Google scale threat detection Detect Everything
The biggest challenge that the security operations team faces is the volume and rate of cybersecurity attacks. The alerts have grown to the point where absolute numbers are difficult to deal with. The cause for this could be the growing complexity of technology systems, as well as people’s reliance on them. Once there was only the website and a firewall, but now there are multiple flows of bi-directional data, Internet, third party and wireless gateways, users with their own devices as well as company-issued ones, and data and applications in the cloud. The attacker community’s intelligence and professionalism are increasing now a day.
“Malware and botnets are available as services; the market is complicated, functional, and worldwide; ransomware, phishing attacks, and intrusions have advanced to the point where basic controls are no longer effective”
Computers help to solve this problem by being able to repeat complex analyses predictably and reliably; however, they aren’t as “tuned in” as the human mind at spotting things that are “interesting” unless they have been programmed to do so, or, as is becoming more common, they have been programmed to “learn how to” do so. To address all these within a single tool is impossible. Every SOC has a user-friendly SIEM tool to collect and analyze logs and for alerting rules. We all usually think of SIEM as it’s just a log collecting tool, but Google has proved that it’s more than a log collecting tool by releasing its own SIEM tool CHRONICLE.
“Chronicle is a global security telemetry platform for detection, investigation, and threat hunting within the enterprise network. Chronicle makes security analytics instant, easy, and cost-effective.”
Also Read: Latest Cyber Security News – Hacker News !
Why do we need the Chronicle?
The mission of the Chronicle is to build a large-scale system for storing and analyzing all security telemetry and making it useful for detecting, hunting, and responding to threats quickly. The speed for the search is really quick because it is in the Google cloud.
The Security analytics provided by the chronicle are:
- SIEM for Event logs.
- Threat Intelligence Platform/Feeds for Threat Intel.
- EDR solution for Endpoint logs.
- Identity and Access Management for User/Access logs.
- For vulnerability data, there is a vulnerability management service.
- DNS/Proxy logs are stored in a web/network service.
Chronicle Architecture:
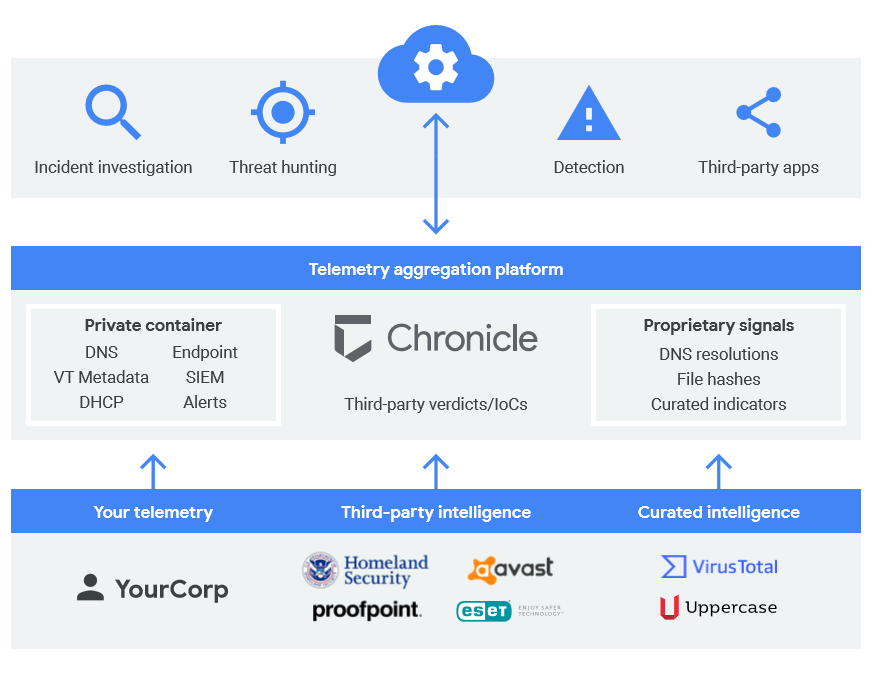
Here the first layer is the specialized applications for investigation. The second layer is to retain, analyze and automate. And the third layer is fed with enterprise telemetry, 3rd party threat feeds, and curate threat signals.
Capabilities and benefits of Chronicle:
| Feature | Description | Benefit |
| Continuous enrichment | Automated IP to host correlation | Time to investigate is reduced, and analyst productivity is increased. |
| Context and insights (threat / IoC, vulnerability, asset, user, file/process) | 1) Threat intelligence sources embedded in the system (Proofpoint, DHS AIS, OSInt, Avast, ESET) 2) Threat intelligence sources provided by the customer 3) User context, asset, and vulnerability 4) Derived Insights | Time to investigate is reduced, and analyst productivity is increased. |
| Read APIs | APIs that expose Backstory functionality to downstream enterprise and MSSP SOC playbook stages and tools with high performance (ticketing, orchestration, dashboarding) | 1) Automation of SOC playbooks 2)Integration with MSSP portals 3) Faster time to remediation |
| Ingest APIs and Unified Data Model | APIs with high throughput that allow data to be sent directly to the Backstory data pipeline without the use of a Forwarder | Time to value is faster, and there is no deployment footprint. |
| Raw Log Scan | 1) Full access to all fields that haven’t been parsed 2) Look for any unprocessed security telemetry. | All security telemetry is onboarded more quickly. |
| Security / Compliance | 1) Adherence to Google Cloud common controls 2) SOC 2 and SOC 3 3) ISO 27001 4) HIPAA BAA | At every tier, there are documented, severe rules in place to protect the data. |
Why Chronicle is different from other SIEM platforms?
There are more SIEM platforms. But Chronicle is standing a little bit up from those all because of the following reasons:
Intelligent Data Fusion: The timeless and enriched data model for investigation and detection.
- Unified data model: A rich, flexible data model with dimensions and attributes covering asset, user, and IoC.
- IP to host correlation: Automated IP to host correlation enables instant asset and IoC analytics.
- Historical event deduplication: Analysis is made easier and faster due to the logical event layer (user logins, network connections, and so on) and visualization.
Continuous IOC Evaluation: Continuous, retrospective analysis of telemetry vs. threat intelligence.
- IoC matching is automated, continuous, and retroactive.
- Instant correlation of IoCs against 1 full year of security telemetry.
- IPs, domains, URLs, and files have intelligence feeds available out of the box.
- Threat Intel Platforms and customer-owned threat intelligence subscriptions are supported (TIPs)
Modern Threat Detection: YARA-L for detecting modern malware-based threats.
- Broad coverage like logs, EDR, traffic, etc.
- Real-time and historical
- Unified data model
- Smart matching
- Focused detection language YARA-L (clear and easy detection, not data queries)
- Mix and match rules and ML models
Hunt At Google Speed: Sub-second searches against petabytes of data.
Self-Managed: Unlimited scale-out without customer tuning, sizing, or management.
Disruptive Economics: Full security telemetry retention, analysis at a fixed, predictable cost.
- Future proof investment: Capture, analyze all enterprise security telemetry at a fixed annual cost per employee, NOT based on data volume.
- Eliminate costs and effort: SaaS model eliminates hardware, setup, and expansion costs.
- No infrastructure setup costs.
- All the data at a fixed cost.
- Sub-second latency searches.
- No proprietary search language.
- Analyst efficiency multiplier.
Two main products of chronicle:
The two cybersecurity tools Tanium and Backstory provide customers with a real-time, integrated view of activity across the enterprise environment.
Backstory:
The backstory is the first global security telemetry platform designed for a world that thinks in petabytes. The backstory is a global cloud service where companies can privately upload, store, and analyze their internal security telemetry to detect and investigate potential cyber threats.
How does it work?
Chronicle built a new layer over core Google infrastructure where we can upload the security telemetry, including high-volume data such as DNS traffic, Netflow, endpoint logs, proxy logs, etc. so that it can be indexed and automatically analyzed by the analytics engine. The data remains private. It isn’t scanned by or available to anyone for other purposes.
Backstory compares the network activity against a continuous stream of threat intelligence signals, curated from a variety of sources, to detect potential threats instantly. It also continuously compares any new piece of information against the company’s historical activity, to notify any of the historical access to known-bad web domains, malware-infected files, and other threats. The backstory was designed for a world where companies generate massive amounts of security telemetry and struggle to hire enough trained analysts to make sense of it.
Also Read: Advanced Hunting to Find the Ransomware
Tanium:
Chronicle also integrated with Tanium which is feature-packed endpoint management and endpoint security platform designed to strengthen and optimize an organization’s cybersecurity efforts. It provides more effective investigations and responses to cyber-attacks. Tanium’s endpoint security and management platform provide a unified view across customer endpoints, as well as automated remediation capabilities.
Customers using Tanium Threat Response can proactively send enterprise-wide endpoint telemetry to Backstory for rapid incident investigation and remediation. Backstory links Tanium endpoint telemetry with network, vulnerability, threat intelligence, and other information into a complete and unified data structure. Having both the right types of data and enough of that data allows security teams to better understand what has happened and is still happening in their networks.
Also Read : Threat Hunting using Sysmon – Advanced Log Analysis for Windows
How do investigate a phishing attack with Backstory?
We need to analyze a phishing email. This can either be an alert generated by a security tool or a forwarded email coming from the end-user, who found a particular email to be suspicious. In either case, we need to treat the potential phishing email like a crime scene. We need to use the evidence that we do have to carry out our investigation. A common phishing email will say something like,
“Please review the document to proceed further”
Now, we can begin our investigation with Backstory using the evidence that we have, in this case– a link to a website. Begin by entering the domain name into Backstory. In this example, we’re using the phishing domain drroppbox[.]com. Backstory will search through an entire year of the company’s network data to see if anyone in the organization has ever visited the website that was linked in the email.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
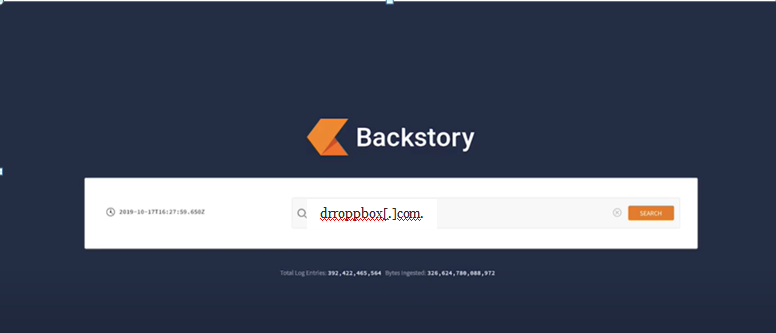
By hitting the Search button, we can see all of the network connections to the domain.
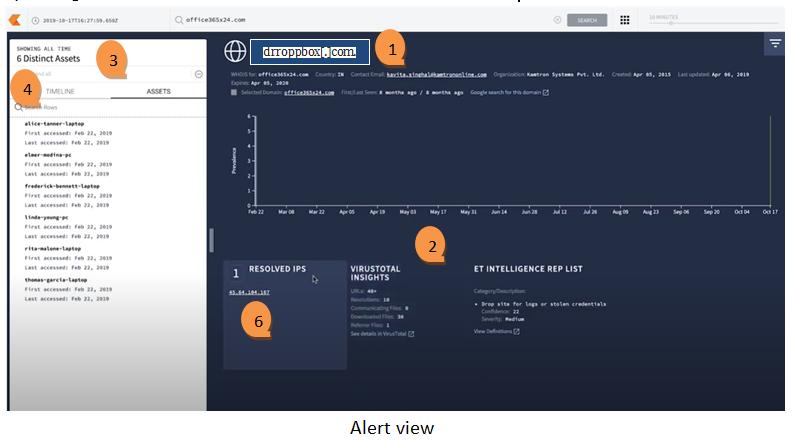
In the above example,
- No special query language was needed, and we can see the six people in our organization that have ever visited the domain drroppbox[.]com.
- On the right-hand side of the screen, we can see all of the automatic enrichment that Backstory does to this domain. This includes information from WhoIs, threat intelligence information, VirusTotal information, and passive DNS information as well.
- On the left side, there is a list of people who visited it. While it’s important to know that the six people visited the website, it’s also important to know what they did when they were at that website.
- By going to the Timeline view, we can search for a POST request to the domain. There is 2 POST request to the login[.]php page. This likely indicates that they posted their credentials to this website.
- Now from here, we would follow the remediation playbook to make sure that everything is cleaned up. To understand the full scope of this campaign, we can take our investigation deeper.
- By clicking on this IP address, we can see all of the network connections to this IP address, not just to this particular domain.
Also Read: Latest Ransomware CVEs – Vulnerabilities Abused by Ransomware Actors
Conclusion:
We can’t say chronicle as just a SIEM, it’s good to say it as a “Security analytics” tool. Overall it is providing SIEM, Threat intelligence and hunting, SOAR, SOC playbook, etc. And the main factor is, it is in the cloud. So jumping into the new SIEM will make SOC operations more effective.



































