Overview
Microsoft Autoruns v14.06 is a Microsoft Sysinternals tool written by Mark Russinovich, an excellent application that enables you to find the malware auto-starting locations on boot finds programs that are configured to run during system bootup or login. Autoruns reports Explorer shell extensions, toolbars, browser helper objects, Winlogon notifications, auto-start services, and much more.
It can be operated on both a command-line interface and GUI. Most significant is this tool to check third-party auto-starting images that are configured for the accounts on a system. Integration of the popular Virustotal in the tool provides more insights into the suspicious files that are hiding in the system. Much more to do with autostart utilities, Let’s get started.
Installation steps
- Download Autoruns for Windows v14.06 from https://docs.microsoft.com/en-us/sysinternals/downloads/autoruns
- Extract the .zip file.
- Run the .exe file for your system as administrator in command prompt.
- For a 32-bit system, choose Autoruns.
- For a 64-bit system, choose Autoruns64.
Also Read: FireEye’s Open-Source Tool – CAPA to Identify Malware Capabilities
Working with Autoruns
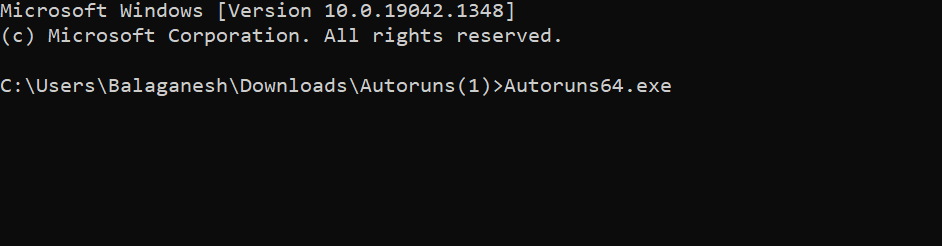
The above figure shows, Autoruns64.exe is started in command prompt, and immediately a graphical window pops up and shows the list of images that are enabled to startup on boot.
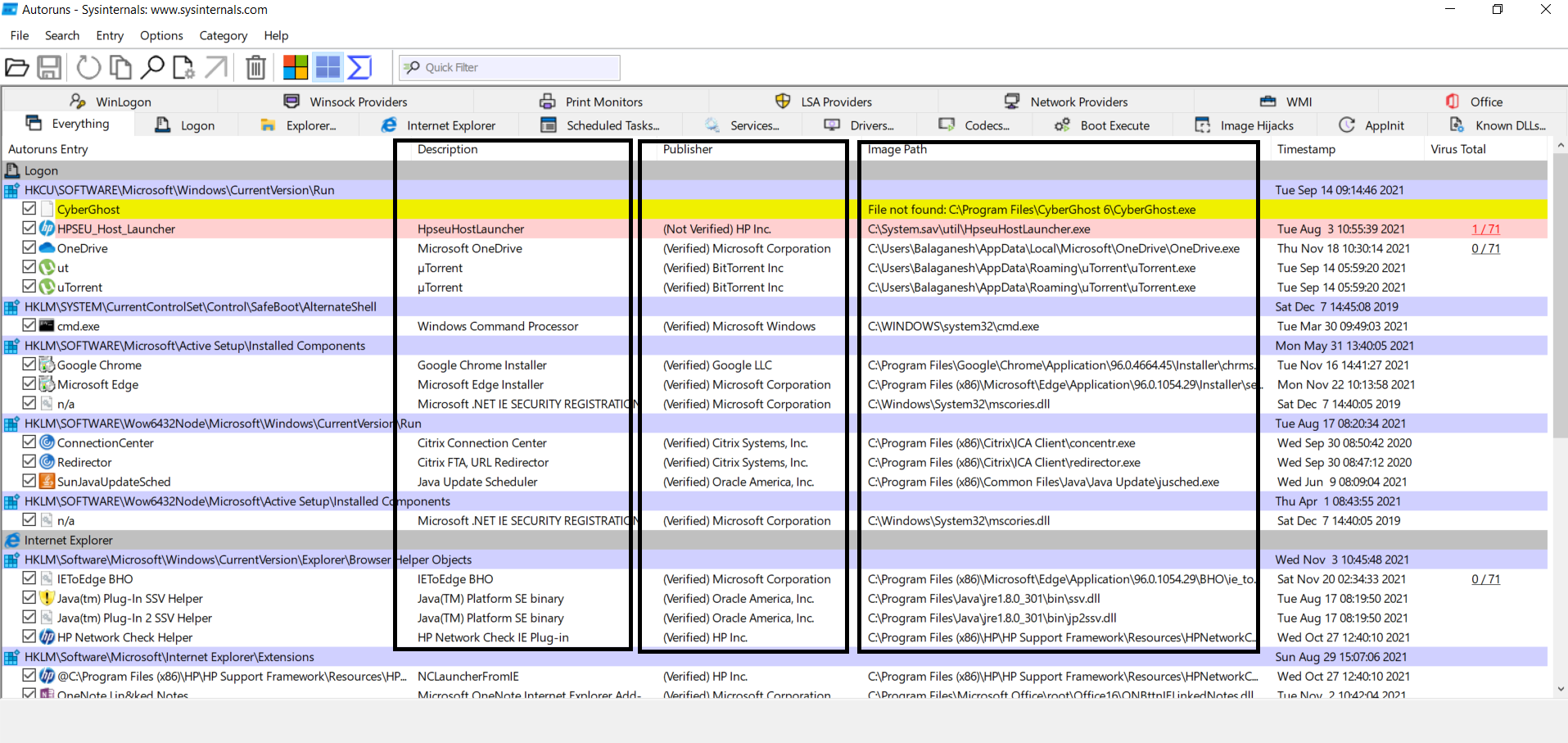
The above figure shows a list of information about the autostart image path, publisher names, descriptions, and more. Some of the publishers are shown in red line means that is not verified. Verified publishers are shown in white lines. Yellow lines state file is not found. To cut off the noise of most trusted publishers we will apply the below filters to find the unknown publisher’s image paths.
Also Read: Dynamic Malware Analysis – Procmon to Extract Indicators of Compromise
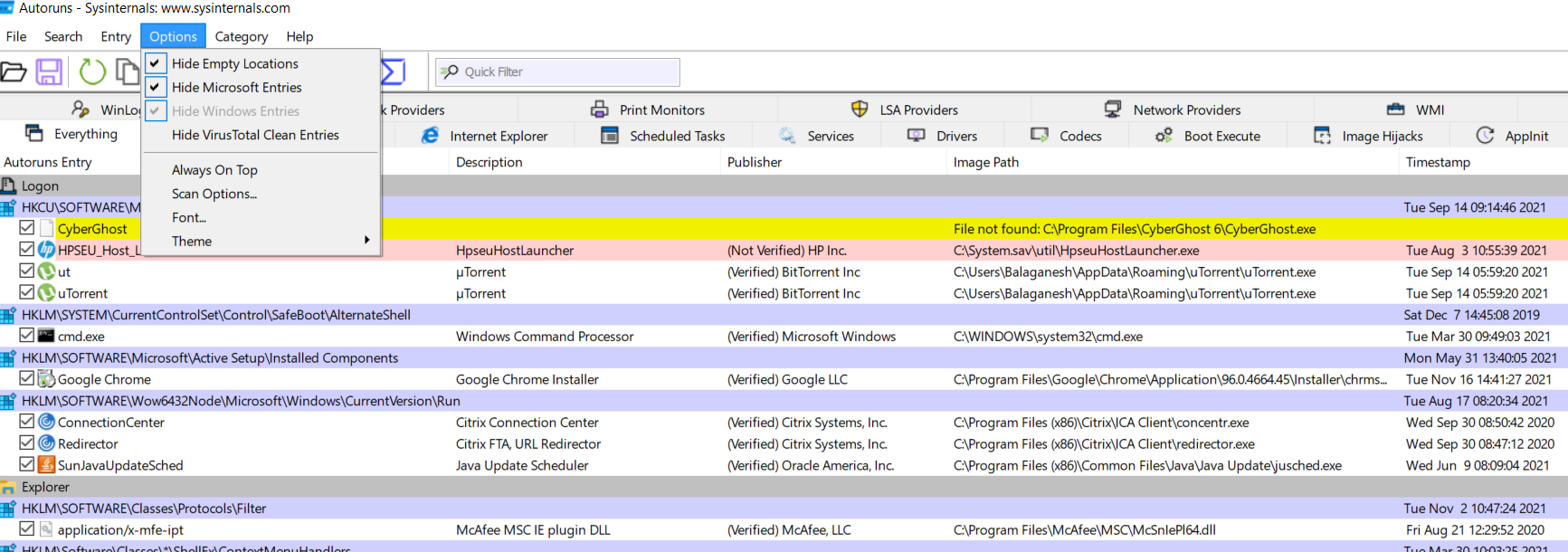
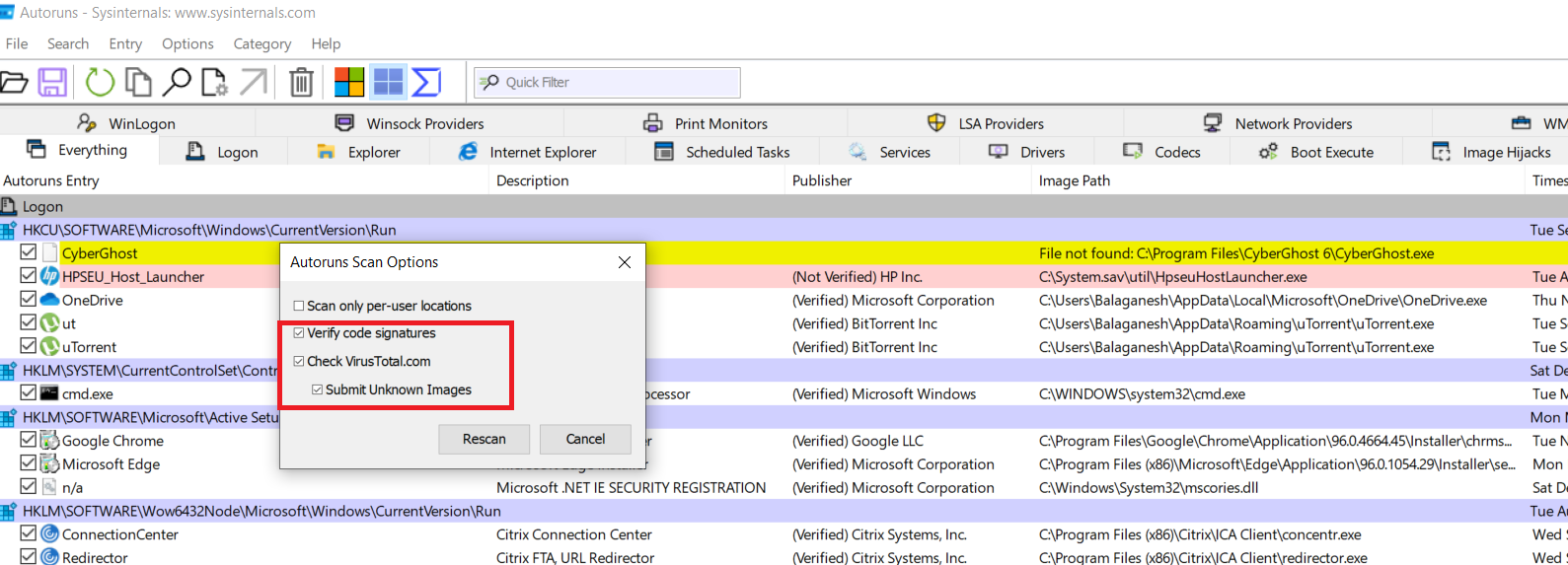
The above figure illustrates, Hiding the empty locations, Microsoft entries, and windows entries will temporarily exclude Microsoft publisher executables. To complete the actions go to scan options and enable verify code signatures, check virutotal.com, and submit unknown images.
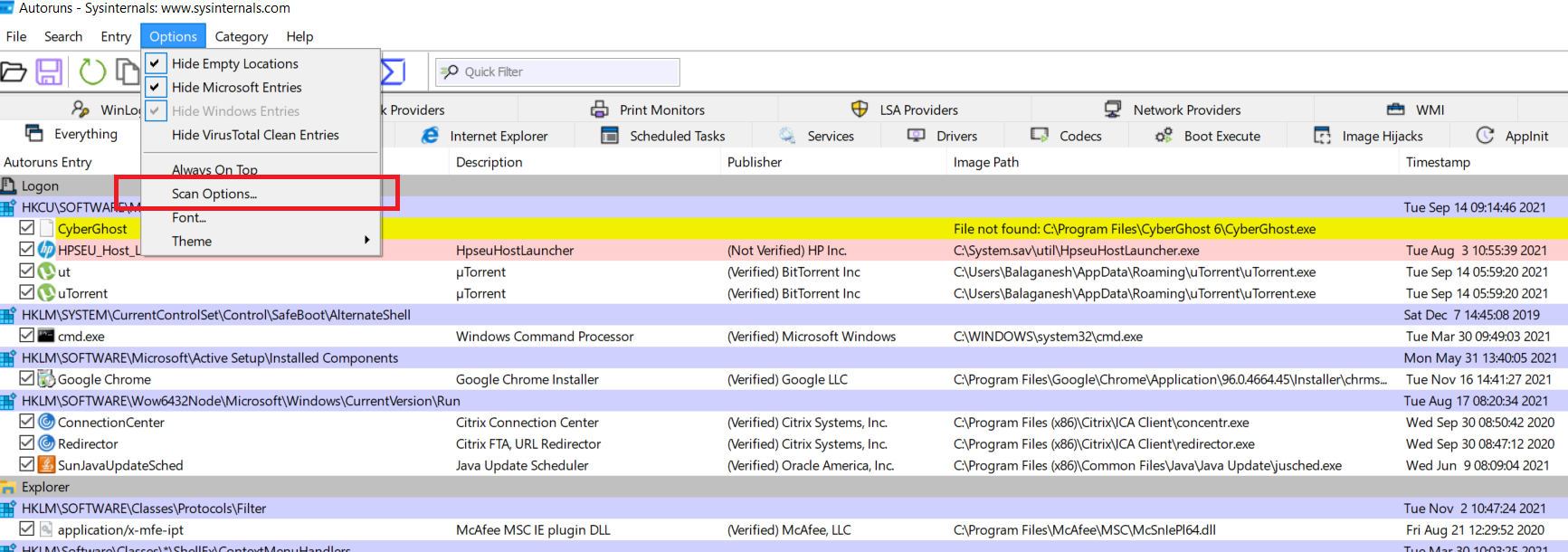
The above list of figures shows, applied filter excludes the Microsoft executables and shows only the files that belong only to other companies which are verified or not verified. Both case malware can achieve its persistence mechanism.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
As we enabled the options such as check virustotal and submit unknown images, these should find us the malicious file that is hiding and executed behind each boot time. Here we see below findings from virustotal
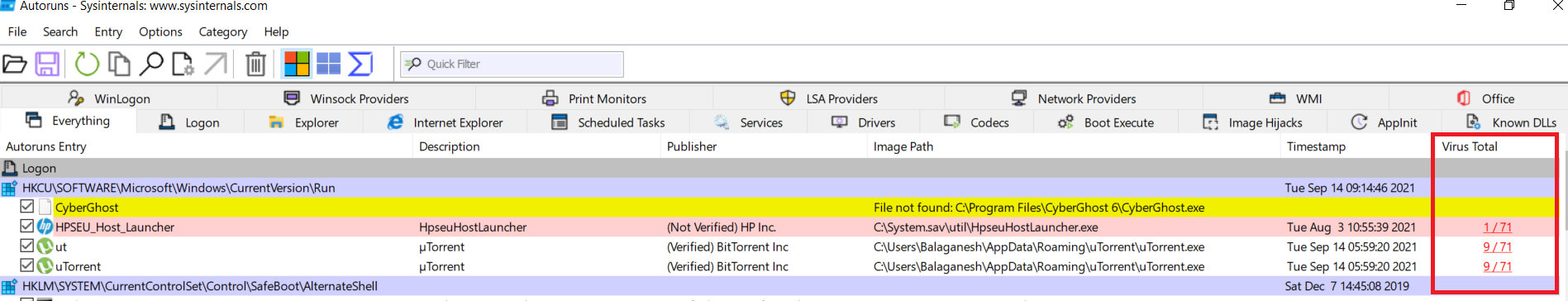
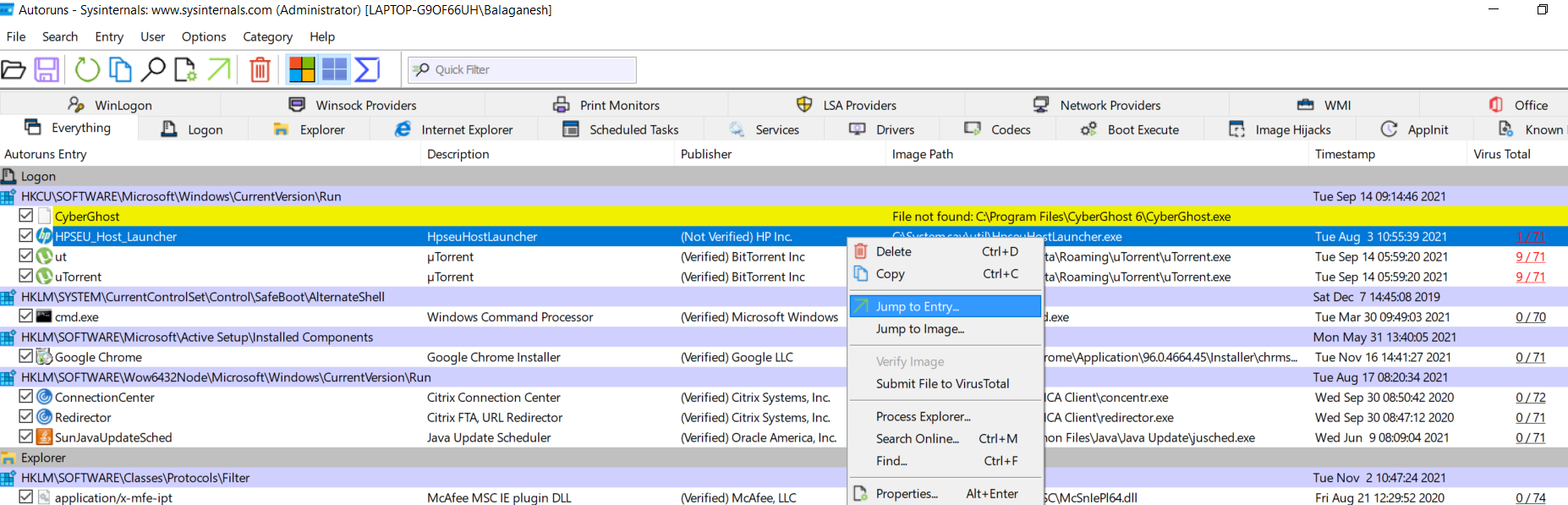
The above figure shows what we see as the Virustotal results for some executables with malware detection ratio. To check the persistence registry locations. Right-click on the image and select Jump to entry, this will take you to the registry.
Also Read: Windows Service Creation and Malware Detection Methods
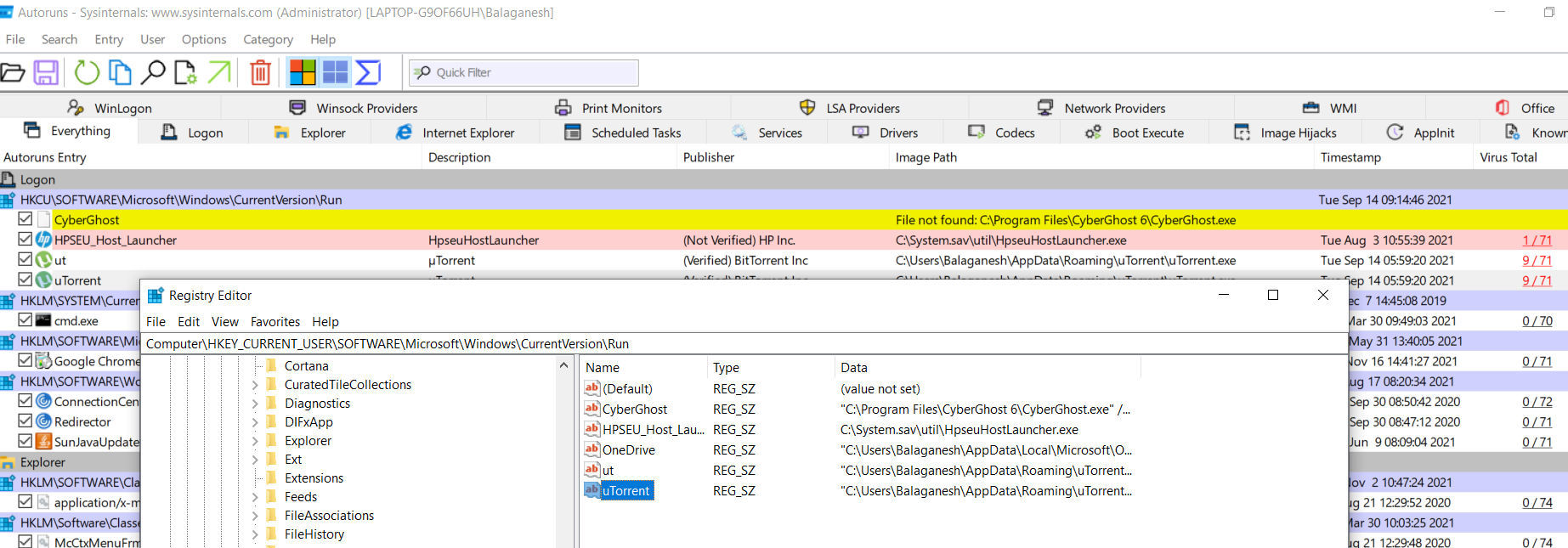
The above figure shows file Utorrent is configured to autostart and the registry location is Computer\HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run , Now you can clean this malware!
Working with autorunsc
Autorunsc is does the same job in command-line interface
Usage: autorunsc [-a <*|bdeghiklmoprsw>] [-c|-ct] [-h] [-m] [-s] [-u] [-vt] [[-z ] | [user]]]
| Parameter | Description |
|---|---|
| -a | Autostart entry selection: |
| * | All. |
| b | Boot execute. |
| d | Appinit DLLs. |
| e | Explorer addons. |
| g | Sidebar gadgets (Vista and higher) |
| h | Image hijacks. |
| i | Internet Explorer addons. |
| k | Known DLLs. |
| l | Logon startups (this is the default). |
| m | WMI entries. |
| n | Winsock protocol and network providers. |
| o | Codecs. |
| p | Printer monitor DLLs. |
| r | LSA security providers. |
| s | Autostart services and non-disabled drivers. |
| t | Scheduled tasks. |
| w | Winlogon entries. |
| -c | Print output as CSV. |
| -ct | Print output as tab-delimited values. |
| -h | Show file hashes. |
| -m | Hide Microsoft entries (signed entries if used with -v). |
| -s | Verify digital signatures. |
| -t | Show timestamps in normalized UTC (YYYYMMDD-hhmmss). |
| -u | If VirusTotal check is enabled, show files that are unknown by VirusTotal or have non-zero detection, otherwise show only unsigned files. |
| -x | Print output as XML. |
| -v[rs] | Query VirusTotal for malware based on file hash. Add ‘r’ to open reports for files with non-zero detection. Files reported as not previously scanned will be uploaded to VirusTotal if the ‘s’ option is specified. Note scan results may not be available for five or more minutes. |
| -vt | Before using VirusTotal features, you must accept the VirusTotal terms of service. If you haven’t accepted the terms and you omit this option, you will be interactively prompted. |
| -z | Specifies the offline Windows system to scan. |
| user | Specifies the name of the user account for which autorun items will be shown. Specify ‘*’ to scan all user profiles. |
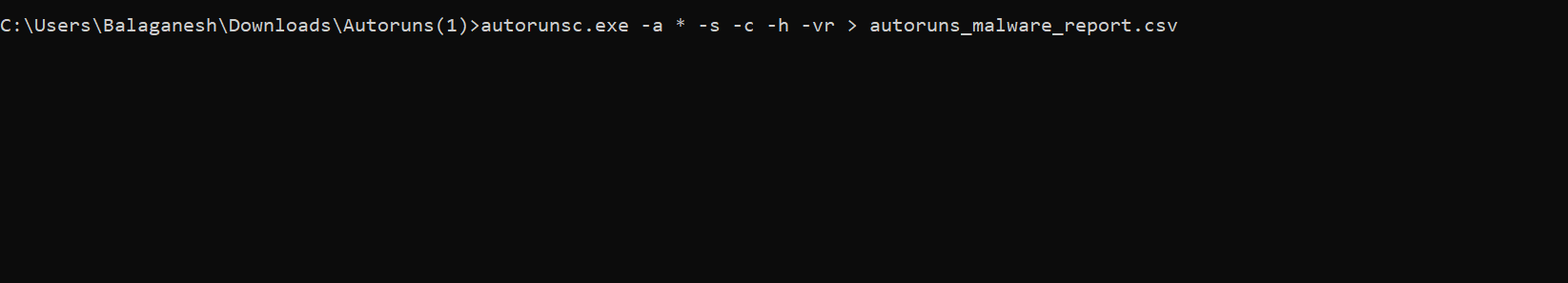
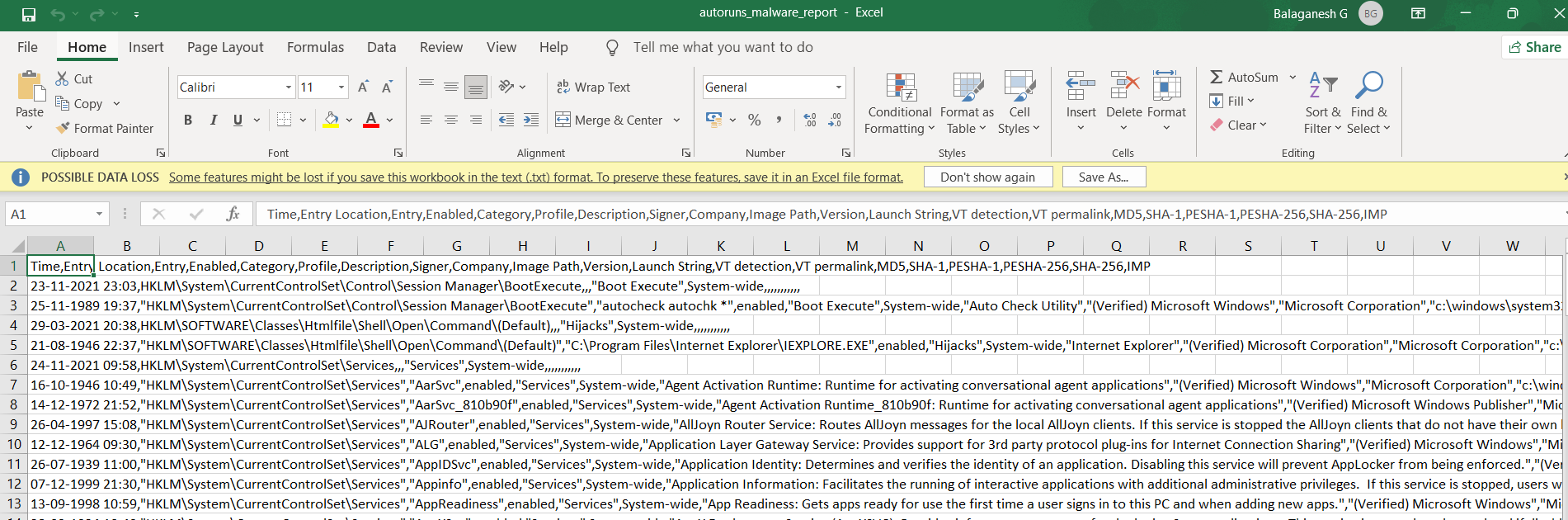
The above figure shows, hunting for all autorun files and checking the hashes in virustotal, and finally, we can export it in CSV for better visibility.
Conclusion
The tool Autoruns has been used across by various cybersecurity professionals, especially for incident response and security operations. The simple tools are more familiar for their robust usage and performance. Happy Hunting!



































