Promon is a tool developed by Microsoft. This is one of the effective tools to provides a windows operating system real-time file system, Registry, and process/thread activity on go. Expertise in malware analysis involves lots of skills like getting yourself familiar with the operating systems, Assembly languages, and programming languages like C & Reverse engineering.
Static Malware Analysis – Involves examining any given malware sample without actually running or executing the code.
Dynamic Malware Analysis – Involves running the malware in an isolated environment and observing its behavior on the system to determine whether it is malware or not.
Security Monitoring & Event Drilldown Capabilities:
- Capturing Process details, image path, Command line, user, and session ID.
- Display and filter out events using matching conditions. I.E begins with, if, is, is not, etc.
- Relationship with processes is provided in the process tree view.
- Boot time logging of all operations.
- Obfuscated or Malicious commands passed in CLI are seen.
Isolated VM Environment:
- To run the malware, use a sandboxed environment with a network that is detached.
- This is real malware when you try the same to your sample. Take precautions steps like (Network detachment, Hard disk partition allocation for VM, and Snapshot’s) to prevent yourself and others from getting infected.
Malware File Details:
File Name: 518_2.exe
Format: Windows Executable 32 bit
Procedure & Observations:
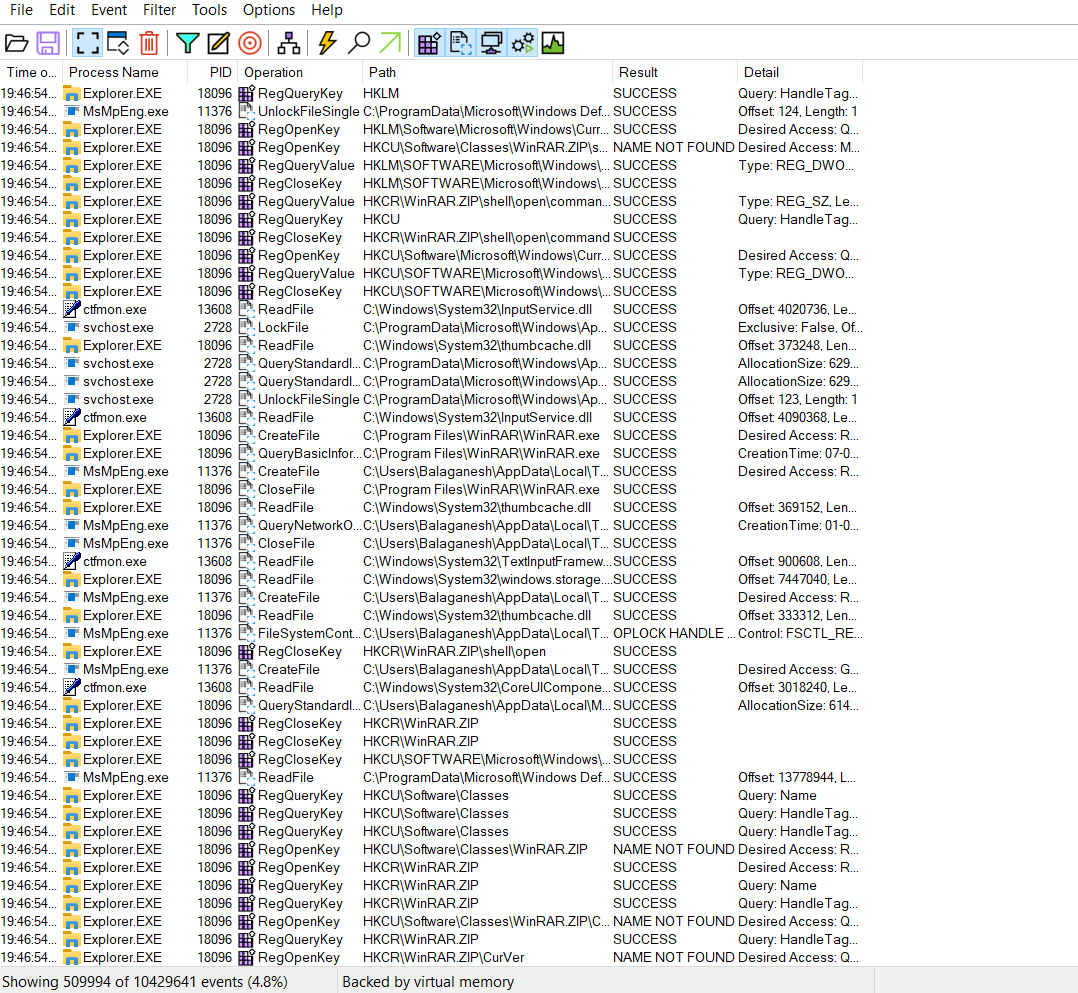
- Double Click and run the procmon. When procmon is prompted, you will see lots of events flowing back and forth. In our case, we have around 10429641 events.
- Let us give the malware the full freedom with admin rights to execute and make changes on the sandboxed machine.
Run as administrator > 518_2.exe
- Before analyzing, Give sometime to malware to actionize and its malicious intentions should be playing around.
- Once you think that we need to check and filter out procmon results with the malware. Filter out the filename with the filter.
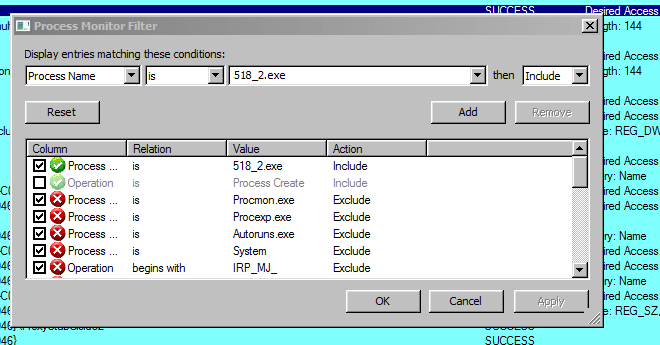
- Apart from filtering out only the process names, procmon has lots of other options to include and add to the search. Options under operations such as Parent PID , PID , Relative Time , Command line , TCP connections etc will help incident responders to hunt IOC’s.
- Procmon provides a separate button for registry activity. Most of the malware will query registry and modify it for persistence.

- Post registry changes malware connects with TCP reconnect with the suspicious external IP 104[.]149.88.198 with port 8080.
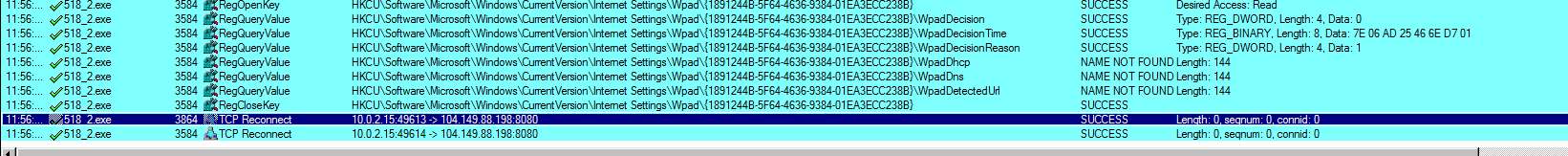
- Malware intervals can be asynchronous. Extra Time was given to sample stay on infected machine and there are no observations for malware beaconing activity.
- Therefore, we have the collected from the malicious sample and the indicator of compromise is 104[.]149.88.198.
The infected machine was bought into a clean state with the help of VM snapshot. Also running netstat -ano on an infected machine prove that there is no connection with external malware IP with respect to the malicious process name.
CMD.exe > netstat -ano
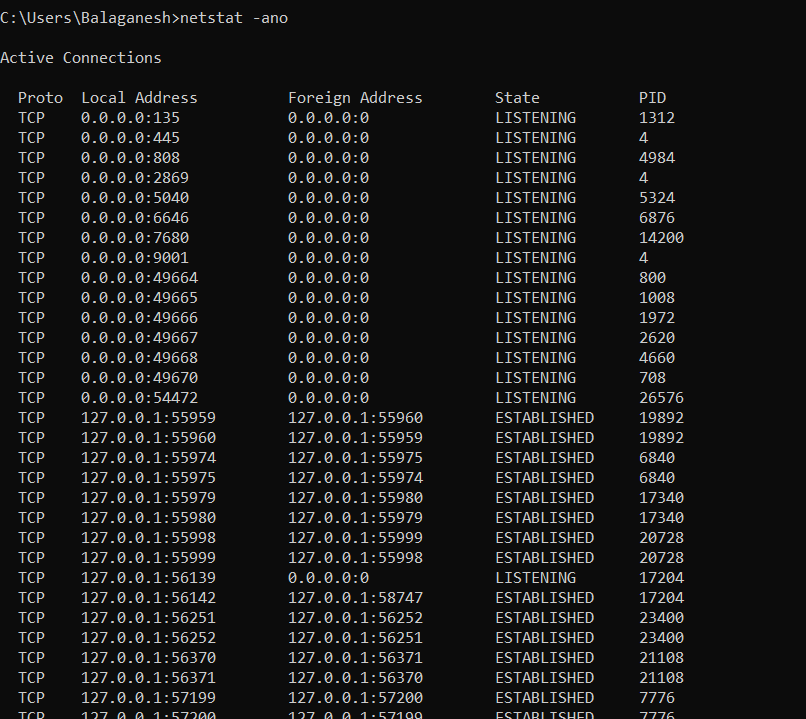
-a Display all connections and listening ports
-n Display addresses and port numbers in numerical form
-o Display the owning process ID associated with each connection.
Wrap Up
Promon is a handy tool for incident responders, Soc analysts, and Malware analysts to do dynamic malware analysis. Although you’ve quickly stepped into procmon with simple analysis and IOC extraction, there are always more options to uncover with this handy utility.



































