Hijacking digital signatures is a form of cyber attack where an attacker gains unauthorized access to a digital signature and uses it to sign and distribute malicious code or content. Digital signatures are used to verify the authenticity and integrity of digital documents, software, and other types of digital content.
To hijack a digital signature, an attacker must first gain access to the private key used to create the signature. This can be done through a variety of means, including stealing the key from the legitimate owner, obtaining it through a phishing attack or other social engineering tactic, or exploiting a vulnerability in the software or hardware used to generate and store the key.
Also Read: Finding the Evil in TLS 1.2 Traffic – Detecting Malware on Encrypted Traffic
Malware authors can obtain code signing certificates through a variety of means, including purchasing them from legitimate certificate authorities using stolen identities or fake company names, or by exploiting vulnerabilities in the certificate issuance process.
Once the malware author has obtained a code signing certificate, they can use it to sign their malicious code, making it appear as though it was created by a trusted source. This can help the malware evade detection by security software and make it more difficult for users to identify and remove.
Some of the famous tools to hijack the certificate from trusted binaries include SigPirate & SigThief.
Hijacking Digital Certificate
Let’s attempt to hijack a certificate from a reliable Tor Browser binary executable and apply the certificate to the malicious code ( mimikatz ).
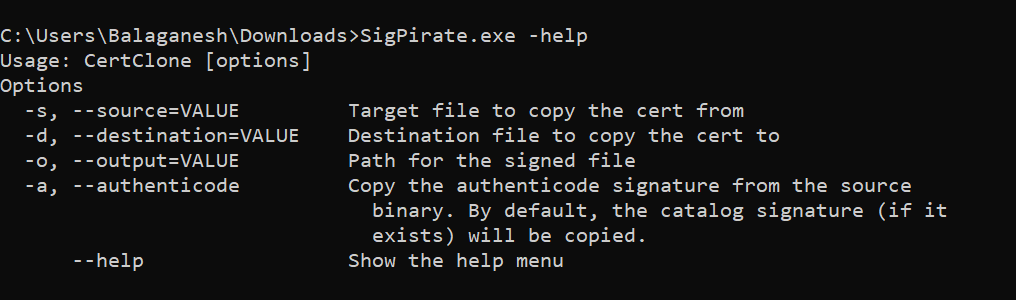
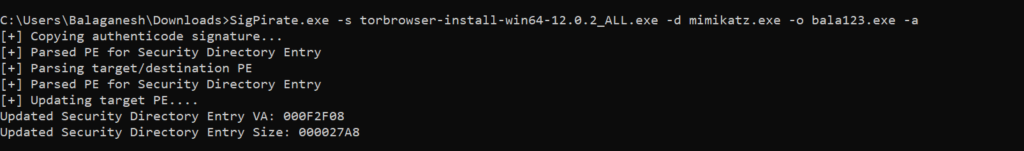
Above figure illustrates, SigPirate stealing the source file ( Tor Browser ) certificate and applying the certificate to the unsigned malware code ( Mimikatz ) and saving the output to a different filename.
How can a Blue team determine if a digital signature is hijacked ?
Blue team can determine if a digital signature hijack attack has occurred on the system. Check the validity of the digital signing hash with Get-AuthenticodeSignature and Review keys of registry values.
Authenticode Signature uses in windows
Authenticode signature is a digital signature technology used by Microsoft Windows operating systems to verify the authenticity and integrity of software and other types of digital content. It is a type of code signing certificate that helps ensure that software and other types of digital content are safe to download and use.
When a file is signed using Authenticode signature, it is given a digital signature that includes information about the file, such as its publisher, version number, and a hash of the file contents. This signature is then embedded in the file, and when the file is opened, Windows checks the signature to verify that the file has not been tampered with or modified since it was signed.
Also Read: JARM Tool – TLS Fingerprint to Detect Malware C2 Proactively
Authenticode signature is used by Windows to provide several important security features, including:
- Authenticity: The digital signature provided by Authenticode signature helps to ensure that the software or digital content was created by a trusted source and has not been tampered with or modified since it was signed.
- Integrity: The digital signature also helps to ensure that the software or digital content has not been modified in any way that could compromise its integrity or security.
- User trust: When users download software or other types of digital content that have been signed using Authenticode signature, they can have greater confidence that the software is safe to use and that it comes from a trusted source.
Abusing code signing certificates is a form of cyber attack where attackers obtain code signing certificates and use them to sign malicious software or other types of digital content. This can make the malware appear legitimate and trustworthy, making it easier to infect computers and evade detection by security software.
There are several tools and techniques that attackers can use to abuse code signing certificates, including:
- Stolen Certificates: Attackers may obtain code signing certificates by stealing them from legitimate certificate holders. This can be done through phishing attacks, malware infections, or by exploiting vulnerabilities in the certificate issuance process.
- Rogue Certificates: Attackers may also obtain code signing certificates by creating fake identities or companies and applying for certificates using fraudulent information. This can be particularly effective if the certificate authority does not have strong identity verification processes in place.
- Certificate Revocation: Even if a certificate is obtained through legitimate means, attackers can abuse it by creating and distributing malware that is signed with the certificate. If the certificate is eventually discovered and revoked, the attacker may simply apply for a new certificate and continue the attack.
Authenticode signature is used by a wide range of software developers and publishers to provide security and trust in their products. It is particularly important for software that is distributed over the internet, as it helps to protect users from downloading and installing malicious software or other types of digital content.
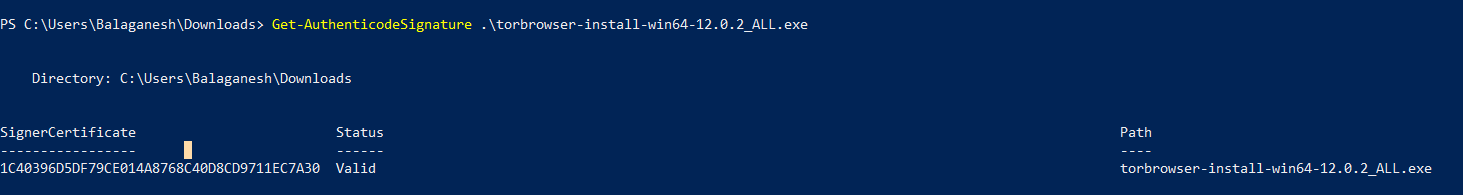
First, we are going to launch the Get-AuthenticodeSignature in powershell to check the digital certificate issuer, Serial number, Dates & Subject details.
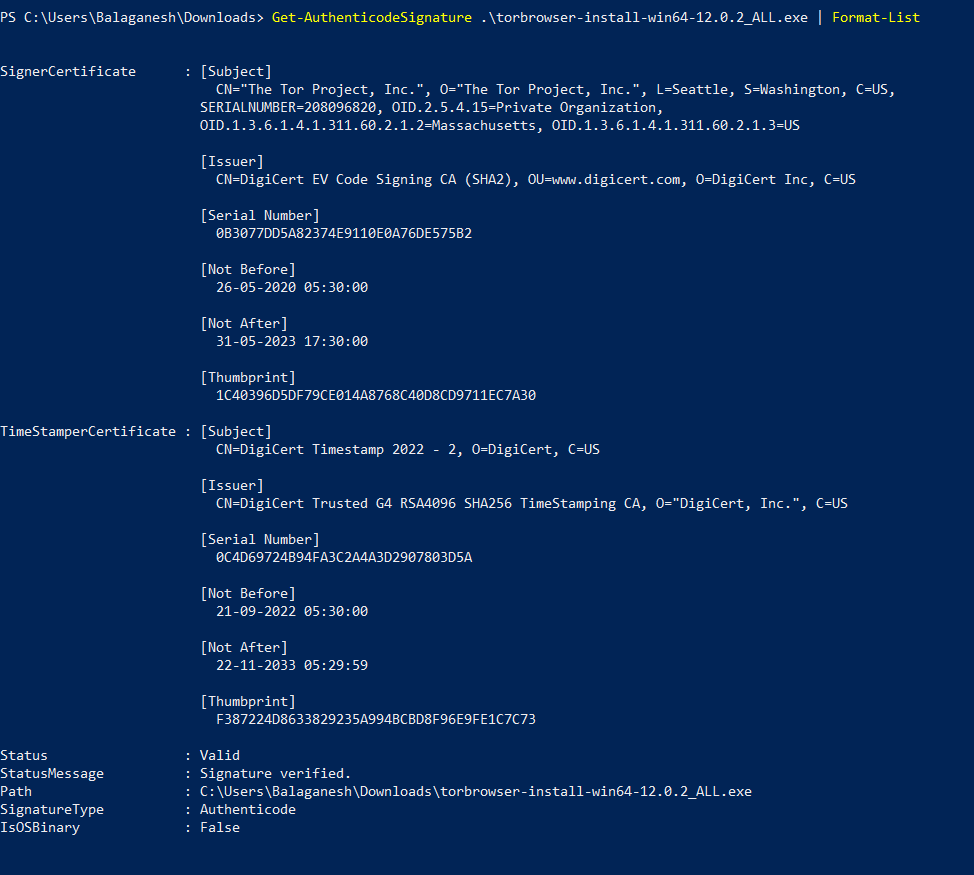
Above figure shows , signature is valid and the type is Authenticode.
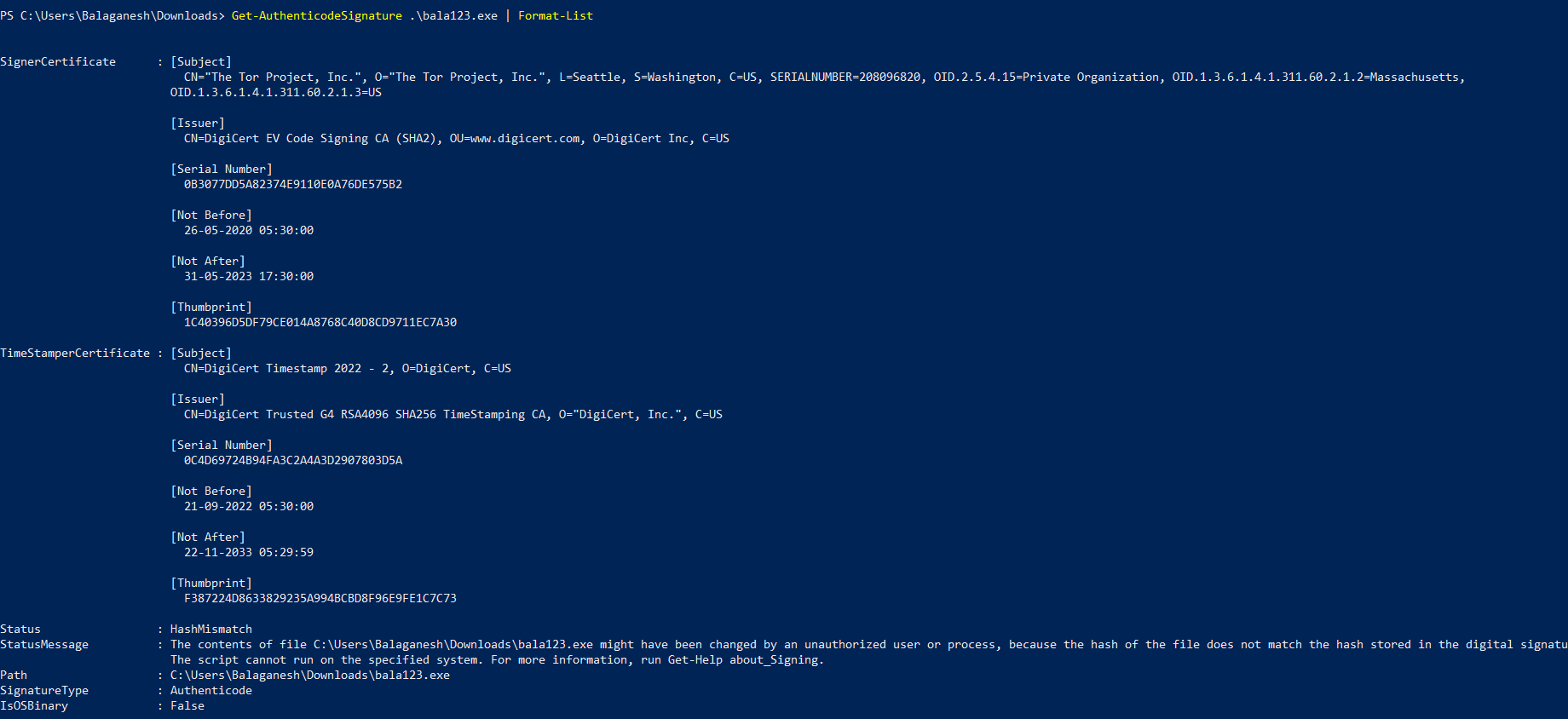
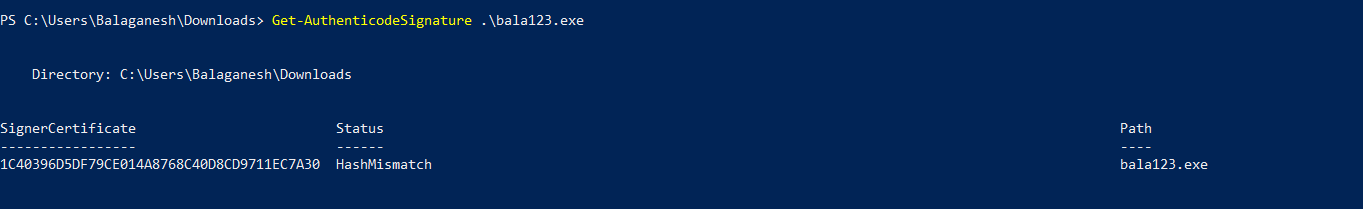
The figure above shows , Hash Status shows Mismatch that bring to our attention that the above certificate is hijacked and the signatures are applied to the mimikatz tool.
Also Read: Soc Interview Questions and Answers – CYBER SECURITY ANALYST
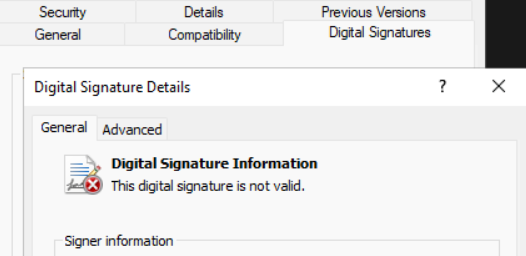
Authenticode Signature Mismatch:
Misused certificate gets a HashMismatch status code. The file hash does not match the hash stored on the digital signature; this may be the identification of an invalid digital certificate.
Attackers can apply other techniques such as changing the registry keys of authenticode & Cryptography to obtain their binary as valid. Monitor below registry key changes.
HKLM\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptSIPDllGetSignedDataMsg\{603BCC1F-4B59-4E08-B724-D2C6297EF351}
DLL – C:\Windows\System32\WindowsPowerShell\v1.0\pwrshsip.dll
FuncName – PsGetSignature
HKLM\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptSIPDllGetSignedDataMsg\{C689AAB8-8E78-11D0-8C47-00C04FC295EE}
DLL – C:\Windows\System32\ntdll.dll
FuncName – CryptSIPGetSignedDataMsg
HKLM\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptSIPDllVerifyIndirectData\{603BCC1F-4B59-4E08-B724-D2C6297EF351}
DLL – C:\Windows\System32\WindowsPowerShell\v1.0\pwrshsip.dll
FuncName – PsVerifyHash
HKLM\SOFTWARE\Microsoft\Cryptography\OID\EncodingType 0\CryptSIPDllVerifyIndirectData\{C689AAB8-8E78-11D0-8C47-00C04FC295EE}
DLL – C:\Windows\System32\WINTRUST.DLL
FuncName – CryptSIPVerifyIndirectData
Also Read: Latest IOCs – Threat Actor URLs , IP’s & Malware Hashes
MITRE Technique
T1588.003 – Obtain Capabilities: Code Signing Certificates
Adversaries may buy and/or steal code signing certificates that can be used during targeting. Code signing is the process of digitally signing executables and scripts to confirm the software author and guarantee that the code has not been altered or corrupted. Code signing provides a level of authenticity for a program from the developer and a guarantee that the program has not been tampered with.[1] Users and/or security tools may trust a signed piece of code more than an unsigned piece of code even if they don’t know who issued the certificate or who the author is.
Prior to Code Signing, adversaries may purchase or steal code signing certificates for use in operations. The purchase of code signing certificates may be done using a front organization or using information stolen from a previously compromised entity that allows the adversary to validate to a certificate provider as that entity. Adversaries may also steal code signing materials directly from a compromised third-party.
Whoever used the technique
LAPSUS, MegaCortex, Ryuk, OutSteel, Stuxnet, BlackTech, Ember Bear and Wizard Spider.
This is a time-consuming process, but ensures that missing, compromised or unused certificates are revoked, renewed or replaced. Incident Responder / Soc analyst can Verify the validity of the digital signature hash with Get-AuthenticodeSignature in powershell for specific files, monitor for changes in registry modification and a write effective Windows Defender Application Control (WDAC) policy rules to find and block the code signing abuse.



































