Technologies are always surprising us with new innovations. Experts and cyber-interested folks are introducing more useful software/technology when it comes to cyber-related technologies. Password attacks contribute to 70% of all security breaches. Each day, creating a password for each console is like traversing a sea. Those who work in the shared SOC are aware of the challenges. I’m also a member of the SOC team, and I’m dealing with the same issue every day as our client base grows. It’s a headache to remember separate passwords for each of your web accounts! Cybercriminals may be able to take over your account if you use the same one all the time. FIDO ( Fast ID Online ) is a revolutionary technology that allows you to securely sign in to websites without using a password.
Passwordless Feature organizations:
We may finally bid farewell to our passwords. Google, Apple, and Microsoft have all stated that passwordless compatibility will be built into their respective device platforms. The three technology companies will roll out passwordless FIDO sign-in standards across Android, Chrome, iOS, macOS, and Safari, as well as Windows and Edge, over the next year. This means that you won’t need a password to log into devices, websites, or applications any time soon. Instead, your phone will keep a passkey, a FIDO credential that can be used to unlock your device as well as your entire online account.
Also Read: Osquery for Cyber Threat Detection & Incident Response
What is the FIDO Alliance?
The FIDO Alliance is an open industry organization that was founded in 2013 with the goal of developing authentication standards that “help minimize the world’s over-reliance on passwords.”
The idea of using biometrics to authenticate users instead of passwords was first addressed in 2009 at a meeting between PayPal and Validity Sensors. This conversation sparked the idea for a passwordless login industry standard based on public-key cryptography and local authentication techniques.
Three sets of specifications have been issued by the FIDO Alliance, all of which are based on public-key cryptography:
- Universal Authentication Framework (UAF)
- Universal Second Factor (U2F)
- FIDO2
FIDO Universal Authentication Framework (UAF):
- The FIDO UAF protocol enables online service providers to provide passwordless sign-on experiences to their customers. If further security is desired, multi-factor sign-on experiences are also available.
- Users must have a personal device, such as a computer or smartphone, and must register with an internet service to use UAF. Users are asked to choose the method they want to use to authenticate with the service in the future throughout the registration process.
- Service providers assess which authentication procedures are appropriate and provide a list of possibilities, which could include facial or voice recognition, fingerprint reading, or entering a PIN. Users can authenticate using more than one of these alternatives if a multi-factor sign-on experience is necessary.
- Users no longer need to type their passwords to log in; instead, they can use the methods they choose to authenticate themselves.
Also Read: PECmd – Windows Prefetch Analysis For Incident Responders
How exactly does it work?
Registering process:
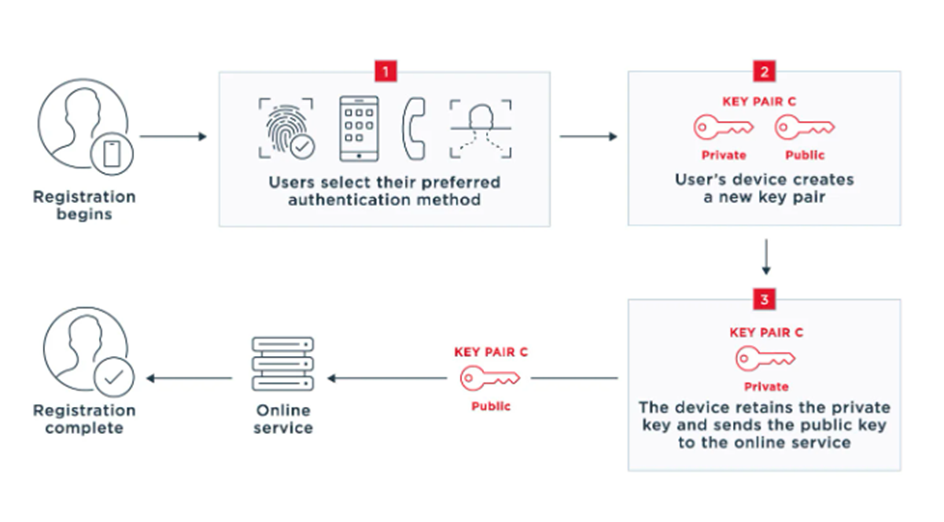
Let’s begin by discussing the registration process. When a person first attempts to access an online service, they are prompted to register.
- The user selects the authentication method they want to use to sign in during the registration process. Only methods that comply with the acceptance policy of the service are available.
- The user’s device, which could be a laptop or a smartphone, generates a new key pair that is specific to the device, online service, and user account.
- The private key is kept on the user’s device, while the public key is sent to the online service linked with the user’s account, completing the registration process.
- Throughout the process, communication is encrypted, and private keys and biometric information never leave users’ devices, thus reduces the risk of security breaches.
After the registration process:
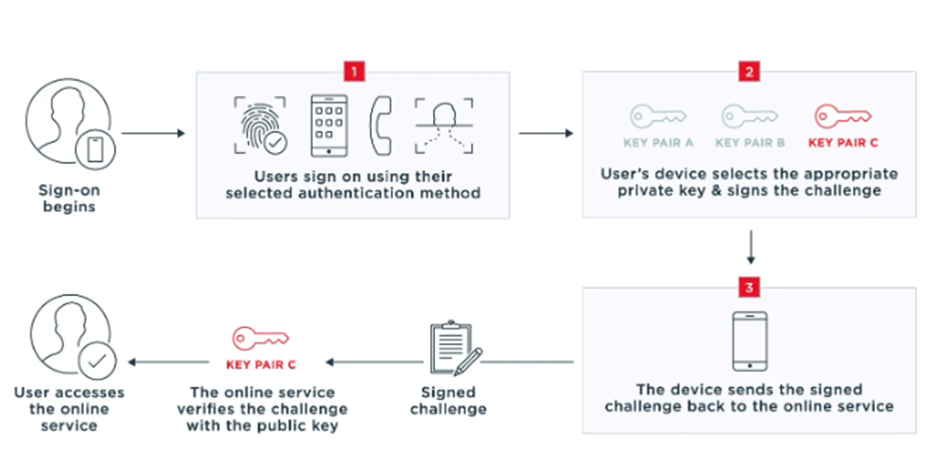
The user can quickly access the application after registration by using the authentication method they selected.
- The user logs in to the online service using the identity verification method they selected.
- The device selects the appropriate private key using the account identifier and signs the online service’s challenge in a way that proves the device has the private key.
- The device transmits the signed challenge back to the online service, which verifies it against the public key and grants the user access.
FIDO Universal Second Factor (U2F):
Rather of replacing traditional password-based security, the FIDO U2F protocol complements it. Users must give two pieces of documentation to prove their identity with U2F:
- Something they are familiar with, such as their account and password
- They have something, such as a registered fob or USB device. U2F authentication tokens or security keys are security devices that may complete authentication processes using USB, NFC (near-field communication), or Bluetooth technology.
- When the security device is turned on, the computer browser connects with it directly and grants access to the online service.
Also Read: Sigcheck v2.82 – Quick Malware Auditing for Incident Responders
How does it function?
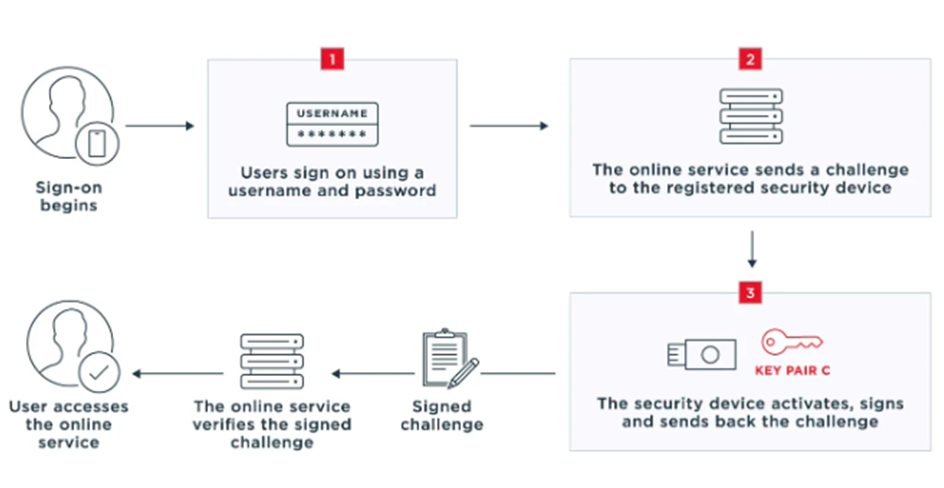
When a person first tries to utilize an online service, they are prompted to register and create a username and password. When a person uses their browser to visit an online service, the following happens:
- The user enters their username and password recognized by that online service.
- The service sends a challenge to the registered security device.
- The security device activates, acknowledges that it received the challenge, signs the challenge in a way that proves it has possession of the private key and sends the signed challenge to the online service.
- The user gains access to the online service. As with the UAF protocol, communication is encrypted throughout this process, and private keys never leave users’ devices.
What is FIDO:
- FIDO stands for Fast Identity Online. FIDO is a new technology that allows you to sign in securely and without using a password to any website that supports it. It works on any web browser and on everyday devices such as your smartphone, desktop or laptop computer, tablet, or smartwatch.
- The Universal Authentication Framework (UAF) and the Universal Second Factor (U2F) protocols are supported by FIDO. During registration with an online service, the client device generates a new key pair using UAF and keeps the private key; the public key is registered with the online service. During authentication, the client device verifies access of the service’s private key by signing a challenge, which involves a user–friendly action like submitting a fingerprint, entering a PIN, taking a picture, or speaking into a microphone.
- A strong second factor, such as an NFC tap or a USB security token, is required for U2F authentication. During login, the user is asked to insert and touch their U2F device. The public key is shared with the online service and associated with the user’s account, and the user’s FIDO-enabled device generates a new key pair. The service can then verify the user’s identity by requesting the registered device to sign a challenge using the private key.
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
Working Architecture:
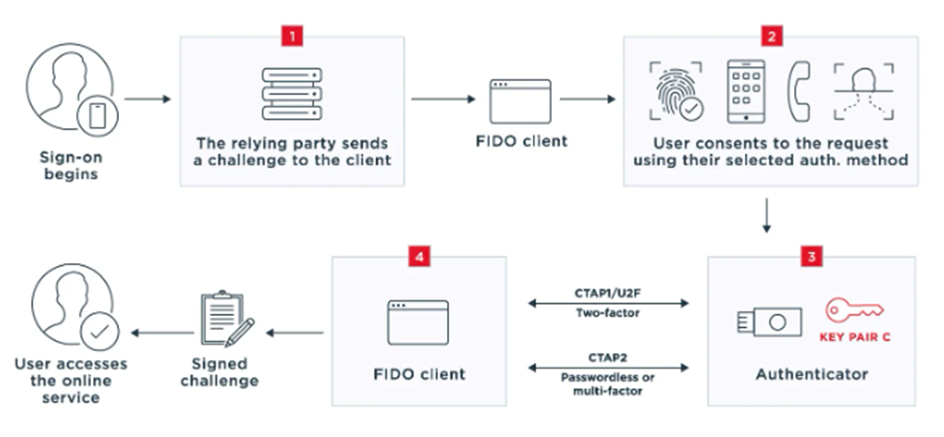
- When the user attempts to sign on to an application, the relying party, also known as a FIDO2 server, sends the FIDO client a challenge using WebAuthn, asking it to sign the data with the private key. The FIDO client could be a browser, desktop application, mobile application, or platform.
- The user consents to the request by using the method of authentication they selected during the registration process.The domain of the relying party is checked against the domain that was associated with this relying party at registration time. If the two do not match the authentication will not be allowed to continue and an error will be displayed. This association and runtime check is what gives FIDO its strong phishing resistance.
- The client obtains the private key from the authenticator. The authenticator can be part of the user’s computer or smartphone, or an external piece of hardware.
- The client signs the challenge in a way that proves the device has possession of the private key, and the user gains access to the online service.
Conclusion:
Finally, we will be liberated from passwords. Using FIDO is a brilliant idea for any company. Despite the existence of password managers for storing credentials, the number of breaches is increasing. As a result, FIDO authentication will reduce security breaches by 50% in the coming year.



































