Cyber threat hunting is a proactive approach in the defense phase. Threat hunters are experienced cyber defense professional, who actively searches malicious signs of traffic on network and endpoints with machine-based techniques to identify security incidents. This expert has a good skill set in understanding analytics in-depth with AIML algorithms, Adversary TTP (Tactics, Techniques, and Procedures) to find out security gaps on existing detection tools.
Threat Hunting Characteristics
Threat hunters do not pitch in when an alert is fired from existing logging tools or Checking with the IOCs does not mean that they are threat hunters. Below are the threat hunters Characteristics
Being Proactive – Threat hunting is the proactive procedure and it’s not reactive. Reactive alerts are handled by security operation center analysts with the roles of Tier1 & Tier2. So basically threat hunters proactively sniffing out potential intruders before any alerts are generated.
Hypothesis Driven Investigations – Scientific method (Mathematics Algorithms) requires finding the active threat actors’ behaviors from existing TTP. This helps threat hunters to understand the various event time gaps analysis, low-profile asynchronous communication (Data Transfer attempts from well-known protocols, I.E HTTP, HTTPS, DNS, etc. and Predict the security loopholes. Often time investigation will start with limited shreds of evidence only.
Follow Footprints – The threat hunting procedure is also to find the clues that left beside the beach and check for further clues for any well-known malicious packages that are installed in the environment or any specific connection is getting established as malware beaconing activity.
Cyber Forensics – Geek in computer forensics to understand most insightful information’s on assets behaviors.
Baselining – Baselining helps threat hunters to understand what is normal and abnormal within the organization. SANS Suggest hunters consider the below questions.
- How Prevalent and use of Power-Shell in the environment?
- If prevalent, what does normal system administrator activity look like?
- Where does PowerShell activity typically come from, and what user accounts typically run it?
As a result, a hunter may not need to baseline all of PowerShell, but rather look for unexpected outliers or attacker-specific command structures.
Leverage OSINT- Use of open will provide more useful thoughts to threat hunters. According to SANS lists the following benefits hunters can gather from third-party sources:
- Ruling out false-positive leads
- Focus on interesting leads
- IP lookups
- Geolocation
- Encrypted traffic metadata
- Log detection
- Attacker technique overlays
- Link analysis of internal vs. external or host vs. network data points
Threat Hunting Steps:
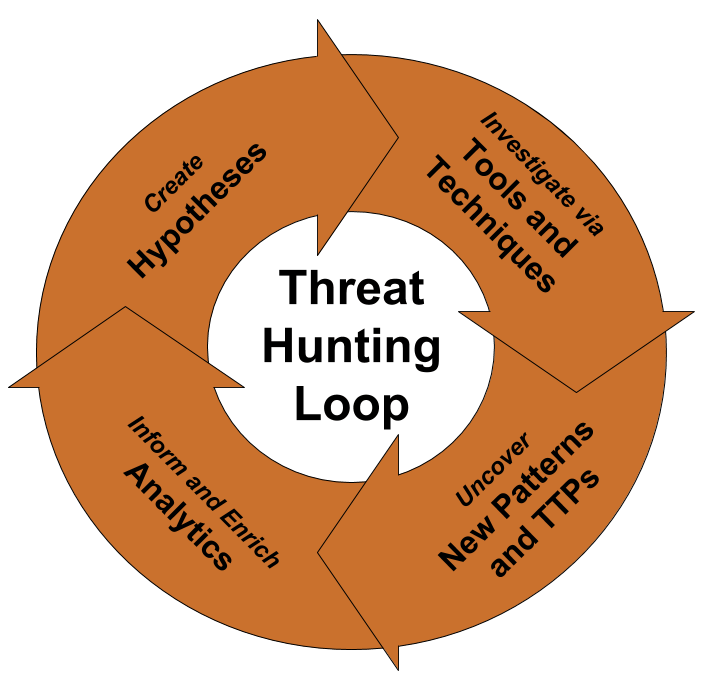
Create Hypothesis
Ask question on yourself, what threats might be in the environment and how to find them. A hypothesis can include a suspected attacker’s tactics, techniques, and procedures (TTPs). Logical thinking and out of box ideas will bring a new detection.
Tools and Techniques
Build an advanced logical query on Security Information and Event Management (SIEM) software to provide insights on threat actor’s behaviors in the environment.
New pattern and TTPs
Uncover new patterns and TTP from the existing one. Compare the changes from existing similar TTP.
Inform and enrich Analytics
Observed malicious activity can be the active indicator of attack, enrich such information’s into SIEM as rules, Tweak EDR ( Endpoint Detection and response) signatures, Update firewall /IPS rules, deploy security patches, Baseline secure configurations, and hardening.
Happy Hunting !!!



































