Directory is a familiar word we use or we know which will contain some files in it. Files are kept held together in a Folder. Directory is the term we use more in Linux and folders in windows.
Let’s start with a sample structure of web application.
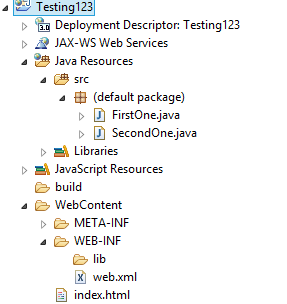
We can see a sample of how files are organized during development phase in an IDE. Once development completed, same structure needs to be deployed in the web server for the code to work properly. Here the above pic we can see java files are under Java resources. Html content is under WebContent. It goes as the number of files in increase. We got some detail about directory and structures before knowing about threat which directory listing brings to an application.
Protecting the sensitive information is must for all the application. Leaking sensitive information will result in huge impact to the business.
Directory listing will also can lead to leak sensitive information. Directory listing is an option available to web servers ( IIS, Apache tomcat etc) to expose the files in web browser. This indexing or listing directly can’t be tagged as vulnerable until a sensitive file is exposed without any control to the unknown user.
Let’s look a sample directory listing for an application to know how it leads way in leaking sensitive information.
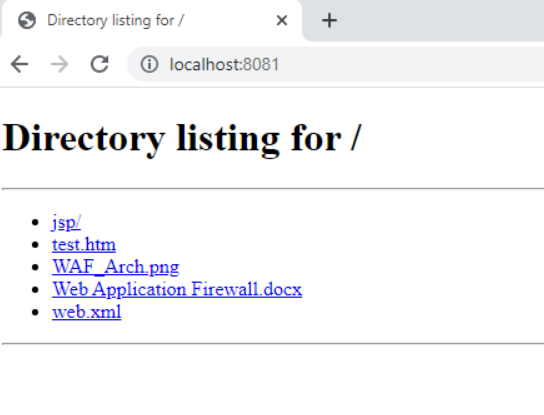
We can see that this application is something developed based on WAF to the security team. Web Application Firewall plays a major role in filtering malicious requests to a web application. So, something that important left unprotected in wild will seriously give attackers to march their way into application breaking the WAF rules. Also, we can see web.xml file ,jsp/ directory is left unprotected which gives away configuration details about the application to attacker. Thus, with little information we can gather lots of information to take advantage over that application. Let us consider same directory indexing for a large enterprise application, attacker will be swimming in the information pool. So, it’s very important for the developer as well as the site administrator to protect the necessary information in their application. Good practice involves in disabling directory listing for the web application unless it is business requirement to keep it enabled. What if there is a option to upload files in the web application or through put(if enabled) command file can be uploaded, attacker can upload the shell file and use the directory listing to execute their shell to control the server.
Additional References: CWE-538, CWE-548, CAPEC-127. To find the CVE associated along with CWE-538 (https://www.cvedetails.com/vulnerability-list/cweid-538/vulnerabilities.html) and CWE-548 (https://www.cvedetails.com/vulnerability-list/cweid-548/vulnerabilities.html)
Directory listing can be enabled or disabled, partially enabled in the web server configuration file.
Detections :
- Attacker tries to access the diferrent parts of URI path , Were http status codes will be 200 ( successful retrivel of the page/file ) or 302 ( Redirection and page landed )
- External IP will do unnessary bruteforce with list of default file directorty names. HTTP status codes 404 ( file or page not found ) ,200 or 302 can be observed at the moment of enumeration of the attacker.
- Check the past vulnerability scanners results and judge wheather the targeted application is vulnerable to directory listing loopholes.
Preventions:
- Create blank index.html and place in each directory. This will prevent directory listing and display blank page in web browser. (Not a recommended method)
- Disable directory listing for entire application.
- In business needs, create a directory and enable directory listing only for that alone. All web servers have these options to configure.
Now, we might have some overview about directory listing and what might go wrong with weak configurations in web applications.



































