Security researchers have noticed a malicious campaign that used Windows event logs to store malware, a technique that has not been previously documented publicly for attacks in the wild. The method enabled the threat actor behind the attack to plant fileless malware in the file system in an attack filled with techniques and modules designed to keep the activity as stealthy as possible.
Besides the event logs the actor is obsessed with memory injection – lots of RAT commands are related to it and are used heavily. Along with the aforementioned custom modules and techniques, several commercial pentesting tools like Cobalt Strike and SilentBreak’s toolset are used.
The infection chain
In February 2022 Denis Legezo, a lead security researcher at Kaspersky observed the technique of putting the shellcode into Windows event logs for the first time “in the wild” during the malicious campaign. It allows the “fileless” last stage Trojan to be hidden from plain sight in the file system.
Also Read: Windows Event ID 5379 to Detect Malicious Password-Protected File unlock
Researchers divide it into classes to technically describe this campaign. Actually, covers the following sets of modules: commercial pentesting suites, custom anti-detection wrappers around them, and last stage Trojans.
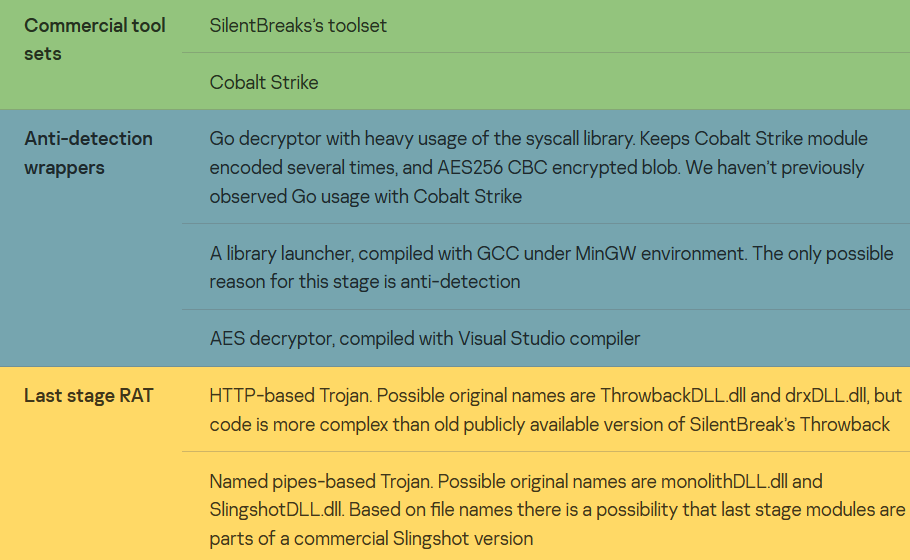
Initial infection
The investigation tracked the initial stage of the attack to September 2021 when the victim was tricked into downloading a RAR archive from the file sharing service file.io.
The threat actor then spread the Cobalt Strike module, which was signed with a certificate from a company named Fast Invest ApS. The certificate was used to sign 15 files and none of them were legitimate.
Due to the different infection scenarios for all the targeted hosts, we will describe just one of the observed ones. Having the ability to inject code into any process using Trojans, the attackers are free to use this feature widely to inject the next modules into Windows system processes or trusted applications such as DLP.
For the anti-detection wrappers, different compilers are in use. Besides MSVC, Go compiler 1.17.2 and GCC under MinGW have been used.
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
Dropper in DLL, search order hijacking
This code is injected into Windows processes such as explorer.exe. At its single entry point after being loaded into the virtual address space of the launcher process, the dropper removes files created by previous stages or executions.
Firstly, the module copies the original legitimate OS error handler WerFault.exe to C:\Windows\Tasks. Then it drops one of the encrypted binary resources to the wer.dll file in the same directory for typical DLL search order hijacking. For the sake of persistence, the module sets the newly created WerFault.exe to autorun, creating a Windows Problem Reporting value in the Software\Microsoft\Windows\CurrentVersion\Run Windows system registry branch.
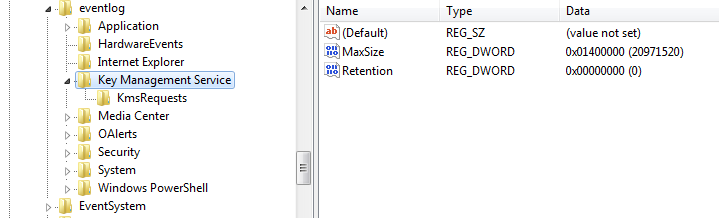
The dropped wer.dll is a loader and wouldn’t do any harm without the shellcode hidden in Windows event logs. The dropper searches the event logs for records with category 0x4142 (“AB” in ASCII) and having the Key Management Service as a source. If none is found, the 8KB chunks of shellcode are written. Created event IDs are automatically incremented, starting from 1423. Microsoft Key Management Service (KMS) enables organizations to activate systems within their own network, eliminating the need for individual computers to connect to Microsoft for product activation.
The event logs technique, which we haven’t seen before, is the most innovative part of this campaign. With at least two commercial products in use, plus several types of last-stage RAT and anti-detection wrappers, the actor behind this campaign is quite capable. There is the possibility that some of the modules we described here as custom ones are part of a commercial toolset as well. The code is quite unique, with no similarities to known malware. Securelist will continue to monitor similar activity.
Also Read: Latest Cyber Security News – Hacker News !
Indicators of Compromise
File Hashes (malicious documents, trojans, emails, decoys)
Dropper
822680649CDEABC781903870B34FB7A7
345A8745E1E3AE576FBCC69D3C8A310B
EF825FECD4E67D5EC5B9666A21FBBA2A
FA5943C673398D834FB328CE9B62AAAD
Logs code launcher
2080A099BDC7AA86DB55BADFFBC71566
0D415973F958AC30CB25BD845319D960
209A4D190DC1F6EC0968578905920641
E81187E1F2E6A2D4D3AD291120A42CE7
HTTP Trojan
ACE22457C868DF82028DB95E5A3B7984
1CEDF339A13B1F7987D485CD80D141B6
24866291D5DEEE783624AB51516A078F
13B5E1654869985F2207D846E4C0DBFD
Named pipes trojan and similar
59A46DB173EA074EC345D4D8734CB89A
0B40033FB7C799536C921B1A1A02129F
603413FC026E4713E7D3EEDAB0DF5D8D
Anti-detection wrappers/decryptors/launchers, not malicious by themselves
42A4913773BBDA4BC9D01D48B4A7642F
9619E13B034F64835F0476D68220A86B
0C0ACC057644B21F6E76DD676D4F2389
16EB7B5060E543237ECA689BDC772148
54271C17684CA60C6CE37EE47B5493FB
77E06B01787B24343F62CF5D5A8F9995
86737F0AE8CF01B395997CD5512B8FC8
964CB389EBF39F240E8C474E200CAAC3
59A46DB173EA074EC345D4D8734CB89A
A5C236982B0F1D26FB741DF9E9925018
D408FF4FDE7870E30804A1D1147EFE7C
DFF3C0D4F6E2C26936B9BD82DB5A1735
E13D963784C544B94D3DB5616E50B8AE
E9766C71159FC2051BBFC48A4639243F
F3DA1E157E3E344788886B3CA29E02BD
Host-based IoCs
C:\Windows\Tasks\wer.dll
C:\Windows\Tasks\WerFault.exe copy of the legit one to sideload the malicious .dll
Named pipe MonolithPipe
Event logs with category 0x4142 in Key Management Service source. Events ID auto increments starting from 1423.
PDB paths
C:\Users\admin\source\repos\drx\x64\Release\sb.pdb
C:\Users\admin\source\repos\drx\x64\Release\zOS.pdb
C:\Users\admin\source\repos\drx\x64\Release\ThrowbackDLL.pdb
C:\Users\admin\source\repos\drx\x64\Release\drxDLL.pdb
C:\Users\admin\source\repos\drx\x64\Release\monolithDLL.pdb
Source/Credits: https://securelist.com/a-new-secret-stash-for-fileless-malware/106393/



































