Overview
APT-Hunter is the threat hunting tool for windows event logs which will detect APT movements and uncover suspicious activities. It was written by ahmedkhlief. This tool will be useful for Threat Hunter, Incident Responder, or forensic investigators. A list of default rules within this tool will detect the indicator of attack which includes the apt techniques and map the tactics and techniques of the Mitre ATT&CK framework to Windows event log event IDs.
APT-Hunter Features
- Provide output with time sketch format to upload it directly and start analyzing the timeline.
- Events Categorized based on Severity to make the filtering easy and focus on what important.
- Have A log collection automation script to collect all the required logs to save the time required to export important logs .
- Gather and analyze ( Sysmon , Security , System , Powershell , Powershell_Operational , ScheduledTask , WinRM , TerminalServices , Windows_Defender ) .
- This rule tested in many real incidents and provided a great information that reduced the time to detect initial evidence .
- Easy to add new detection rule as the fields clear and syntax easy to use.
- Support windows event logs exported as EVTX and CSV .
Events Detected by APT-Hunter
- [ T1086 ] Detecting Powershell with Suspicious Argument using sysmon logs
- [ T1543 ] Detecting Sc.exe manipulating windows services
- [ T1059 ] Detecting wscript or cscript running script
- [ T1218.005 ] Detecting Mshta found running in the system
- [T1053] Detecting Scheduled Task manipulation
- [T1047] Command run remotely Using WMI
- [T1082] System Information Discovery
- [T1117] Bypassing Application Whitelisting with Regsvr32
- Prohibited Process connecting to the internet
- Detecting Psexec running in the system
- Detecting Prohibited Process connecting to the internet
- Detect Exchange Web service exploitation, such as ( CVE-2020-0688 )
- Detecting password spray attack using security logs
- Detecting Pass the hash attack using security logs
- Detecting Suspicious Attempt to enumerate users or groups using security logs
- Detecting Powershell Operation including TEMP Folder using Powershell operational logs
- Detecting Suspicious PowerShell commands using multiple event IDs using Powershell operational logs
- Detecting Suspicious PowerShell commands using multiple event IDs using Powershell logs
- Detecting connecting RDP from socks proxy using terminal services logs
- Detecting connecting RDP from public IP using terminal services logs
- Detecting connection is initiated using WinRM from machine Powershell remoting
- Detecting connection is initiated using WinRM to machine Powershell remoting
- Detecting User Creation using Net command using security logs
- Detecting Process running in suspicious location using security logs
- Detecting Privilege Escalation using Token Elevation using security logs
- Detecting suspicious executable running using security logs
- Detecting suspicious PowerShell commands using security logs
- Detecting User Created through management interface using security logs
- Detecting Windows shutting down Events using security logs
- Detecting User added to local group using security logs
- Detecting User added the user to a global group using security logs
- Detecting User added the user to a universal group using security logs
- Detecting User removed from the global group using security logs
- Detecting User removed from the universal group using security logs
- Detecting User removed from the local group using security logs
- Detecting User removed from the global group using security logs
- Detecting User account removed using security logs
- Detecting Audit log cleared.
- Detecting System audit policy changes using security logs
- Detecting scheduled tasks creation using security logs
- Detecting scheduled task deletion using security logs
- Detecting scheduled task updates using security logs
- Detecting schedule task enabled using security logs
- Detecting schedule task disabled using security logs
- Detecting Windows Defender took action against Malware using windows defender logs
- Detecting Windows Defender failed to take action against Malware using windows defender logs
- Detecting Windows Defender Found Malware using windows defender logs
- Detecting Windows Defender deleted history of malware using windows defender logs
- Detecting Windows Defender detected suspicious behavior Malware using windows defender logs
- Detecting Windows Defender real-time protection disabled using windows defender logs
- Detecting Windows Defender real-time protection configuration changed using windows defender logs
- Detecting Windows Defender scanning for malware is disabled using windows defender logs
- Detecting schedule task registered using scheduled tasks log
- Detecting schedule task updated using scheduled tasks log
- Detecting schedule task deleted using scheduled tasks log
- Detecting System Logs cleared using system logs
- Detecting Service Installed with executable in TEMP Folder using system logs
- Detecting Service installed in the system using system logs
- Detecting Service start type changed using system logs
- Detecting service state changed using system logs
Install Python Requirements :
evtx
netaddr
numpy
pandas
python-dateutil
pytz
six
XlsxWriter
Installation & Start Guide
A Simple command-line option to get install and uninstall APT-Hunter.
• Download the tool using this filename: APT-Hunter-main-Windows-V1.1-Stable.zip , using this link
• Extract the Zip File
• To extract event logs, Allow exceptions on script execution policy on PowerShell to run scripts from apt-hunter.
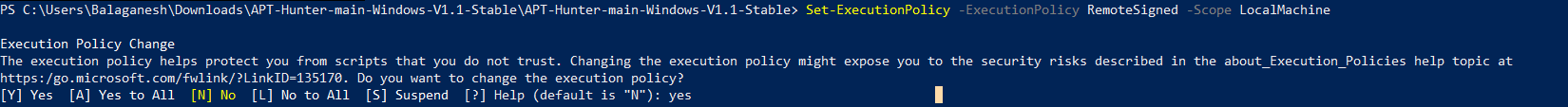
• Run the script .\windows=log-collector-full-v3-csv.ps1 to collect all events from the destination machine.
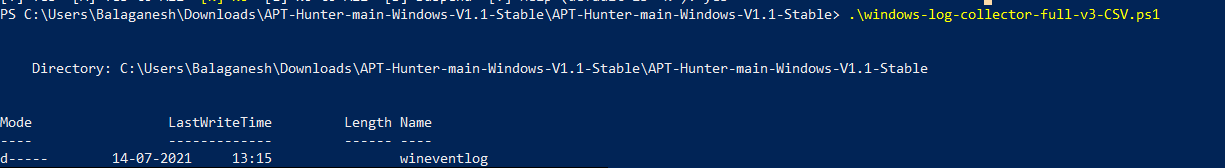
- Wineventlog file shows that logs extraction was successful. Now it’s time to run the APT-HUNTER tool against these event logs to get detection for possible APT techniques.
Also Read : What is the MITRE ATT&CK Framework? How Is It Useful
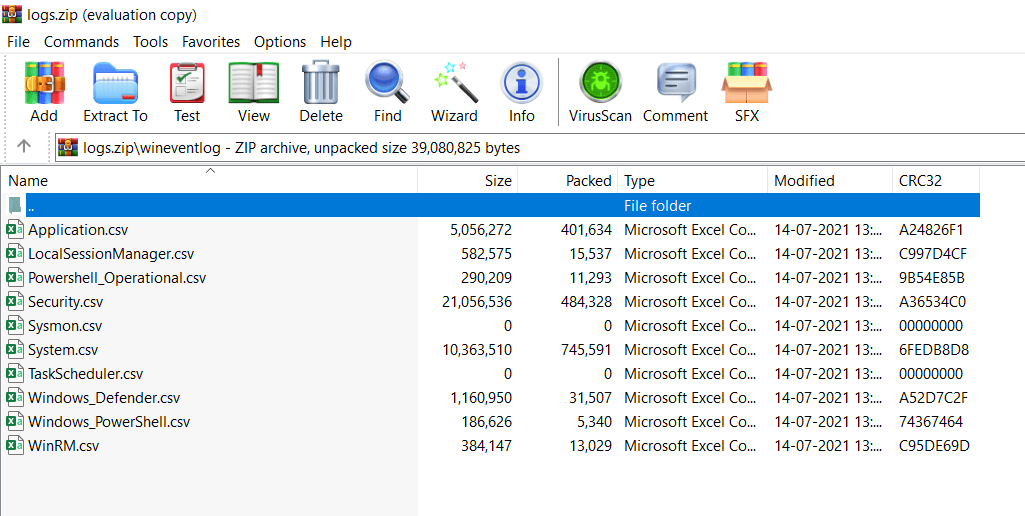
Working with APT-Hunter
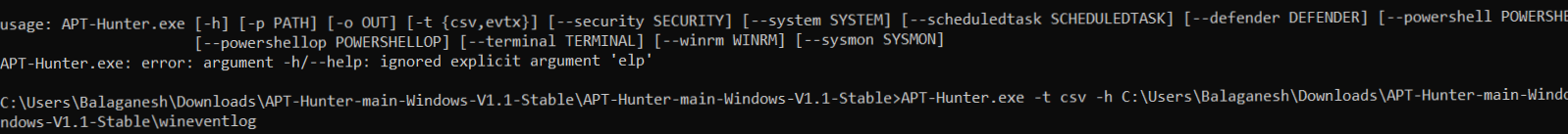
- Run the APT-Hunter tool with the collected log files directory and wait for some seconds.
-t = FileFormat ( We have collected logs in csv format )
-P = Log File Path ( Mapping the log file location )
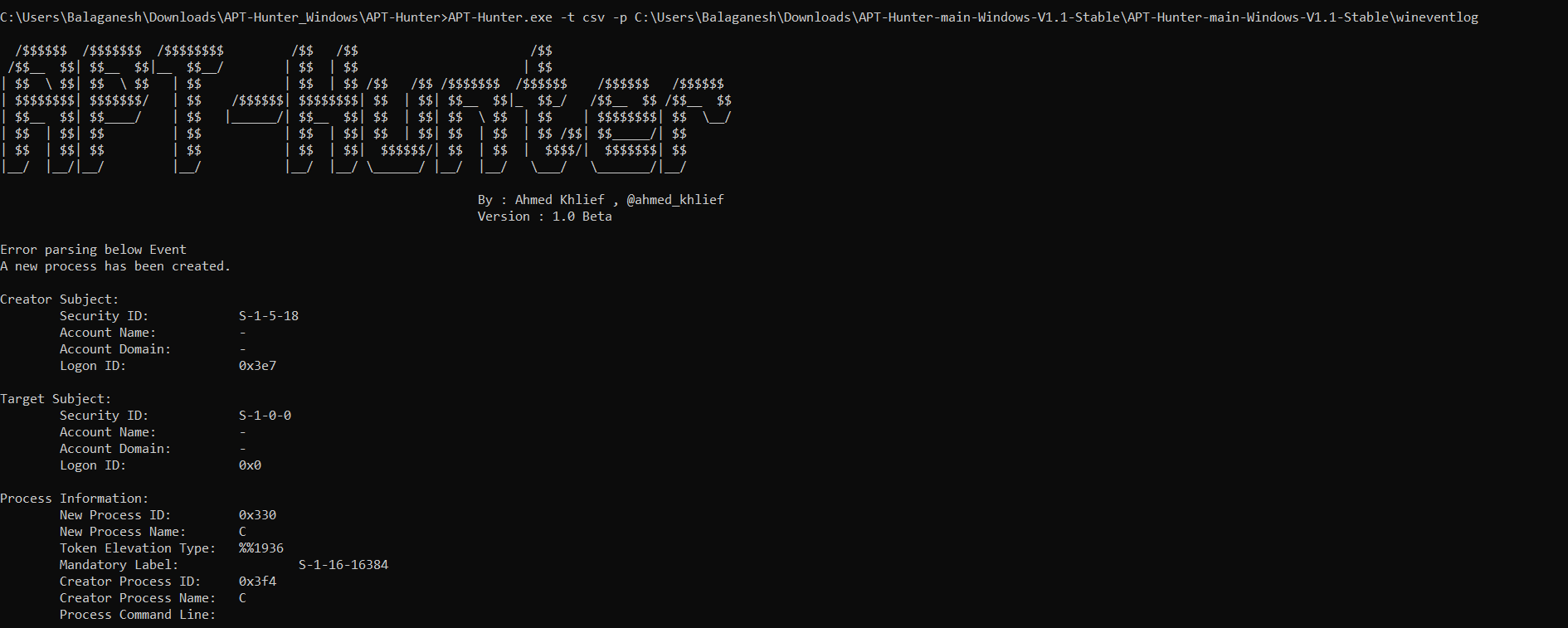
- Tool with run and check the default rules and results will be populated on this console
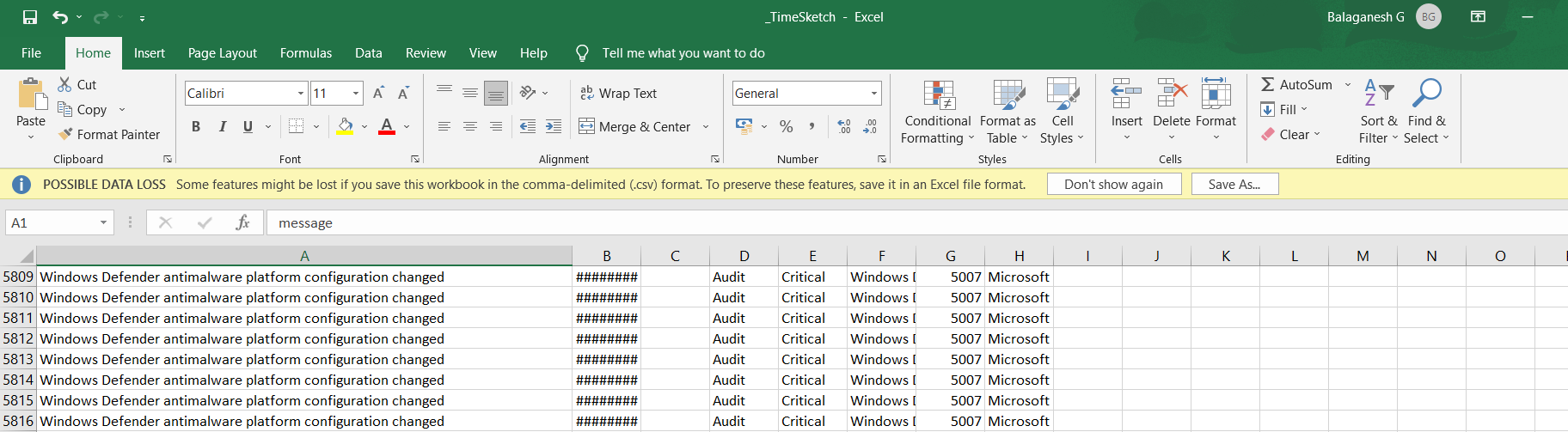
- Results are Exported in the APT-Hunter Folder under the file name _Report.xlsx and _TimeSketch.xlsx , Analyst can use this file to quickly check the security risk level.
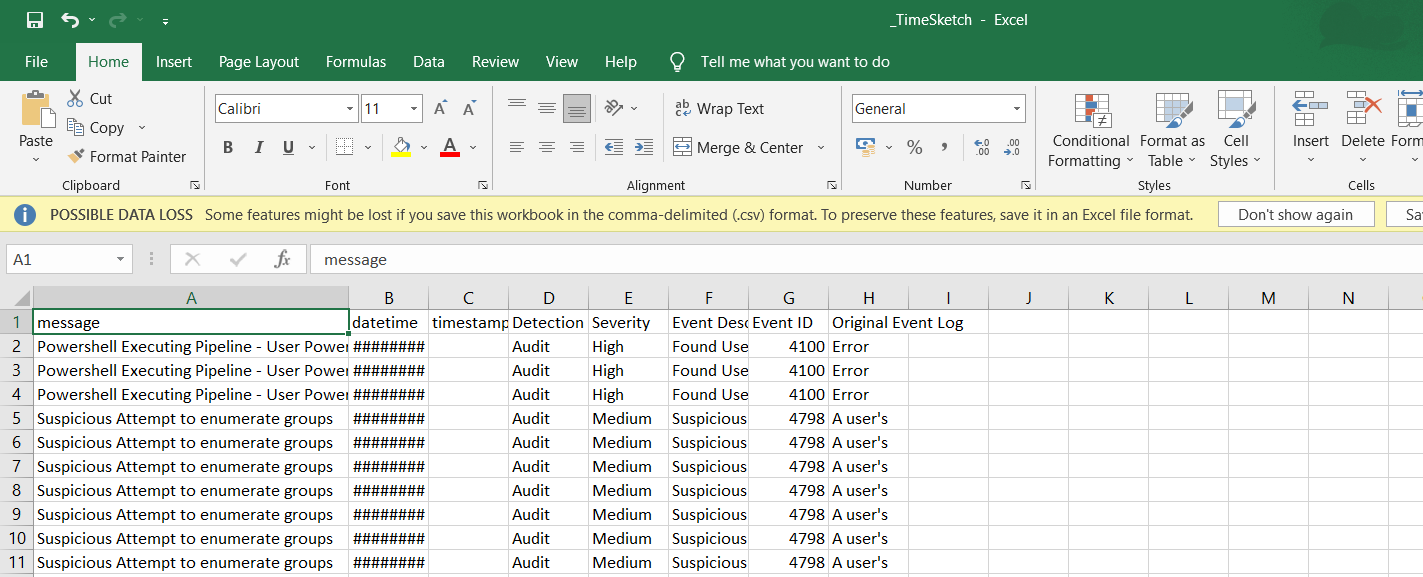
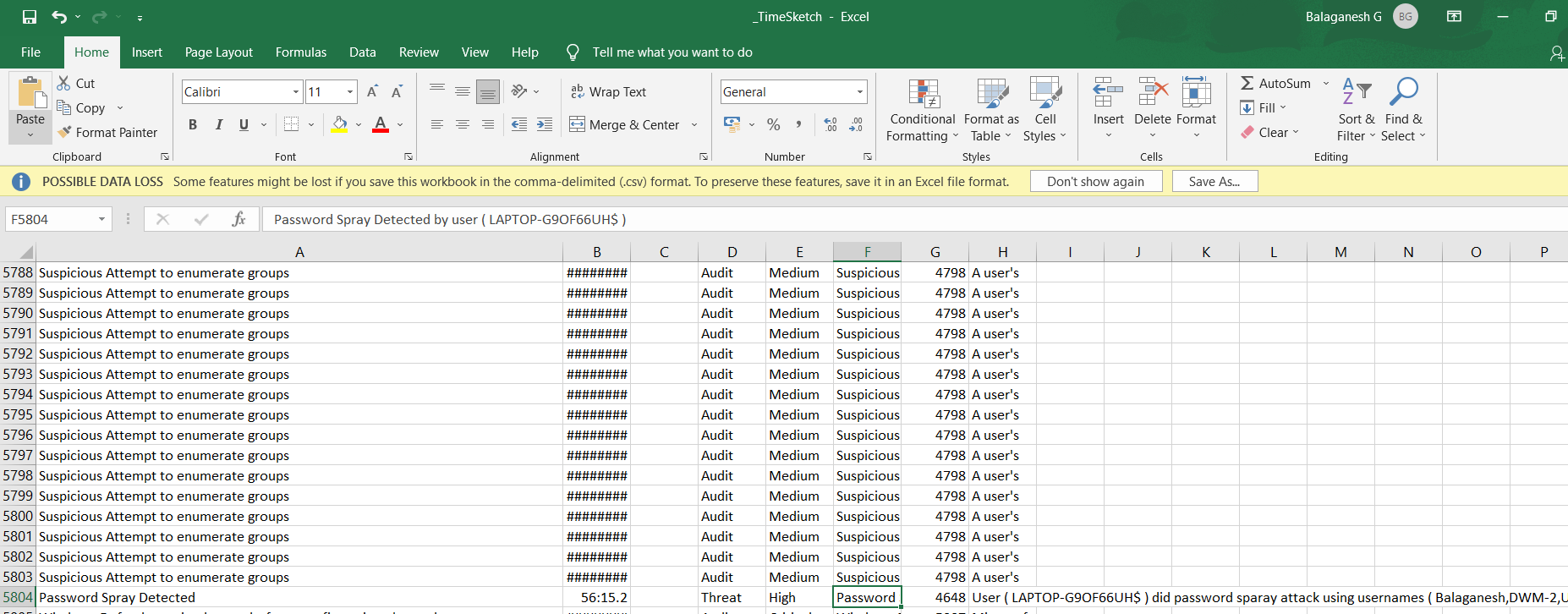
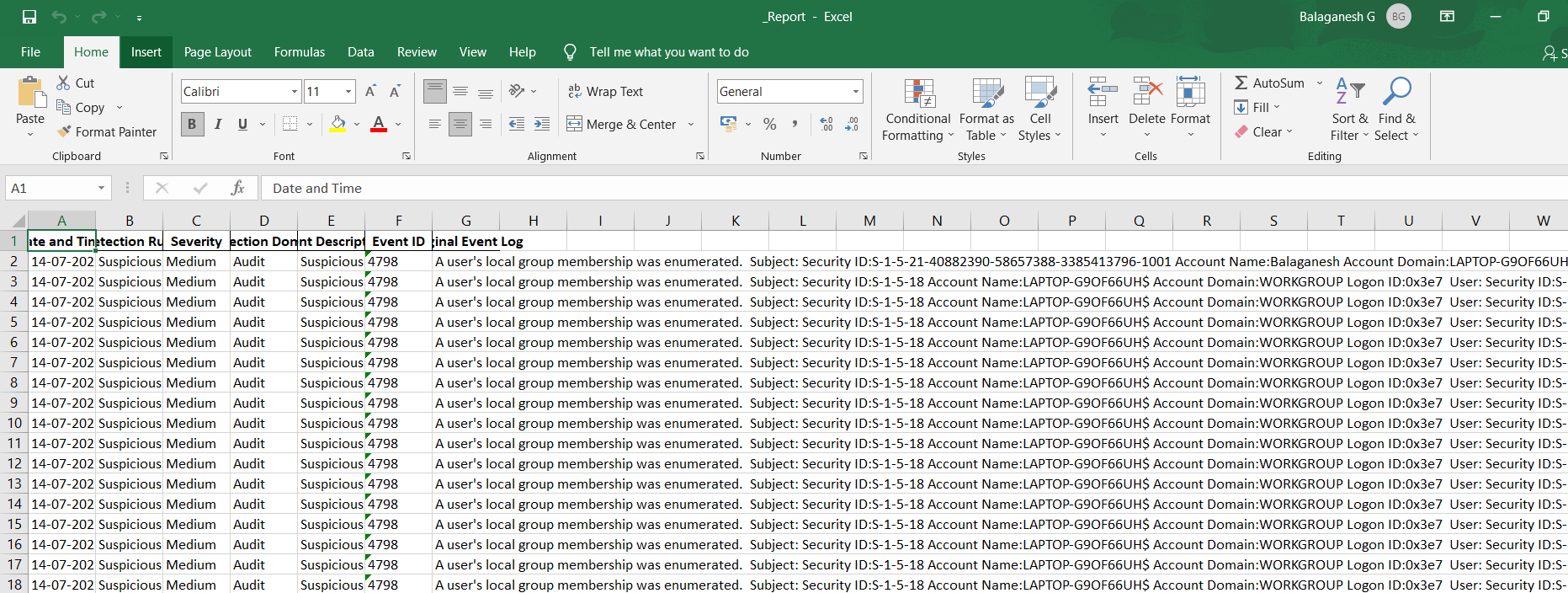
- Report.xlsx : This excel sheet will have details of the events detected from every windows log provided to APT-Hunter.
- TimeSketch.csv : This excel sheet will have details of the time sketch in order to have timeline analysis that will help you see the full picture of the attack.



































