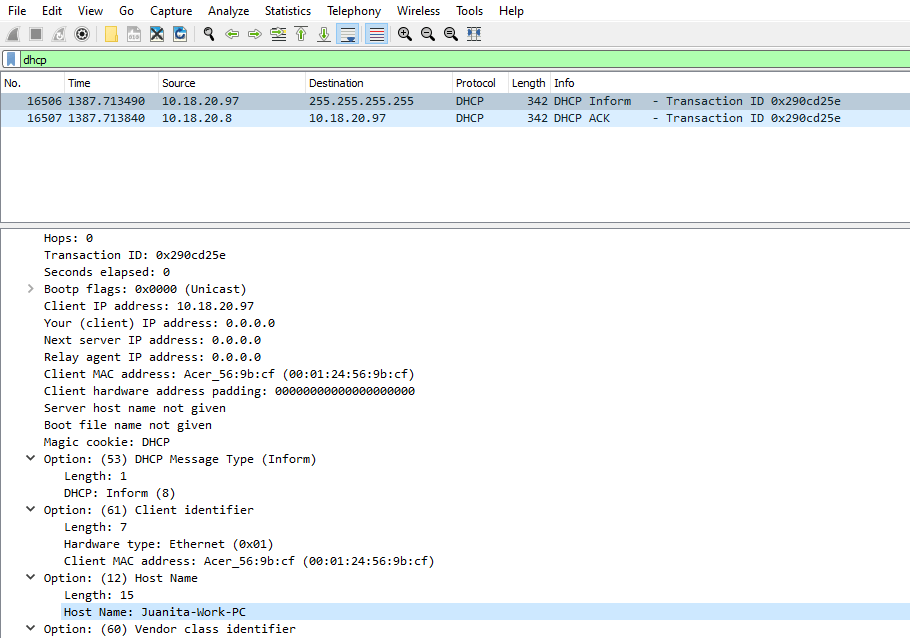
Hunting the DHCP packets gives us additional information such as which host is infected and its MAC address. As below results shows us Source IP 10.18.20.97 with MAC 00:01:24:56:9b:cf is broadcasted and Server 10.18.20.8 tells the IP 10.18.20.97 is free and it can be used with DHCP ACK packet.
While checking Option 12 in the packet, we found that Hostname: Juanita-Work-PC which is requesting to DHCP server. Now we have completed our first set of actions as we suspect the high connections we investigated and took details like (IP address, MAC address and hostname) for further investigation.
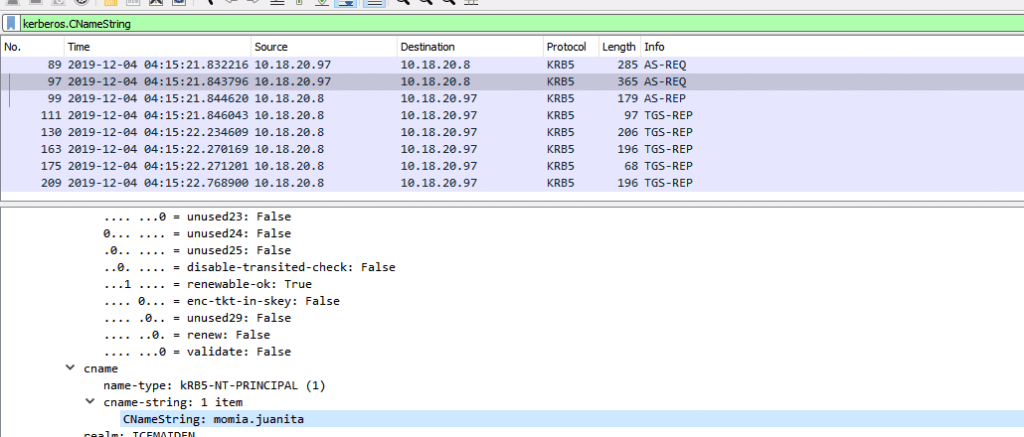
Next we have to find out the Windows user account name on this infected Windows host, we can find out user account names in Kerberos authentication server traffic as part of Active Directory (AD).
In Kerberos Cname contains the user name being authenticated. Here we can apply a Wireshark filter ( kerberos.CNameString ) to check authentications. Below figure shows as: Victim momia.juanita is infected with an malware.
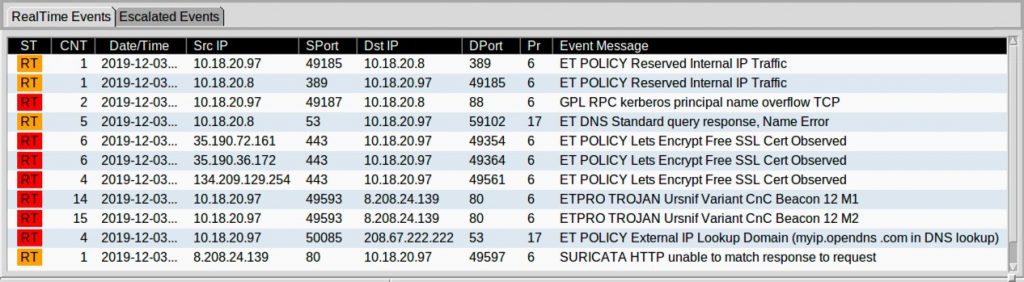
Next questions are, what malware it is, for this we will check some alerts for this IP address 10.18.20.97 in IDS/IPS. We have an event message shows as this is Ursnif.
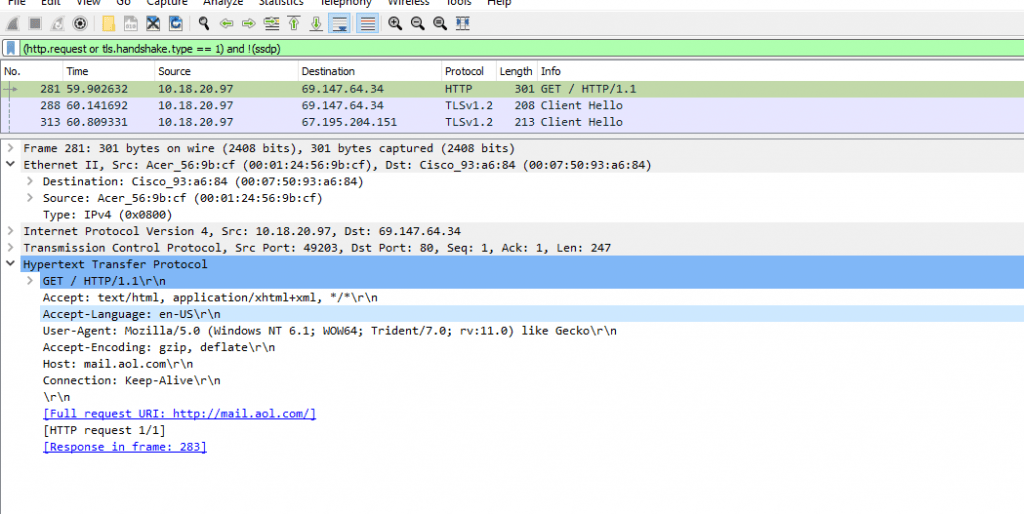
Let’s find the root cause like, We will put a query in Wireshark to filter out http and https requests and excluding SSDP ( Simple Service Discovery Protocol ) to reduce noise. Check below results
Also Read: Top Malware Hiding Techniques in Windows Operating System
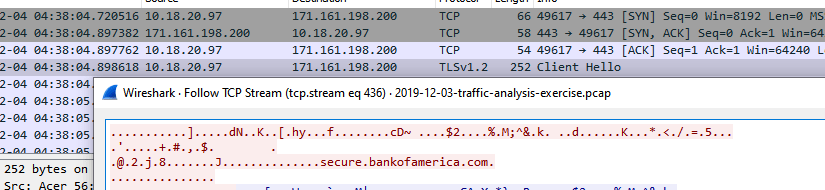
Above Results shows the Full Request URI as http://mail[.]aol[.]com ,IP address “10.18.20.97” with the user “ momia.juanita “ clicked the phishing email on AOL email and which caused this infection. Final question is ,Post infections what type of web page/website did the victim appear to visit ? Request next to mail.aol.com shows https://secure[.]bankofamerica[.]com which is ursnif tries to steal the financial data !!! HAPPY HUNTING



































