Mandiant Threat researchers have compiled a report on FIN7 activities from late 2021 to mid-2022, adversary continues to be very active, evolving, and trying new monetization methods. FIN7 continued to leverage PowerShell throughout their intrusions, including in a new backdoor called POWERPLANT, which FIN7 has continually developed over the last two years. Another new development is the evolution of the Birdwatch downloader, which has two variants now, named Crowview and Fowlgaze.
Evolution of Toolset Over Time
The PowerShell backdoor known as PowerPlant, which has been associated with FIN7 for years now, is still being developed into new variants, as Mandiant has identified version numbers ranging from 0.012 to 0.028.
In some intrusions, FIN7 was observed tweaking the functionality and adding new features to PowerPlant, and deploying the new version in the middle of the operation.
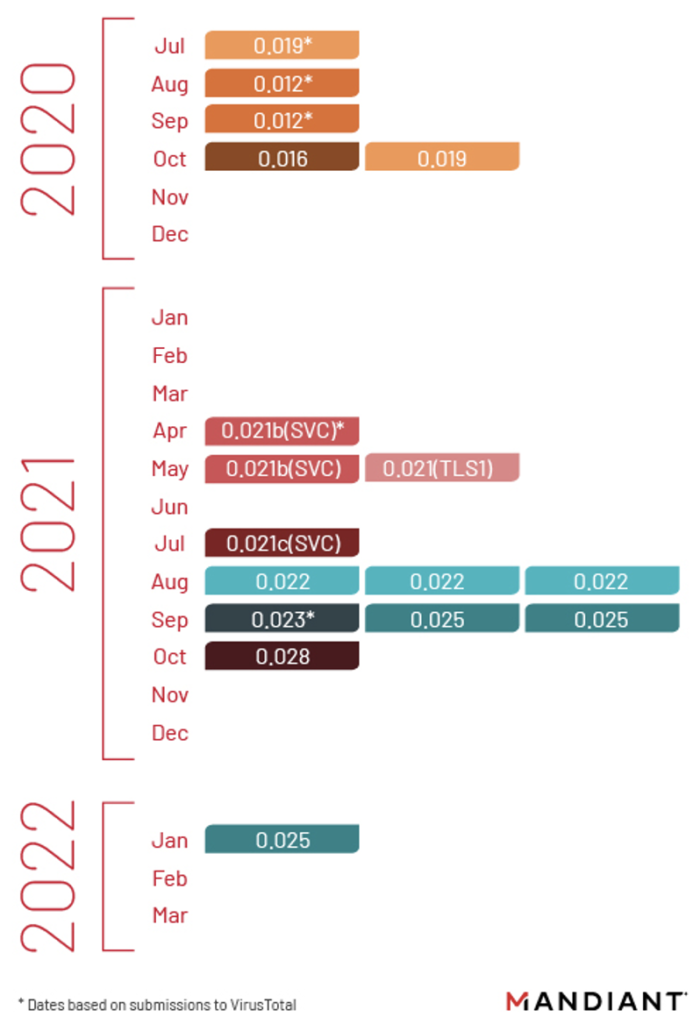
According to Mandiant, PowerPlant has replaced Loadout and Griffon in 2022 operations, while the Carbanak and Diceloader malware have also taken a back seat. During deployment, PowerPlant fetches different modules from the C2 server, so the resulting set of capabilities varies. Two of the most commonly deployed modules are named Easylook and Boatlaunch.
Easyloook is a reconnaissance utility that FIN7 has used for at least two years to capture network and system information details like hardware, usernames, registration keys, operating system versions, domain data, etc.
AMSI (antimalware scan interface) is a built-in Microsoft tool that helps detect malicious PowerShell execution, so Boatlaunch is there to help prevent that. Mandiant has spotted both 32-bit and 64-bit module versions.
Another new development is the evolution of the Birdwatch downloader, which has two variants now, named Crowview and Fowlgaze. Both variants are .NET-based, but contrary to Birdwatch, they feature self-deletion capabilities, come with embedded payloads, and support additional arguments.
Like Birdwatch, these new variants support retrieving payloads over HTTP and continue to offer basic reconnaissance operations that tell FIN7 what processes run on the system, what the network configuration is, and what web browser is used.
FIN7 and Ransomware
In at least two incident response engagements in 2020, FIN7 intrusion activities were recognized before ransomware encryption, including the utilization of MAZE and RYUK. Comparatively, in 2021, Mandiant ascribed dynamic FIN7 interruption action during an occurrence reaction commitment including ALPHV ransomware. In this large number of cases, the ransomware organization is presently credited with independently followed danger bunches because of variables of the examination and our visibility.
“In addition to evidence produced from intrusion data, secondary artifacts suggest FIN7 played a role in at least some DARKSIDE operations,” says Mandiant
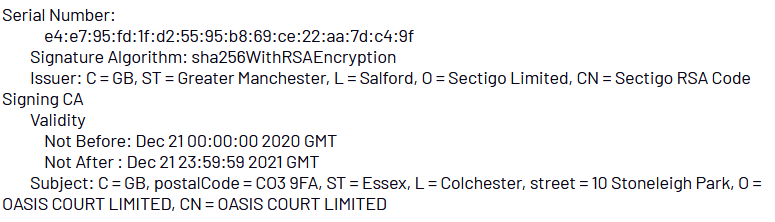
“A low global prevalence code signing certificate used by FIN7 in 2021 to sign BEACON and BEAKDROP samples were also used to sign multiple unattributed DARKSIDE samples recovered in the wild.”
The specifically mentioned code signing certificate used by FIN7 contained the SSL subject common name of “OASIS COURT LIMITED”
Indicators of Compromise (IOCs)
| Indicator | Notes |
0c6b41d25214f04abf9770a7bdfcee5d | BOATLAUNCH 32bit |
21f153810b82852074f0f0f19c0b3208 | BOATLAUNCH 64bit |
02699f95f8568f52a00c6d0551be2de5 | POWERPLANT |
0291df4f7303775225c4044c8f054360 | POWERPLANT |
0fde02d159c4cd5bf721410ea9e72ee2 | POWERPLANT |
2cbb015d4c579e464d157faa16994f86 | POWERPLANT |
3803c82c1b2e28e3e6cca3ca73e6cce7 | POWERPLANT |
5a6bbcc1e44d3a612222df5238f5e7a8 | POWERPLANT |
833ae560a2347d5daf05d1f670a40c54 | POWERPLANT |
b637d33dbb951e7ad7fa198cbc9f78bc | POWERPLANT |
bce9b919fa97e2429d14f255acfb18b4 | POWERPLANT |
d1d8902b499b5938404f8cece2918d3d | POWERPLANT |
edb1f62230123abf88231fc1a7190b60 | POWERPLANT |
findoutcredit[.]com | POWERPLANT C2 |
againcome[.]com | POWERPLANT C2 |
modestoobgyn[.]com | POWERPLANT C2 |
myshortbio[.]com | POWERPLANT C2 |
estetictrance[.]com | POWERPLANT C2 |
internethabit[.]com | POWERPLANT C2 |
bestsecure2020[.]com | POWERPLANT C2 |
chyprediction[.]com | POWERPLANT C2 |
d405909fd2fd021372444b7b36a3b806 | POWERTRASH Cryptor & CARBANAK Payload |
122cb55f1352b9a1aeafc83a85bfb165 | CROWVIEW (BIRDWATCH/JssLoader Variant) |
domenuscdm[.]com | CROWVIEW/LOADOUT C2 |
936b142d1045802c810e86553b332d2d | LOADOUT |
23e1725769e99341bc9af48a0df64151 | LOADOUT |
4d56a1ca28d9427c440ec41b4969caa2 | LOADOUT |
50260f97ac2365cf0071e7c798b9edda | LOADOUT |
spontaneousance[.]com | LOADOUT C2 |
fashionableeder[.]com | LOADOUT C2 |
incongruousance[.]com | LOADOUT C2 |
electroncador[.]com | LOADOUT C2 |
6fba605c2a02fc62e6ff1fb8e932a935 | BEAKDROP |
49ac220edf6d48680f763465c4c2771e | BEACON |
astara20[.]com | BEACON C2 |
coincidencious[.]com | BEACON C2 |
52f5fcaf4260cb70e8d8c6076dcd0157 | Trojanized installer containing Atera Agent |
78c828b515e676cc0d021e229318aeb6 | WINGNIGHT |
70bf088f2815a61ad2b1cc9d6e119a7f | WINGNIGHT |
4961aec62fac8beeafffa5bfc841fab8 | FLYHIGH |
Source : Mandiant / bleeping Computer



































