Malware is the buzzword that we could hear every other day through some of the other means. There is a drastic increase in the opportunities for threat actors to manipulate legitimate software for malicious purposes. Cybersecurity defenders have as seen lots of sophisticated attacks as threat actor’s behaviors are detected after several days to months.
In the blog post. We will see the Microsoft LNK files and their behaviors. In Microsoft operating system, LNK files are the shortcut file to point to an executable. These shortcut files are used as a direct link to an executable file.
Manipulated. LNK file’s possible actions include masquerade system process to execute malware, Download malicious files from the internet, Delivery of . LNK files with email attachments.
How .lnk files are build?
Let us see this from the attacker’s perspective, creation of this file and doing malicious actions are simple with the below steps.
Right-click on the executable > Create Shortcut > Edit the shortcut target path > Add the windows process which needs to be elevated
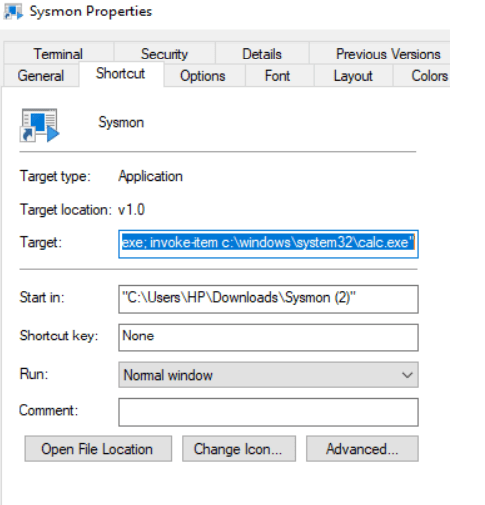
Here we have given the legitimate software calc.exe to open, In action, this can be an unknown executable or it could be malware also.
How this files are executed?
Clicking phishing email attachments from an unknown sender will elevate the malicious actions or Directly clicking the .lnk files will execute its suspicious codes written within LNK files.
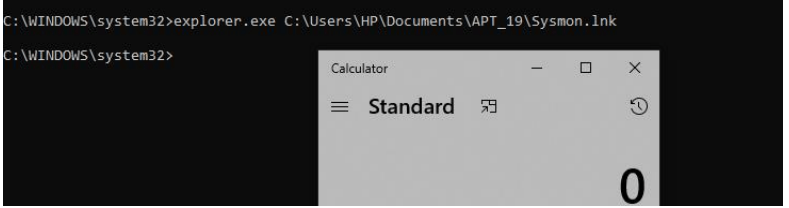
The above figure Illustrates, Microsoft software component Explorer.exe is leveraged to execute the suspicious LNK file. As you see, the calculator has opened successfully. Similar ways malware codes can be executed.
Also Read: Investigation of the Malware Persistence on Defragmented Disk
Hunting the evil on shortcut file?
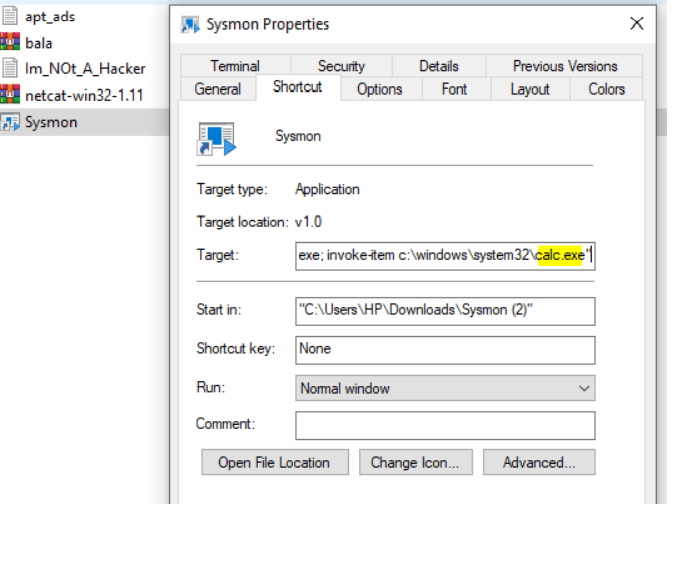
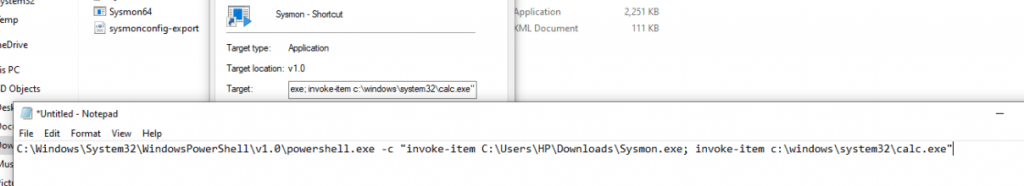
While reviewing the target file path, it reveals as this .lnk file uses a power-shell command like “Invoke-item” followed by specific legitimate software sysmon.exe, When a user clicks an emails attachments from an unknown sender or clicking unknown files will leverage windows inbuilt software components to execute the malicious scripts. In this case, it is “calc.exe” which is a legitimate one. Similar actions can also be performed to execute malicious files on the target. Drilldown your EDR and check the command line arguments for such behaviors and take possible actions to eradicate it. Happy Hunting !!!



































