Dynamic malware analysis is a practical, controlled method for examining malware by running it in a secure environment and observing its behavior.
Unlike static analysis, which looks at the code itself, dynamic analysis allows you to see the malware in action, revealing its real-time behavior and any potentially harmful effects it could have on your systems.
This approach is particularly effective because it doesn’t just provide theoretical insights; it uncovers exactly what the malware does when active, making it easier to identify and prevent future attacks.
Here’s what you can uncover through dynamic analysis:
1. Behavioral Patterns of the Malware
Observing the malware in motion allows analysts to capture its unique behavioral patterns. You can see the exact files it creates, modifies, or deletes, the registry keys it alters, and the specific processes it initiates or injects code into.
In an interactive sandbox like ANY.RUN, you can follow every action as it happens. This level of interaction is invaluable for building precise detection signatures and identifying vulnerable system components. It gives you a detailed roadmap of how the malware impacts a system and what to watch out for in future detections.
| Sign up for free on ANY.RUN today and start analyzing malware with no limits |
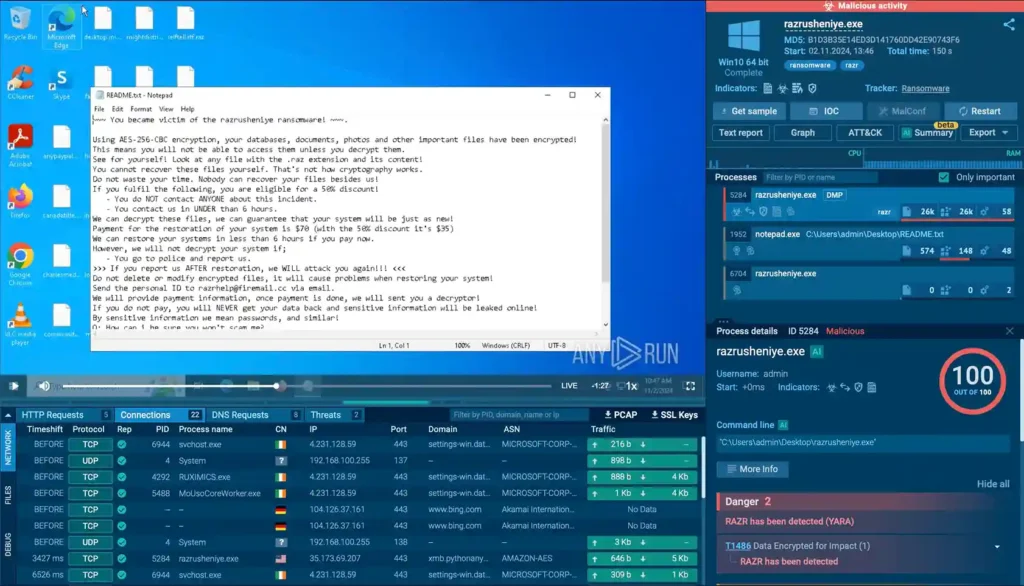
Dynamic malware analysis inside ANY.RUN’s sandbox
2. Indicators of Compromise (IOCs)
Dynamic analysis reveals clear indicators of compromise, such as IP addresses, file hashes, and registry paths, by capturing how the malware interacts with the system.
These IOCs serve as valuable clues for cybersecurity teams, offering concrete data points that can be used to identify, track, and block similar threats across networks.
For instance, here are the IOCs collected for the following malware analysis session ANY.RUN’s sandbox:
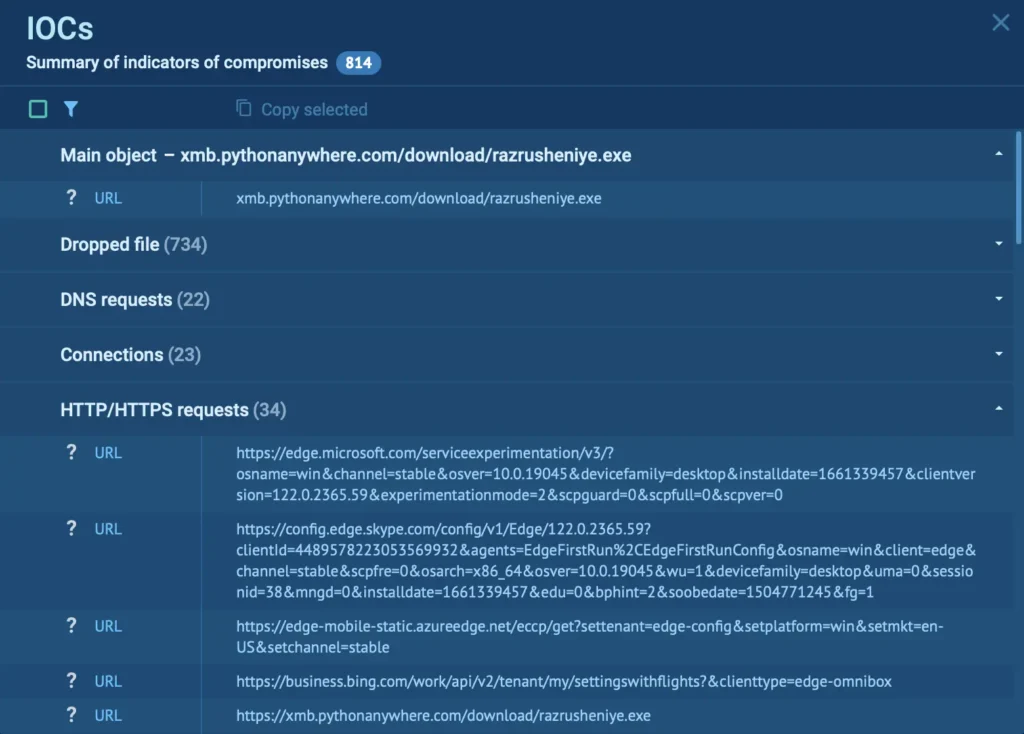
Collection of IOCs inside sandbox
To get all the IOCs associated with the specific task, you’ll need to click on the IOC button on the upper right corner of the screen.
IOC button for the collection of IOCs
3. Command-and-Control (C2) Communication
Many malware variants connect to external servers to receive commands or exfiltrate data. Dynamic analysis lets you capture these C2 channels in action, revealing the domains, IPs, and communication protocols the malware relies on.
With this information, defenders can proactively block these communication lines to minimize the risk of data breaches or future infections.
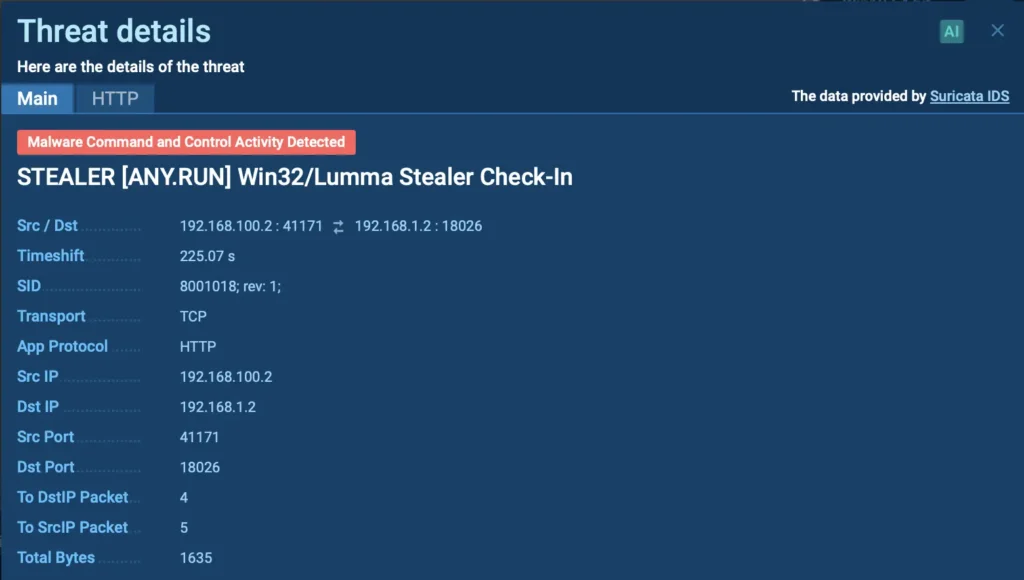
Command and Control activity detected in ANY.RUN sandbox
4. Propagation Methods and Infection Vectors
Malware often includes mechanisms for spreading within networks or infecting additional systems.
With dynamic analysis, you can observe these infection methods, whether through file duplication, code injection, or network exploitation.
This information allows security teams to recognize vulnerable points within a system, effectively closing off infection vectors to prevent further compromise.
For instance, you can easily interact with malicious emails within the controlled environment to understand the initial stages of the attack.
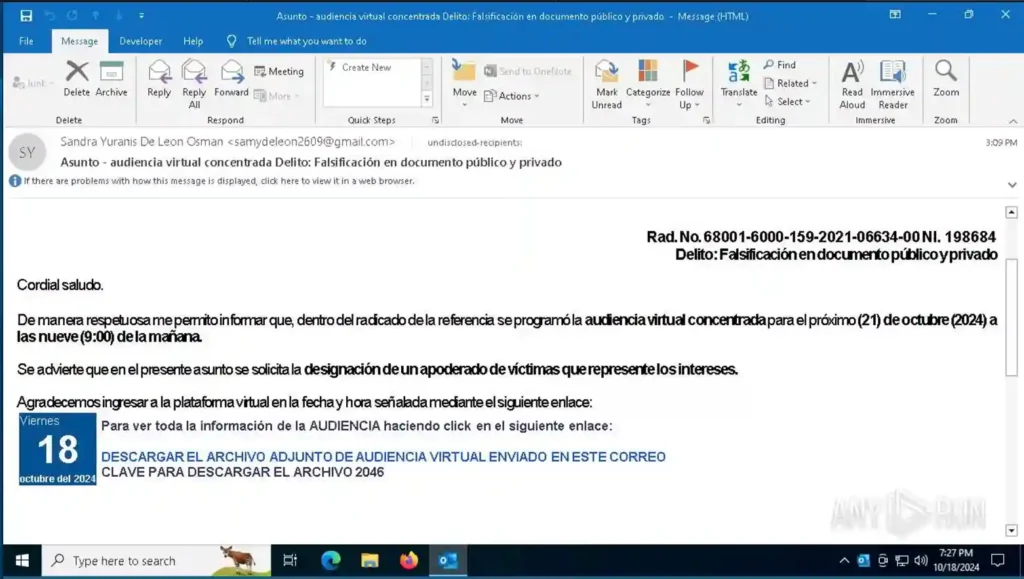
Phishing email with fake invitation in ANY.RUN’s sandbox
5. Resource and System Impact
By executing malware in a controlled environment, analysts can assess its impact on system resources like CPU, memory, and network usage.
Understanding the resource footprint helps distinguish between different types of malware (e.g., cryptominers vs. spyware) and informs strategies for identifying similar threats based on performance anomalies.
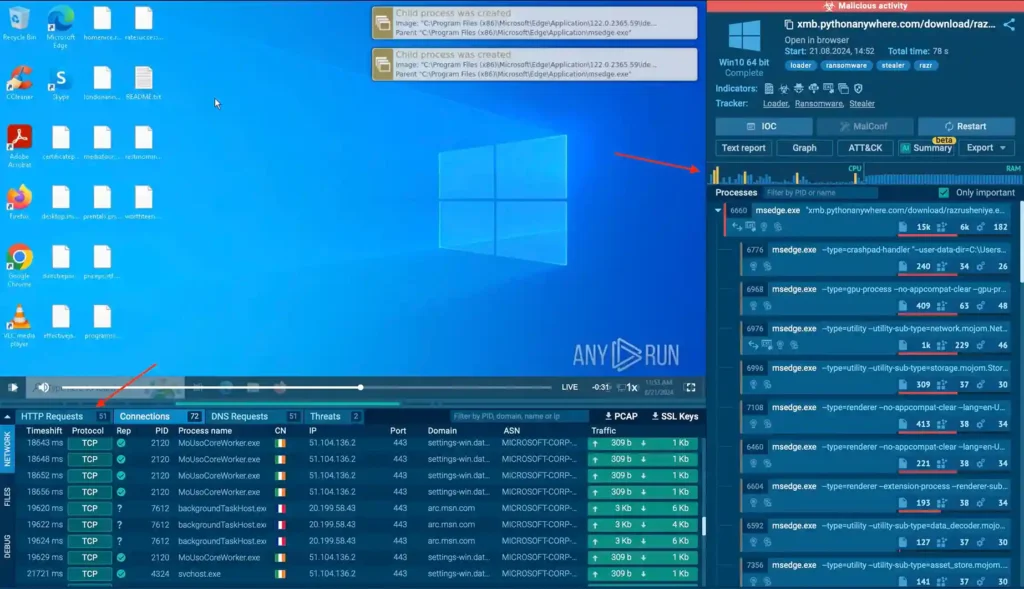
CPU, RAM and network usage inside ANY.RUN’s sandbox
Analyze Malware Quickly and Effectively
Dynamic malware analysis lets you observe malware behavior in real-time, revealing valuable insights for improved security.
With tools like ANY.RUN’s interactive sandbox, you can experience the full range of benefits firsthand—fast, secure, and in-depth.
Sign up for free today and elevate your malware analysis process!



































