As discussed in the previous blog about Azure Sentinel for IT Security and its SIEM Architecture. In this blog, we will cover azure sentinel has its significant components. While other SIEM platforms have a wide variety of components, the sentinel is one step ahead and has in-built hunting methodologies. Let’s discuss the azure sentinel components.
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
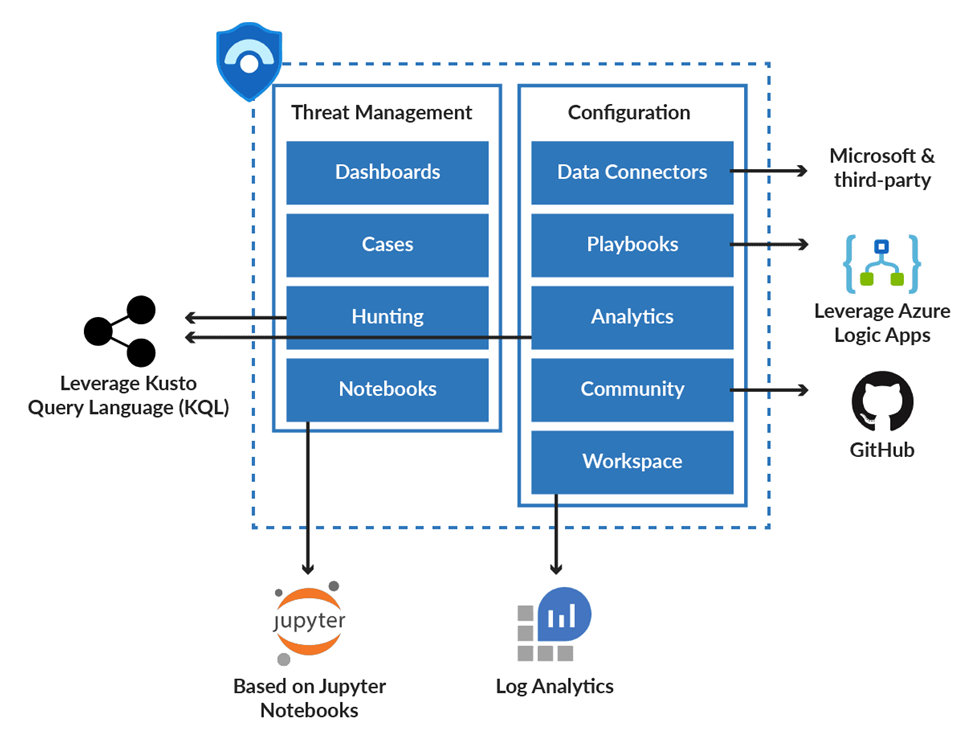
Dashboards: Azure Sentinel comes with built-in dashboards that allow you to visualize data from various sources. Allows the security team to get a better understanding of the events that those services generate.
Cases: A case is a collection of all relevant evidence related to a certain investigation. A case can contain one or more than one alerts based on the analytics defined by the user.
Hunting: For security analysts and threat analysts, hunting is a crucial component. Its job is to detect and evaluate security threats by doing proactive threat analysis across the environment. KQL (Kusto Query Language) improves Azure Sentinel’s search capabilities. Because of its machine learning capabilities, it is capable of detecting suspicious behavior. Anomalies in firewall data include abnormal traffic and traffic patterns, suspicious authentication patterns, and resource creation anomalies.
Notebooks: Azure Sentinel’s out-of-the-box integration with Jupyter Notebook, which includes an in-built collection of libraries and modules for machine learning, embedded analytics, visualization, and data analysis, provides flexibility and broadens the scope of what can be done with the collected data.
Data Connectors: Azure Sentinel includes built-in connectors for data ingestion from Microsoft products and solutions as well as partner solutions.
Also Read: Event ID 4663 -Occurrence , Log fields Explanation & Use cases
Playbooks: A Playbook is a set of procedures that Azure Sentinel can run in response to an alert trigger. They use Azure Logic Apps to accomplish this. As a result, the user can make use of Logic Apps’ flexibility, capacity, customizability, and built-in templates. To automate and orchestrate tasks/workflows that can be configured to run manually or execute automatically when specific alerts are triggered.
Analytics: Analytics allows users to use Kusto Query Language to construct custom alerts (KQL).
Community: The Azure Sentinel Community page on GitHub offers detections based on several data sources. Users can use it to create alerts and respond to threats in their environment. Sample hunting queries, security playbooks, and other artifacts are also available on the community website.
Log Analytics Workspace: Workspace or Log Analytics Workspace is a container that consists of data and configuration information. This container is used by Azure Sentinel to store data collected from various data sources. For data storage, you can either establish a new workspace or use an existing workspace. However, having a dedicated workplace would be helpful because alert rules and investigations do not work across workspaces. The following functionalities are available in a Log Analytics workspace:
- A geographic location for data storage.
- Data isolation by granting different users access rights following Log Analytics’ recommended design strategies for workspaces.
- A scope for configuration settings, such as pricing tier, retention, and data capping.
Also Read: Windows Management Instrumentation Attacks – Detection & Response
Azure Sentinel Roles:
The Role-Based Access Control (RBAC) authorization model in Azure Sentinel allows administrators to set up granular permissions based on various criteria and permissions. To deploy Azure Sentinel, one needs contributor permissions to the subscription in which the Azure Sentinel workspace resides. Use the RBAC approach to provide granular permissions to various groups to provide access to different teams based on their work using Azure Sentinel. There are three built-in roles in Azure Sentinel:
- Reader: Users with this role can view incidents and data, but cannot make changes.
- Responder: Users with this role can view incidents and data, as well as perform some actions on adventures, such as assign to another user or change the incident’s severity.
- Contributor: Users assigned to this role have access to incidents and data, as well as the ability to create and delete analytic rules.
Now that you know Azure Sentinel’s primary roles, it’s time to familiarize yourself with the specific tasks it can perform. These include:
- Gather data across all applications, devices, infrastructure, users in multiple clouds and on-premises.
- Spot undetected threats and reduce false positives using analytics and threat intelligence.
- Conduct investigations on threats using artificial intelligence to efficiently spot suspicious activities on a large scale.
- Respond to security-related incidents with automation of common tasks and built-in orchestration.
Understanding these tasks can help you better understand the importance of Azure Sentinel in your overall cloud security operations. However, it’s essential to know that going to the cloud doesn’t mean your enterprise is free from any security problems. Cloud systems are also targets of cyberattacks. As your company grows, many cybercriminals will see it as a great opportunity to hack cloud systems and steal information from users.
Therefore, in addition to investing in Azure Sentinel, you may want to check out other credible websites and resources like Leet Privacy and other similar platforms. They can provide expert advice and guides pertaining to cybersecurity education and other related topics.
Conclusion
If you’re running an enterprise, having a holistic cloud security system is essential in protecting your resources from cyberattacks. Fortunately, with the advent of modern solutions like Azure Sentinel, businesses can implement security protocols within premises and across multiple clouds. Therefore, if you’re considering investing in Azure Sentinel, keep the information mentioned above in mind to learn more about this security management solution and how you can use it for your enterprise.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
Let’s continue more details about Azure Sentinel in the next blog.



































