Bumblebee is a kind of Trojan-loader malware and it’s distributed via spam emails. As it’s a new threat actor, this group uses the other payload downloaders like Bazar-Loader and IcedID for their infection. Also, this malware is delivered by an ISO file that’s spread via .eml attachment files which are in achieved file format to deliver their payload files such as [ .LNK (or) .EXE (or) .DLL ].
Bumblebee Infection Chain:
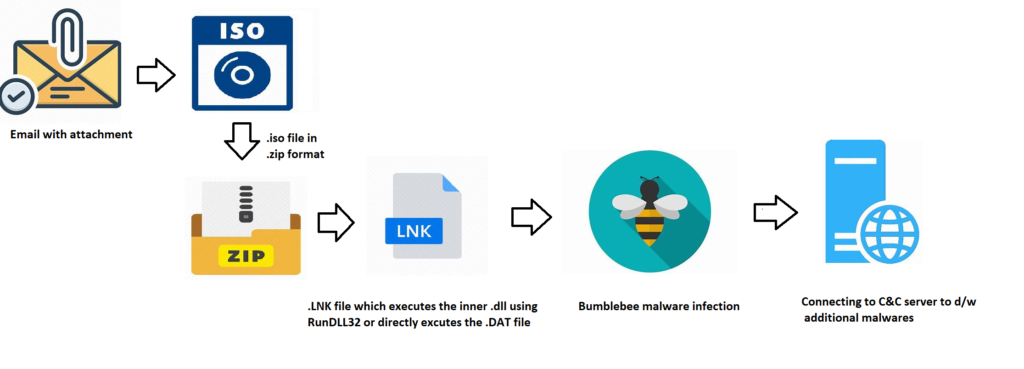
Bumblebee is a small malicious program whose goal is to download and execute additional payloads on compromised machines without detection. To achieve this, they use various techniques to inject or attach these payloads to existing legitimate processes. They also collect system information about the compromised computer that can later be used to uniquely identify the victim machine in the attackers’ command-and-control panel.
Also Read: Malspam with new Matanbuchus Loader – Detection & Response
Why are ISO files being used?
ISO files are used to store file system copies of optical discs as a disc image but are essentially in an archive file format.
Also, malware authors know that many email gateway scanners don’t scan ISO file attachments properly. This is due to the fact that ISOs tend to be hundreds of megabytes in size, making them larger efficiently and effective for scanning. However, ISOs can also be very small and may contain nothing more than a half-megabyte malware binary.
Also Read: Lyceum APT group new .NET-based DNS backdoor – Detection & Response
Nowadays ISO files are very easy to open. This increases the chances of the target opening the file and infecting their victim machines.
Technical Analysis:
Bumblebee’s code contains a single function that handles the initialization, deployment, response handling and sending requests.
Once the malware is launched on a compromised device, it gathers the victim’s information, then communicates to the C2 server. Basically, this malware is used to fetch and run additional malicious payloads, such as Cobalt Strike, Sliver, Meterpreter, etc.,
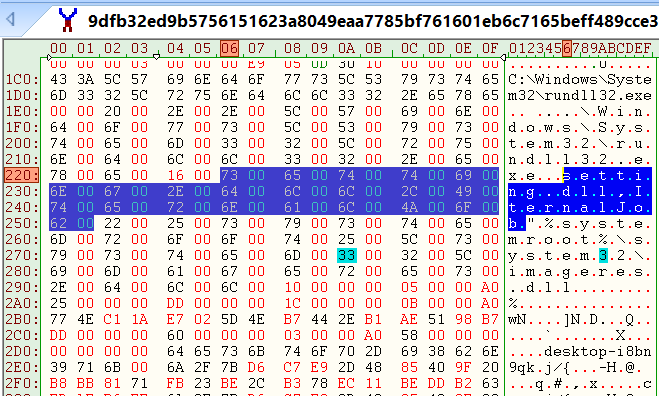
Targeted command line:
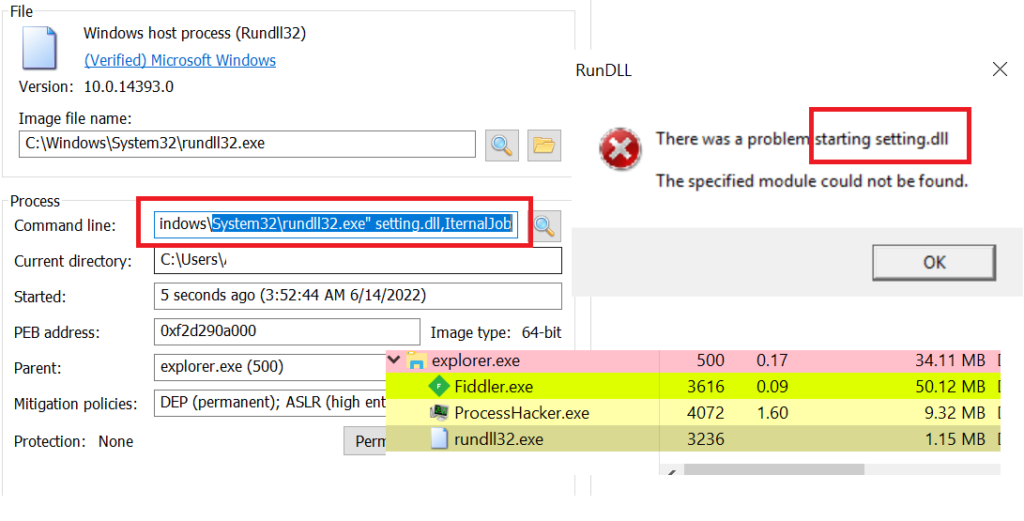
We can be able to see the payload name once the infection starts. Every malware used to identify the virtual environment, likewise, Bumblebee performs the following actions:
- Queries registry keys related to Virtual Machine-related software.
- Executes WMI queries to identify them.
- Identifies emulator by reading the respective registry keys.
- Identify the window name of the running process.
Indicator of Compromise:
File Hashes:
90576eb6754dd1c38fb4cea4bf3f029535900436a02caee891c057c01ca84941
78c5d780b2ca553cbd3fb0140813e0e1fb7c48491090df605f03c309d0086baf
7db1126c80901edbc3be6948f208d4c450a23ea453ecf2e684bb4c8363c60db0
598b792b8231a4d897d71d95437043730fbb423f2863b8261d29a1e5712c9919
422c03f96a7 2fdd657c2ebca1387bd1f6be6e0b1b30a352827c48ef6fc16995e
9dfb32ed9b5756151623a8049eaa7785bf761601eb6c7165beff489cce31bb08
Detection & Response:
Qradar:
SELECT UTF8(payload) from events where LOGSOURCETYPENAME(devicetype)='Microsoft Windows Security Event Log' and ("Image" ilike '%\rundll32.exe') and ("Process CommandLine" ilike '%setting.dll%' or "Process CommandLine" ilike '%InternalJob%' or "Process CommandLine" ilike '%.dat%' or "Process CommandLine" ilike '%ProcessLoad%' or "Process CommandLine" ilike '%toso3l.dll%' or "Process CommandLine" ilike '%#1%' or "Process CommandLine" ilike '%m3n4rat.dll%')Qradar:((Image="*\\rundll32.exe") AND (CommandLine="*setting.dll*" OR CommandLine="*InternalJob*" OR CommandLine="*.dat*" OR CommandLine="*ProcessLoad*" OR CommandLine="*toso3l.dll*" OR CommandLine="*#1*" OR CommandLine="*m3n4rat.dll*")) AND source="WinEventLog:*"Arcsight:(((destinationProcessName CONTAINS "*\\rundll32.exe" OR sourceProcessName CONTAINS "*\\rundll32.exe" OR deviceProcessName CONTAINS "*\\rundll32.exe")) AND ((destinationServiceName CONTAINS "*setting.dll*" OR destinationServiceName CONTAINS "*InternalJob*" OR destinationServiceName CONTAINS "*.dat*" OR destinationServiceName CONTAINS "*ProcessLoad*" OR destinationServiceName CONTAINS "*toso3l.dll*" OR destinationServiceName CONTAINS "*#1*" OR destinationServiceName CONTAINS "*m3n4rat.dll*" OR deviceCustomString1 CONTAINS "*setting.dll*" OR deviceCustomString1 CONTAINS "*InternalJob*" OR deviceCustomString1 CONTAINS "*.dat*" OR deviceCustomString1 CONTAINS "*ProcessLoad*" OR deviceCustomString1 CONTAINS "*toso3l.dll*" OR deviceCustomString1 CONTAINS "*#1*" OR deviceCustomString1 CONTAINS "*m3n4rat.dll*")))Elastic Query:(process.executable:*\\rundll32.exe AND process.command_line:(*setting.dll* OR *InternalJob* OR *.dat* OR *ProcessLoad* OR *toso3l.dll* OR *#1* OR *m3n4rat.dll*))Fireeye:(metaclass:`windows` process:`*\rundll32.exe` args:[`setting.dll`,`InternalJob`,`.dat`,`ProcessLoad`,`toso3l.dll`,`#1`,`m3n4rat.dll`])GrayLog:(Image.keyword:*\\rundll32.exe AND CommandLine.keyword:(*setting.dll* *InternalJob* *.dat* *ProcessLoad* *toso3l.dll* *#1* *m3n4rat.dll*))Logpoint:(Image IN "*\\rundll32.exe" CommandLine IN ["*setting.dll*", "*InternalJob*", "*.dat*", "*ProcessLoad*", "*toso3l.dll*", "*#1*", "*m3n4rat.dll*"])Microsoft Defender:DeviceProcessEvents | where ((FolderPath endswith @"\rundll32.exe") and (ProcessCommandLine contains "setting.dll" or ProcessCommandLine contains "InternalJob" or ProcessCommandLine contains ".dat" or ProcessCommandLine contains "ProcessLoad" or ProcessCommandLine contains "toso3l.dll" or ProcessCommandLine contains "#1" or ProcessCommandLine contains "m3n4rat.dll"))Microsoft Sentinel:SecurityEvent | where EventID == 4688 | where ((NewProcessName endswith @'\rundll32.exe') and (CommandLine contains 'setting.dll' or CommandLine contains 'InternalJob' or CommandLine contains '.dat' or CommandLine contains 'ProcessLoad' or CommandLine contains 'toso3l.dll' or CommandLine contains '#1' or CommandLine contains 'm3n4rat.dll'))RSA Netwitness:((Image contains '\rundll32\.exe') && (CommandLine contains 'setting\.dll', 'InternalJob', '.dat', 'ProcessLoad', 'toso3l\.dll', '#1', 'm3n4rat\.dll'))SumoLogic:(_sourceCategory=*windows* AND (Image = "*\rundll32.exe") AND (CommandLine = "*setting.dll*" OR CommandLine = "*InternalJob*" OR CommandLine = "*.dat*" OR CommandLine = "*ProcessLoad*" OR CommandLine = "*toso3l.dll*" OR CommandLine = "*#1*" OR CommandLine = "*m3n4rat.dll*"))



































