An external attacker executes code as a local system on a domain machine, either by social engineering to get access to privileged credentials or by exploiting vulnerabilities that allow code execution. The attacker’s goal is to steal information by moving from a low-value compromised asset to a higher-value domain computer.
It would need to escalate its privileges at some point during its lateral movement activities, via one of the privilege escalation strategies. When malware or an attacker successfully escalates privileges on a compromised system, it gains the ability to undertake stealthier lateral movement, usually by doing operations as a privileged user and avoiding mitigations such as User Account Control.
Access Token:
- Access tokens are used by Windows applications to access APIs. An access token contains information like who initiated a process, the app that generated the token and its expiry time.
- An access token is part of a user’s logon session, and it also contains their credentials for Windows single sign on (SSO) authentication to access local or remote network services.
- When a user signs on to a machine ((irrespective of the logon type), the system generates an access token for them. With this access token, Windows handles the user’s identification, security, and access rights on the system, effectively selecting what system resources they may access and what tasks they can accomplish.
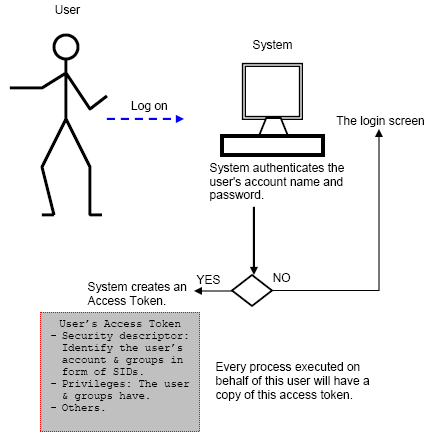
An access token for a user is basically a kernel object that serves as a unique identifier for that user in the system, but it also contains many other details such as groups, access rights, process integrity level, privileges, and so on. There are two kinds of access tokens:
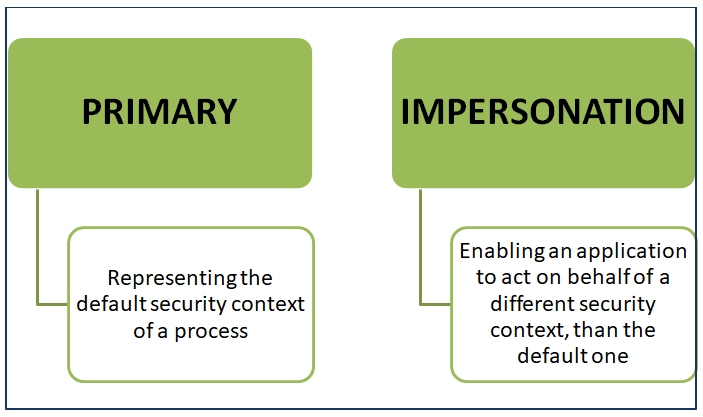
These access tokens remain on a computer not only for the duration of the session, but also until the computer is rebooted. This circumstance occurs to make it easier to gain access to resources that are secured by authentication and authorization systems without having to re-enter credentials with each access attempt. The caching of access tokens is a vulnerable feature that attackers can use to get additional access and move around the network.
Once the attacker gains an initial foothold on the target by compromising the initial system, they would want to move around the network laterally to access more resources or critical assets. One of the ways for an attacker to achieve this is to use the identity or credentials of already logged-on users on the compromised machine to pivot to other systems or escalate their privileges and perform the lateral movement in the context of another logged-on higher privileged user. Process access token manipulation helps the attackers to precisely accomplish this goal.
What is access token manipulation?
- An attacker can manipulate access tokens to make a process appear to be initiated by a different user account, when in reality, the request was originated by the attacker’s account in your network.
- Attackers use access tokens to escalate privileges from administrative to SYSTEM level, allowing them to undertake malicious operations and remotely access systems in your network to take advantage of various system processes.
Manipulating Access Token by injecting malware:
Process tokens are used by a variety of malware and advanced persistent threats to achieve higher rights on the system. Malware can achieve this objective in a variety of ways. However, it would exploit the Windows APIs to perform token stealing or token impersonation in order to get higher privileges and continue its lateral movement operations via all of these channels. Few examples are given below:
- If the current logged-on user on the compromised or infected machine is a member of the administrator group of users OR is running a process with higher privileges (e.g., by using the “runas” command), malware can take advantage of the privileges of the process’s access token to elevate its privileges on the system, allowing it to perform privileged tasks.
- Malware can enumerate the Windows processes running with higher privileges (typically SYSTEM level privileges), obtain the access tokens for those processes, and utilise the acquired token to launch new processes. As a result, the new process is launched in the context of the SYSTEM user, as represented by the token.
- Malware can also perform a token impersonation attack, in which it copies the access tokens of higher-level SYSTEM processes, converts them into impersonation tokens using appropriate Windows functionality, and then impersonates the SYSTEM user on the infected machine, thereby elevating its privileges.
- These token manipulation attacks will allow malware to authenticate to a remote network resource using the credentials of the currently logged on user or another privileged user, allowing it to advance its lateral movement activities.
- These attack approaches allow malware to escape several mitigations such as user authentication, access control lists, and heuristic detection techniques, allowing malware to move across the network more stealthily.
Methods used to manipulate access tokens:
Access tokens are obtained in one of three ways by the attackers:
1-Theft of access tokens:
An attacker can copy and use existing tokens from other processes to undertake malicious activities using the built-in Windows API functions:
- To make duplicate tokens of existing access tokens, utilise the DuplicateTokenEx() function.
- The ImpersonateLoggedOnUser() function is used to run the process as another user. The attackers make certain that the impersonated user has all of the required rights to complete the task.
- Additionally, attackers can assign an impersonated token to a thread using the SetThreatToken() function.
2-Using a stolen access token to create a new process:
Intruders can utilize the CreateProcessWithTokenW() function to create a new process with a duplicated token. The attackers can use this function to generate tokens that implement the security context of any user they want to impersonate.
3- Creating Logon sessions:
If an attacker has the credentials for any user account, they can use the LogonUser() function to create logon sessions for them remotely. They can then gain a token from the security context of the logged in user, which they can give to a thread to launch a process.
Mitigation:
- Since attackers can only use access tokens and their built-in functions from a privileged user account, it’s critical to keep an eye on all privileged user accounts for suspicious activity. These accounts can create, disable, and assign permissions to system and user accounts, so keep an eye on them.
- Use the principle of least privilege (POLP) to ensure that no user or role has greater privileges than are required.
- Regularly review your Group Policies to ensure that only authorized people are able to create, duplicate, or change access tokens.
- Logins made via the Command Line Interface should be monitored.
- Usage of runas command has to be monitored at proximity to identify impersonation.
Event ID 4624:
The Windows Security Log entry “4624: An account was successfully logged on” can be used to track account impersonation activities. However, determining whether such an event is part of an attack or part of normal activity is difficult. If the account to whom the impersonation is being created, particularly delegate impersonation, has high privileges on the domain, it’s worth looking into.
Conclusion:
An access token is the most prioritized part of the authentication. If the access token falls in dirty hands, then adversaries can use it in lateral movement and in many attacks. Taking security precautions increases your chances of detecting an intruder who steals data from an authorized account.



































