Attackers are always looking for new ways to bypass security defenses, and archive files such as ZIPs, RARs, and ISOs have become one of their favorite tools for delivering malware. These seemingly harmless compressed files often contain dangerous payloads designed to steal data, spy on victims, or grant cybercriminals remote access to systems.
But why are archives so effective for malware distribution? Let’s explore the key reasons cybercriminals rely on them and how security teams can detect and analyze these threats.
1. Archives Bypass Email Security Filters
Many email security tools scan attachments for malicious content, but archives act as a wrapper that can hide malware from initial detection. Some security tools don’t fully inspect the contents of ZIPs, allowing malicious files to reach inboxes.
2. Social Engineering & Trust Exploitation
Cyber attackers take advantage of human psychology. ZIP files are particularly useful for phishing attacks because they blend perfectly into everyday business communication.
Attackers use different tactics to make sure their targets open them:
- They disguise the archive as an invoice, contract, or shipping document; something people expect to receive in a professional setting.
- They impersonate trusted senders, using fake email addresses that mimic colleagues, clients, or suppliers.
- They create urgency, pushing the recipient to act fast without thinking.
- They exploit curiosity, making the attachment seem important or relevant.
- They take advantage of the fact that opening a ZIP file doesn’t immediately trigger alarm. So, malware can sit inside quietly, waiting to execute.
Here’s an example of a real-world attack analyzed inside the secure ANY.RUN sandbox.
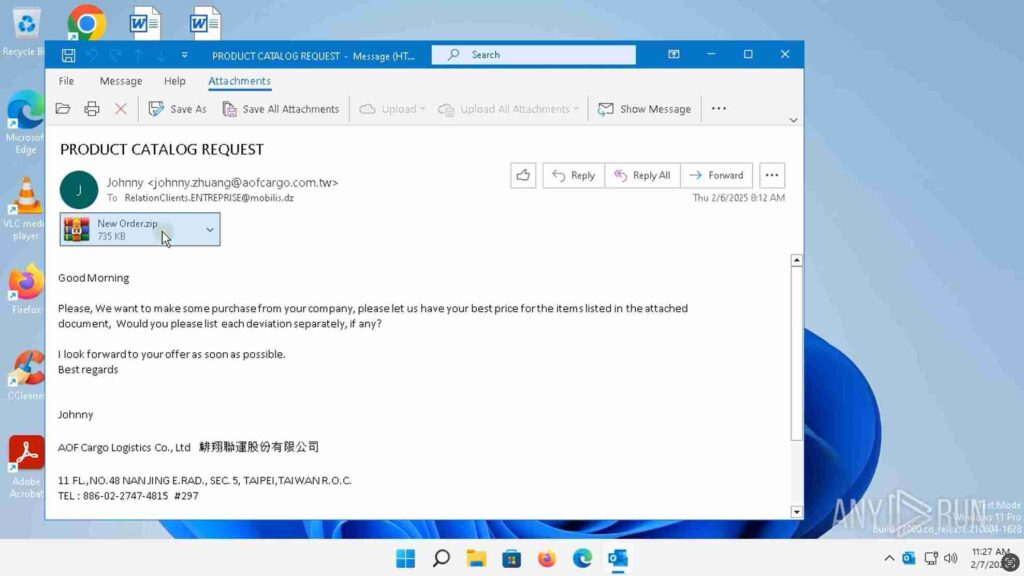
Phishing email with malicious archive analyzed inside ANY.RUN sandbox
In this analysis session, the attackers posed as potential buyers, claiming they were interested in placing an order. They asked the recipient to open the attached ZIP file, supposedly containing a product catalog with the items they wanted to purchase.
| Equip your team with real-time threat analysis. Sign up for a free 14-day trial of ANY.RUN today to speed up investigations, enhance security operations. Sign up now |
On the surface, nothing about this email seems suspicious. It’s the kind of message many businesses receive daily.
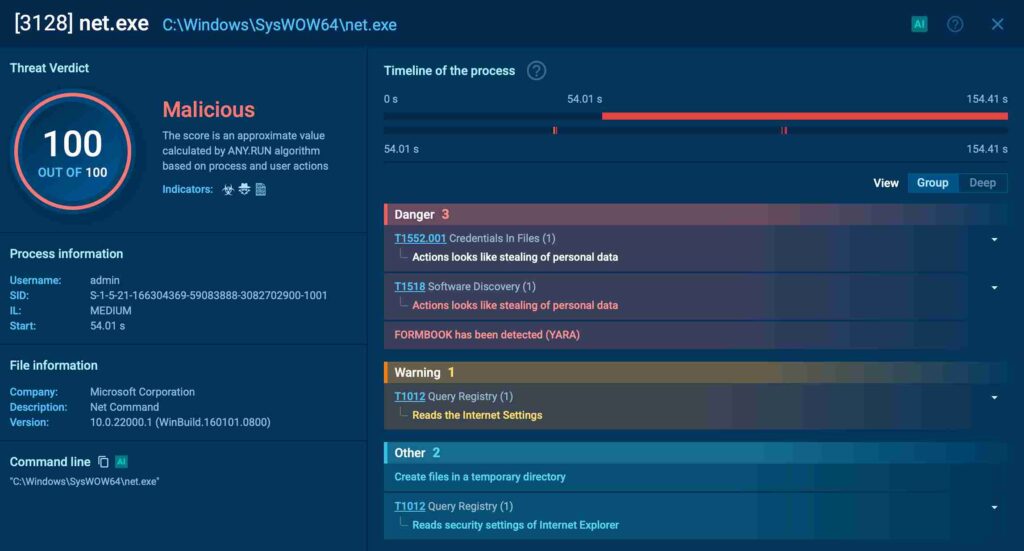
Malicious .exe file detected by ANY.RUN
However, the ZIP file attached was malicious. Instead of a legitimate product list, it contained an EXE file that, once opened, installed Formbook malware.
This info-stealer silently ran in the background, stealing credentials, and exfiltrating sensitive data.
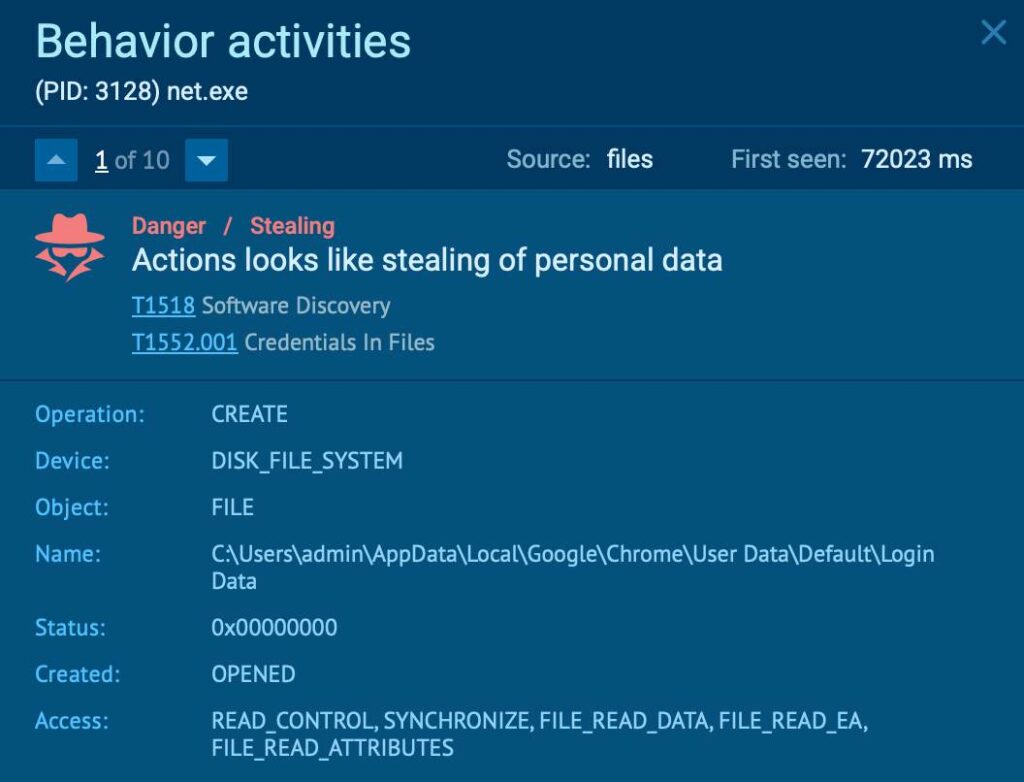
Malicious activities detected inside ANY.RUN sandbox
3. Archives Can Bundle Multiple Malware Files
One of the biggest advantages for attackers is that archives can contain multiple malware components. This allows them to:
- Drop several malicious files into the victim’s system
- Execute scripts to install additional payloads
- Avoid triggering detection mechanisms by running files in a specific order
4. Evasion via Password-Protected Archives
Attackers often encrypt or password-protect ZIP files to make detection even more difficult. Since most email security systems can’t scan encrypted files, the malicious payload inside remains hidden until the recipient manually extracts it.
This tactic serves a dual purpose. First, it bypasses automated security filters, allowing the email to reach the inbox without triggering alerts.
Second, it adds an element of credibility, making the recipient believe the file contains sensitive or confidential information. A password-protected archive feels more secure and legitimate, leading to a false sense of trust.
To reinforce this, attackers often include the password in the email body, making it seem like an intentional security measure. For example, an email might say:
“For security reasons, we’ve protected this document with a password. Use 1234 to unlock the file.”
Once the recipient enters the password and extracts the archive, the malware executes, infecting the system before any security software can intervene.
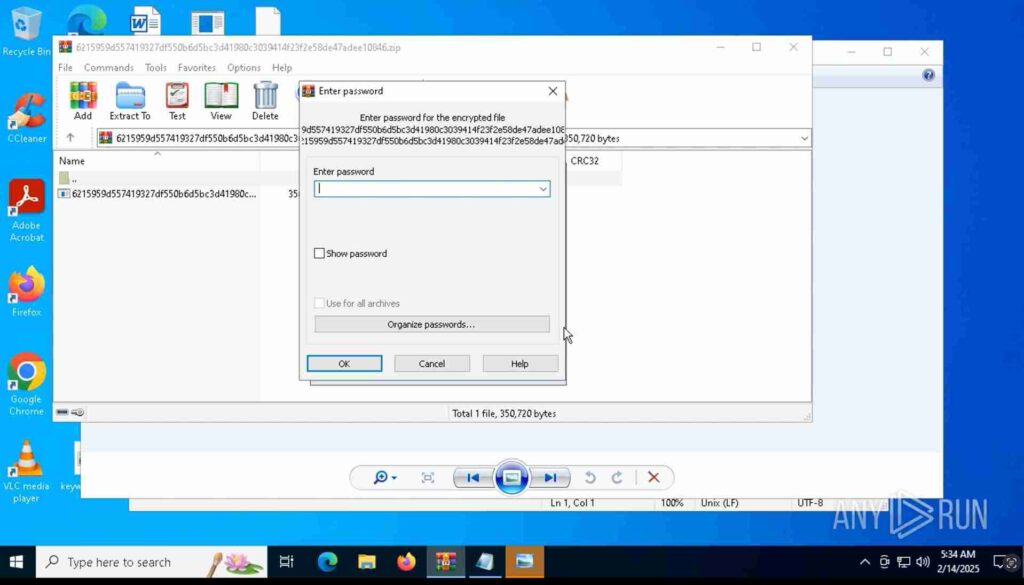
Password request for malware distribution analyzed inside ANY.RUN
Fast Detection and Analysis of Archive-Based Malware
Since archive-based attacks are designed to evade traditional security tools, analyzing them in an interactive malware sandbox is one of the most effective ways to uncover threats.
A sandbox like ANY.RUN provides real-time interactive analysis, allowing security teams to:
- Observe how a malware sample executes inside an isolated environment
- Track network activity and connections to malicious servers
- Identify behavioral indicators of malware before it can infect real systems
- Collect IOCs for threat intelligence and security investigations.
- Get a shareable report for teams, incident response, or law enforcement.
Sign up for a free 14-day trial of ANY.RUN today to analyze unlimited threats in real time!



































