CyberChef is a simple, intuitive web app for carrying out all manner of “cyber” operations within a web browser. These operations include simple encoding like XOR or Base64, more complex encryption like AES, DES, and Blowfish, creating binary and hex dumps, compression, and decompression of data, calculating hashes and checksums, IPv6 and X.509 parsing, changing character encodings, and much more.
Tool Download:
You can download this tool here. or Access the online version here.
Use case: Company A got a phishing email with a malicious HTML file and you are given the job to analyze and hunt for malicious actions & extract IOCs.
Also Read : Cooking Malicious Documents with Cyberchef – Detect & Respond
Malware Analysis on Morse Code :
Morse Code: Morse code is a method used in telecommunication to encode text characters as standardized sequences of two different signal durations, called dots and dashes, or dits and dahs. It is widely used in Radiotelegraphy and aviation. Morse code is transmitted on its radio frequency to the aircraft pilots to decode the message from the ground station.
Pilots do not actually have to know Morse to identify the transmitter because the dot/dash sequence is written out next to the transmitter’s symbol on aeronautical charts. Some modern navigation receivers automatically translate the code into displayed letters.

How attackers are using morse to bypass proxy and email filters?
Hackers convert their malicious domains in the International Morse Code and embedded into email attachments. Since security controls will be checking only the domains in the blacklist list, Using these techniques attackers have opportunities to successfully execute the phishing attack.
Also Read : Cooking Malicious Documents with Cyberchef – Detect & Respond
Analyzing the Morse phishing Email:
- Below we can an email attached with a HTML file , while opening the file most of the codes are onfucated and not in the readable format.
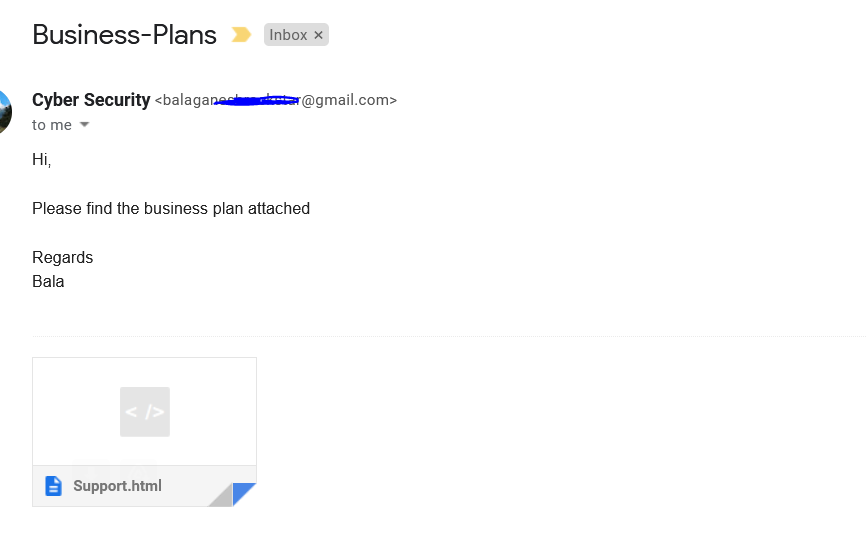
- Above figure shows , User has received some emails with suspicious HTML attachements are detected. Now let us open the attachment with notepad to see the HTML codes.
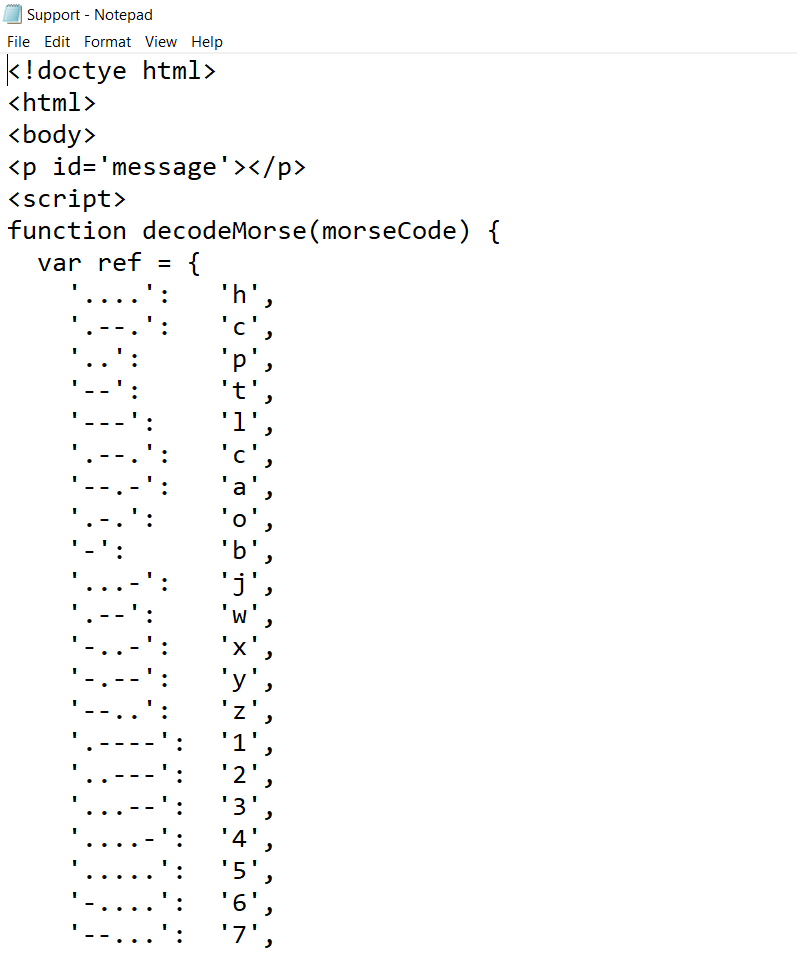
- Above figure shows , Morse codes functions and variables are mapped towards some of the letters and numbers , scrolling down a bit gives more information.

- Above figure shows , variable is getting decoded with above morse codes and printed on the console. Once this is executed , Morse codes will be decoded with actual letters and numbers ( Domain names of Hackers ) and retrive the phishing page to the end user.
Also Read : Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
Cyberchef in Action :
- Now lets copy below the morse code and analyse it with cyberchef.
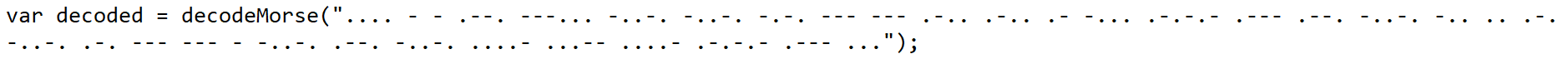
- Now we will use the Entropy Recipe to check for any randomness in the data which is compressed/Encrypted.
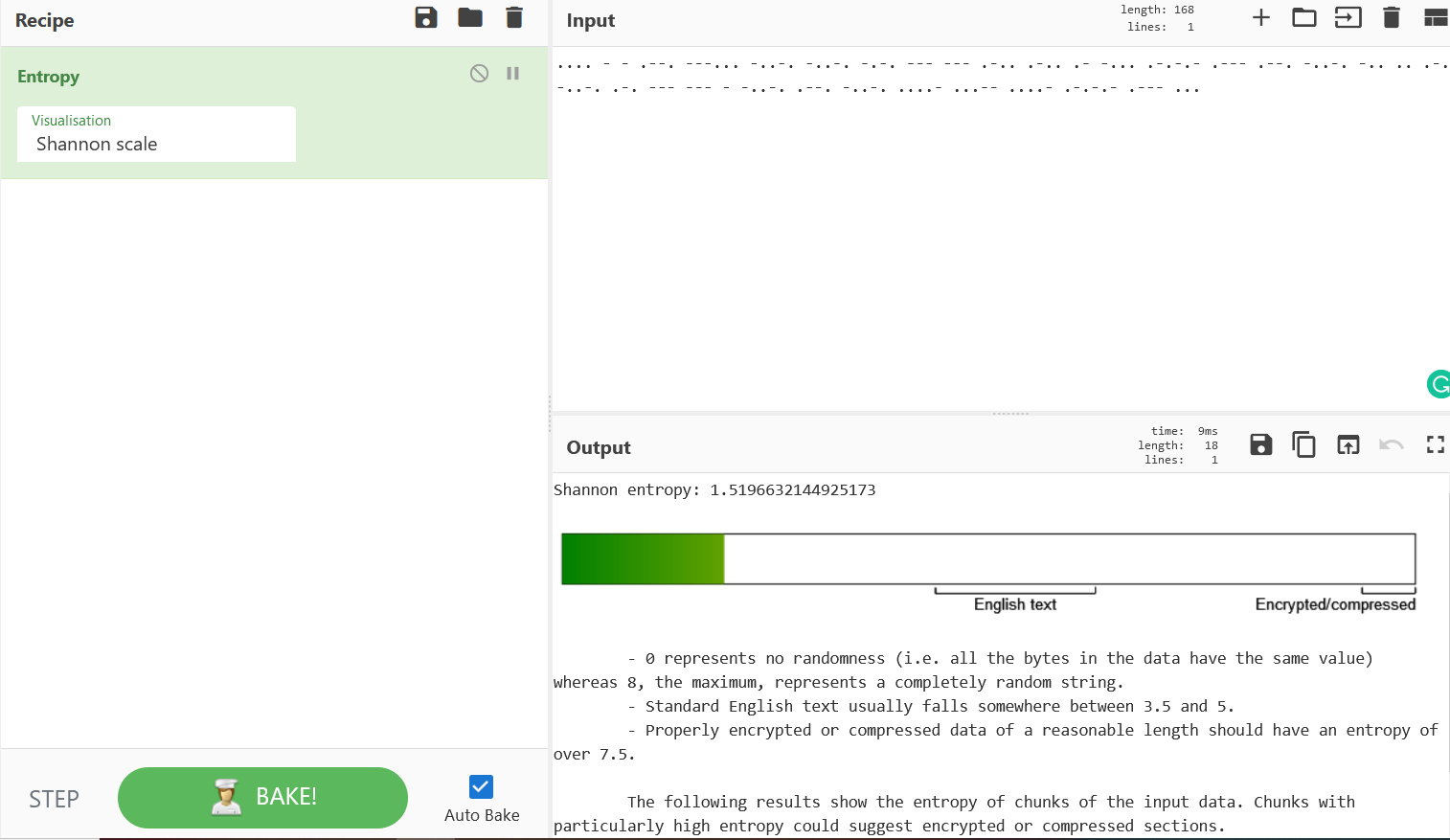
- Above figure shows the score as 1.5196632144925173 , Only value “0” states that no randomness in data value. Greater than zero is considered as randomness in data value with compression and encryption in place.
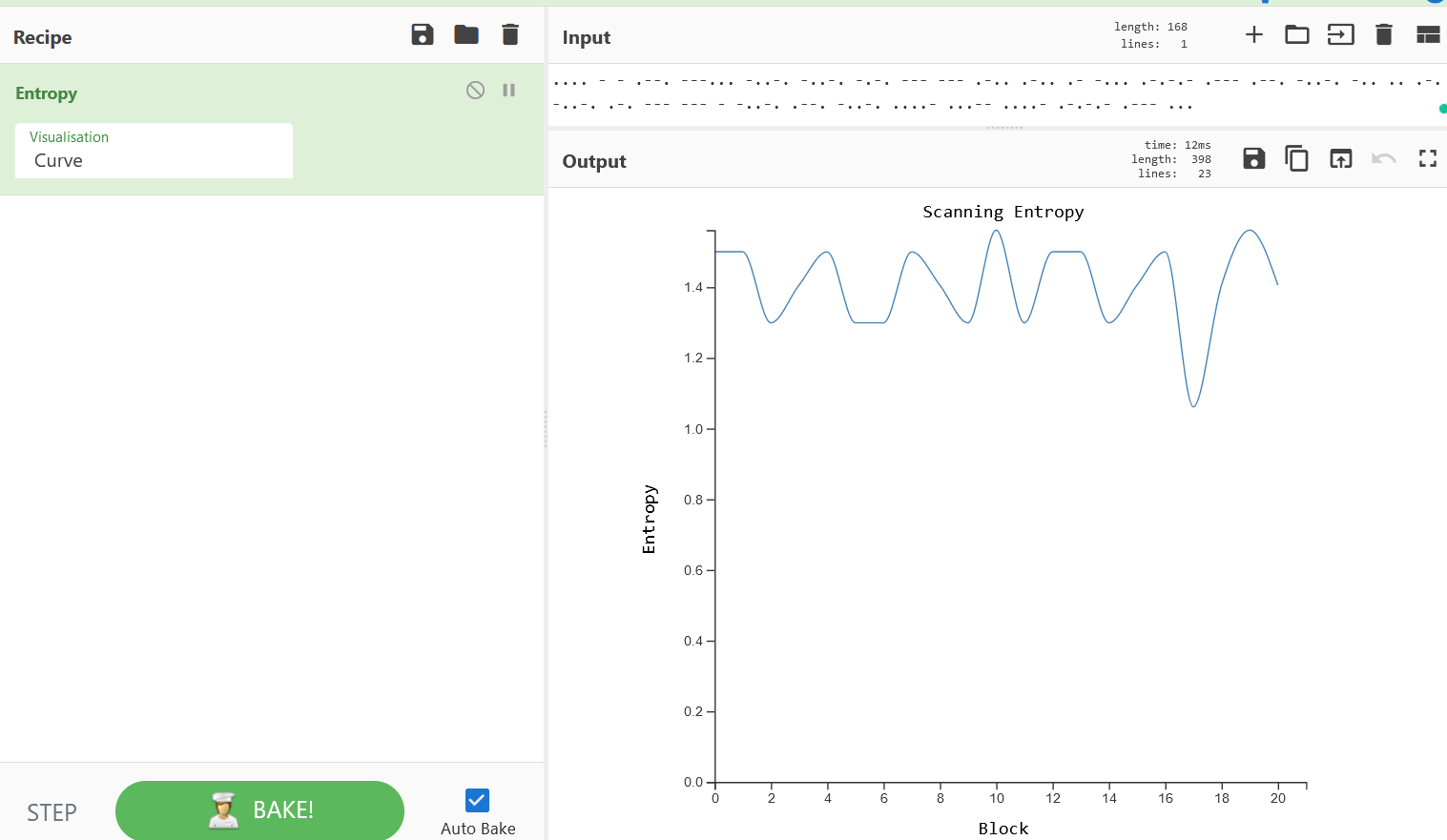
- Above scale shows more infromation about the data values in curve representation. Now we will use the From Morse recipe to decode this codes.
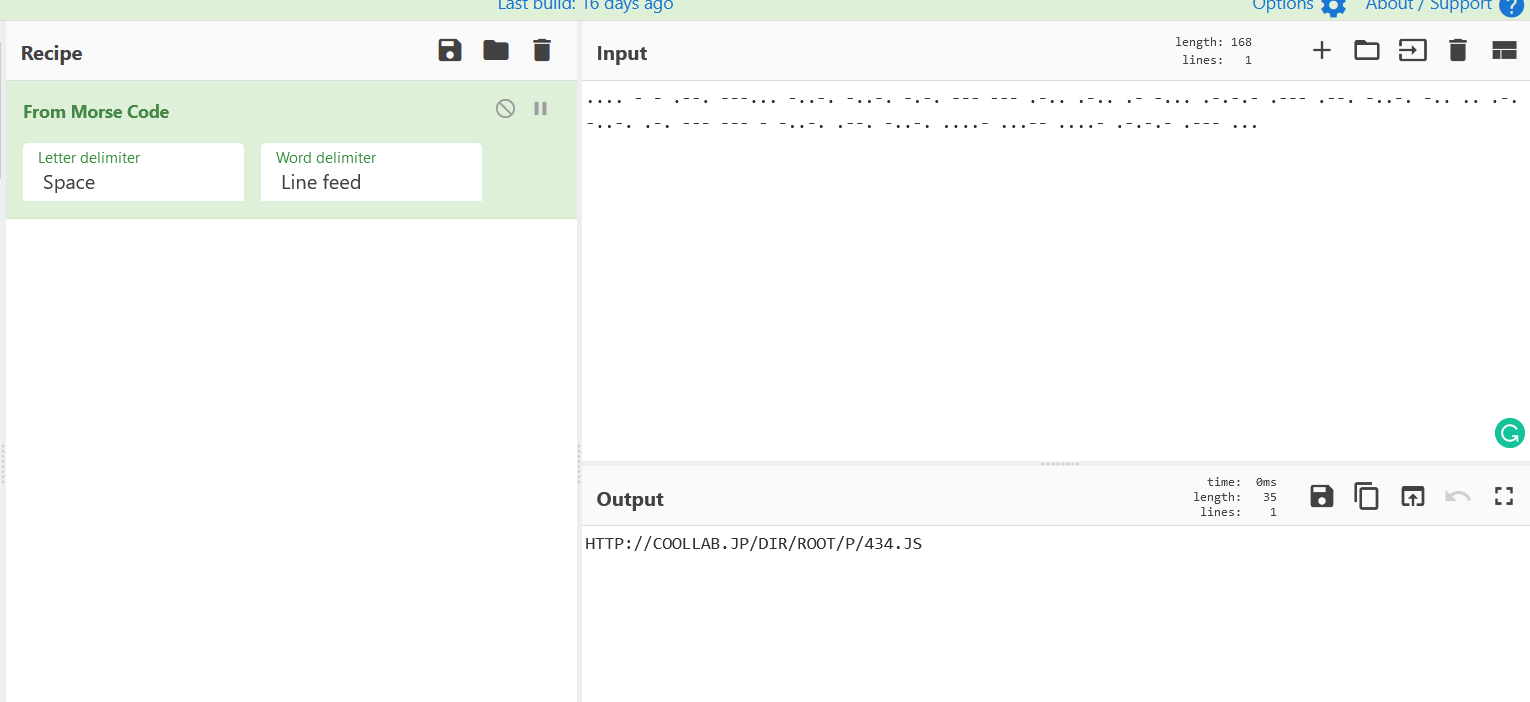
- Above figure shows , CyberChef has sucessfully decoded the morse and the following domain http[:]//coollab[.]jp/dir/root/p/434.js and the javscript 434.js which will gives end user the phishing page to steal passwords.
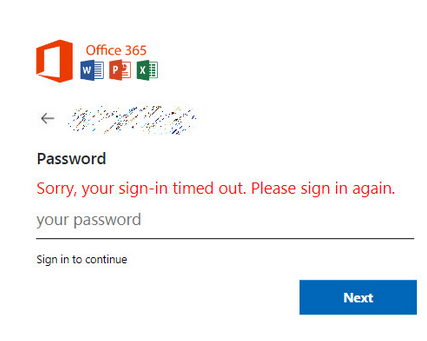
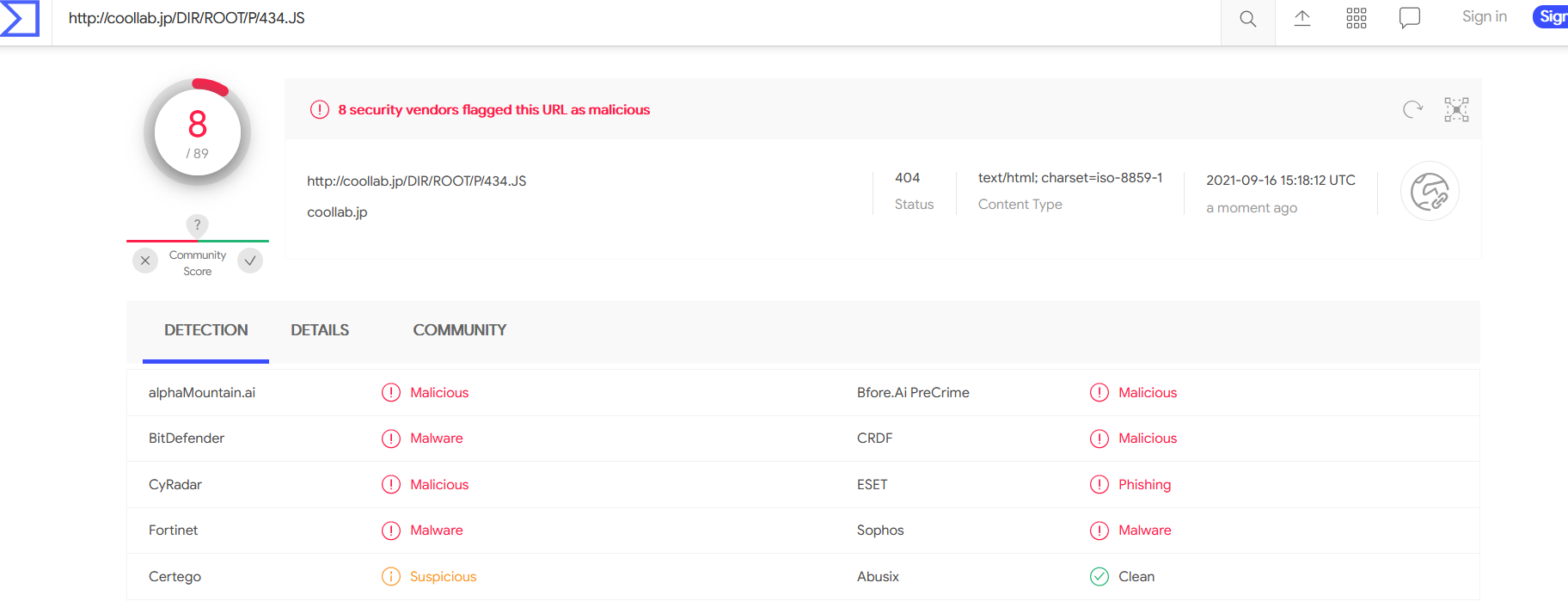
- Checking the same on VirusTotal. We have understood that this malicious morse codes are used for active phishing attempts.



































